How to Set Up a Secure Hybrid Network on AWS
 Pierre-Francois H
Pierre-Francois H
Establishing a secure and scalable hybrid network is essential for organizations looking to extend their on-premises infrastructure to the cloud. A robust infrastructure forms the backbone of any successful cloud workload.
This article provides a guide to deploying a secure hybrid network on AWS using Terraform. It leverages services such as Transit Gateway, VPC, Direct Connect and/or S2S VPN, Route 53, and AWS Network Firewall to ensure robust security and centralized management.
Architecture Overview
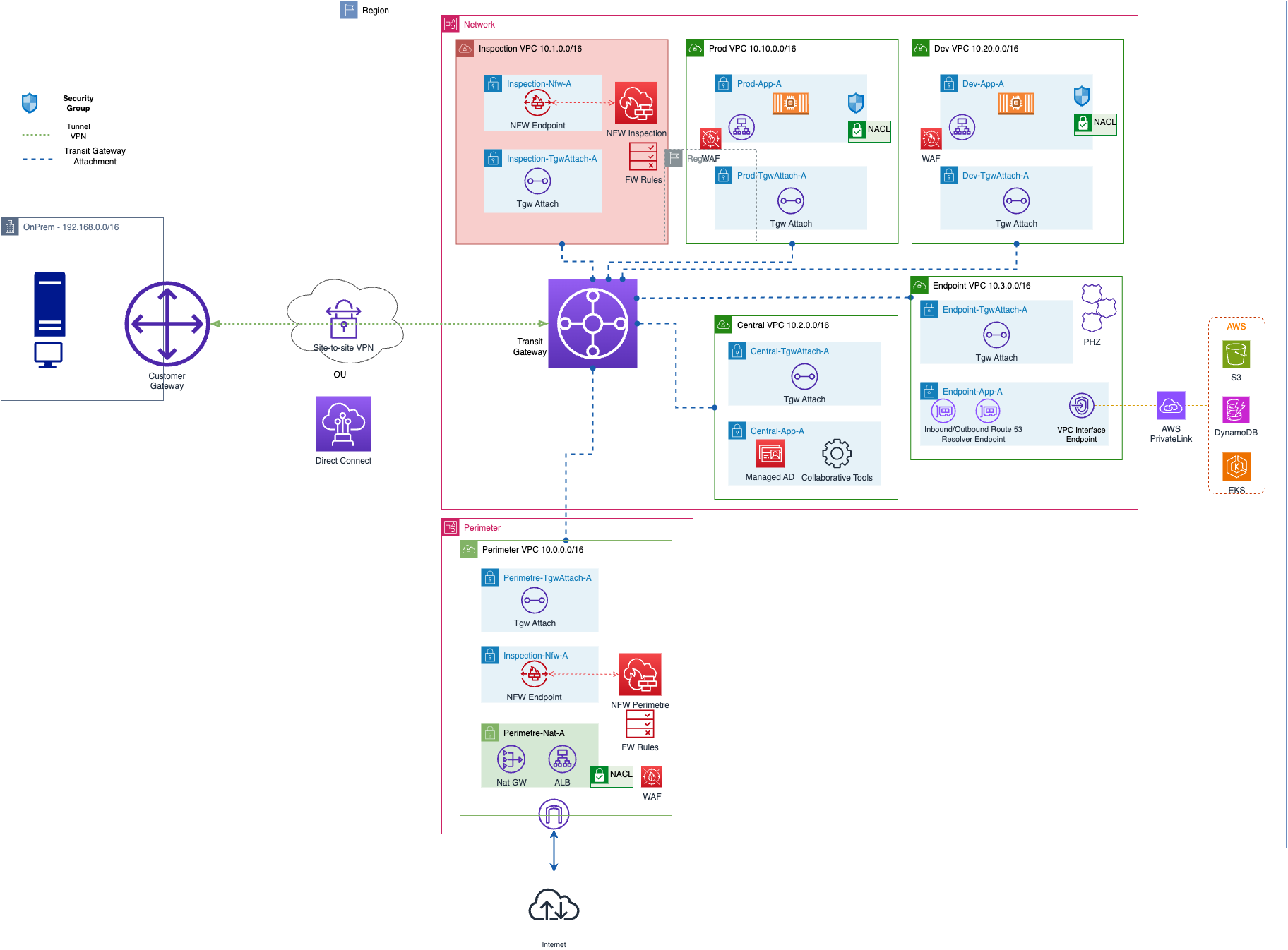
Target Architecture
The architecture uses AWS Transit Gateway as a central hub, connecting multiple VPCs and on-premises networks in a hub-and-spoke model. This setup allows for centralized and dynamic routing, supporting up to 20 Gbps per connection and enabling efficient peering regionally and inter-regionally.
Key Components
AWS Transit Gateway
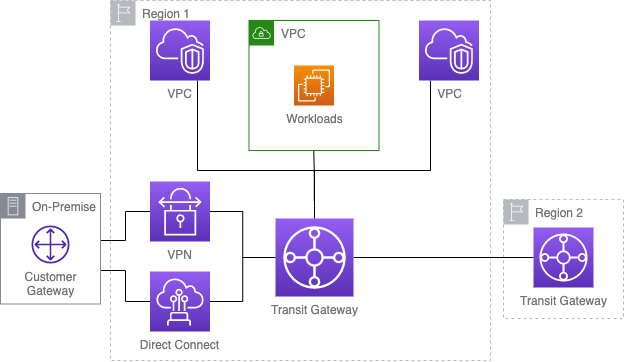
The AWS Transit Gateway acts as a central hub, simplifying the network by connecting multiple VPCs and on-premises networks. This setup uses a hub-and-spoke model, where the Transit Gateway is the hub, and the connected networks are the spokes. Here are some key considerations for the Transit Gateway:
Routing: Transit Gateway uses route tables to manage traffic flow between connected VPCs and on-premises networks. Each attachment (VPC, VPN, Direct Connect) can be linked to a specific route table, allowing precise control over traffic flow.
Static and Dynamic Routing: Transit Gateway supports both static and dynamic routing. Static routes are manually set, while dynamic routing uses Border Gateway Protocol (BGP) for automatic route updates, ensuring efficient traffic flow and less manual configuration.
Appliance Mode: This feature ensures that both incoming and outgoing traffic pass through the same network interface and Availability Zone, maintaining consistent routing throughout the flow.
Centralized Management: Efficient peering and centralized management are achieved via AWS Resource Access Manager (RAM).
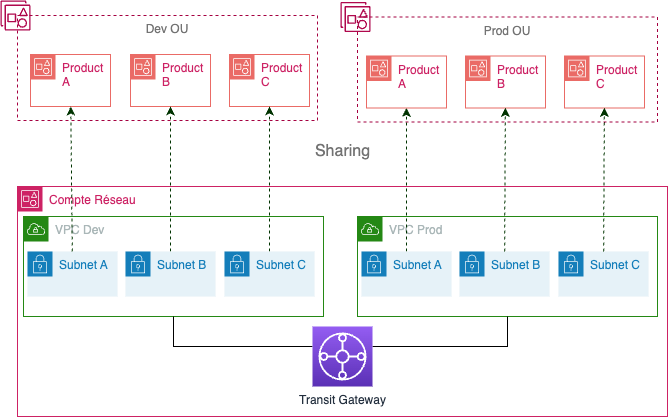
VPC Sharing
We already know what a VPC is. VPC sharing allows you to share VPCs with multiple AWS accounts, facilitating centralized management of network resources while reducing the number of VPCs needed. Some key features include:
Resource Sharing and Centralized Management: Subnets are shared across accounts, enabling resource management from a central account while maintaining security boundaries with Security Groups and Network ACLs (micro-segmentation).
Cost Efficiency: By reducing the number of VPCs, VPC sharing helps lower the costs associated with inter-VPC data transfer fees.
This design choice implies that different workloads ENIs stay in the same subnet or VPC. You can choose to deploy VPC per environment as displayed on the diagram or follow your organization's compliance rules.
Centralized Ingress/Egress and Inspection
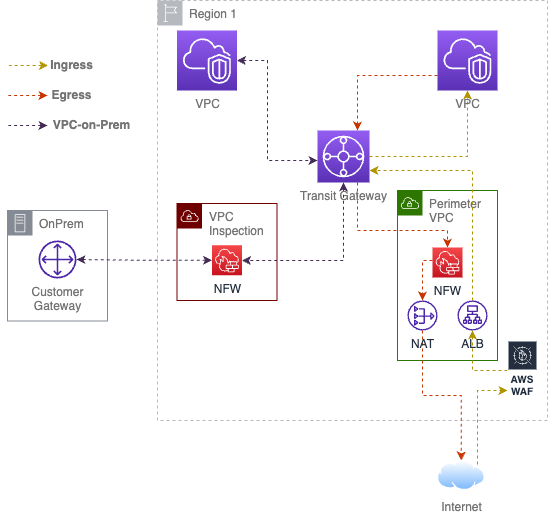
To enhance security, the architecture centralizes ingress and egress traffic.
Egress Traffic
NAT Gateway: Centralized NAT Gateway handles outbound traffic from private subnets. This setup reduces the need for multiple NAT Gateways, simplifying management and reducing costs. It is also easy to apply restrictive policies for workloads that do not allow access to the Internet.
AWS Network Firewall: Outbound traffic is inspected by the AWS Network Firewall before reaching the NAT Gateway.
Ingress Traffic
Application Load Balancer (ALB) and AWS WAF: The ALB, combined with AWS WAF, protects against web exploits and bots, ensuring that only legitimate traffic reaches your applications. ALB advanced request routing can be used to route traffic to multiple workloads
AWS Network Firewall: Inbound traffic is inspected by the Network Firewall in the Perimeter before reaching the application servers.
Inspection
VPC-to-VPC or OnPrem-to-VPC traffic can be inspected by implementing a centralized Inspection VPC. You can choose which traffic is inspected by setting the appropriate routes on the corresponding Transit Gateway routing table.
Hybrid DNS Resolution
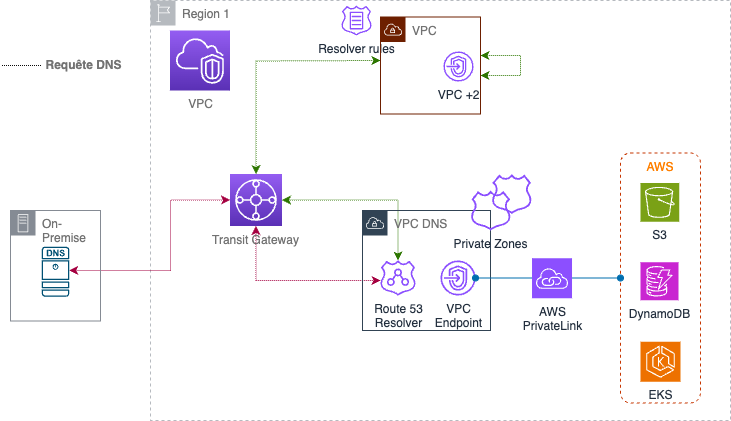
Effective DNS resolution is critical for hybrid networks. This architecture leverages AWS Route 53 for both internal and hybrid DNS resolution.
Private Hosted Zones
Private Hosted Zones: These zones allow DNS records to be visible only within specific VPCs. By associating private hosted zones with VPCs, internal DNS resolution is enabled, ensuring that internal services can communicate efficiently.
VPC Attachments: Private hosted zones can be attached to multiple VPCs, allowing for seamless DNS resolution across different network segments within the AWS environment.
Route 53 Resolver
Inbound Resolver: The inbound resolver endpoints enable DNS queries from on-premises networks to be resolved within AWS. This setup ensures that on-premises systems can resolve AWS internal DNS names.
What happens is that DNS servers OnPrem forward DNS queries for your AWS private hosted zones to the Inbound resolver endpoint which has a network interface in the Endpoint VPC. All private hosted zones should be associated with the VPC Endpoint allowing DNS resolution.
Outbound Resolver: The outbound resolver endpoints allow DNS queries from within AWS VPCs to be forwarded to external DNS servers. You can add Resolver rules for domains hosted on OnPrem.
Services Endpoint
Centralizing access to VPC private endpoints enables secure communication between VPCs and services such as Amazon S3, EKS, SSM, and other AWS services. This approach reduces the need for internet gateways, enhances security, and simplifies network architecture management.
Deployment
In this section, we’ll provide an overview of deploying this architecture using Terraform. You can find the complete code in the GitHub repository.
As illustrated in the diagram, the deployment uses two AWS accounts: one for Network resources and another for Perimeter resources. Additionally, the on-premises resources are deployed in a separate region, with an EC2 instance acting as the customer gateway.
The Terraform code is structured into modules that handle different components of the architecture:
Transit Gateway: Sets up the Transit Gateway as well as its routing tables. The TGW is shared with the principals provided in the
ram_principalsvariable.Perimeter VPC: Creates the VPC responsible for egress and ingress traffic handling, including Network Firewalls, NAT Gateways, and Application Load Balancers. The corresponding TGW route table is associated with this VPC.
Endpoint VPC: Endpoint services are listed in the variable
services. TGW route table propagation and association are also added in the configuration.Development and Production VPCs: Establishes isolated environments for development and production workloads, utilizing centralized VPC endpoints for connectivity to AWS Services. These VPCs are shared with the organization principals listed in the
subnet_sharing_principalsvariable. TGW route table propagation and association are also added in the configuration.On-Premises VPC: Sets up a simulated on-premises network environment in a different region, including VPN connections for secure communication with cloud VPCs. We use strongSwan and bird with an EC2 instance to handle IPSec VPN and BGP propagation.
This modular approach ensures that each part of the network is configured correctly and can be easily managed and updated. The architecture provides a robust and secure hybrid network foundation, facilitating seamless integration and efficient management of both cloud and on-premises resources.
Conclusion
This architecture provides a scalable and secure multi-VPC AWS network infrastructure using AWS Transit Gateway, VPC sharing, centralized ingress/egress inspection, and hybrid DNS resolution. By following this guide, organizations can extend their on-premises infrastructure to the AWS cloud, ensuring strong security and centralized management.
For further questions or detailed walkthroughs, feel free to reach out or leave a comment below. Happy networking!
Good to read:
Building a Scalable and Secure Multi-VPC AWS Network Infrastructure
Subscribe to my newsletter
Read articles from Pierre-Francois H directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Pierre-Francois H
Pierre-Francois H
👋 Hi, I’m @hpfpv ☁️ I’m a Cloud Infrastructure Architect | 8x AWS Certified 🚀 I build secure, scalable, and automated solutions on AWS using Terraform, CloudFormation, and CI/CD 📚 Always exploring hybrid cloud, serverless, and AI-driven architectures