[SEC Playground: Half Year CTF 2024] - Crackme
 Keqingsmellgood
Keqingsmellgood
Introduction to the Challenge
The challenge was a zip file containing a crackme.exe binary.
When executed, it showed this message.
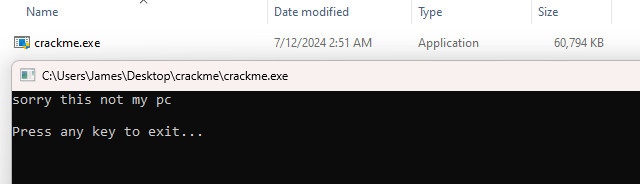
Do something with the program and the flag will show.
Format: re{flag}
Password for unzip: secplayground
Anti-Debugging Techniques
Monitor and Kill Debugging Applications
I tried to debug using x64dbg and System Informer, but I found that the debugging tools were forcibly closed when I tried to open the application.
So, I assumed there was some kind of anti-debugging logic implemented.
Decompiling Binaries with ILSpy
First thing I usually do when facing a Windows binary is to try decompiling it with dnSpy or ILSpy.
Just drag .exe binary into ILSpy windows.
Focus on the crackme function. The main application logic was decompiled back to C# language.
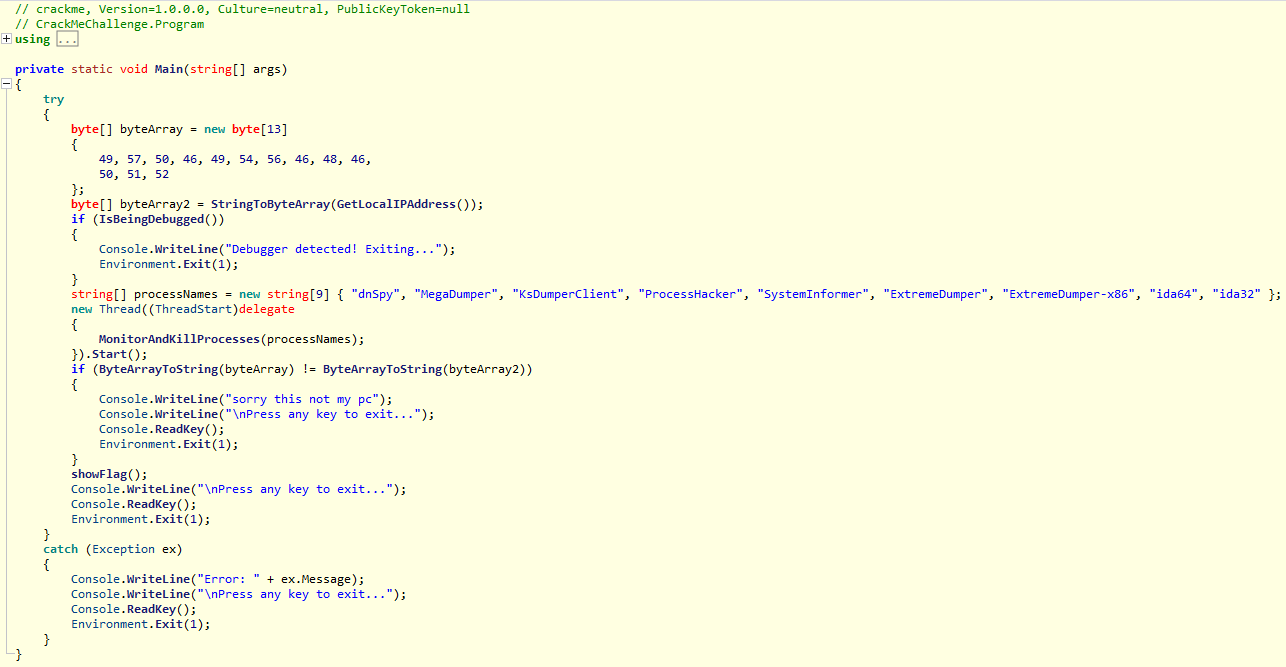
private static void Main(string[] args)
{
try
{
byte[] byteArray = new byte[13]
{
49, 57, 50, 46, 49, 54, 56, 46, 48, 46,
50, 51, 52
};
byte[] byteArray2 = StringToByteArray(GetLocalIPAddress());
if (IsBeingDebugged())
{
Console.WriteLine("Debugger detected! Exiting...");
Environment.Exit(1);
}
string[] processNames = new string[9] { "dnSpy", "MegaDumper", "KsDumperClient", "ProcessHacker", "SystemInformer", "ExtremeDumper", "ExtremeDumper-x86", "ida64", "ida32" };
new Thread((ThreadStart)delegate
{
MonitorAndKillProcesses(processNames);
}).Start();
if (ByteArrayToString(byteArray) != ByteArrayToString(byteArray2))
{
Console.WriteLine("sorry this not my pc");
Console.WriteLine("\nPress any key to exit...");
Console.ReadKey();
Environment.Exit(1);
}
showFlag();
Console.WriteLine("\nPress any key to exit...");
Console.ReadKey();
Environment.Exit(1);
}
catch (Exception ex)
{
Console.WriteLine("Error: " + ex.Message);
Console.WriteLine("\nPress any key to exit...");
Console.ReadKey();
Environment.Exit(1);
}
}
From the decompiled source code, the application has anti-debugging logic that checks the process name.
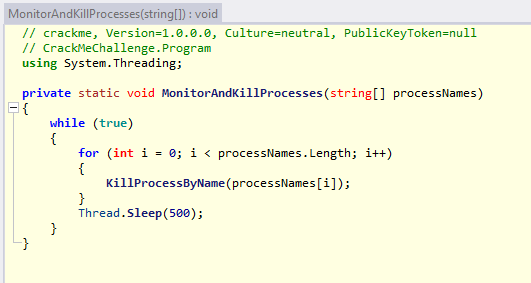
Then it checks the host's local IP address and compares it with hardcoded strings.
If they match, the application will decrypt and display a flag.
Hardcoded Local IP Address Comparison
Flag Retrieval
First method: Change local IP address
Decode the hardcoded IP address value with CyberChef.
49, 57, 50, 46, 49, 54, 56, 46, 48, 46, 50, 51, 52
From_Decimal('Space',false)
192.168.0.234
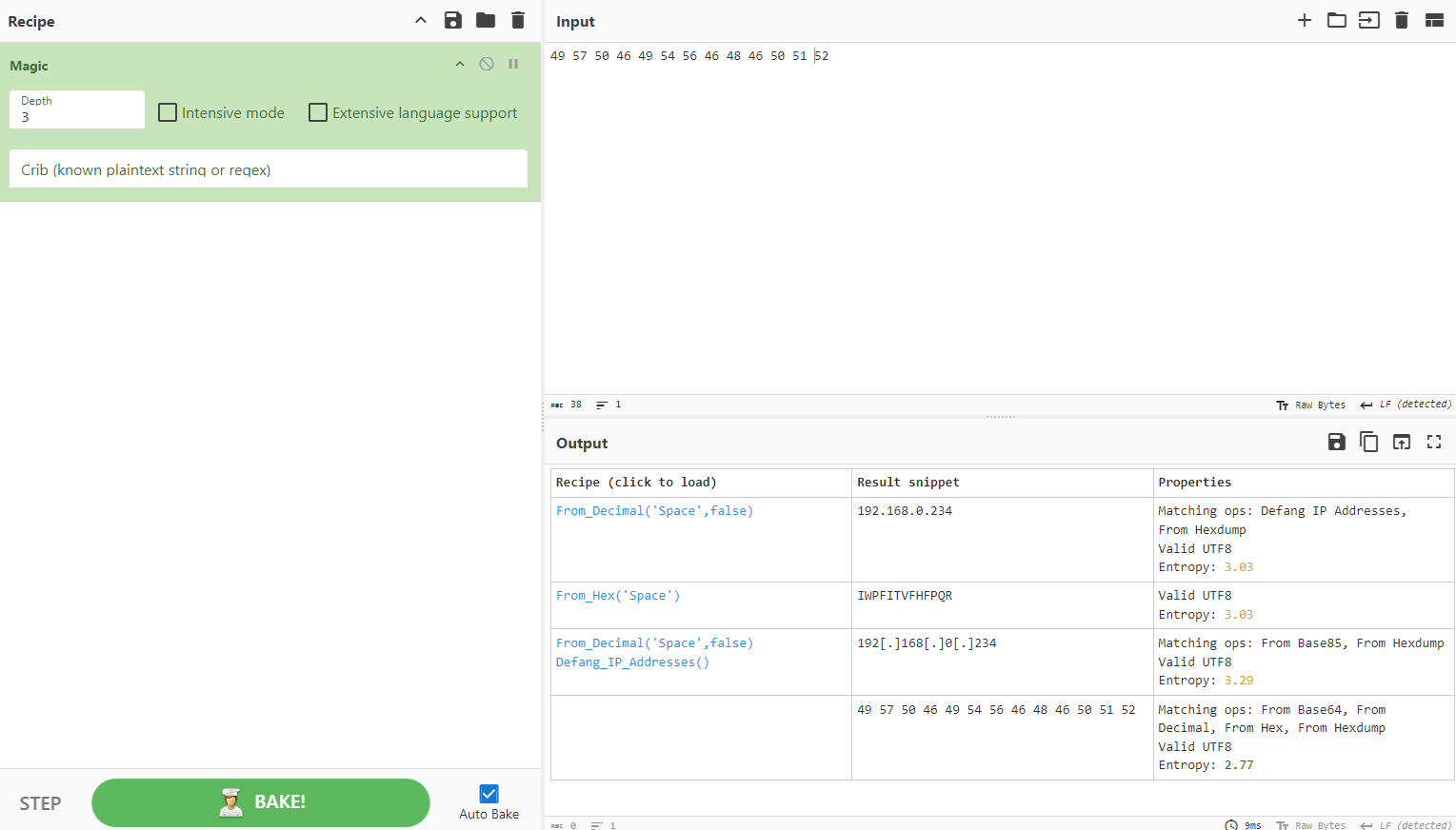
Change the IP address to 192.168.0.234, and the flag will appear.
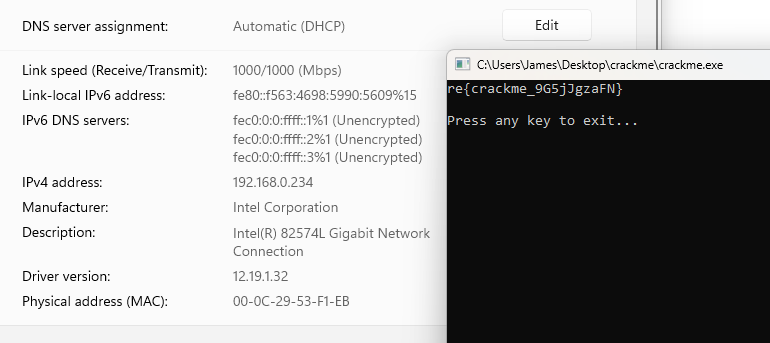
Second method: Decrypt AES encrypted strings
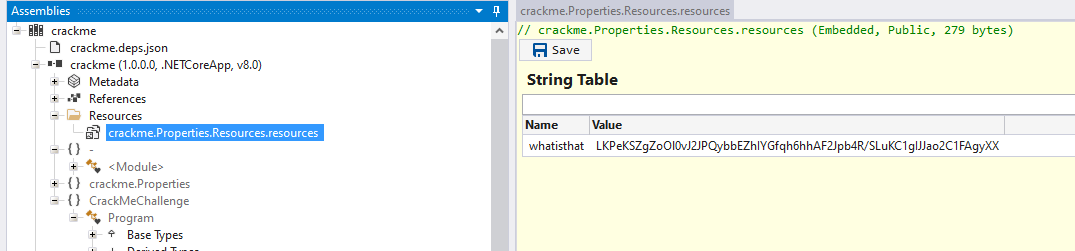
In the decompiled source code, there was a key and IV hardcoded, as shown in the screenshot below.
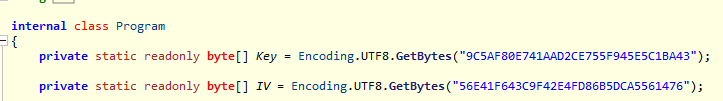
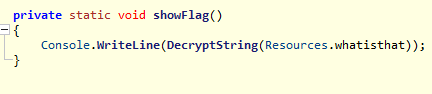
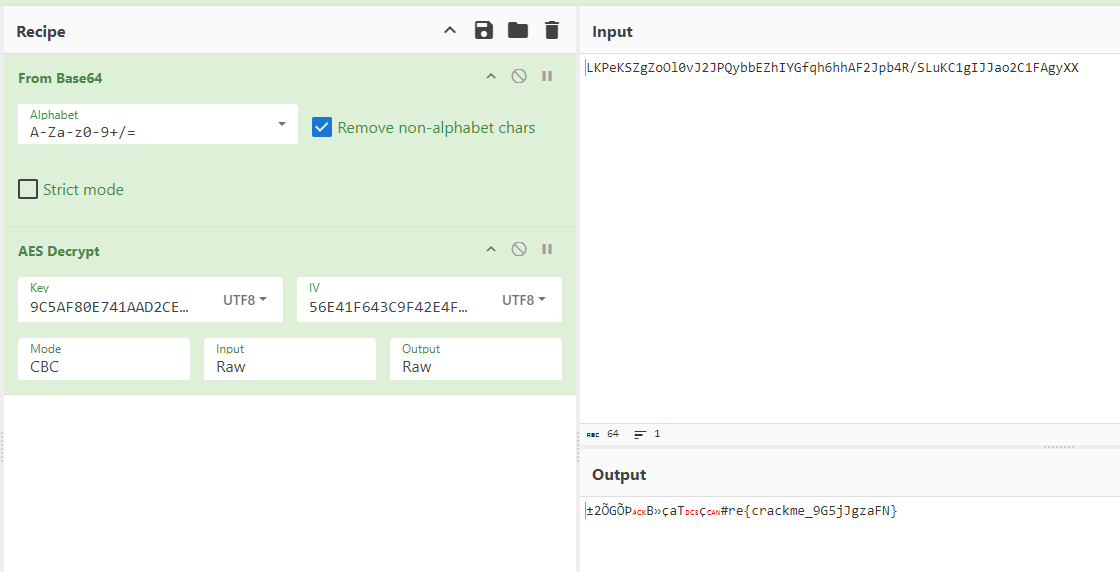
I decrypt the string from the resource file using CyberChef.
Subscribe to my newsletter
Read articles from Keqingsmellgood directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
