Try Hack Me: Friday Overtime Complete Write-up 👾
 Christine Coomans
Christine Coomans
In my most recent side-quest in life, I decided to dive back into the world of hAcK1_nG. The last time I was dabbling in the art of Cybersecurity, I focused more on red-teaming, but this time my interest is peaked by the life of a blue-teamer.
That’s right, I’m joining The Defenders (trademark coming soon). But before I do that, let’s have a look at completing the Friday Overtime room.

So in this scenario, we are the only remaining CTI Analyst working overtime at PandaProbe Intelligence. We need to investigate potential file attachment breaches that are suspected to contain malware samples.
Let’s start by running our machine. This might take a few minutes, so wait until your machine IP is populated.
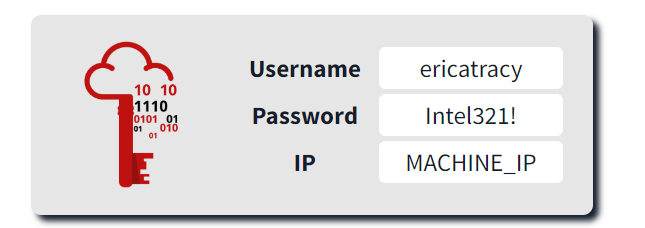
After your machine is up and running, let’s start answering our questions.
1. Who shared the malware samples?
On the machine, open up Chromium and navigate to your given IP Address. At the top of the CentOS screen is an option to “Log in — DocIntel”. Click on it and log in with the given credentials.
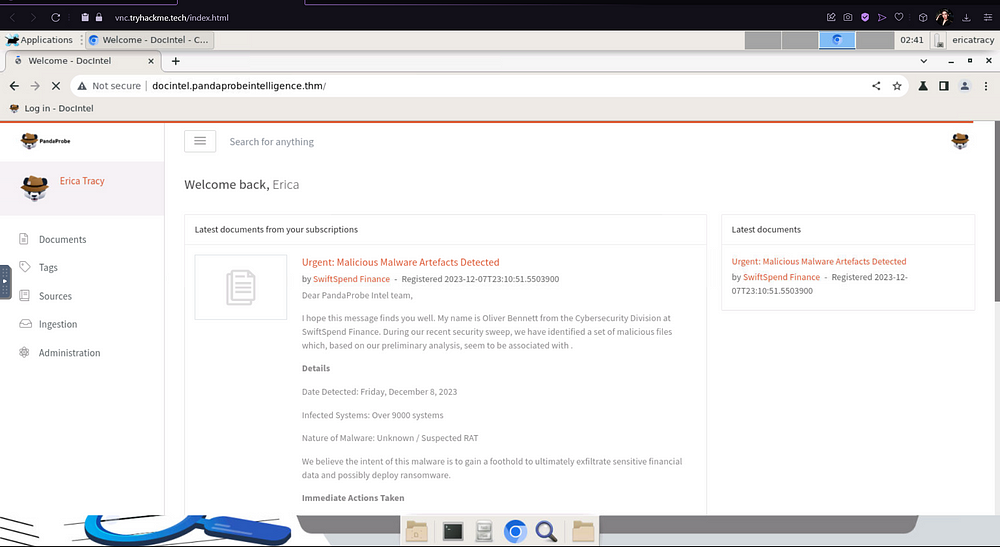
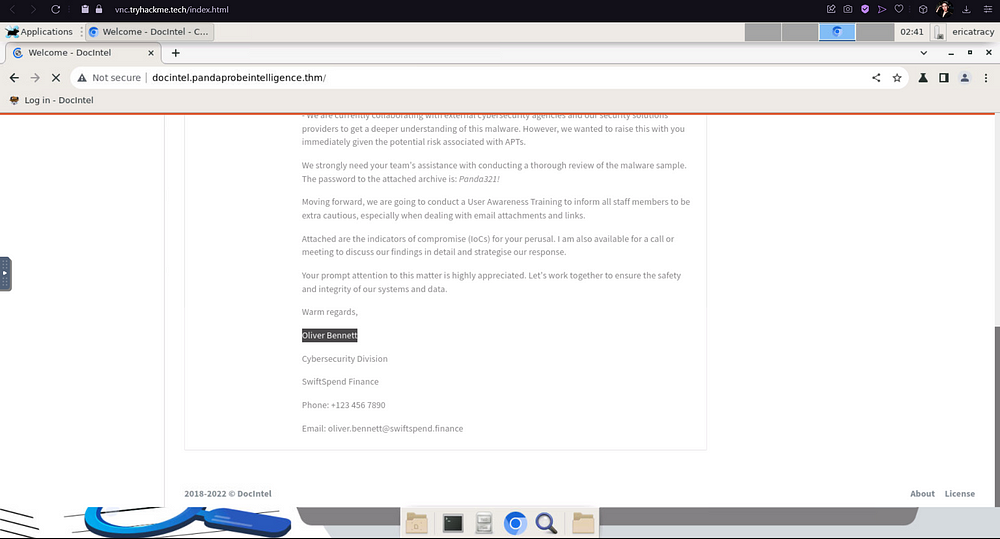
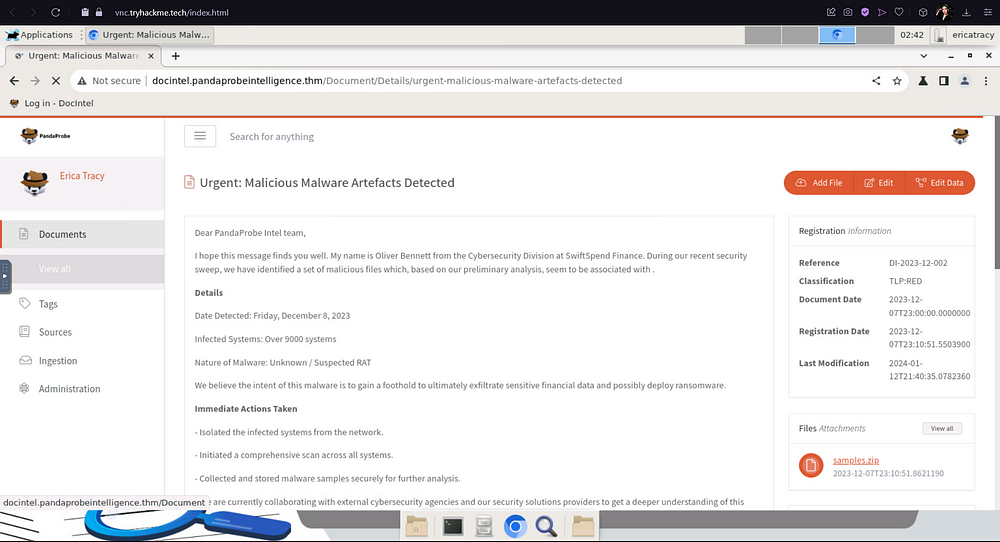
From there on you will be greeted by your email, which contains the information on the breach as well as the document containing the files, and the password to the document.
If you scroll down, you will see the name of the person who shared the malware sample files.


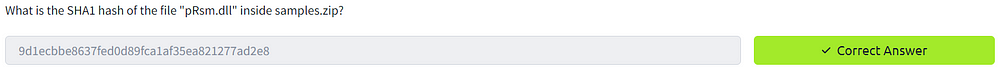
2. What is the SHA1 hash of the file “pRsm.dll” inside samples.zip?
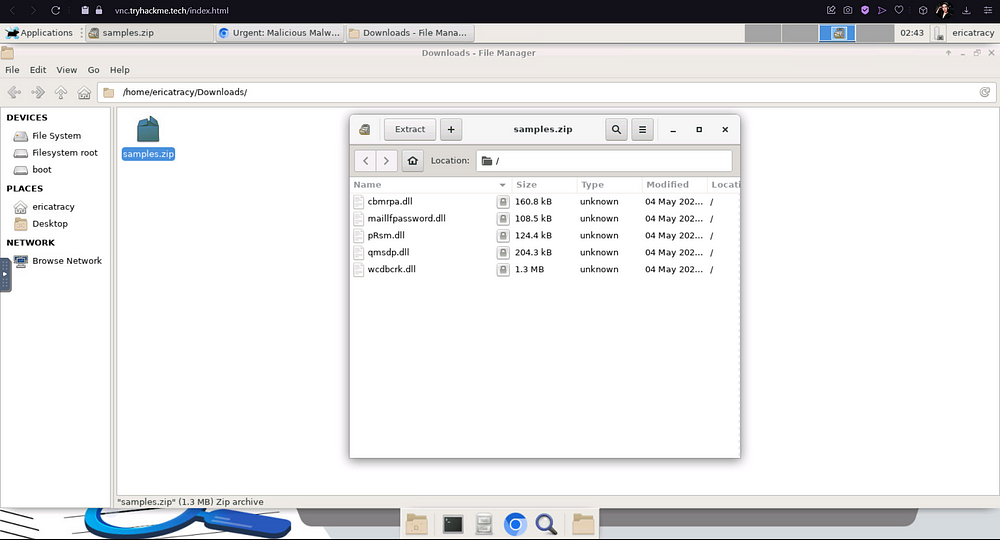
To find this out, we will need to first download the actual attachment and extract the files from it. Click on the attatchment on the right to download the file called “sample.zip”.

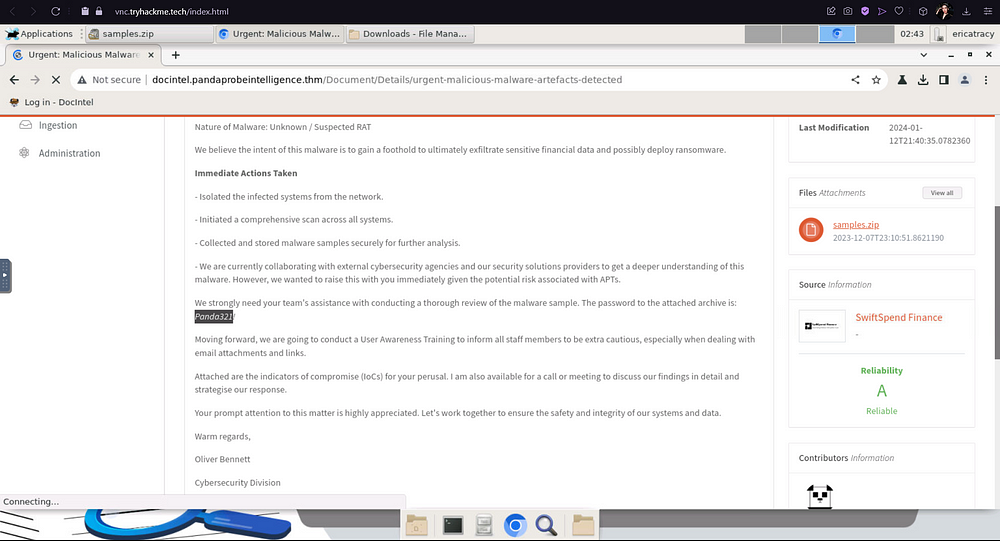
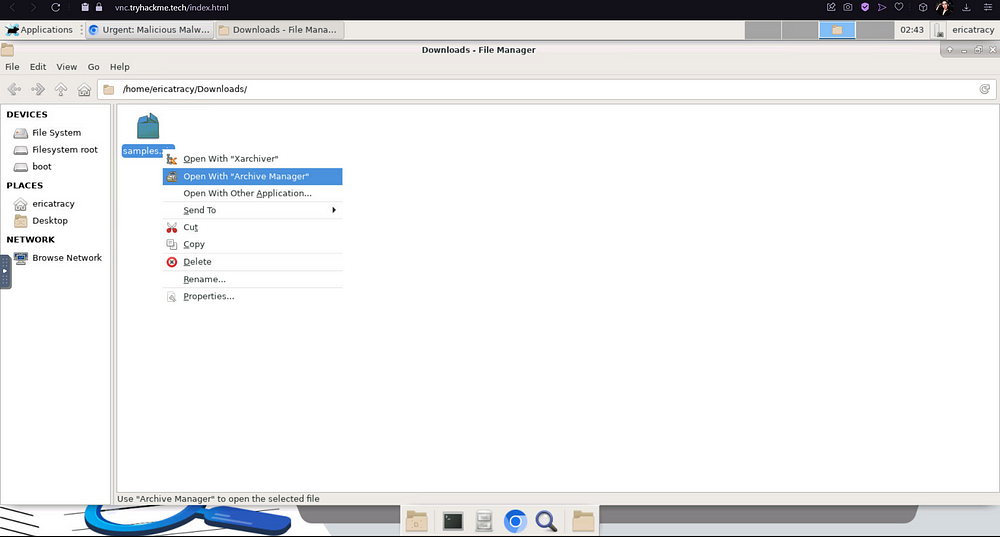
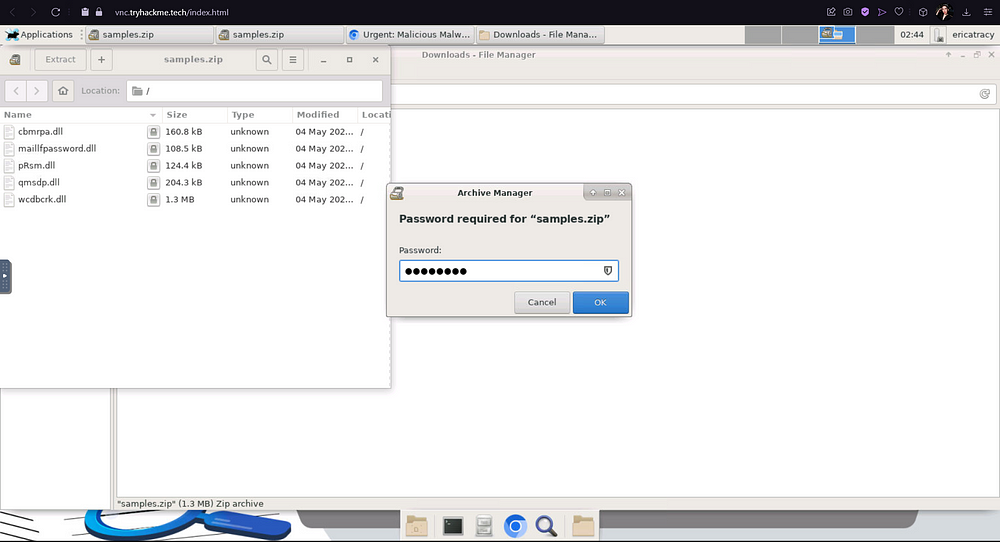
Now, you can either extract this zipped folder in the Command Line, or just by right-clicking it and extracting it manually. Remember, the password to this file is Panda321!, so enter that when prompted.
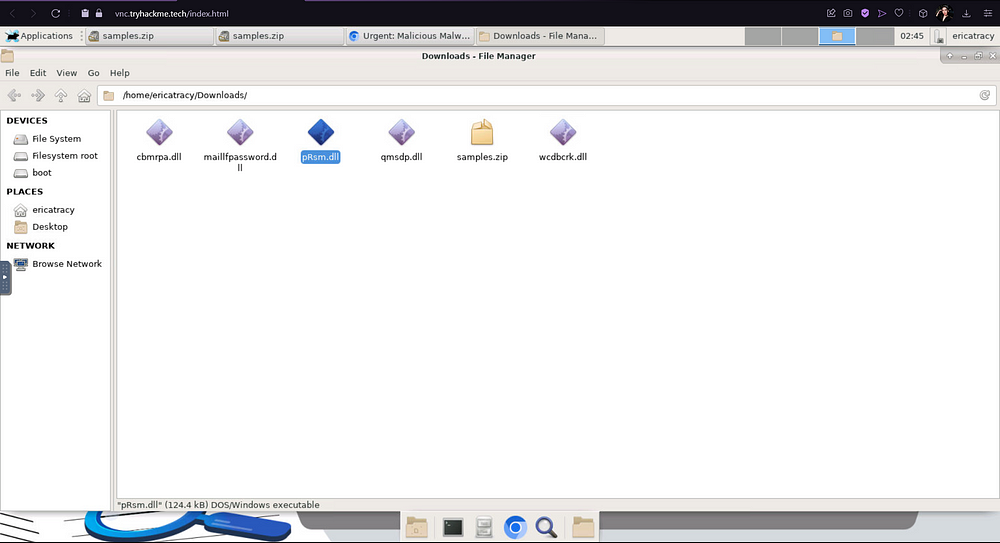
Let’s open up our Terminal so that we can read the SHA1 hash of the file “pRsm.dll”.
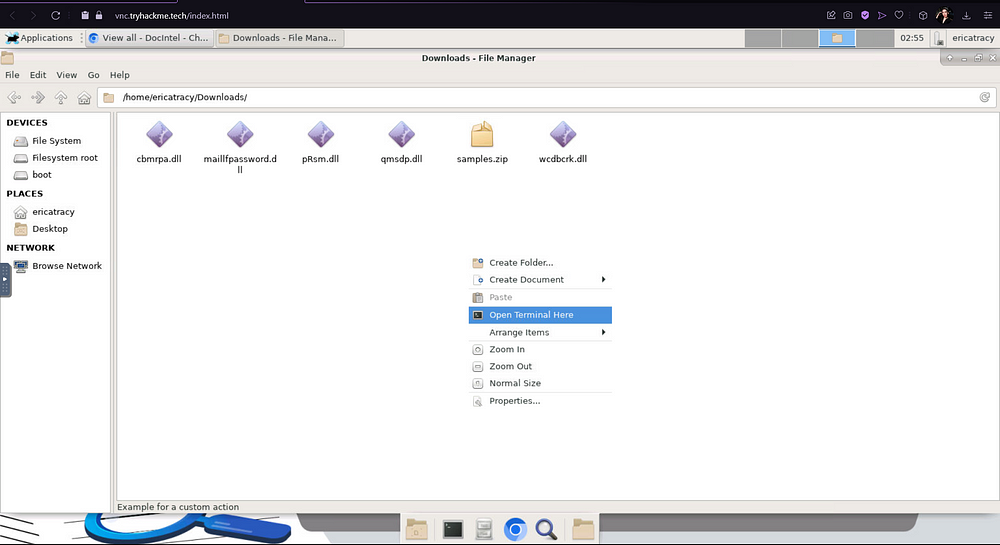
To read the hash of our file, we will make use of sha1sum. SHA1sum is a utility that computes and verifies SHA-1 cryptographic hash values. The primary reason you can use SHA1sum to read the hash of our.dll file — or any file, for that matter — is due to its ability to process binary data and generate a fixed-size hash value, which is a representation of the file’s content.
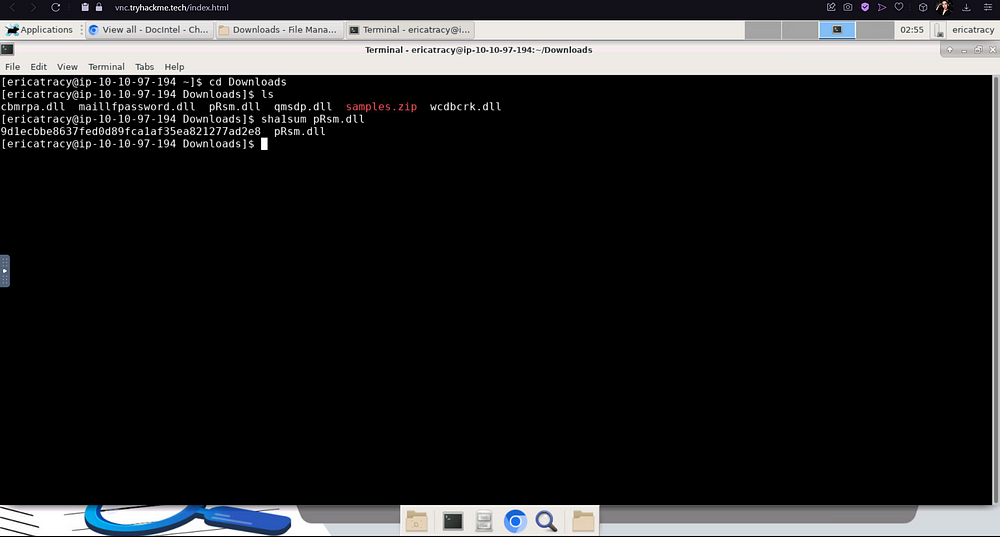
3. Which malware framework utilizes these DLLs as add-on modules?
For this question, I turned to good old Google to see if I could find any information on “pRsm.dll” and the framework used.
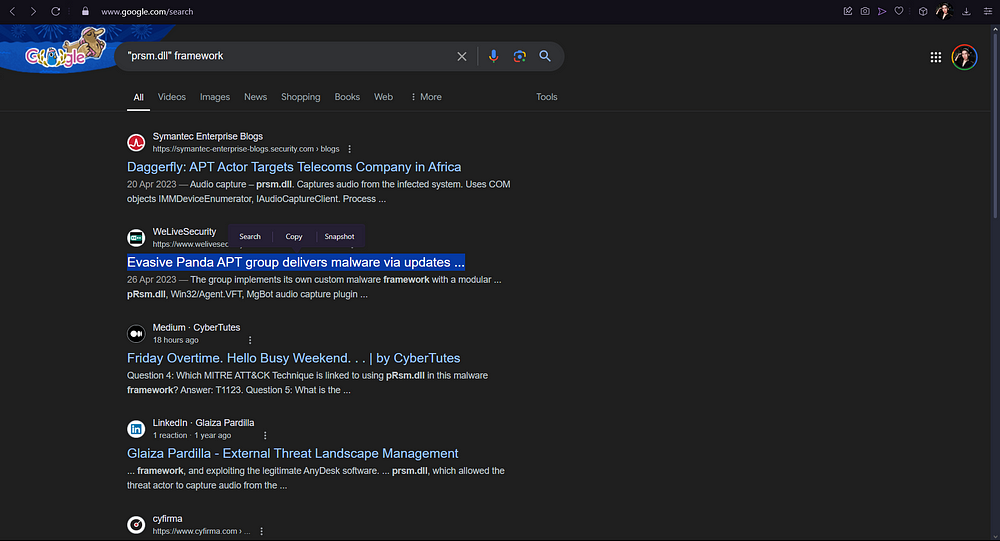
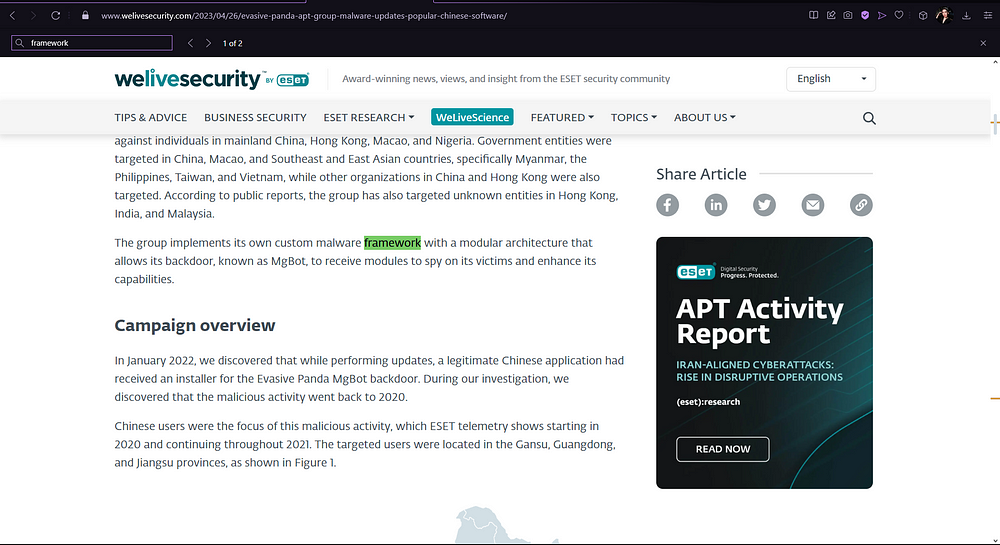
I saw it flagged in this article, so I clicked on it and searched for “framework”. Without too much effort, you can find the answer in the second paragraph of the article.

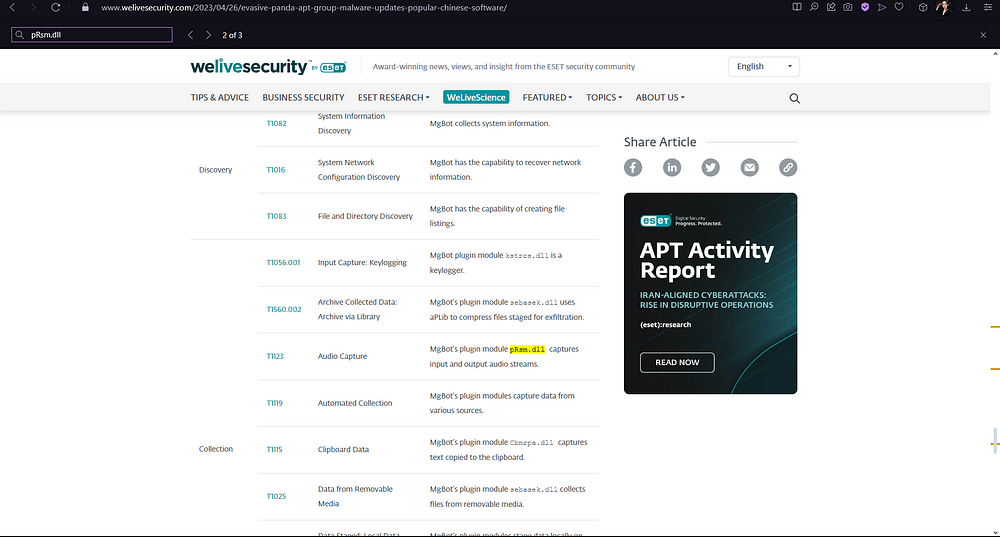
4. Which MITRE ATT&CK Technique is linked to using pRsm.dll in this malware framework?
For this, we need to search “pRsm.dll” and look out for a Technique ID (TXXXX), since we see that the answer required has 5 characters.
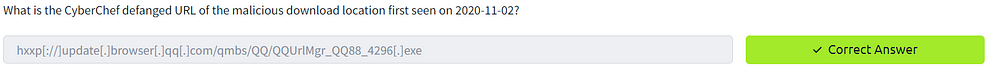
5. What is the CyberChef defanged URL of the malicious download location first seen on 2020–11–02?
Now we need to find a URL connected to 2020–11–02, and defang it on CyberChef. Defanging URLs and IPs is a critical practice for safely sharing potentially harmful links, and CyberChef simplifies this process, especially when handling large volumes of data. This practice is essential when sharing resources that might contain harmful data.
Let’s head back to our article, and search for our date “2020–11–02”. We can see that it lands on a result that has a URL attached to it.
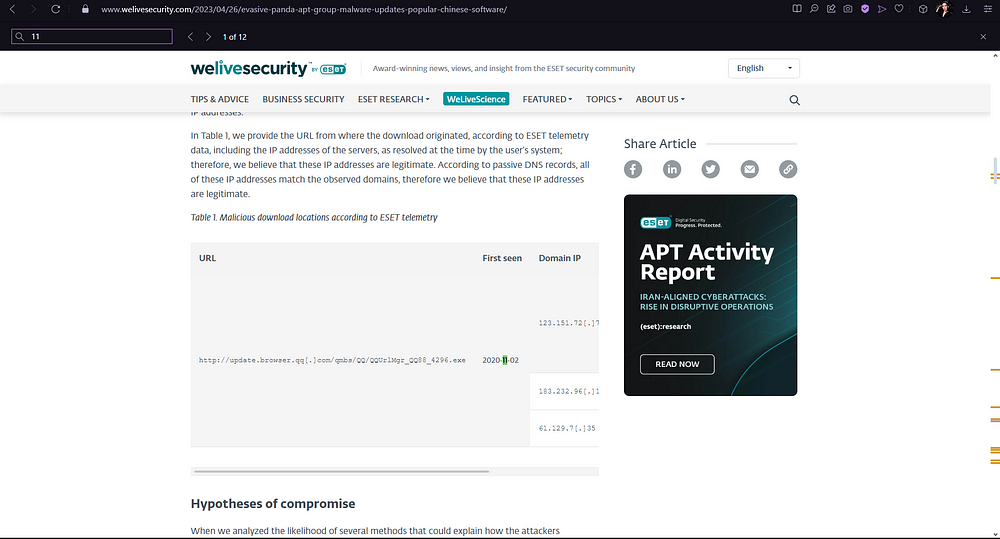
Copy and paste this URL into the CyberChef input, and add the recipe “Defang URL”. The output will give you your answer.
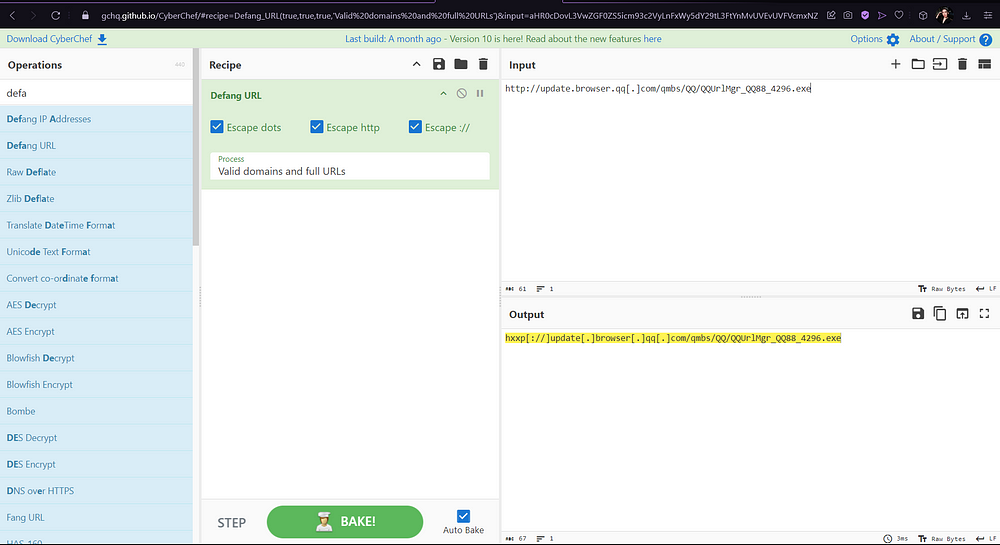
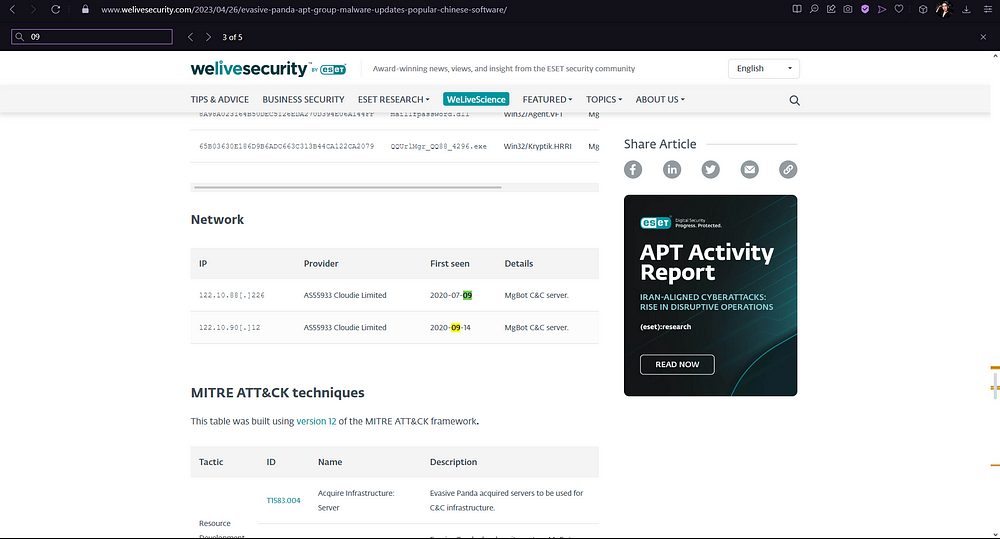
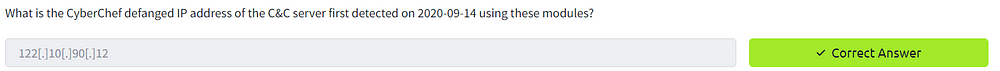
6. What is the CyberChef defanged IP address of the C&C server first detected on 2020–09–14 using these modules?
For this, we also need to search our date on the article we sourced previously. The IP should correlate to the date first seen on “2020–09–14”.
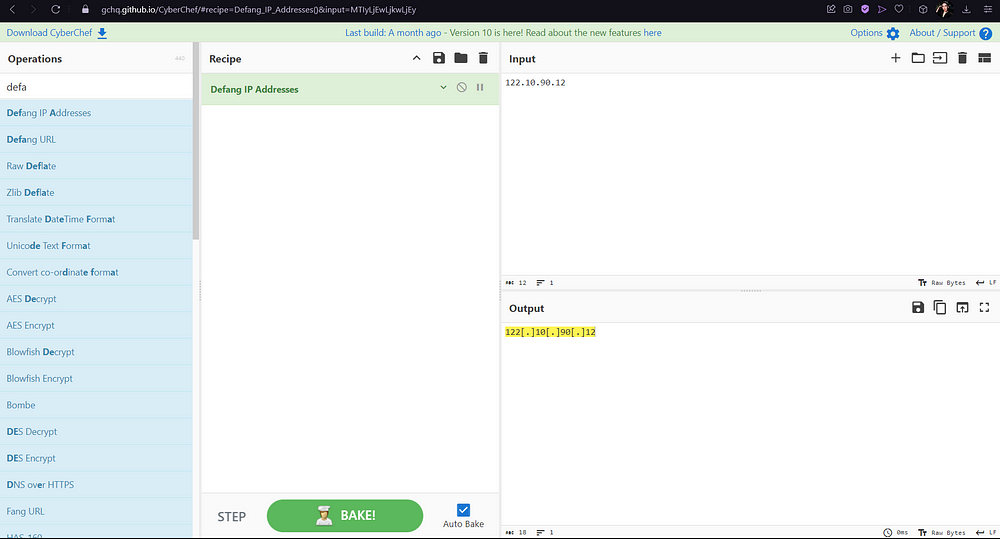
Let’s copy this IP into the CyberChef input (remove the brackets because it should be pure data). Change the recipe to “Defang IP”. The result should be your answer.
7. What is the SHA1 hash of the spyagent family spyware hosted on the same IP targeting Android devices on November 16, 2022?
Unfortunately, we cannot find the SHA1 hash of the malware on the article that we’ve been using. But, luckily for us, we can make use of a service that analyzes files and URLs for viruses, worms, trojans, and other kinds of malicious content detected by antivirus engines and website scanners.
Can you think of a service that can do all of the above? Well, we can use VirusTotal. VirusTotal will allow us to search for the malware connected to the IP address, and analyze all of its characteristics. So let’s open up the site and search for any data connected to our “fanged” IP address.
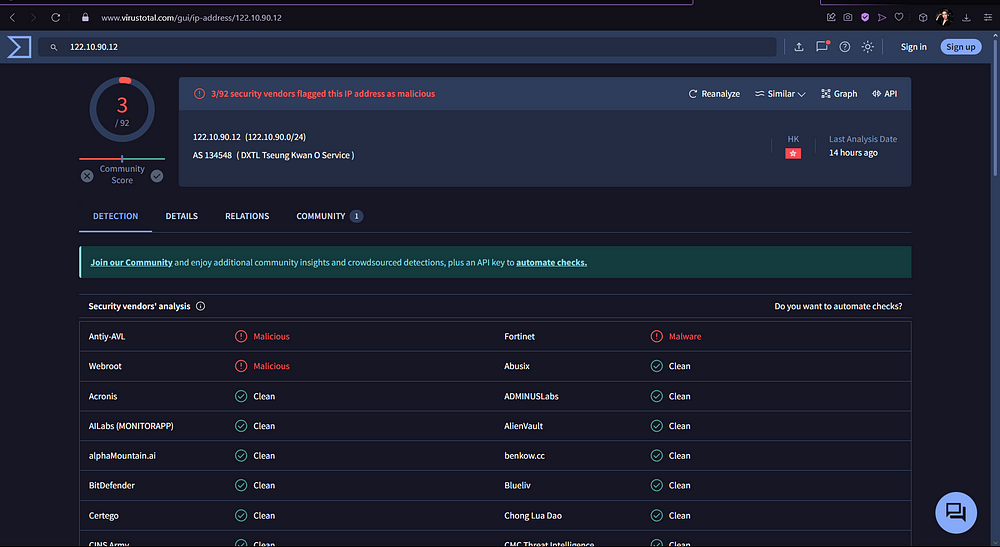
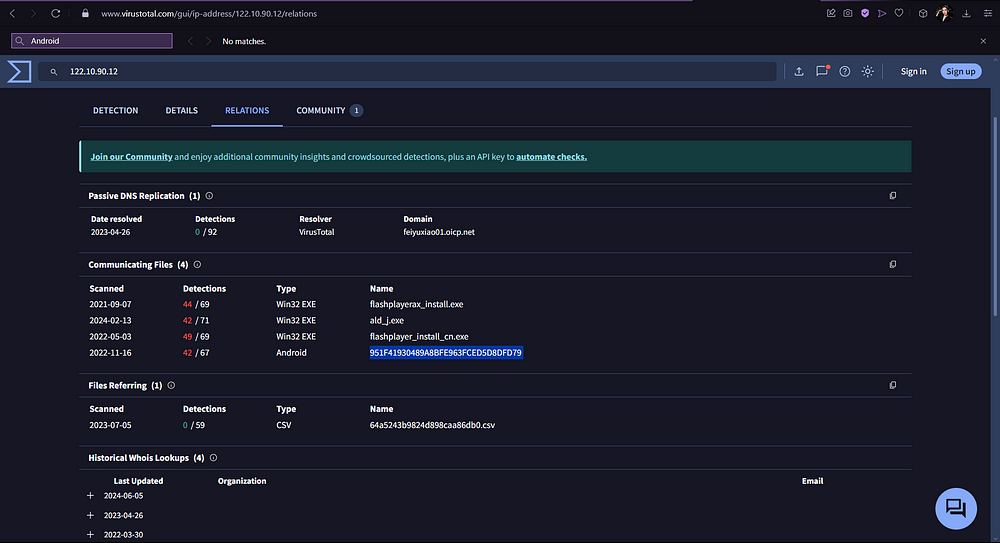
Click on the “Relations” panel to see where this IP has been flagged. This panel helps us explore the relationships between various indicators of compromise (IoCs) such as files, URLs, domains, and IP addresses.
You will see that an IoC from this IP was picked up on Android on the date of 2022–11–16. This is the name of our spyagent family spyware.
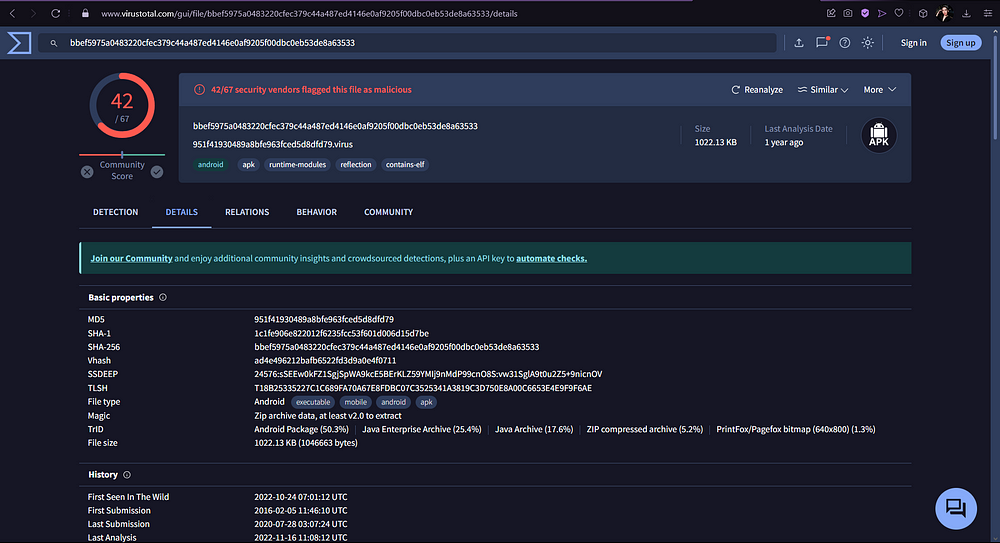
Now all we need is the hash value of this spyagent. Copy the name and search it. If we click on the “Details” of our result, we will see that there is a SHA1 hash value, which is what we need for our final flag!
Conclusion
Congratulations on completing the room. I hope you found the writeup valuable, and that you could follow along with ease.
Now, onwards to the next room! 😊
Subscribe to my newsletter
Read articles from Christine Coomans directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Christine Coomans
Christine Coomans
I'm just a developer who loves making cool applications, games, and tools using a variety of technologies and engines. When I'm not busy coding, I enjoy sharing my knowledge of development and other tech topics that I find interesting through written content and YouTube videos.