Understanding AWS IAM: Your Essential Identity and Access Management Solution
 Pratik Anil Yadav
Pratik Anil Yadav
AWS IAM Explained: Comprehensive Guide to Secure Access Management
Fine-grained control of who can do what
Eg -user Bob can launch server
AWS IAM Demystified: Key Features and Best Practices
Free
Centralized AWS service
Default scope is AWS account
Deny by default
Authentication:-
Supports Multi-Factor Authentication (MFA) to enhance security.
Access Control: -
Identity-based Policies: JSON policy documents that are attached to an identity (user, group, or role) and define what actions are allowed or denied.
Resource-based Policies: Attached directly to resources (like S3 buckets) to control access to those resources.
Temporary Credentials:-
Generate temporary security credentials for accessing AWS services and resources.
Federation:-
Integrate with corporate directories and SSO providers to use existing identities for access to AWS resources.
Auditing and Monitoring:-
Track user activity and resource access through AWS CloudTrail.
Best Practices:-
Use the principle of least privilege to give users only the permissions they need.
Regularly rotate security credentials to enhance security.
Enable MFA for critical operations.
Compliance:-
IAM helps meet compliance requirements by providing secure access controls.
Scalability:-
Scales seamlessly to handle millions of users and permissions.
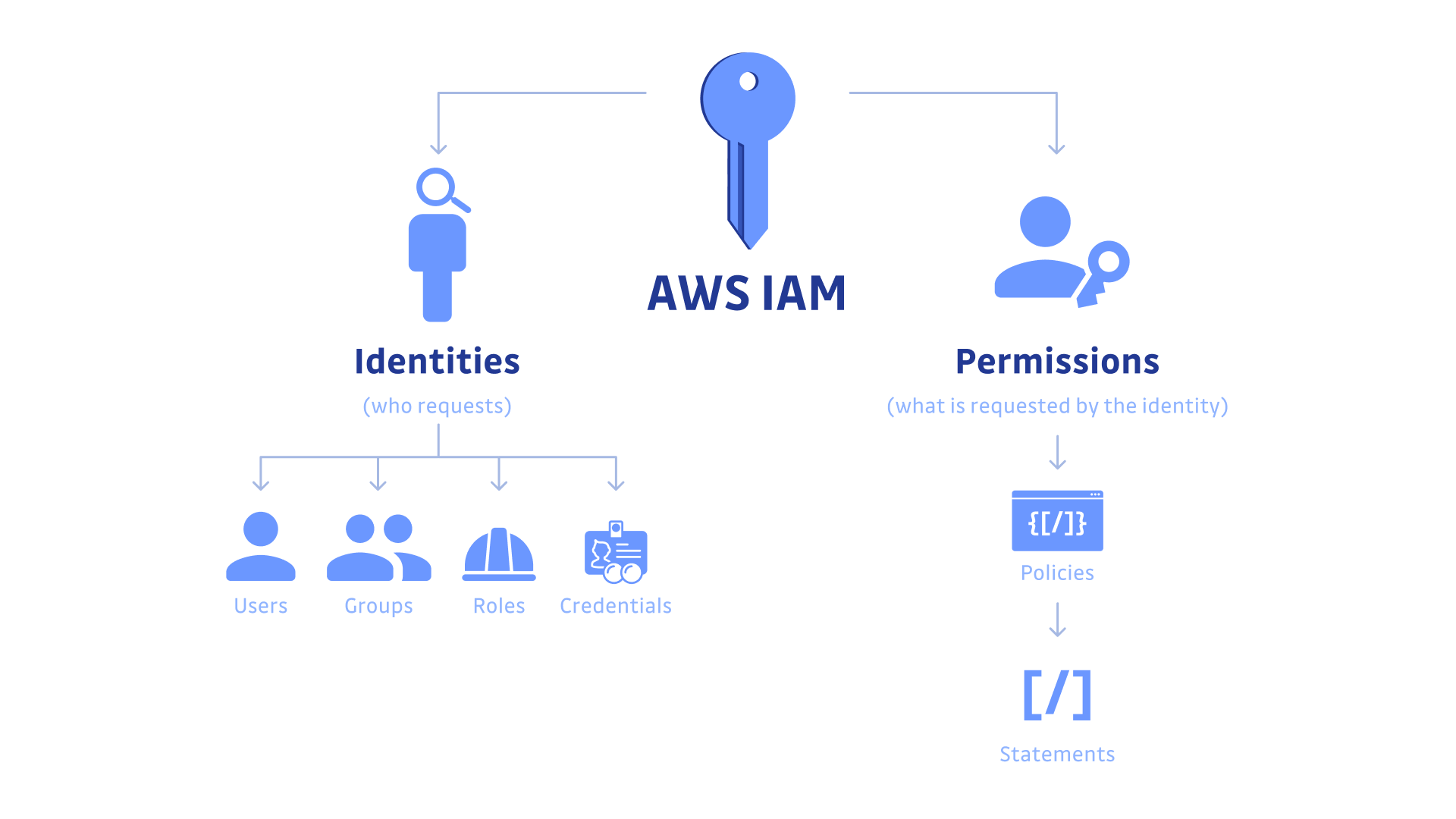
IAM user :-
Root
IAM User
Root User
The identity used to create AWS account
Complete access
Best practices
Don’t use this account for the everyday
Setup physical MFA and lock it away
Don’t use your Amazon.com shopping account
IAM Users
an identity with assigned permissions
can have username/password access to AWS console
can have (secret) key-based access to AWS APIs
Best Practices
rotate credentials (keys, passwords)
MFA
password policy
IAM Groups
collection of IAM users
operates like you’d think
Best practices
manage permissions with groups
i.e., assign policies to groups instead of users
IAM Policies
Set of permissions to be granted or denied
JSON documents
Can be assigned directly to IAM users
IAM Role
A 2nd type of AWS identity–also has assigned permissions–similar to IAM users
Designed to be temporarily assumed–e.g. by an EC2 instance
No associated credentials
Instance Profiles–assigned to EC2 instance–container for one or more IAM roles
Best Practice
.Users – Create individual users.
•Permissions – Grant least privilege.
•Groups – Manage permissions with groups.
•Conditions – Restrict privileged access further with conditions.
•Password – Configure a strong password policy.
•Rotate – Rotate security credentials regularly.
•MFA – Enable MFA for privileged users.
•Roles – Use IAM roles for Amazon EC2 instances.
•Root – Reduce or remove use of root.
Conclusion :
In conclusion, AWS IAM is an essential tool for managing access and ensuring security within your AWS environment. By leveraging its robust features such as multi-factor authentication, identity and resource-based policies, and temporary credentials, you can maintain fine-grained control over who can access your resources and what actions they can perform. Adhering to best practices like the principle of least privilege, regular credential rotation, and enabling MFA for critical operations will further enhance your security posture. AWS IAM not only helps in meeting compliance requirements but also scales seamlessly to accommodate growing user bases and complex permission structures, making it a vital component of your cloud security strategy.
Subscribe to my newsletter
Read articles from Pratik Anil Yadav directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
