Satoshi Scoop Weekly, 26 Jul 2024
 Cryptape
CryptapeTable of contents
- Cypto Insights
- Nashville Bitcoin 2024: Beyond Price Trends and Political Dynamics, What to Watch?
- A Free Bitcoin Relay Attack Is Disclosed
- Is It Possible to Open 10 Billion Lightning Channels per Year?
- StarkWare: Its First ZKP Successfully Verified on Bitcoin Signet
- What Happened in the Evolution from RGB to RGB++ then to RGB++ Layer?
- UTXO Stack: Scaling Bitcoin with RGB++
- IBO Platform Launched by Seal: New Way for Bitcoin Asset Issuance
- Does Bitcoin 'E-Waste' Hold Up?
- Three Most Common Crypto Business Models
- Top Reads on Blockchain and Beyond

Cypto Insights
Nashville Bitcoin 2024: Beyond Price Trends and Political Dynamics, What to Watch?
Discussion topics from the Open-Source Stage of the upcoming Bitcoin 2024 event have been announced. This article highlights some technological breakthroughs to watch, including innovations from the past year (Unlocking Expressivity With OP_CAT, BITVM), privacy issues (Bitcoin's Legal Battle for Privacy, Cross-Input Signature Aggregation), and Bitcoin Free Banking (ecash).
For more details, see the full conference agenda.
A Free Bitcoin Relay Attack Is Disclosed
Developer Peter Todd disclosed an extremely low-cost relay attack on the Bitcoin development mailing list (referred to as the Free Relay Attack). This attack exploits the lack of full RBF (Replace-By-Fee) in Bitcoin Core, broadcasting transactions with different fee rates at an exceptionally low cost, taking advantage of policy differences between Bitcoin Core nodes and miners, leading to node bandwidth waste.
Peter Todd said he had reported similar relay attack issues to the Bitcoin Core, but the team closed his PR proposing to enable full RBF by default, without showing any due attention to this issue.
Is It Possible to Open 10 Billion Lightning Channels per Year?
- Peter Todd mentions that he is working on the math of opening about 10 billion channels per year using the current Lightning technology.
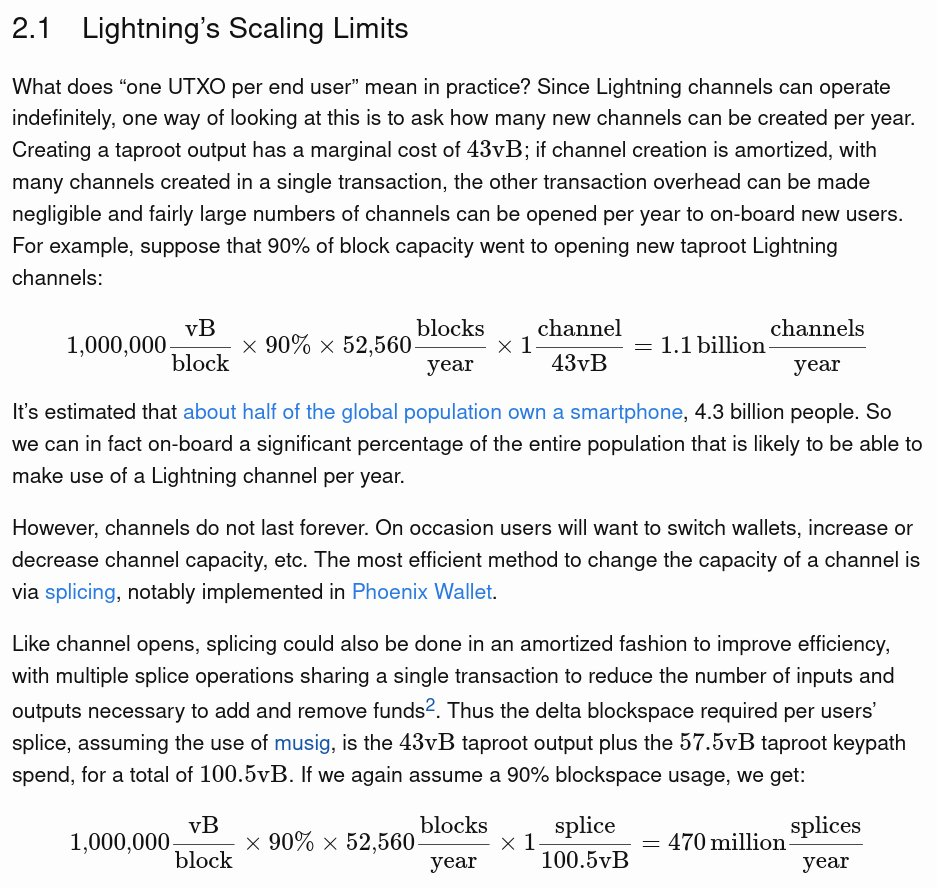
Image: @peterktodd
StarkWare: Its First ZKP Successfully Verified on Bitcoin Signet
- StarkWare announced their first successful verification of zero-knowledge proof on the Bitcoin Signet network using a new STARK verifier. This development paves the way for ZK-based Bitcoin layer 2 solutions, enhancing Bitcoin's scalability and advancing global payment prospects.
What Happened in the Evolution from RGB to RGB++ then to RGB++ Layer?
RGB++ Layer Upgrade: This upgrade expands the relationship between Bitcoin and CKB to all UTXO chains. RGB++ protocol has been abstracted and stands alone as a layer combining all UTXO chains, serving as a universal, cross-chain interoperable UTXO middleware. It enables not just CKB, but any Turing-complete UTXO chain to integrate as an indexer.
Beyond Cross-Chain: Unlike traditional bridges that create 'fake coins' on side chains, RGB++ uses a 1:1 interaction between chains, eliminating the need for any 'cross-chain' action.
Bitcoin Finance (BTCFi) : The RGB++ Layer upgrade aims to promote the growth of BTCFi by enhancing interoperability and functionality across UTXO chains.
UTXO Stack: Scaling Bitcoin with RGB++
Native Layer 2 Scalability: UTXO Stack introduces a Bitcoin-native, programmable Layer 2 solution that aligns seamlessly with Bitcoin's UTXO model, unlike non-native solutions that require patches for compatibility and often rely on centralized services.
Innovative Isomorphic Binding: The RGB++ protocol features Isomorphic Binding, a technique that maps Bitcoin UTXOs to eUTXOs on the RGB++ Layer, enabling smart contract capabilities without the need for separate client-side validation, thus enhancing user-friendliness.
Bridgeless Cross-Chain: A standout feature of the RGB++ protocol is the ability to transfer assets across chains without traditional bridges, but relying on a "leap" where asset ownership is bound to UTXOs, allowing assets to move to another chain when the UTXO of that chain is used to unlock them.
IBO Platform Launched by Seal: New Way for Bitcoin Asset Issuance
With the advent of RGB++ Layer and UTXOSwap, the IBO (Initial Bitcoin Offering) emerges as a secure method for asset issuance on UTXO chains.
Secure and Community-Driven: IBOs enable projects to raise funds securely, with the capital locked for liquidity creation on UTXOSwap and Liquidity Provider tokens locked for a year. The majority of tokens are distributed to the community through staking, fostering quick circulation and eliminating continuous VC unlock pressures.
Fair Pricing and Smart Contract Protection: Prices are set at seed round levels, giving the community equal opportunities. The use of a bonding curve ensures that if the sale isn't completed in time, funds are automatically refunded, safeguarding participants.
Does Bitcoin 'E-Waste' Hold Up?
- In this study, Daniel Batten challenges the claim that Bitcoin mining results in electronic waste, contending that the assertion is inherently flawed. He highlights that the recycling of obsolete ASICs is quite profitable. Additionally, ASICs are free of heavy metals, easily recyclable, and contribute minimally to landfill waste. Moreover, they possess a longer service life, being 2.76 times more durable than the average smartphone.
Three Most Common Crypto Business Models
Mason Mystrom from Variant Fund outlines several common cryptocurrency business models, which are:
Exchange and marketplaces — fee on transactions
Transaction sequencing — own and monetize valuable order flow
Asset managers — fee on assets under management or yield generation
Top Reads on Blockchain and Beyond
Mining Pool Game Theory During Forks
Bitcoin developer 0xB10C provides a detailed introduction to the behavior of mining pools during forks, including: which block a pool chooses to mine on, whether they act rationally and mine on their own blocks, and how does the game play out. The article also provides some recent examples of pool behavior.
A short video on this topic is also available on YouTube.
BIP 353 Username Guide: Use Repeatable, Privacy-Preserving Payment Method for Enhanced Anonymity
BIP 353 DNS Payment Instructions aims to solve the problem of how to repeatedly pay someone without having to confirm a new address with them, enabling access to payment information without running a server.
With the increasing popularity of Silent Payments and BOLT 12 invoices, and their integration into wallets like Cake Wallet, Phoenix Wallet, and Zeus, users can generate reusable payment codes for on-chain and Lightning Network transactions, set up static DNS records, and receive repeat payments without linking any two payments. This article is a BIP 353 guide, helping users utilize this new feature to enhance privacy.
Subscribe to my newsletter
Read articles from Cryptape directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
