Trusted Platform Computing 🚀
 Abhinandan Khurana
Abhinandan Khurana
Hello, Tech enthusiasts!
Welcome to this blog series where we delve into the fascinating world of Trusted Platform Modules (TPMs). In this series, we will explore what TPMs are, their history, how they work, and their practical applications in enhancing security. By the end of this series, you'll have a solid understanding of TPMs and their importance in modern computing.
Glossary
TPM (Trusted Platform Module): A hardware-based security device that performs cryptographic operations.
NVRAM (Non-Volatile Random-Access Memory): Memory that retains data even after the system is powered off.
ECC (Elliptic Curve Cryptography): A type of public key cryptography based on the algebraic structure of elliptic curves.
RSA (Rivest-Shamir-Adleman): A widely used public key cryptosystem for secure data transmission.
SEED: Initial value used in key generation processes within TPM.
Primary Key: A key generated by the TPM that never leaves the TPM, used to encrypt child keys.
Child Key: A key created by the TPM and encrypted by its parent key for various cryptographic operations.
What is TPM?
The Trusted Platform Module (TPM) is a security tool that can be part of your computer's motherboard, CPU, or provided by a software that controls the system.
It works below the level of the operating system and the boot sequence, which means it can check if these systems are safe even if they've been tampered with.
However, if you look at the many pages of guidelines and additional documents by TCG (Trusted Computing Group), you'll see that TPMs are quite complicated.
Small scenario related to importance of TPM in security
Imagine a large financial corporation, VulnCorp, handling sensitive customer data and financial transactions. Despite their robust digital security measures, a group of hackers managed to infiltrate their network through a phishing attack. They installed malware that could manipulate the boot process and load malicious software before the operating system.
Here’s where a TPM could have made a difference: TPMs check the integrity of the boot process, verifying each component before the operating system loads. If VulnCorp had implemented TPM technology, the TPM would have detected unauthorized changes to the boot sequence initiated by the malware. This would trigger a security alert, preventing the system from loading the compromised operating system, thus nullifying the hackers’ attempts to steal sensitive data.
History of TPM
Early Development and Origins (1999-2003)
1999: Concept emerges from the Trusted Computing Platform Alliance (TCPA) by IBM, Intel, HP, Microsoft.
2001: TCPA releases first specification (TCPA Main Specification 1.0).
Establishment of the Trusted Computing Group (TCG) (2003)
- 2003: TCPA evolves into TCG; TPM 1.1b specification released.
TPM 1.2 Specification and Adoption (2005-2009)
2005: TCG releases TPM 1.2 specification with enhanced key management and platform attestation.
2006-2009: Widespread adoption in enterprise devices (laptops, desktops, servers).
Transition to TPM 2.0 (2011-2014)
2011: TCG releases TPM 2.0 specification; more cryptographic algorithms, flexible architecture.
2013-2014: Integration into new hardware platforms and major OS support (Windows, Linux, macOS).
TPM 2.0 Implementation and Regulatory Mandates (2015-2020)
- 2015-2020: TPM 2.0 becomes industry standard; adoption driven by regulatory guidelines (NIST, GDPR).
TPM in Modern Computing (2020-Present)
2020: Continued evolution of TPM 2.0; enhanced for cloud computing, IoT devices.
2021: Microsoft mandates TPM 2.0 for Windows 11, underlining its importance in modern security.
How TPM works?
TPM functions as a secure cryptoprocessor, performing key management, encryption, and integrity checking below the operating system level. It can store passwords, security certificates, and encryption keys securely, preventing unauthorized access and tampering.
Practical Applications of TPM
Here are the main tasks a TPM performs:
The TPM stores passwords, security certificates, and encryption keys securely and prevents unauthorized tampering.
It stores information about the computer securely, so it’s easy to detect if anyone has tampered with the computer.
A TPM can securely generate encryption keys so that the process cannot be spied upon or interfered with.
Seal and unseal keys, ensuring keys are only accessible when the system is trustworthy.
In conclusion, TPMs are used in various security applications:
Checking the boot state
Device identification
Secure key management
Creating secure authorization systems
Ensuring secure sessions
How does TPM works internally?
Here is an example to make it simpler and clearer: (READ THIS AGAIN AFTER COMPLETING the latter content)
Let's say you have a safe (the TPM) and inside that safe, you have a locked box (primary key). Inside this locked box, you place another smaller locked box (child key). The smaller box can be taken out of the safe, but it can't be opened because it's protected by the lock from the bigger box (encrypted by the parent key). The big box can't be taken out of the safe (never leaves the TPM).
So, the big box (primary key) protects the smaller box (child key), and the safe (TPM) protects the big box. This process ensures a secure way of handling keys, where even if the child key is somehow exposed, it can't be used because it's encrypted by the primary key.
TPM has the following architecture
SEED - This is usually setted-up by the manufacturer, which plays a vital role in generating the primary/private key data inside the KDF (key derivation function) which also adds additional entropy to the KDF.
BONUS: By using the same user entropy added to the internal seed we can know who generated the same primary key.
What is PRIMARY KEY?
Primary Keys are generated by the TPM and never leave the TPM. They are used to protect (encrypt) child keys.
The Primary Key is at the root of the TPM's storage hierarchy. It's created when you take ownership of the TPM and it is protected by the Storage Root Key (SEED), which is burned into the TPM at manufacture time.
The private portion of a primary key, also called an endorsement key, is never exposed to any other component, software, process, or user.
As the private material of private keys never leave the TPM, we can only regenerate them. We can also persist a TPM key to avoid the regeneration of the keys.
We don't associate primary key in usual operations.
Primary keys are always asymmetric - ECC or RSA.
Usually, primary keys do not support signing, it is possible, however it is meant to wrap the child key by default.
What is CHILD KEYS?
Child keys can leave the TPM if they are encrypted by a parent key (also known as wrapping). This means that the child key is protected by the parent key.
A child key is a key that is created by a TPM and wrapped (encrypted) by its parent key.
A child key can be used for various purposes, such as signing, encryption, or storage.
A child key can also become a parent key if it meets certain conditions, such as being a storage key.
A child key can only be unwrapped (decrypted) by its parent key.
Child keys are the one that we usually associate with different operations.
They can be symmetric or key-hash as well like AES128
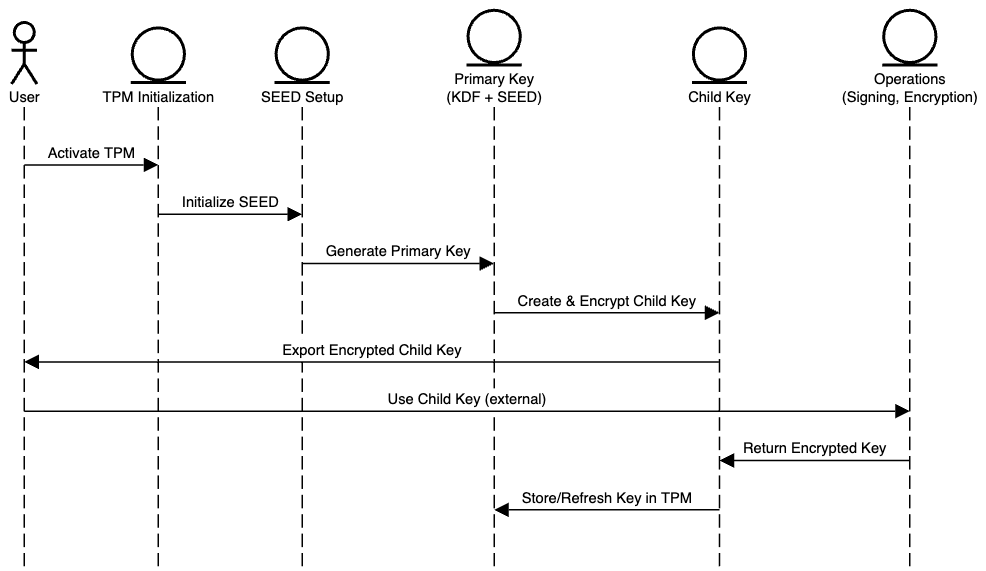
Visualize - illustrating sequential operation of a TPM in laymen terms
TPM Activation: The TPM is activated and initializes by setting up the SEED.
Primary Key Generation: Utilizing the SEED and the key derivation function (KDF), the TPM generates the primary key.
Child Key Creation: The primary key generates a child key, which it then encrypts.
Child Key Usage: The encrypted child key is exported for external operations like signing or encryption.
Child Key Return: After use, the child key is returned to the TPM, still encrypted.
When not to use a TPM?
For Speed - Built for high grade security, not for speed.
For Storage - Enough storage for critical artifacts like secrets and keys.
Primary Security Solution - Cannot be used as a standalone security solution (it's a passive security device)
Where to use TPM?
Better physical tamper protection
Built-in protection against MITM (Man-in-the-Middle)
TPM Secure storage use-cases:
Store certificates and other forms of authorizations in TPM's NVRAM
Use TPM's NVRAM as a secure counter (e.g., for counter the miles in taxis)
Use the TPM's NVRAM to store sensitive data
Conclusion
TPMs have become an essential component in safeguarding systems against unauthorized access and tampering. By understanding how TPMs work and their benefits, you can better appreciate their importance in today's security landscape.
I hope this series has provided valuable insights, and I encourage you to share your thoughts or questions in the comments below.
P.S. If you feel something can be improved in the above blog please feel free to contact me on LinkedIn, I am always open to constructive feedback!
Stay tuned for more detailed explorations in my upcoming posts!
Subscribe to my newsletter
Read articles from Abhinandan Khurana directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
