What is a Distributed Denial-of-Service (DDoS) Attack?
 Temitope
Temitope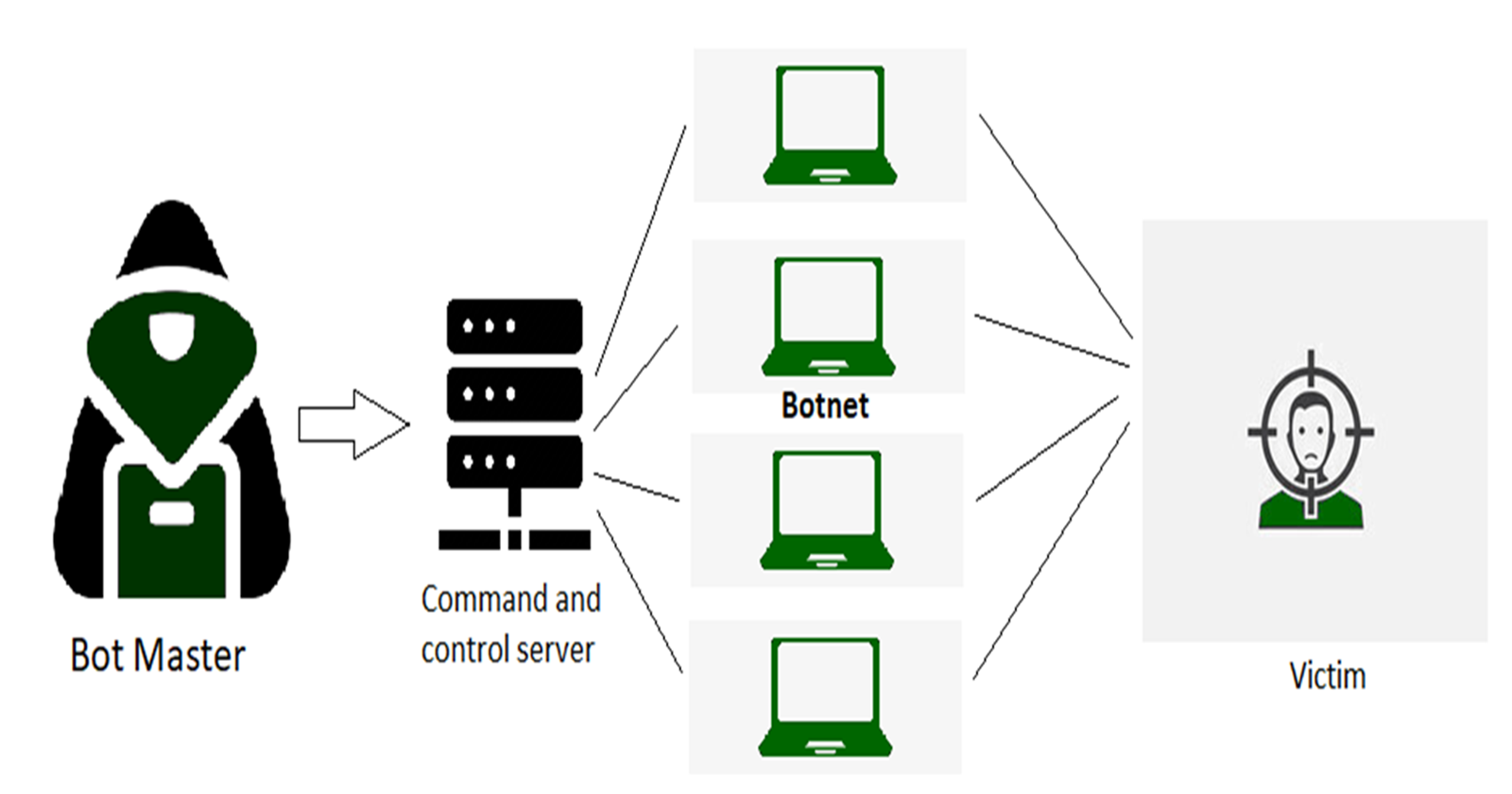
Basic Idea: A DDoS attack is like a digital traffic jam. Imagine you're trying to get into a popular concert, but thousands of people who have no intention of seeing the show are blocking the entrance. You and other real fans can't get in because the venue is overwhelmed by the crowd. This is similar to what happens during a DDoS attack but online.
How It Works:
Botnet Army:
Hackers create a network of compromised computers called a "botnet." These are ordinary computers that have been infected with malicious software, often without the owner's knowledge.
The botnet can consist of hundreds, thousands, or even millions of these infected machines.
Flooding the Target:
The hacker commands all these infected computers to send requests to a specific website or online service simultaneously.
This sudden surge in traffic is like a flood of people rushing to the concert entrance all at once.
Overloading the System:
The target website or service gets overwhelmed by the massive amount of traffic.
Just like the concert venue can't handle too many people at once, the website's servers can't handle this flood of requests.
As a result, the website slows down significantly or crashes entirely, making it inaccessible to regular users.
Why It's Bad:
Disruption: The main goal of a DDoS attack is to disrupt the normal functioning of a website or online service. This can cause significant downtime, leading to lost revenue, especially for e-commerce sites.
Frustration: Users trying to access the site get frustrated because they can't get the information or services they need.
Damage: Extended downtime can damage the reputation of the business or service provider.
Real-World Examples:
If a major online retailer gets hit by a DDoS attack, customers might not be able to make purchases, leading to lost sales.
If an online banking service is targeted, customers can't access their accounts, leading to a lack of trust in the bank's security.
Protection Against DDoS Attacks:
Firewalls and Routers: Use advanced configurations to filter out malicious traffic.
DDoS Protection Services: Companies can use specialized services that detect and mitigate DDoS attacks by distributing the traffic across multiple servers or blocking malicious traffic.
Redundancy: Having multiple servers and data centers so that if one is attacked, others can take over.
In essence, a DDoS attack is a way for hackers to create chaos and disrupt online services by overwhelming them with fake traffic, making it difficult or impossible for legitimate users to access the targeted sites.
Subscribe to my newsletter
Read articles from Temitope directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
