Strengthen Your Selenium Tests with Pynt Security Scans
 Yogendra Porwal
Yogendra PorwalSelenium automates web browser interactions, making it a valuable tool for functional testing. However, it doesn't inherently assess security risks (or web application security vulnerabilities). Here's where Pynt comes in! Pynt, a dynamic API security testing solution, scans for vulnerabilities as your Selenium tests interact with your application. This integration empowers you to identify and address security issues early in the development lifecycle.
Note: If you want to integrate Pynt with your api test automation, you can refer to EMPOWERING API SECURITY TESTING WITH PYNT AND PYTEST
Pynt and its Features
Pynt is a user-friendly API security testing tool designed for developers and testers. It offers a comprehensive suite of features to identify vulnerabilities such as SQL injection, Cross-Site Scripting (XSS), and Broken Authentication. Pynt's key features include:
Dynamic Analysis: Pynt analyzes traffic during runtime, mimicking real user interactions. This allows for a more thorough assessment compared to static analysis tools.
Easy Integration: Pynt security scan integrates seamlessly with various development environments and testing frameworks.
Detailed Reports: Pynt generates comprehensive reports highlighting vulnerabilities, their severity levels, and potential remediation steps.
Prerequisites:
Pynt Installation: Ensure you have Pynt installed on your development machine. You can follow the official installation guide based on your operating system: install-pynt
Docker Installation: Make sure docker is installed and running on your system. As Pynt use docker to run their scanning mechanism on api traffic. To install Docker, you can follow the guide: here
Step-by-Step Guide
1. Running Pynt Listen:
Start Pynt proxy by using below command .
Bash
pynt listen --captured-domains <domains to scan>
We can use different options as well, that can help to run your test on proxy smoothly.
Bash
--port - Set the port pynt will listen to (DEFAULT: 5001)
--ca-path - The path to the CA file in PEM format
--proxy-port - Set the port proxied traffic should be routed to (DEFAULT: 6666)
--report - If present will save the generated report in this path.
--insecure - use when target uses self signed certificates
--host-ca - path to the CA file in PEM format to enable SSL certificate verification for pynt when running through a VPN.
--return-error - 'all-findings' (warnings, or errors), 'errors-only', 'never' (default),
When Pynt proxy is started successfully, you will be able to see below logs.
Bash
API Security testing autopilot
Pynt CLI version 0.1.90
Pulling latest docker
Docker pull done
Launching Server...
Pynt docker is ready
Listening to traffic on port: 6666
Will scan APIs that belong to '['tutorialsninja.com']' domains only
Press Enter to stop recording traffic and run security scan...
Now that Pynt proxy is started and listening on port 6666, lets configure selenium to redirect its traffic through this proxy.
2. Configuring Selenium to Redirect Traffic to Pynt Proxy:
To integrate selenium tests with pynt security scans, let’s first create a basic test that interacts with a web application and redirect its traffic through Pynt proxy. For this we need to follow below steps before driver intialization:
Create an instance of
org.openqa.selenium.ProxySet http and ssl proxy to Pynt proxy url.(
localhost:6666)Update ChromeOptions to use this proxy instance.
Below is the code snippet to setup proxy in selenium and initialise WebDriver with it.
JAVA with Selenium WebDriver:
Java
// Set WebDriver proxy
String proxyUrl = "localhost:6666";
Proxy proxy = new Proxy();
proxy.setHttpProxy(proxyUrl);
proxy.setSslProxy(proxyUrl);
//Configure ChromeOption
ChromeOptions co = new ChromeOptions();
co.setAcceptInsecureCerts(true);
co.setProxy(proxy);
// Initialize WebDriver (replace with your desired browser with ChromeOptions)
WebDriver driver = new ChromeDriver(co);
Other WebDriver Languages:Similar configurations can be achieved with other WebDriver languages by setting the appropriate proxy settings within their respective libraries.
Now that Proxy is configured in selenium, we need to create a basic sample test to try it out.
You can use a sample test from github.
3. Run Sample Code:
Now that integration of selenium tests with pynt security scans is done, lets execute your Selenium test scripts while Pynt is listening. Pynt will intercept the network requests triggered by your tests and capture them.
4. Generate Report:
Once your tests complete, go back to the terminal where we started Pynt Proxy.
If you pay attention the last line in console says.
Bash
Press Enter to stop recording traffic and run security scan...
So lets press enter, and pynt will start analysing the captured API requests.
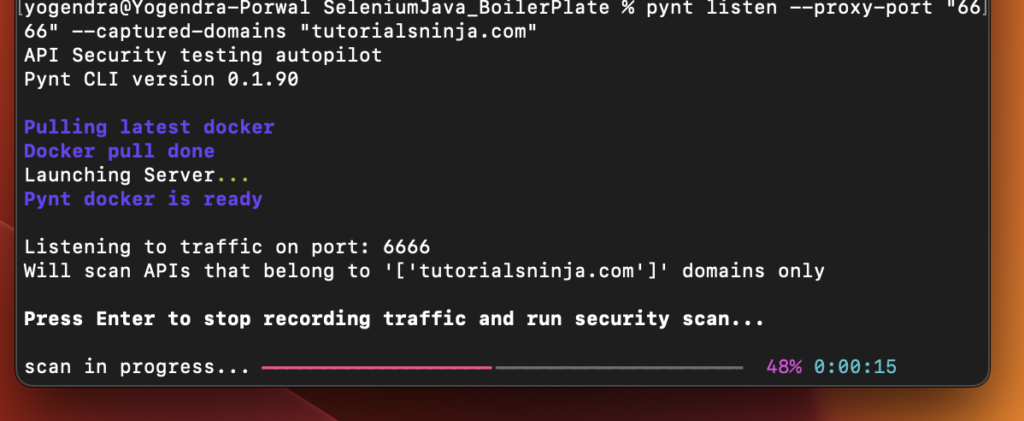
As soon as scan is done, Pynt will show the report summary in console.
Bash
Functional Tests
┏━━━━━━━━━━━┳━━━━━━━━━━┓
┃ Endpoints ┃ Requests ┃
┡━━━━━━━━━━━╇━━━━━━━━━━┩
│ 3 │ 9 │
└───────────┴──────────┘
Security Tests
┏━━━━━━━━┳━━━━━━━━━━┳━━━━━━━━┳━━━━━━━━━━━━━┓
┃ Errors ┃ Warnings ┃ Passed ┃ Did Not Run ┃
┡━━━━━━━━╇━━━━━━━━━━╇━━━━━━━━╇━━━━━━━━━━━━━┩
│ 0 │ 11 │ 22 │ 1 │
└────────┴──────────┴────────┴─────────────┘
Pynt will also automatically open a detailed html report on your default browser as well.
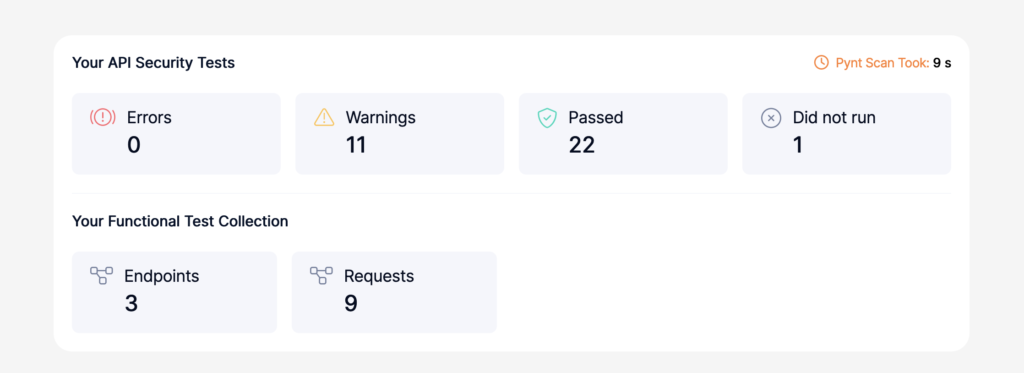
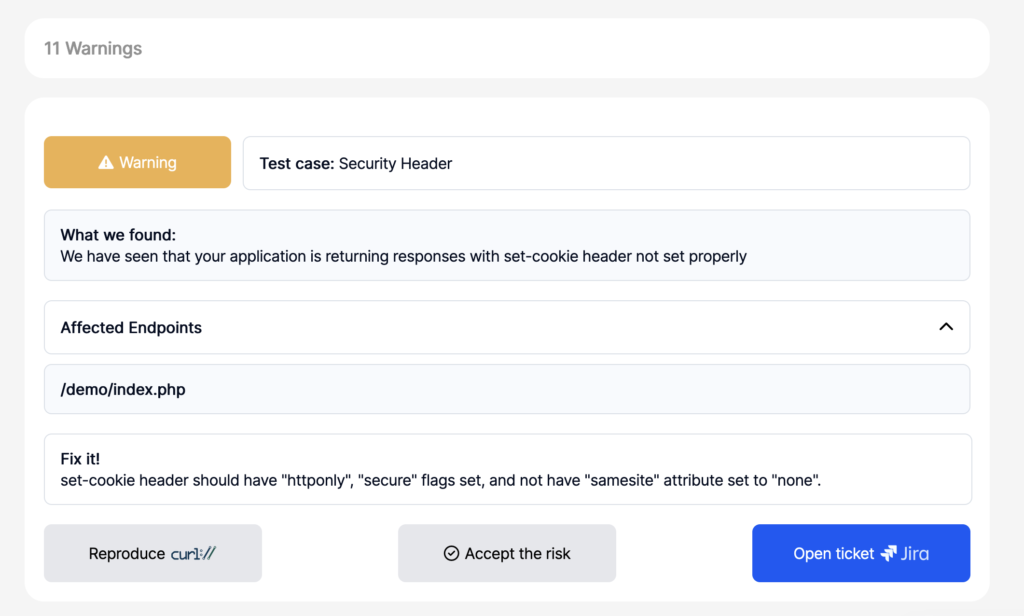
Trouble shooting:
1. Docker is unavailable (mac specific issue)
If you are using mac, You might face below issue even if the docker is up and running.
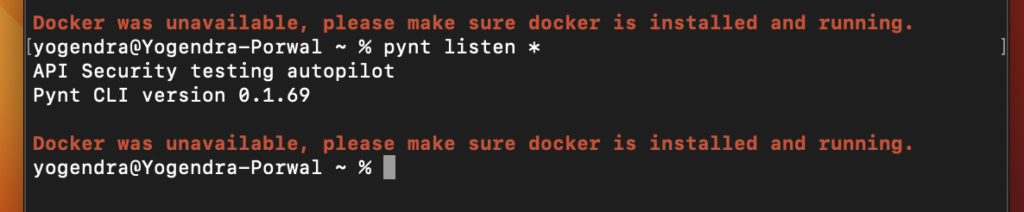
You need to provide execute permission to your docker application, you can do that with below commands.
Bash
sudo chown -R $(id -u):$(id -g) /Users/yogendra/.docker
#or
sudo ln -s "$HOME/.docker/run/docker.sock" /var/run/docker.sock
2. Docker is running but having credential issue:
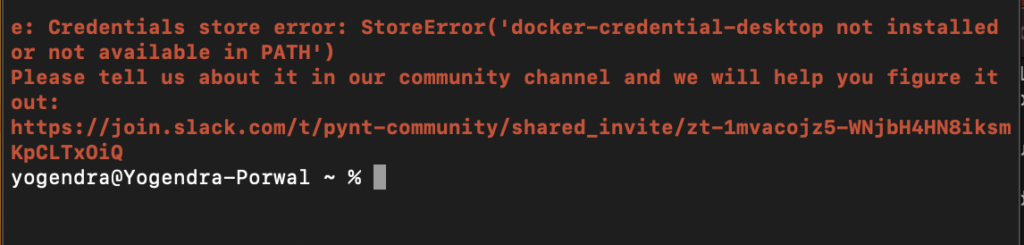
You can fix above by updating $HOME/.docker/config.json. You need to change the key name from credsStore to credStore. Your config should be like below.
JSON
{
"auths": {},
"credStore": "desktop",
"currentContext": "desktop-linux",
"plugins": {
"debug": {
"hooks": "exec"
},
"scout": {
"hooks": "pull,buildx build"
}
},
"features": {
"hooks": "true"
}
}
3. Issue with insecure certificate:
Most of the sites , does not allow insecure connection, so you might need to install certificate to make your selenium tests work through proxy. You can find pynt proxy certificate in ~/.pynt/cert.
It can be done in 2 ways:
Provide path to certificate(.pem formate) in arguement --ca-path while starting pynt proxy.
Install this certificate in browser.
For mac user if you are using chrome, you might need to install the certificate in system's keychain access directly.
Conclusion
Integrating Pynt with your Selenium tests offers a powerful way to enhance your application's security posture. By identifying vulnerabilities early on, you can prevent potential security breaches and build more robust web applications. Although pynt proxy need to be started and stopped manually but this can also be automated with ProcessBuilder in java but that is for another article :P. So, go ahead, strengthen your Selenium tests with Pynt and ensure the security of your web applications.
You can also checkout out other security article at Security Testing Archive.
If you are looking for a comparison between Zap and Pynt, please refer to detailed blog : Burp Suite vs. ZAP: Features, Key Differences & Limitations
Subscribe to my newsletter
Read articles from Yogendra Porwal directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Yogendra Porwal
Yogendra Porwal
As an experienced Test Automation Lead, I bring over 9 years of expertise in Quality Assurance across diverse software domains. With technical proficiency in multiple verticals of testing, including automation, functional, performance and security testing among others, my focus is on applying this knowledge to enhance the overall quality assurance process. I also like to go on long journeys with my bike , do sketching in my free time and have keen interest in video games.