What is Secure Shell
 Paminda Kalpa Wickramasinghe
Paminda Kalpa Wickramasinghe
Secure Shell aka SSH is one of the most essential network protocols for Cloud and DevOps to effectively manage and automate remote access to servers, containers, and cloud infrastructure, as well as to securely transfer files, execute commands, and monitor system performance.
In this post, Let's take a brief look how it works, its advantages and how it can be applied in real world scenarios.
What is Secure Shell
Let's try to understand this using a short incident about friends & a confidential letter.
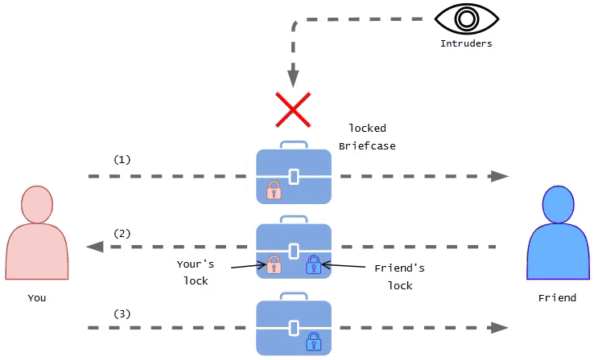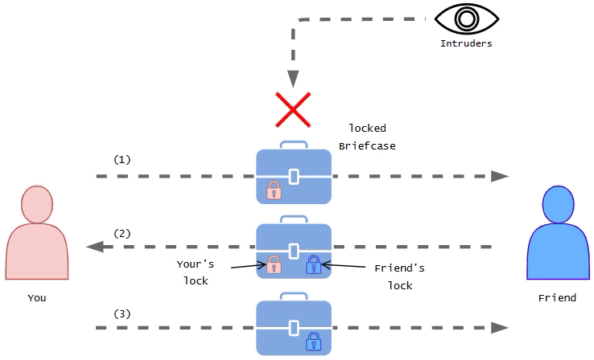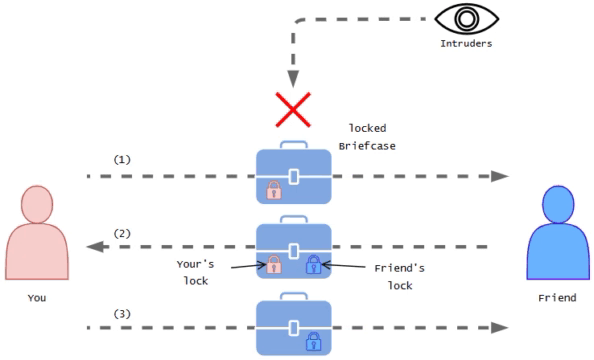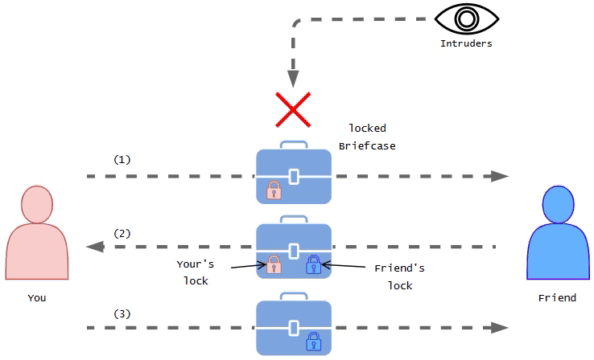
Imagine you have a friend who lives in a different city and you want to send them a confidential letter.
You don't want anyone else to read it. So you using a special container like a briefcase which you can lock using the special key and send this letter confidentially.
At this moment you choose to deliver the locked briefcase to your friend via a reliable messenger service. After receiving the briefcase your friend doesn't have your key to open it, So they add their special key lock for it and send it back to you. Then you have to unlock it and send it back to your friend again. Then the friend unlocks their lock and they can view the letter.
This way even if it is being watched the briefcase remains locked the entire time it's in transit.
In this scenario,
You represents as user or developer
Yours and friends secret special lock keys represents as SSH key pairs
Trusted messenger represents as SSH tunnel
Confidential letter represents as command or file
Friend represents as remote computer or server
Lets see how secure shell works on real world,
Phase 1: Connection Establishment and Key Exchange
First, The user initiates a SSH connection by sending a request to the server, which includes the user's public key.
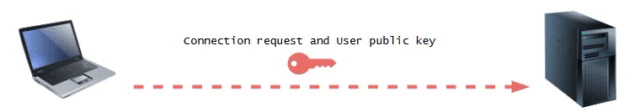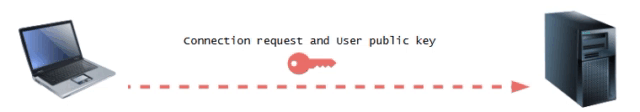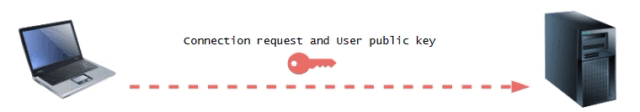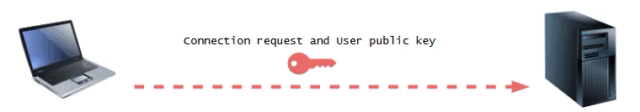
Phase 2 : Key Verification
On receiving the user's public key, the server sends a text to the user. The user then encrypts the text using the private key and sends it to the server.
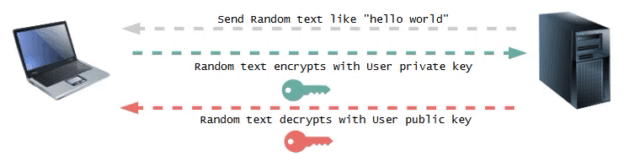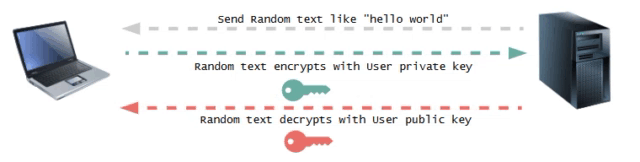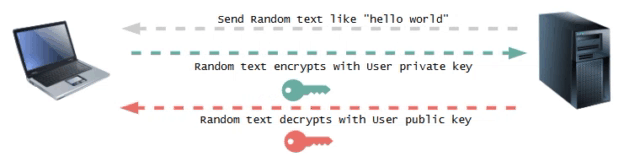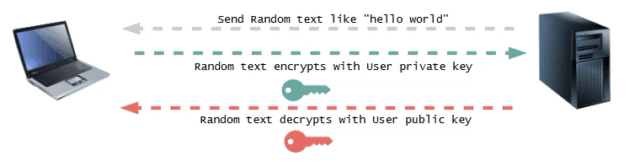
This is an asymmetric key encryption process, where the server uses the user's public key to decrypt the text received. If the decrypted text matches the original text sent by the server, the server verifies that it has the correct public key and notifies the user of the successful authentication.
Phase 3 : Data Transfer
After the connection is authenticated, the data transfer process begins.
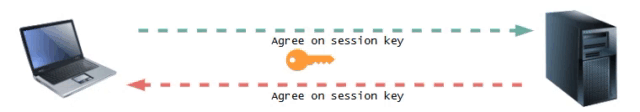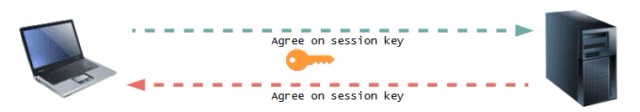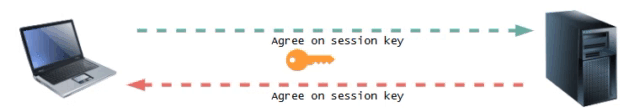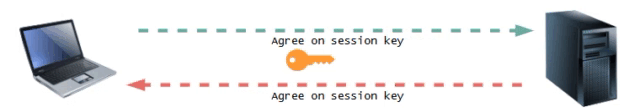
During this process, the data is encrypted using symmetric encryption. The client and server share a single encryption key that is unique to a specific session. This means that all data sent during that session is encrypted with this key, ensuring that even if someone intercepts the data, they will not be able to read it without possessing the correct key.
Why Secure Shell
When the internet was new, some programs like Telnet and FTP didn't care about keeping information safe. They sent passwords and other important info in plain text, making it easy for hackers to read.
In 1995, a password sniffing attack at the Helsinki University of Technology showed just how vulnerable internet communications were. Tatu Ylönen, a developer created a new way to send information called Secure Shell. This way makes sure that passwords and important info are hidden and can't be read by hackers. This was a big help for users who needed to send information safely over the internet.
Advantages of using Secure Shell
When it comes to managing your remote computer or server, using Secure Shell instead of Telnet or FTP can make a big difference in terms of security. Here are some key advantages of using Secure Shell
Encryption : SSH encrypts data, keeping your login credentials and sensitive information safe.
Authentication : SSH uses a unique key pair system, providing an extra layer of protection compared to traditional FTP passwords.
Data Protection : SSH ensures that data remains unchanged during transfer, preventing tampering and corruption.
Secure Tunneling : SSH allows you to securely forward ports, enabling you to access other protocols safely.
Easy Use : Modern SFTP clients have intuitive interfaces, making it easy to switch from FTP software.
So, it seems like you're ending this post and will be diving deeper into SSH commands and connecting to a server using SSH from another blog post.
Thank you for reading my blog post! Your positive feedback inspires me to explore more about technology and innovation.
Subscribe to my newsletter
Read articles from Paminda Kalpa Wickramasinghe directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Paminda Kalpa Wickramasinghe
Paminda Kalpa Wickramasinghe
Hi folks ✌, I’m Paminda Kalpa Wickramasinghe from the beautiful city Galle, a charming coastal city in southern Sri Lanka 🌊. I hold a Bachelor’s degree in Information Technology from the University of Colombo School of Computing. With experience as an IT support professional in server management, backup solutions, and LAN administration, I'm passionate about transitioning to in demand fields like DevOps, Cloud Computing, Platform Engineering, Site Reliability Engineering and emerging technologies.