Phishing Mail Analysis: Uncovering Deceptive Emails
 Harshal Shah
Harshal Shah
Phishing attacks are a prevalent cyber threat that targets individuals by tricking them into divulging personal information. This is typically achieved through deceptive emails that prompt recipients to click on malicious links or download harmful files. Phishing falls into the "Delivery" phase of the Cyber Kill Chain model, where attackers deliver malicious content to their targets.Phishing attacks have become a pervasive threat, with cybercriminals employing increasingly sophisticated tactics to deceive unsuspecting users. Developing a keen eye for identifying and analyzing phishing emails is crucial for safeguarding personal and organizational data. This comprehensive guide will equip you with the knowledge and tools to dissect these malicious messages.
Understanding the Anatomy of a Phishing Email
Before diving into the analysis process, it's essential to comprehend the key components of a phishing email:
Sender Information: The displayed name and email address of the sender.
Subject Line: The subject of the email, often designed to entice or alarm recipients.
Email Body: The content of the email, including text, images, and embedded links.
Attachments: Files attached to the email, which may contain malicious code.
Email Header: Technical information about the email's journey, including sender details, servers involved, and timestamps.
Identifying Spoofed Emails
Email Spoofing is a technique where attackers falsify the sender's information to make the email appear as if it came from a legitimate source. While protocols like SPF, DKIM, and DMARC can help mitigate spoofing, they are not foolproof and are not always implemented.
How to Identify Spoofed Emails Manually
Check the SMTP Address: Use tools like Mxtoolbox to verify the domain's SPF, DKIM, DMARC, and MX records.
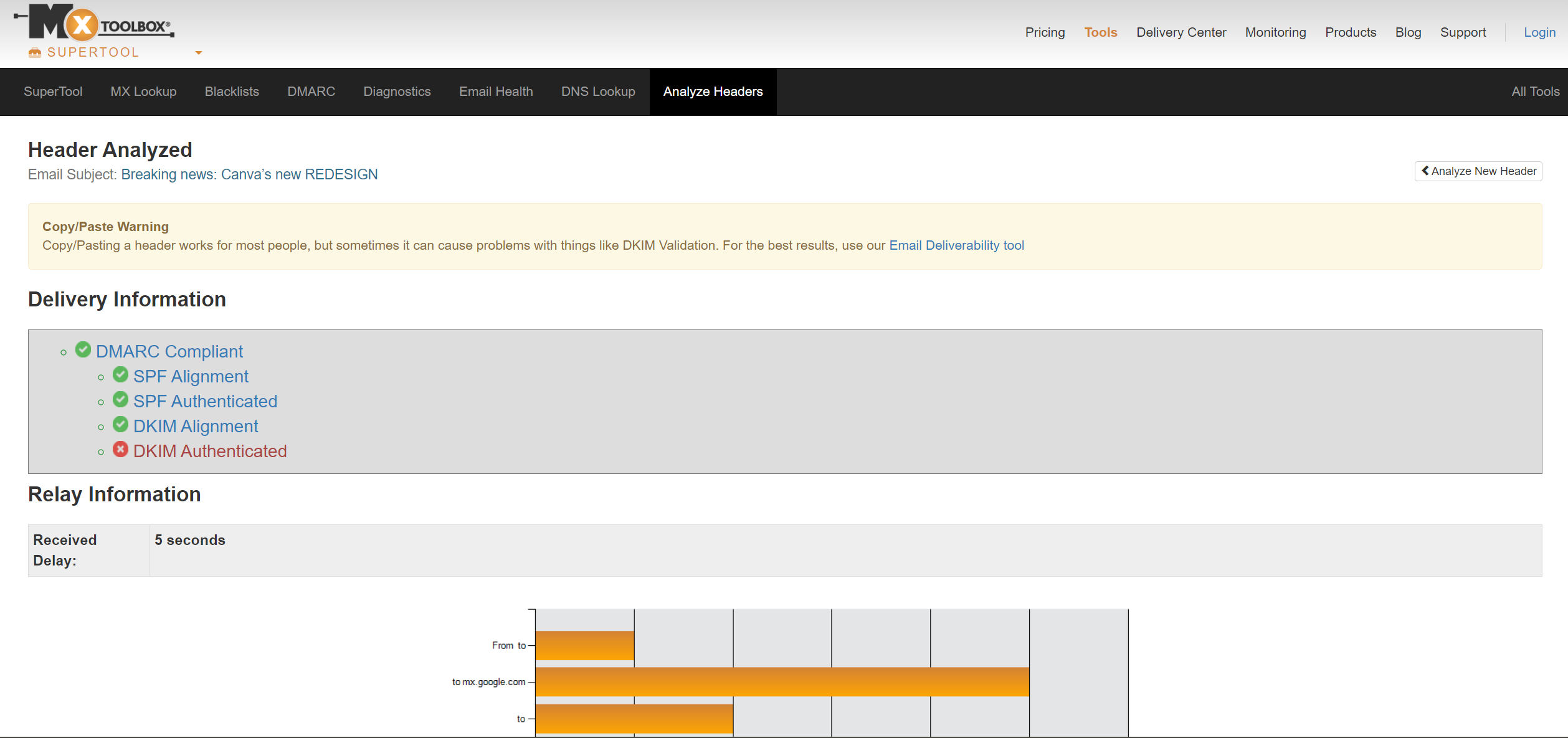
Inspect Whois Records: Verify if the SMTP IP address belongs to the purported institution.
Even if the sender's address is not spoofed, it does not guarantee the email's safety. Malicious emails can originate from compromised legitimate accounts.
Understanding and Reading Email Headers
Email headers contain critical information about the email's journey and authenticity. Key fields include:
From: The sender's name and email address.
To: The recipient's details, including CC and BCC.
Date: The timestamp of when the email was sent.
Subject: The topic of the email.
Return-Path: The address to which replies are sent.
Domain Key and DKIM Signatures: Authenticate the email.
Message-ID: A unique identifier for each email.
MIME-Version: Indicates the email's MIME version.
Received: Lists each mail server the email passed through.
X-Spam Status: Shows the spam score and classification of the email.
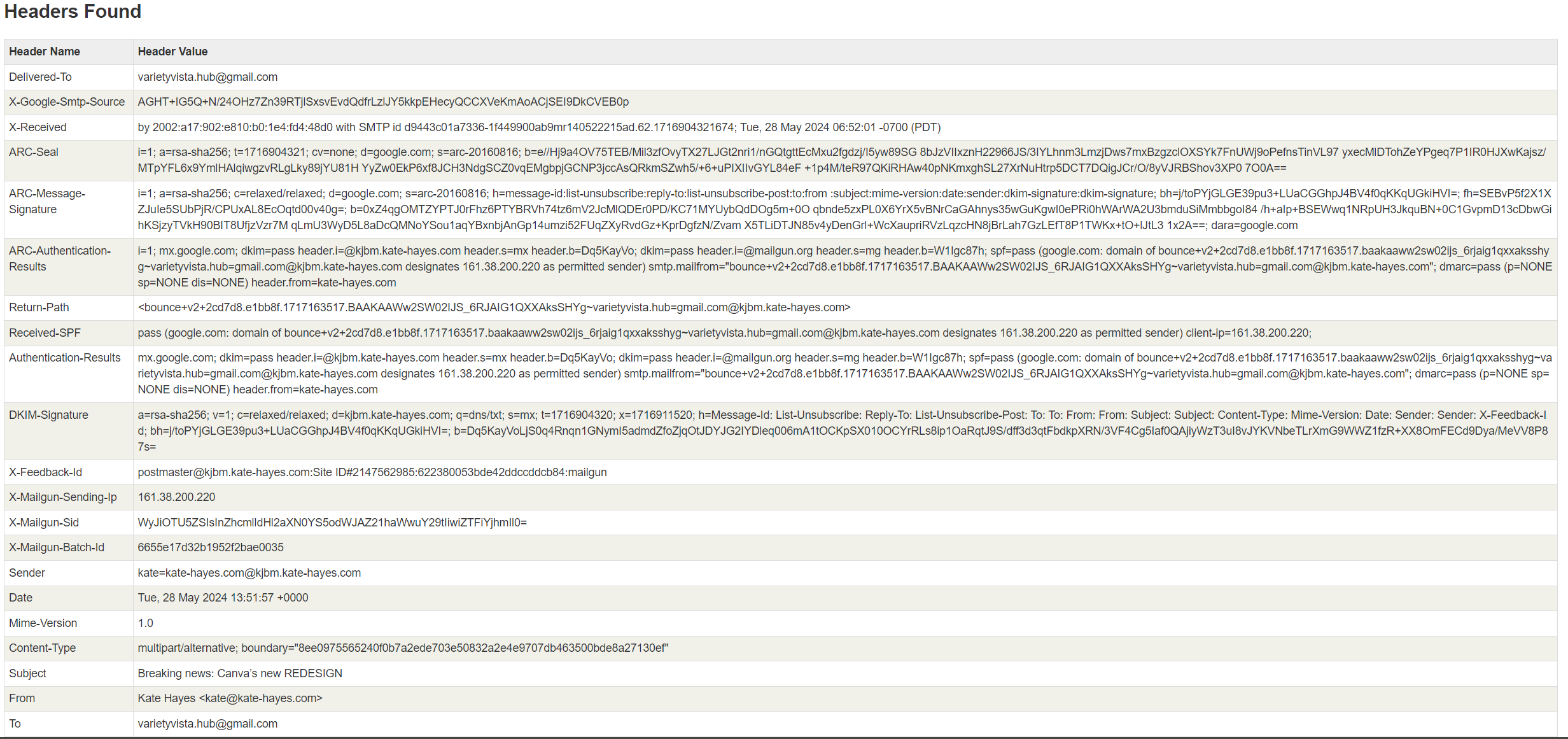
Accessing Email Headers
Gmail
Open the email in question.
Click on the three dots at the top right.
Select "Download message."
Open the downloaded ".eml" file with any notebook application.
Outlook
Open the email in question.
Go to File -> Info -> Properties -> Internet headers.
The Art of Phishing Email Analysis
Initial Inspection
Sender Verification: Scrutinize the sender's email address for inconsistencies or suspicious domains. Legitimate organizations typically use their official domain.
Subject Line Scrutiny: Be wary of subject lines that create a sense of urgency, fear, or excitement. Phishers often employ these tactics to manipulate recipients.
Content Analysis: Examine the email content for grammatical errors, inconsistencies, or suspicious requests for personal information. Legitimate organizations maintain professional communication standards.
Deep Dive into the Email Header
Access the Header: Most email clients allow you to view the full email header. This provides valuable insights into the email's origin.
Sender Authentication: Check for SPF, DKIM, and DMARC records, which are authentication protocols designed to verify the email's authenticity.
IP Address Verification: Compare the sender's IP address with the claimed domain. Discrepancies indicate potential spoofing.
Email Route Analysis: Examine the "Received" headers to trace the email's journey. Suspicious hops or relays might signal a phishing attempt.
Link and Attachment Inspection
Hover Over Links: Before clicking any links, hover over them to reveal the actual URL use browserling to do this. Legitimate links will match the displayed text.
URL Analysis: Use online tools to check the reputation of the domain associated with the link. Avoid clicking on shortened or suspicious URLs.
Attachment Caution: Exercise extreme caution when opening email attachments. Even familiar file types can be infected with malware.
Sandbox Analysis: If you must open an attachment, do so in a virtualized environment or sandbox to isolate potential threats.
Leveraging Online Tools and Services
VirusTotal: Submit suspicious files or URLs to VirusTotal for analysis by multiple antivirus engines.
Whois Lookup: Check the registration information of the domain associated with the email to identify potential red flags.
Phishing Reporting Sites: Report phishing emails to anti-phishing organizations to help protect others.
Email Reputation Services: Utilize email reputation services to assess the sender's trustworthiness.
Common Phishing Tactics and Indicators
Impersonation: Phishers often impersonate well-known brands or individuals to gain trust.
Urgency and Fear: Creating a sense of urgency or fear can induce hasty decisions.
Request for Personal Information: Phishing emails typically request sensitive data, such as passwords, credit card numbers, or social security numbers.
Malicious Attachments: These often contain malware that can infect your system.
Spoofed Links: Clicking on malicious links can redirect you to phishing websites.
Advanced Phishing Techniques
Spear Phishing: Targeted attacks directed at specific individuals or organizations.
Whaling: High-profile individuals, such as CEOs or executives, are the targets.
Business Email Compromise (BEC): Fraudsters impersonate company executives to defraud businesses.
Smishing: Phishing attacks delivered via SMS messages.
Vishing: Voice phishing attacks using phone calls.
Protecting Yourself from Phishing Attacks
Educate Yourself: Stay informed about the latest phishing tactics and trends.
Be Skeptical: Approach unexpected emails with caution.
Verify Information: Cross-check information with trusted sources before taking action.
Enable Two-Factor Authentication: Add an extra layer of security to your accounts.
Keep Software Updated: Ensure your operating system and applications are up-to-date with the latest security patches.
Conclusion
Phishing remains a significant cyber threat, but with careful analysis and the use of various tools and techniques, it is possible to uncover and mitigate these deceptive attacks. By understanding email headers, performing static and dynamic analysis, and being aware of additional phishing techniques, individuals and organizations can better protect themselves from falling victim to phishing schemes. Always remain vigilant and skeptical of unsolicited emails, especially those urging immediate action or offering too-good-to-be-true rewards.
Subscribe to my newsletter
Read articles from Harshal Shah directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Harshal Shah
Harshal Shah
Navigating the convergence of cybersecurity, DevOps, and cloud landscapes, I am a tech explorer on a mission. Armed with the prowess to secure digital frontiers, streamline operations through DevOps alchemy, and harness the power of the cloud, I thrive in the dynamic intersection of these domains. Join me on this journey of innovation and resilience as we sculpt a secure, efficient, and future-ready tech realm.