Launch Week Day 3: Inventory and compliance history
 Lars Kamp
Lars Kamp
Today, we're announcing our History capability for your cloud inventory and compliance status. With Fix, you can now track five different events for your cloud resources over time: created, updated, deleted, compliant, and vulnerable.
Traditional security tools tends to provide a point-in-time check on the status of your resources. But compliance often requires demonstrating continuous adherence over time. Without the historical context of a resource and your cloud(s), it's also difficult to understand trends, validate changes or perform thorough audits.
History solves this core problem with a continuous, historical view of the cloud inventory and its compliance status. This allows users to understand their security posture in context, track changes over time, and gain insights that were previously impossible or time-consuming to obtain.
By default, Fix takes an hourly snapshot of your inventory. Over time, these snapshots add up to a true change history of your cloud and its resources. For example, in the screenshot below, you see a filter applied that shows all resources created during between July 24 and July 31.
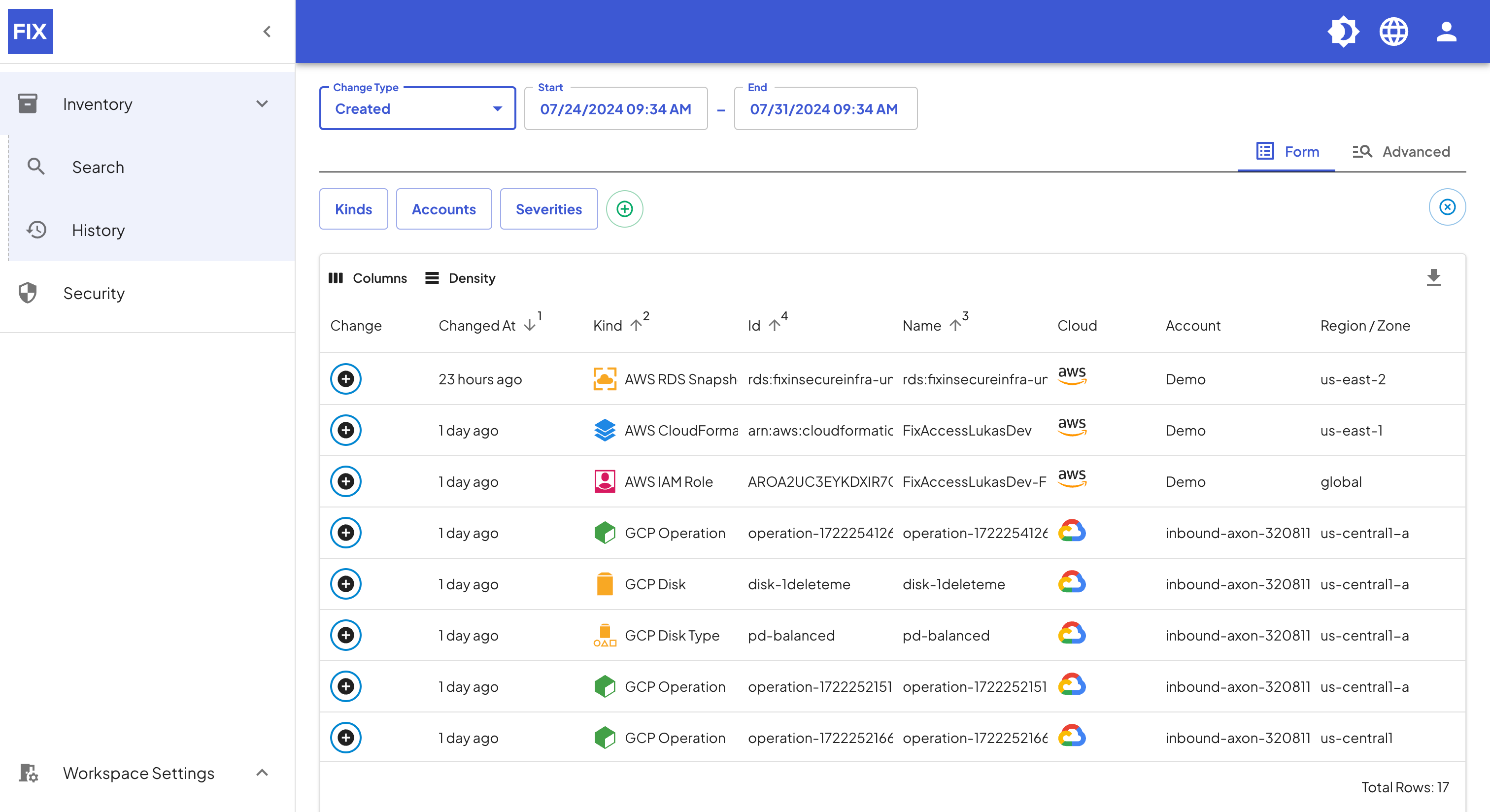
As you can see from the results, with resources from Google Cloud and AWS, History also leverages the multi-cloud inventory we announced on Day 1. The filter on top allows me to change the search to any of the five types of events Fix supports.
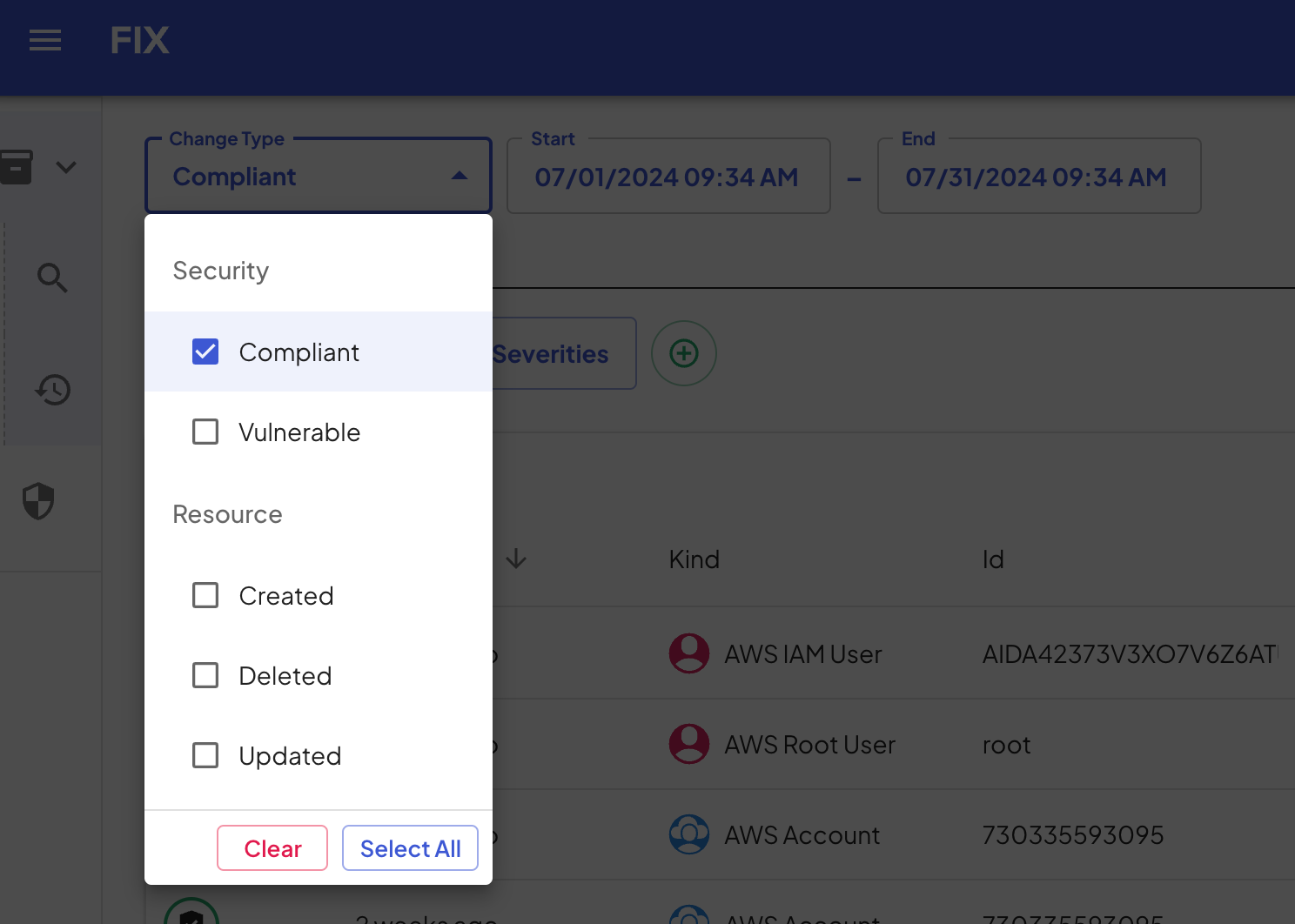
Let's assume now I'm investigating an incident and therefore want to dig a little bit deeper into a specific resource and understand its changes over time. The change history provides a detailed view of all events, ever since Fix recorded the resource for the first time.
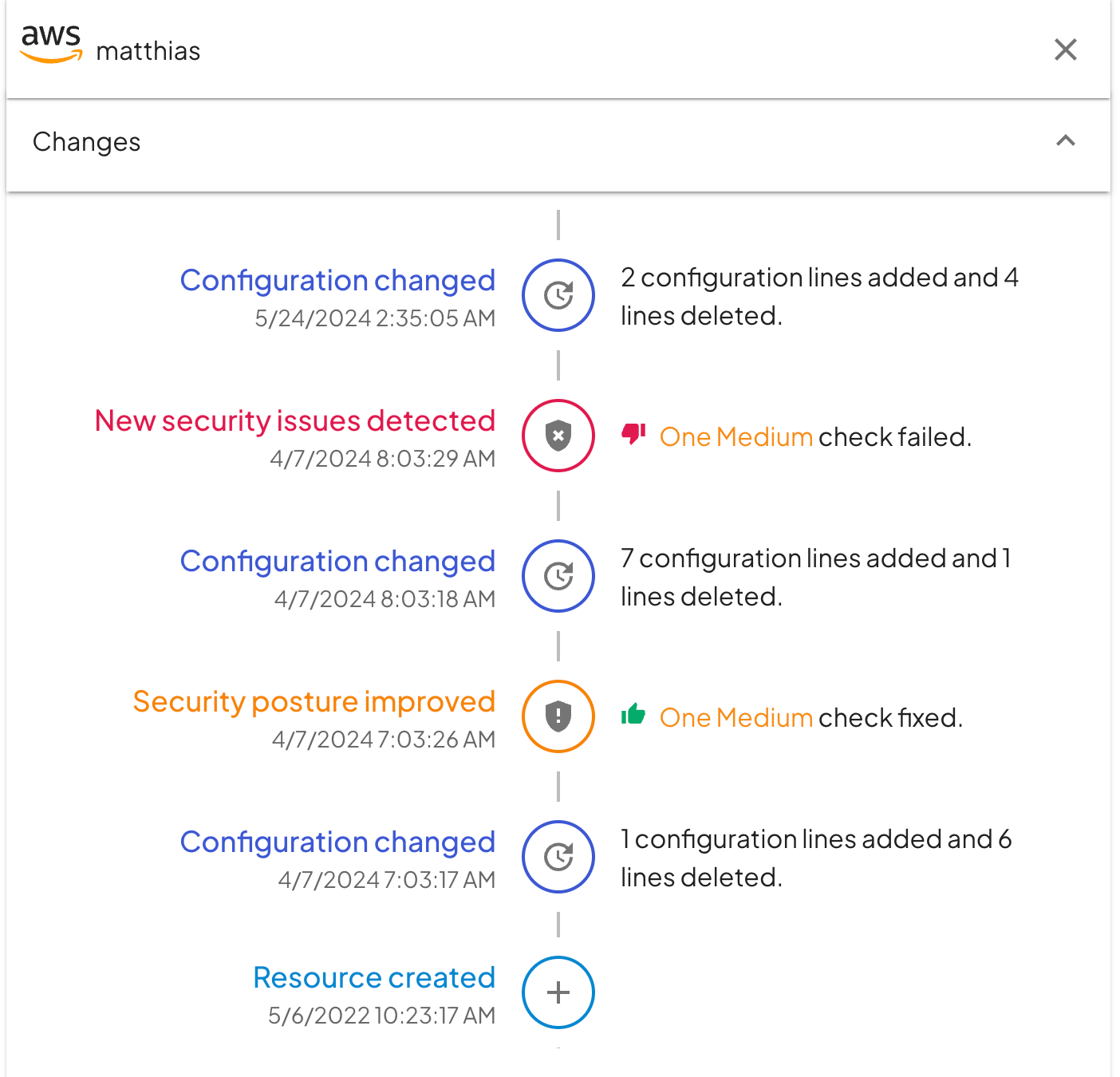
What's of course interesting for developers and security engineers alike is to understand what exactly changed in the configuration for a resource. Fix records and highlights the diff for every configuration change.
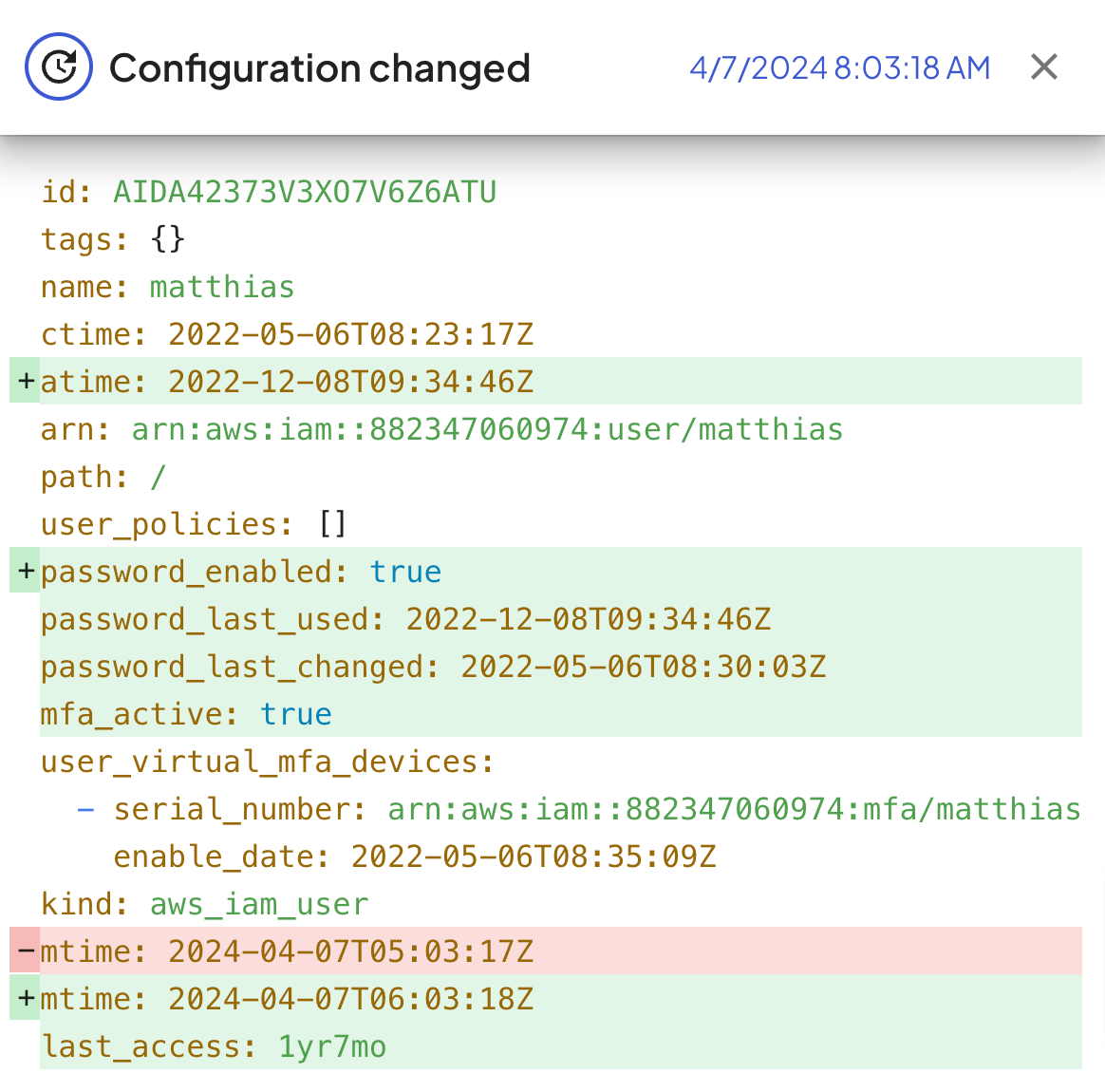
Here are a few more use case examples for our new History capability:
Lifecycle tracking. Monitor the full lifecycle of cloud resources, from creation to deletion, including all modifications.
Investigate. Trace the timeline of compromised resources to identify when and how they became vulnerable.
Verify. Confirm that planned changes were implemented correctly and at the intended time.
Trend. Analyze how overall security posture has changed over time to identify improvement areas
To help you with ideas for use cases and to get started, we've included a set of example searches which you'll see on the landing screen for History.
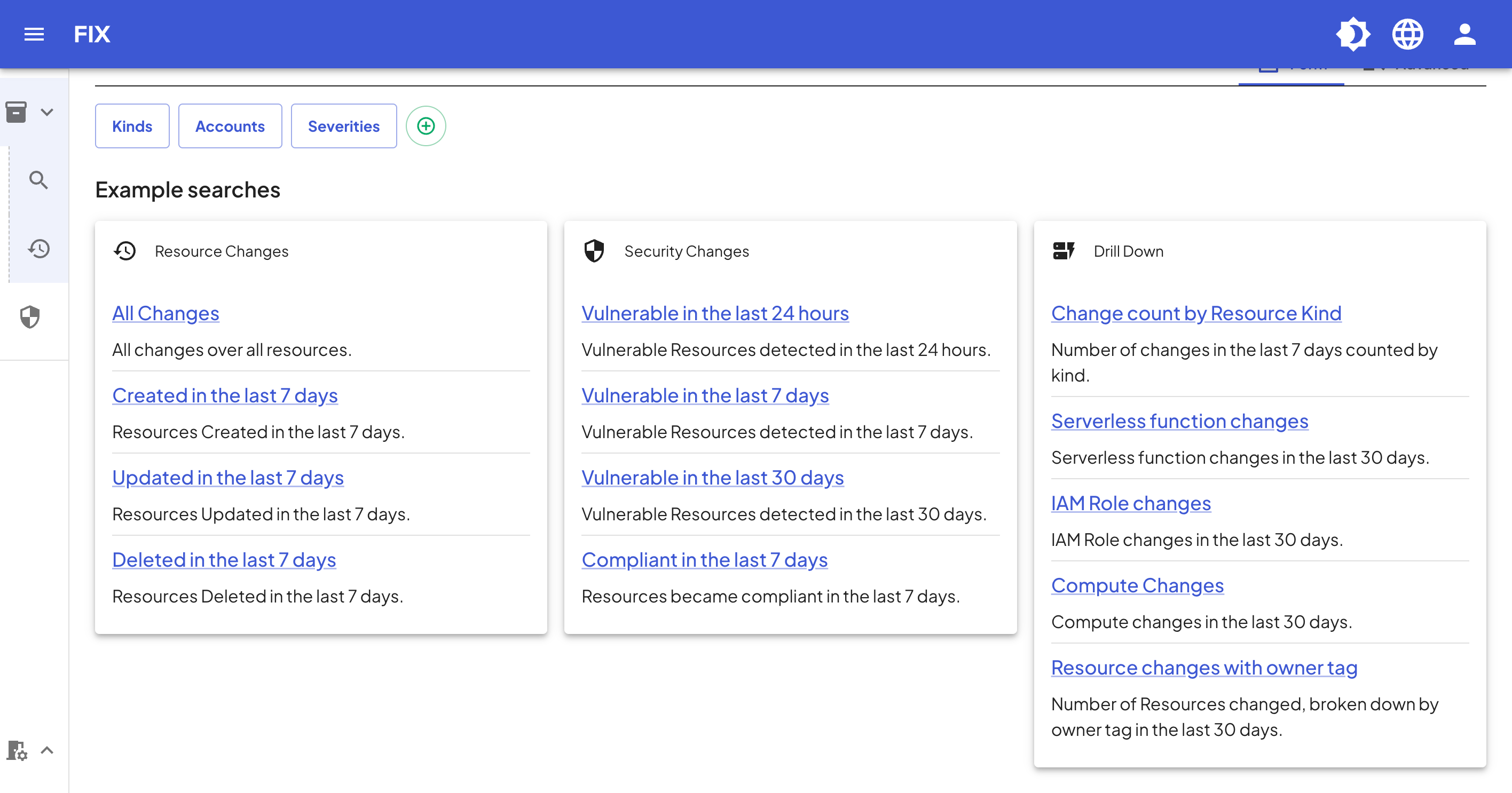
History is available to all Fix subscribers. Head on over and log in to Fix to check it out!
This blog post is part of our Launch Week 1 announcements running from July 29th to August 2nd.
Subscribe to my newsletter
Read articles from Lars Kamp directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
