Implementing VPC Service Controls with Terraform on GCP
 Tanishka Marrott
Tanishka Marrott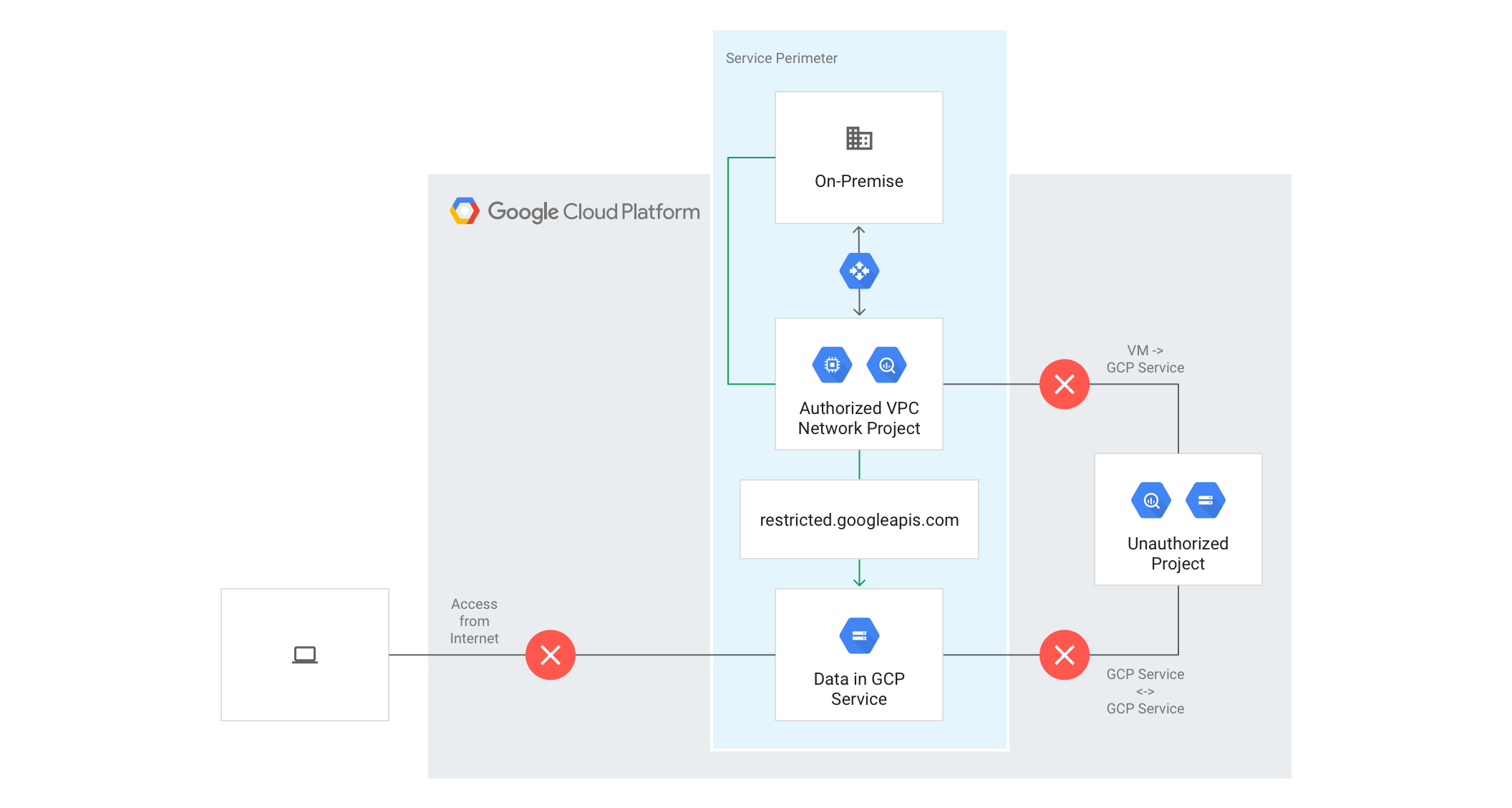
In the rapidly evolving landscape of cloud computing, securing your resources and data is paramount. Google Cloud Platform - GCP offers VPC Service Controls as a robust security feature to help mitigate data exfiltration risks. In this article, we'll explore what VPC Service Controls are, their benefits, and how to implement them using Terraform.
Introduction to VPC Service Controls
VPC Service Controls is a security feature in GCP designed to provide additional security for your resources and data by defining a security perimeter around GCP services. This helps in controlling the movement of data between services inside and outside the defined perimeter, thereby mitigating data exfiltration risks.
Key Concepts
Security Perimeter:
VPC Service Controls allows you to create a security perimeter around your GCP resources, restricting access to only those resources within the defined boundary.
This ensures that sensitive data cannot be moved to or accessed from outside the perimeter, enhancing data protection.
Access Policies:
These are fine-grained access control policies for your resources.
You can restrict access based on attributes such as the origin of the request, ensuring only trusted sources can interact with your resources.
Prevent Data Exfiltration:
By restricting which resources can communicate with each other and limiting access to the internet, VPC Service Controls helps prevent unauthorized data movement.
Ideal for scenarios where strict data governance and compliance requirements are needed.
Integration with IAM:
VPC Service Controls work in conjunction with Identity and Access Management (IAM) to enforce security policies.
This ensures that even if a user has IAM permissions, they cannot access resources outside the security perimeter without proper authorization.
Service Perimeters and Access Levels:
Service Perimeters: Define the boundary around GCP resources (e.g., Cloud Storage buckets, BigQuery datasets).
Access Levels: Specify the conditions under which requests are allowed through the perimeter (e.g., requests from specific IP ranges).
Practical Implementation Using Terraform
To implement VPC Service Controls with Terraform, follow these steps:
Prerequisites
Terraform installed on your machine
GCP account with necessary permissions
Setting Up the Environment
First, create a new GitHub repository to store your Terraform scripts. Name it something like terraform-vpc-service-controls and initialize it with a README file.
Directory Structure
Create the following directory structure in your repository:
terraform-vpc-service-controls/
│
├── main.tf
├── variables.tf
├── outputs.tf
└── README.md
Terraform Scripts
provider "google" {
project = var.project_id
region = var.region
}
resource "google_access_context_manager_access_policy" "access_policy" {
parent = "organizations/${var.organization_id}"
title = var.policy_name
}
resource "google_access_context_manager_service_perimeter" "service_perimeter" {
parent = google_access_context_manager_access_policy.access_policy.name
name = var.service_perimeter_name
perimeter_type = "PERIMETER_TYPE_REGULAR"
status {
resources = var.resources
restricted_services = var.restricted_services
ingress_policies {
ingress_from {
sources {
access_level = google_access_context_manager_access_level.access_level.name
}
}
ingress_to {
operations {
service_name = "all"
}
}
}
egress_policies {
egress_to {
operations {
service_name = "all"
}
}
}
}
}
resource "google_access_context_manager_access_level" "access_level" {
parent = google_access_context_manager_access_policy.access_policy.name
name = var.access_level_name
basic {
conditions {
ip_subnetworks = var.ip_subnetworks
}
}
}
variable "project_id" {
description = "The ID of the GCP project"
type = string
}
variable "region" {
description = "The region of the GCP project"
type = string
}
variable "organization_id" {
description = "The ID of the GCP organization"
type = string
}
variable "policy_name" {
description = "The name of the access policy"
type = string
}
variable "service_perimeter_name" {
description = "The name of the service perimeter"
type = string
}
variable "resources" {
description = "The resources to be included in the service perimeter"
type = list(string)
}
variable "restricted_services" {
description = "The services to be restricted within the perimeter"
type = list(string)
}
variable "access_level_name" {
description = "The name of the access level"
type = string
}
variable "ip_subnetworks" {
description = "The IP subnetworks to be included in the access level"
type = list(string)
}
output "access_policy_name" {
value = google_access_context_manager_access_policy.access_policy.name
}
output "service_perimeter_name" {
value = google_access_context_manager_service_perimeter.service_perimeter.name
}
output "access_level_name" {
value = google_access_context_manager_access_level.access_level.name
}
Applying the Terraform Scripts
Clone the Repository:
git clone https://github.com/your-username/terraform-vpc-service-controls.git cd terraform-vpc-service-controlsInitialize Terraform:
terraform initUpdate
variables.tfwith your project-specific values.Apply the Terraform scripts:
terraform apply
Cleanup
To remove the resources created by Terraform, run:
terraform destroy
Conclusion
Implementing VPC Service Controls with Terraform on GCP enhances your cloud security posture by creating a defined security perimeter around your resources. This not only prevents unauthorized data exfiltration but also ensures compliance with stringent data governance policies. By following the steps outlined in this article, you can efficiently set up and manage VPC Service Controls in your GCP environment.
Feel free to check out the GitHub repository for the complete Terraform scripts and additional resources.
Subscribe to my newsletter
Read articles from Tanishka Marrott directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Tanishka Marrott
Tanishka Marrott
I'm a results-oriented cloud architect passionate about designing resilient cloud solutions. I specialize in building scalable architectures that meet business needs and are agile. With a strong focus on scalability, performance, and security, I ensure solutions are adaptable. My DevSecOps foundation allows me to embed security into CI/CD pipelines, optimizing deployments for security and efficiency. At Quantiphi, I led security initiatives, boosting compliance from 65% to 90%. Expertise in data engineering, system design, serverless solutions, and real-time data analytics drives my enthusiasm for transforming ideas into impactful solutions. I'm dedicated to refining cloud infrastructures and continuously improving designs. If our goals align, feel free to message me. I'd be happy to connect!