Launch Week Day 5: Cloud management and remediation with fixctl
 Lukas Lösche
Lukas Lösche
In complex cloud environments, visibility, control, and security over sprawling resources can quickly become overwhelming. fixctl, the CLI tool designed for Fix Business users, directly addresses these challenges by providing advanced search capabilities and automated operations for both management and remediation tasks.
Whether you're conducting routine audits, performing rapid on-demand queries, systematically cleaning up abandoned cloud resources, or keeping your documentation automatically up to date, fixctl delivers the capabilities necessary to maintain an organized, secure, and cost-efficient cloud environment.
What makes fixctl useful?
Advanced search capabilities in your cloud inventory
fixctl provides insights into resource dependencies and configurations. Users can search for resources based on various criteria, such as resource type, tags, and relationships. This feature enables users to quickly locate resources and understand their relationships within the cloud environment. You can for example express searches like "show me all databases across all my cloud accounts that are open to the internet".
Documentation for compliance and auditing
Keeping documentation up-to-date is important but also tedious, for compliance and auditing purposes. fixctl helps with the generation of detailed reports on you cloud inventory by allowing you to export any search result as CSV, JSON or YAML. Ensuring that documentation is always current and accessible for both internal audits and external compliance checks.
Automated resource management
From identifying to managing unused, underutilized or abandoned resources, fixctl automates critical aspects of cloud resource management. This automation helps in optimizing resource utilization, reducing costs, and maintaining a clean and efficient cloud environment.
Installation and configuration
fixctl is readily accessible via direct download for all major operating systems or through Homebrew for macOS users. Setup is quick, with a single binary file that can be run from anywhere. Once installed, you can configure fixctl with an API token, to connect to your Fix Enterprise workspace. Refer to the CLI documentation for detailed installation and configuration instructions.
Real-world use cases
Cleanup of abandoned resources
fixctl excels in identifying unused resources such as abandoned AWS EBS volumes. With commands that can find these resources based on specific criteria, teams can easily generate lists or even automate the deletion process, ensuring operational efficiency and cost savings.
First let's identify all EBS volumes that are available (i.e. not in-use on a compute instance) and have not been accessed in the last 30 days, using the Fix UI. In the inventory we execute the following advanced search:
is(aws_ec2_volume) and volume_status = available and last_access > 30d
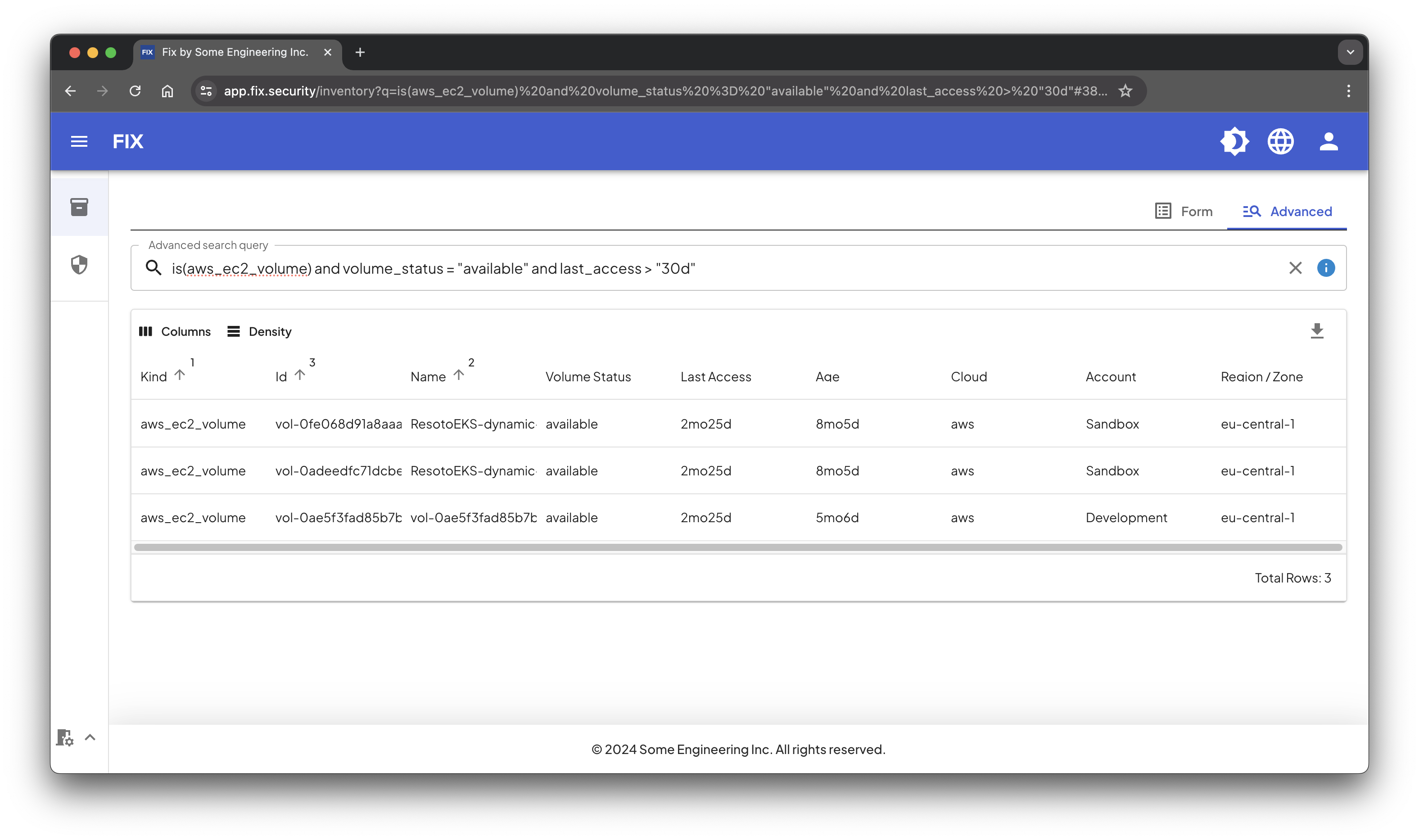
The result in this case are three EBS volumes in our Sandbox and Development accounts that haven't been accessed in over two months.
Next, we execute the same search using fixctl and format the output as CSV
$ fixctl --format csv --search "is(aws_ec2_volume) and volume_status = available and last_access > 7d"
vol-0adeedfc71dcbe9d5,ResotoEKS-dynamic-pvc-e575191f-d4f3-4253-96e4-399ded05bf14,aws_ec2_volume,aws,752466027617,eu-central-1
vol-0ae5f3fad85b7b3c6,vol-0ae5f3fad85b7b3c6,aws_ec2_volume,aws,625596817853,eu-central-1
vol-0fe068d91a8aaaced,ResotoEKS-dynamic-pvc-08ded29a-70c9-4d36-9d28-727140850d96,aws_ec2_volume,aws,752466027617,eu-central-1
Again we find the three EBS volumes from before.
For further processing we'd like to take this data and create AWS CLI commands from it. The idea would be for us to have an AWS CLI profile with the name of the corresponding AWS account and then generate aws ec2 delete-volume commands that, when executed, clean up the abandoned resources.
Now, instead of outputting CSV, we use fixctl's default output format, JSON, and take a look at the raw data. We use jq to pretty-print the JSON.
$ fixctl --search "is(aws_ec2_volume) and volume_status = available and last_access > 30d" | jq .
{
"id": "WymIC9KDLHoseQNQ7ec0vQ",
"type": "node",
"reported": {
"age": "5mo6d",
"arn": "arn:aws:ec2:eu-central-1:625596817853:volume/vol-0ae5f3fad85b7b3c6",
"atime": "2024-04-28T11:06:03Z",
"availability_zone": "eu-central-1a",
"ctime": "2024-02-14T13:57:44Z",
"id": "vol-0ae5f3fad85b7b3c6",
"kind": "aws_ec2_volume",
"last_access": "2mo26d",
"last_update": "2mo26d",
"mtime": "2024-04-28T11:06:03Z",
"name": "vol-0ae5f3fad85b7b3c6",
"snapshot_before_delete": false,
"tags": {},
"volume_attachments": [],
"volume_encrypted": false,
"volume_iops": 3000,
"volume_multi_attach_enabled": false,
"volume_size": 10,
"volume_snapshot_id": "",
"volume_status": "available",
"volume_throughput": 125,
"volume_type": "gp3"
},
"ancestors": {
"account": {
"reported": {
"id": "625596817853",
"name": "Development"
}
},
"cloud": {
"reported": {
"id": "aws",
"name": "aws"
}
},
"region": {
"reported": {
"id": "eu-central-1",
"name": "eu-central-1"
}
}
},
"security": {
"has_issues": true,
"issues": [
{
"benchmarks": [
"iso27001",
"aws_cis_2_0",
"aws_cis_1_5",
"aws_well_architected_framework_security_pillar"
],
"check": "aws_ec2_volume_not_encrypted",
"opened_at": "2024-05-02T18:41:29Z",
"severity": "medium"
},
{
"benchmarks": [
"aws_well_architected_framework_security_pillar"
],
"check": "aws_ec2_ebs_volume_unused",
"opened_at": "2024-05-02T18:41:29Z",
"severity": "medium"
}
],
"opened_at": "2024-05-02T18:41:29Z",
"reopen_counter": 0,
"run_id": "0c4c017a-3475-11ef-b240-ae511cb09148",
"severity": "medium"
}
}
We see that information like the volume's account and region can be found in the ancestors section, while data like the volumes id is part of the reported section. Let's adjust the jq command to format the data and generate the AWS CLI commands that would delete the abandoned volumes:
$ fixctl --search "is(aws_ec2_volume) and volume_status = available and last_access > 30d" \
| jq -r '. | "aws ec2 delete-volume --volume-id \(.reported.id) --region \(.ancestors.region.reported.id) --profile \(.ancestors.account.reported.id)"'
aws ec2 delete-volume --volume-id vol-0adeedfc71dcbe9d5 --region eu-central-1 --profile 752466027617
aws ec2 delete-volume --volume-id vol-0ae5f3fad85b7b3c6 --region eu-central-1 --profile 625596817853
aws ec2 delete-volume --volume-id vol-0fe068d91a8aaaced --region eu-central-1 --profile 752466027617
The resulting commands can either be written to a shell-script or executed directly.
Other use cases
Instead of generating AWS CLI commands, you may want to pass the data to a custom API endpoint using curl or use it to update the internal documentation in a wiki.
Integrating with custom APIs
fixctl can be utilized to feed data directly into custom APIs. This integration is particularly useful for organizations that maintain custom automation workflows or specialized reporting systems. By using fixctl to query and format data, and then piping it through tools like curl, teams can dynamically update APIs with the latest cloud inventory information. For example, you could automatically report changes in resource utilization to a cost management API, or update a security compliance dashboard in real-time.
$ fixctl --search "is(aws_ec2_instance) and instance_status = running" | curl -X POST -d @- https://api.yourcompany.com/update-inventory
Updating internal documentation
Maintaining up-to-date documentation is important for compliance but also benefits internal teams. With fixctl, teams can automate the extraction and formatting of cloud inventory data to update internal documentation systems, such as wikis or Confluence pages. By automating this process, you ensure that documentation is consistently accurate and reflects the current state of your cloud environment.
Example workflow:
$ fixctl --format yaml --search 'is(aws_ec2_instance) and tags.owner = "team xyz"' > latest_team_xyz_resources.yaml
$ python update_wiki.py latest_team_xyz_resources.yaml
This script could be part of a scheduled job that runs daily, ensuring that the team's resource page is always up to date with the latest details.
Dynamic resource tagging and management
fixctl allows teams to search for resources based on specific criteria and apply changes, such as updating tags or initiating management actions. This can be part of both routine housekeeping or specific re-tagging projects, ensuring resources are correctly labeled according to new policies or project alignments.
Example command:
$ fixctl --search 'is(aws_ec2_instance) and tags.project = "old project"' | jq -r '.reported.id' | xargs -I {} aws ec2 create-tags --resources {} --tags Key=Project,Value=new_project
This could find and update the tags of thousands of resources in bulk.
Proactive compliance monitoring
Utilizing fixctl for compliance monitoring allows teams to continuously check for configurations that deviate from established standards. By integrating these checks into continuous deployment pipelines, any non-compliant resources can be flagged or corrected automatically.
Example:
Automatically checking for unencrypted EBS volumes and either alerting or initiating encryption, thereby ensuring compliance with data protection standards without manual intervention.
$ fixctl --search "is(aws_ec2_volume) and volume_encrypted = false" | jq -r '.reported.id' | xargs -I {} aws ec2 encrypt-volume --volume-id {}
Conclusion
fixctl is a CLI tool made for both, individual engineers and enterprise-level teams. For engineers, it provides a powerful interface to interact directly with cloud inventory data, enabling quick searches, updates, and insights across clouds, accounts and regions. This flexibility is ideal for running one-off commands or exploring resource dependencies and statuses in real-time.
For teams, fixctl offers the capability to be fully integrated into automated pipelines, supporting regular maintenance tasks, and generating essential reports for compliance and monitoring. Whether you're looking to automate the cleanup of unused resources, maintain accurate documentation for audits, or implement proactive resource management strategies, fixctl stands out as an essential tool in the cloud management toolkit.
Use fixctl to enhance your cloud resource management and make sure that your cloud operations are both efficient and compliant.
This blog post is part of our Launch Week 1 announcements running from July 29th to August 2nd.
Subscribe to my newsletter
Read articles from Lukas Lösche directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
