TurboCharge Your Nmap Scan: Five Hacks 🧿🔍
 microbytesec
microbytesec
Overview: This post will explore five Nmap hacks and tips that security researchers and ethical hackers can use to optimize their scans, enhancing workflow and automation.
Understanding Nmap Default Scan
To grasp Nmap's scan timing, let's start with a simple scan without options to gauge its duration. By default, Nmap scans the top 1000 ports. Be prepared to grab a coffee ☕️ , as this will take some time.
nmap scanme.nmap.org
This scan took a while.

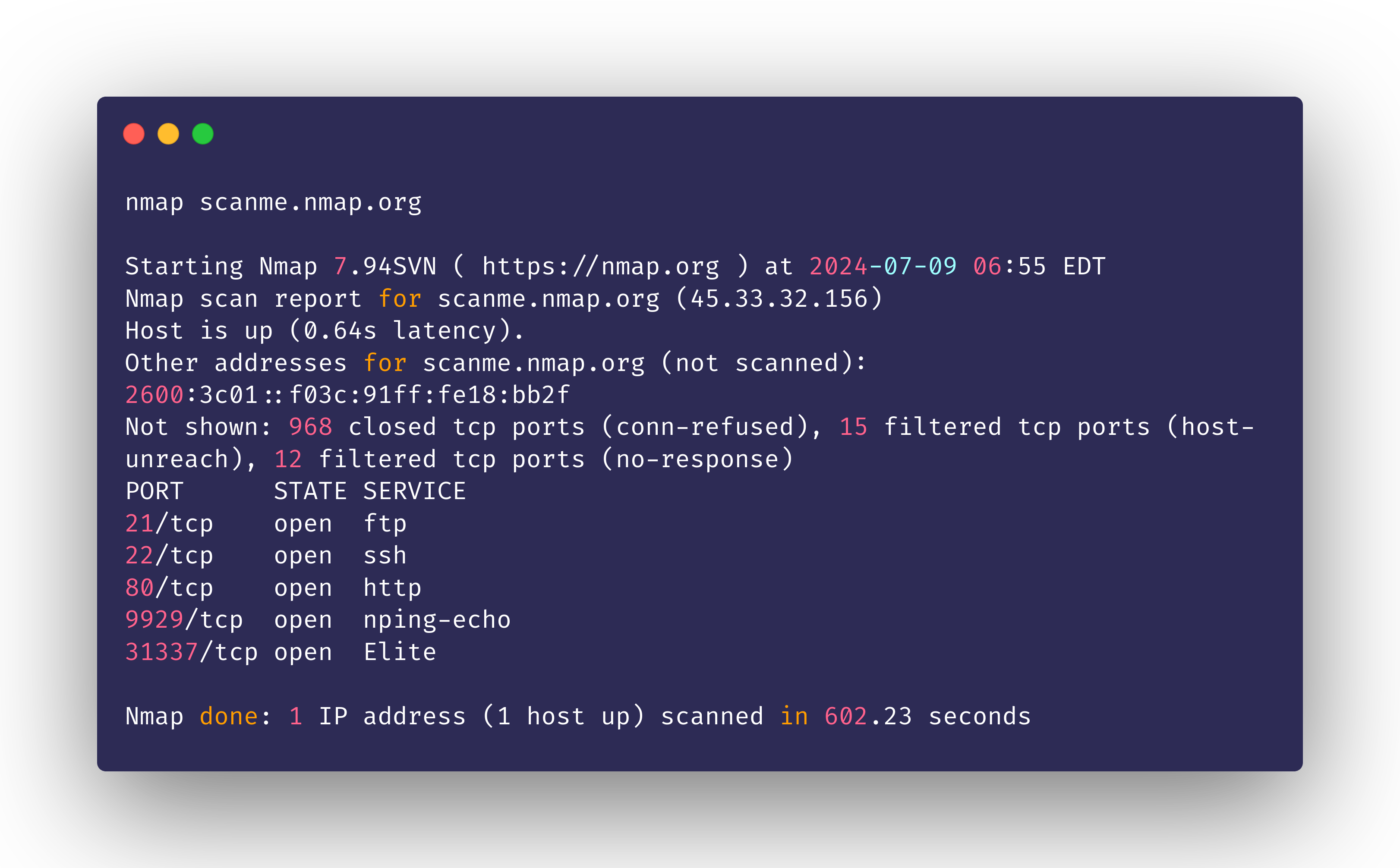
This basic Nmap scan without any configuration took about 10 minutes.
Aggressive Scan
If detection by security devices is acceptable, consider using the aggressive timing scan option. The -T4 option accelerates scanning by minimizing delays and prioritizing speed, though it may overwhelm the host. Be cautious of Intrusion Detection Systems (IDS) and firewalls during aggressive scans.
Nmap offers timing templates from T0 to T5, defaulting to T3 for normal scans. T5 is the fastest and most aggressive, potentially disrupting a host.
nmap -T4 scanme.nmap.org
This scan completed in under 1 minute, significantly faster than the default map scan.
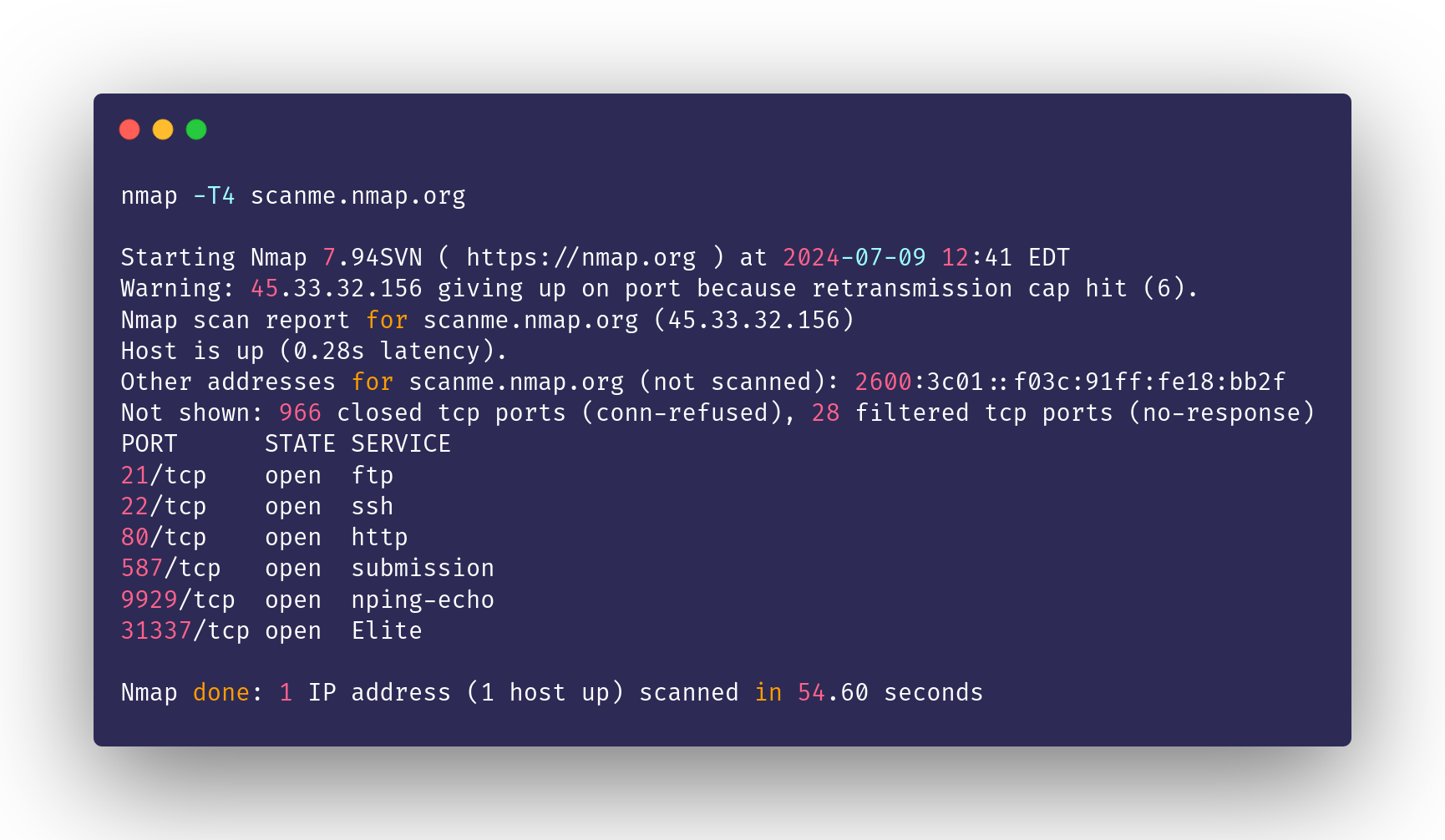
Stealth SYN Scan
The SYN scan method is an advanced and "stealth" scanning option of Nmap that leverages on the functionalities of the TCP protocol.
How the TCP Three-Way Handshake Works
Client initiates a connection by sending a TCP packet with the SYN (Synchronize) flag set.
Server responds with its own SYN and Acknowledgment (SYN-ACK) packet upon receiving the SYN request.
Client acknowledges the server's response with an Acknowledgment (ACK) packet, completing the handshake.
Nmap's TCP SYN scan establishes a connection without completing the full handshake. It enhances scanning speed by bypassing the need to receive SYN-ACK and ACK packets from the target system, reducing scan duration. SYN scanning is particularly effective for quickly identifying open, closed, and filtered ports on a target machine.
Executing a SYN Scan:
nmap -sS scanme.nmap.org
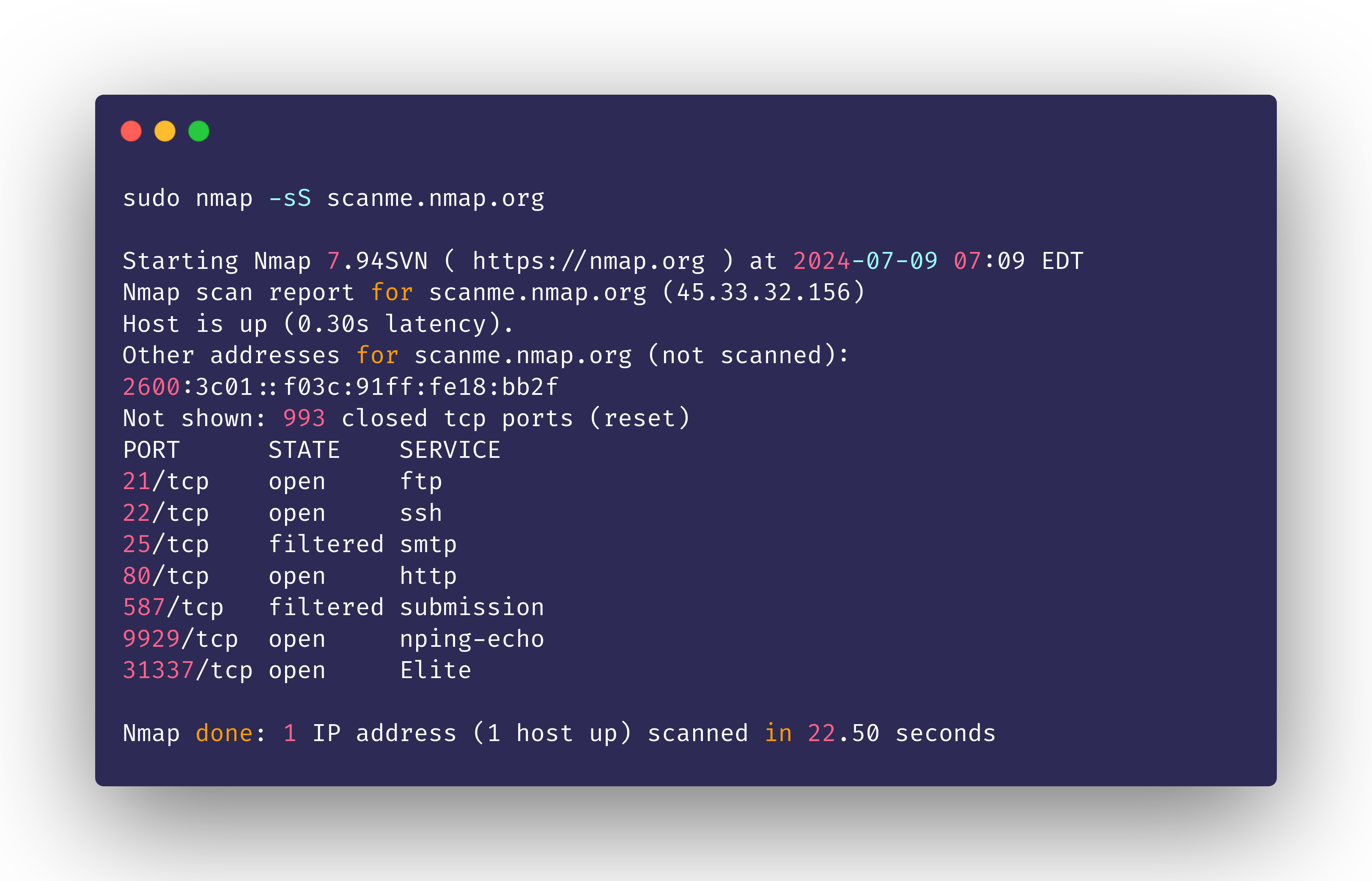
The output shows a significantly reduced scan duration compared to the default Nmap scan.
Disable DNS Resolution
The -n option prevents Nmap from performing hostname to IP address resolution for domains or subdomains, improving scanning efficiency by skipping DNS queries. This is particularly beneficial when scanning numerous hosts.
nmap -sS -n scanme.nmap.org
By utilizing the -n option alongside other Nmap options, scan duration can be further improved
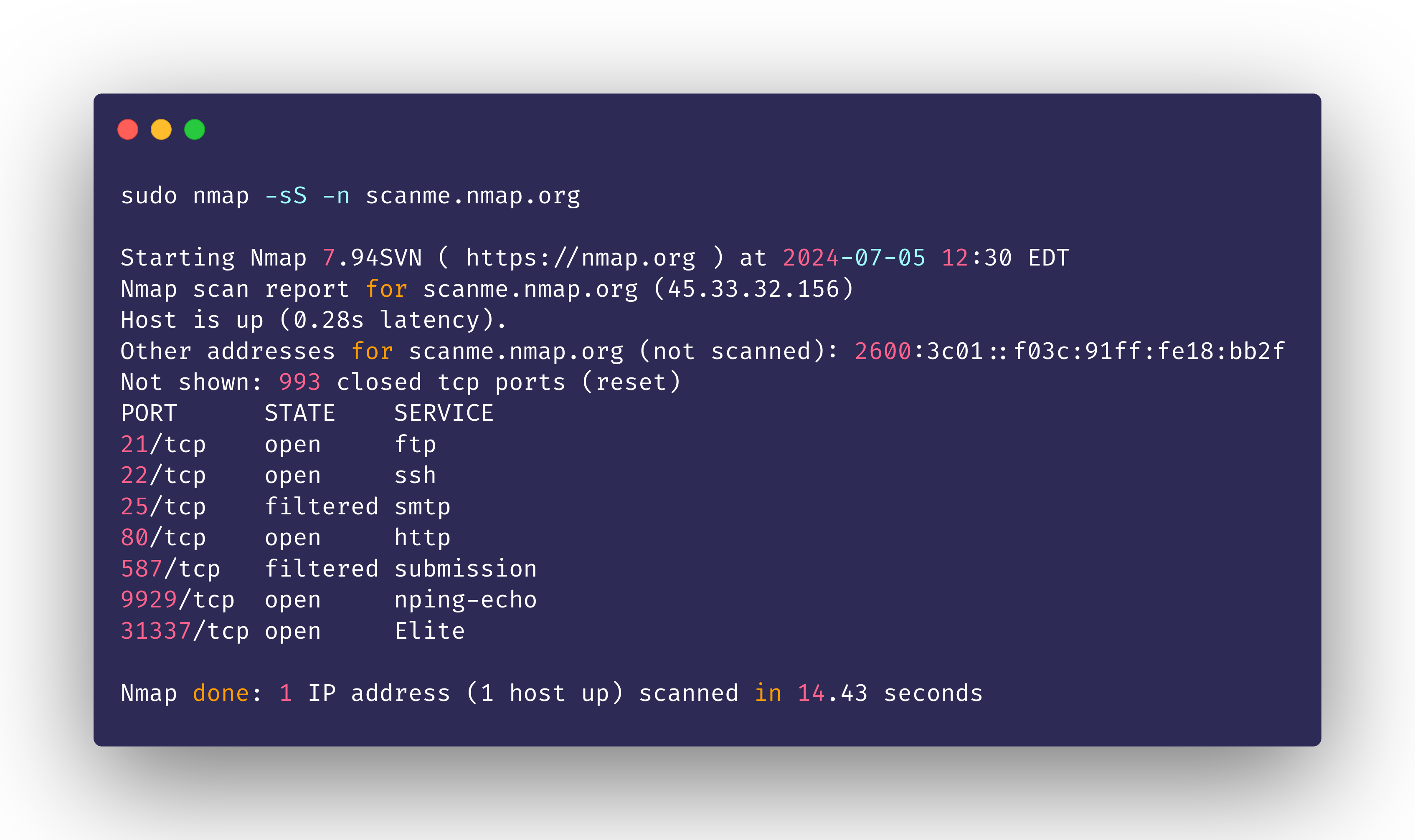
With this we get a much lesser time duration from Nmap.
Combining Method
Practically, we can combine the previous methods to boost the efficiency of the scan timing.For example, using both SYN scanning (-sS) and disabling DNS resolution (-n) together can significantly reduce the overall scan duration. This combination allows for faster identification of open, closed, and filtered ports while skipping DNS resolution.
nmap -sS -n -T4 scanme.nmap.org
Utilizing all the optimization methods yields a much shorter scan duration compared to individual methods
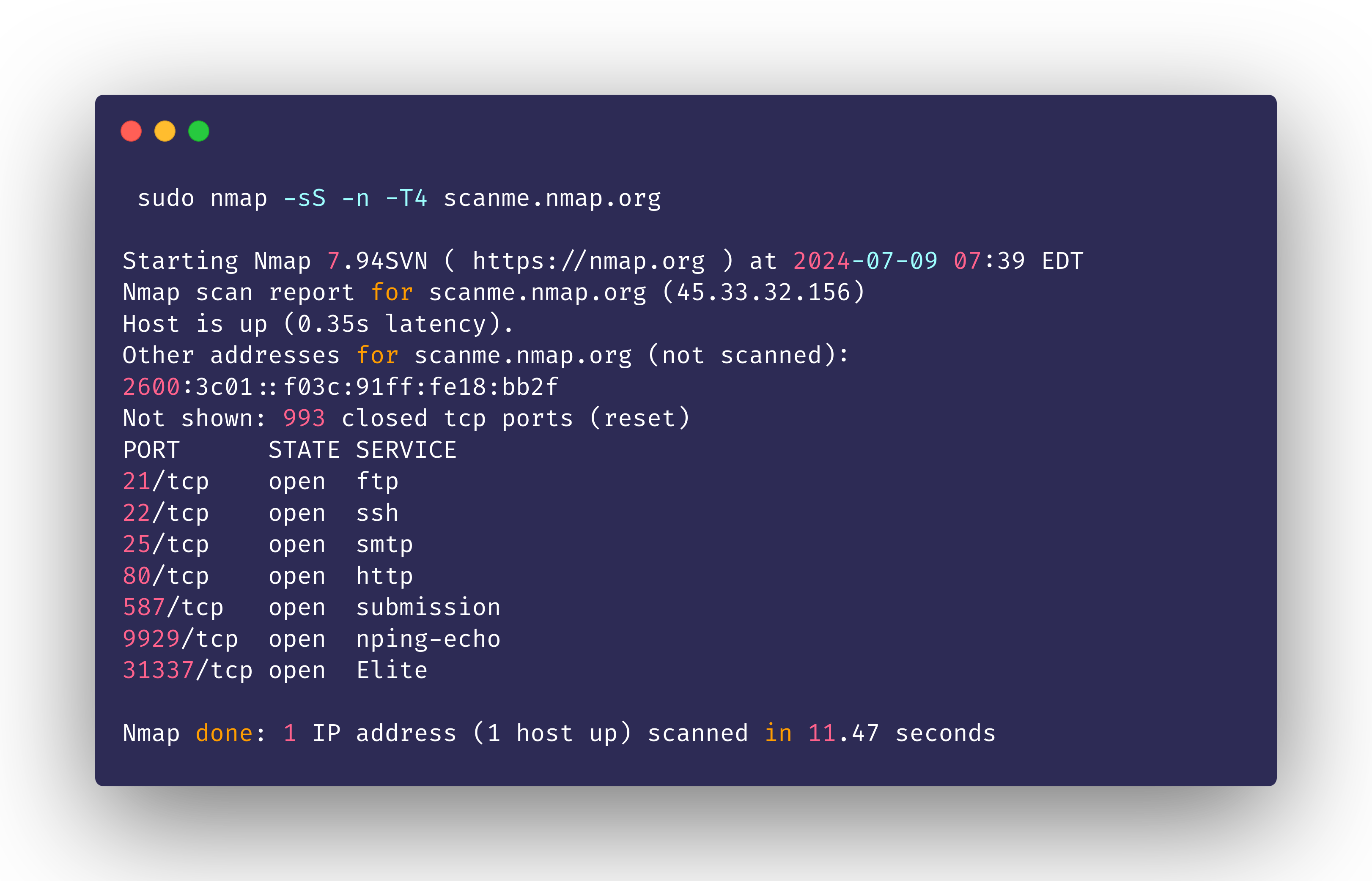
As can be seen, the scan duration is much shorter than the synchronized scan methods.
Go Faster with Fast Scan Method
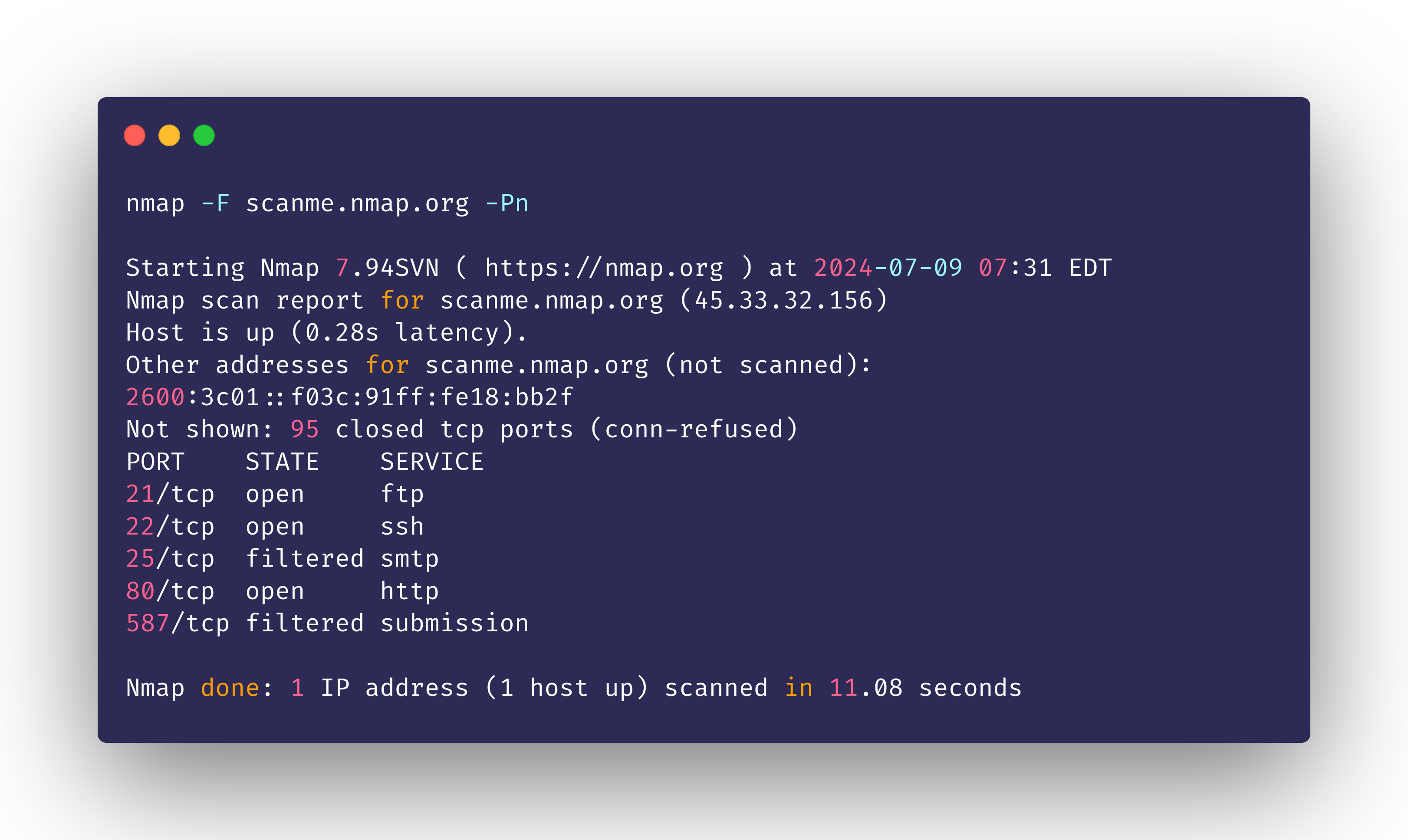
The fast scan method (-F) in Nmap checks fewer ports than the default 1000 and skips service version detection to increase speed. It's recommended to use the -n (disable DNS resolution) or -Pn (disable host discovery) options for better reliability.
nmap -F scanme.nmap.org -Pn
While the output shows fewer open ports, the scan duration is drastically reduced, to about 11 seconds.
Conclusion
By mastering these advanced techniques, security enthusiasts can transform Nmap from from a boring slow scanner to a blazing-fast toolkit. Network security professionals can leverage these techniques to perform comprehensive reconnaissance on a network scale, scan predefined lists of machines or hosts, and efficiently map out a network's attack surface.
Subscribe to my newsletter
Read articles from microbytesec directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by