Understanding Cyber Threat Intelligence
 Chfix
Chfix
Welcome to our exploration of Cyber Threat Intelligence (CTI), a principal cornerstone of the modern cybersecurity landscape.
Whether you're new to cyber threats or aiming to enhance your expertise, understanding Cyber Threat Intelligence (CTI) is crucial.
Look no further, In this post, we'll simplify what CTI is, explore its evolution, and reveal how it can boost your organization’s security.
Let’s dive in!
What is Cyber Threat Intelligence (CTI)?
Definition and Overview
At its core, Cyber Threat Intelligence (CTI) is about understanding the who, what, where, and how of potential cyber threats.
Imagine CTI as a detailed map that guides you through the dark and often chaotic landscape of cyber threats. It involves gathering, analyzing, and interpreting information about current and emerging threats, including the techniques and tactics used by cyber-criminals.
In Practical Terms: Think of CTI as having a crystal ball that provides you with insights into potential threats before and after they happen. This intelligence includes details about:
Threat Actors: Who is behind the threats? Are they hackers, cyber-criminal organizations, or nation-states?
Indicators of Compromise (IOCs): What signs or clues should you look for to detect or prevent these threats?
Tactics, Techniques, and Procedures (TTPs): How do these threat actors operate?
Importance in the Cybersecurity Landscape
In today’s digital world, threats are not just increasing in number but also in sophistication. Relying on traditional security measures alone is like using a map from the 1980s to navigate a modern city. CTI offers a proactive approach by:
Anticipating Threats: By understanding emerging threats and attack patterns, so you can prepare defenses before an attack occurs.
Enhancing Incident Response: CTI provides critical information that helps you respond more quickly and effectively to security incidents.
The Evolution of Cyber Threat Intelligence
Historical Context
Cyber Threat Intelligence has come a long way since its early days. Initially, it was mostly about sharing information on basic malware and vulnerabilities. As cyber threats evolved, so did CTI, expanding to include detailed profiles of threat actors, sophisticated attack methods, and the broader threat landscape.
How CTI Has Evolved with Technology
The evolution of CTI parallels advancements in technology:
Early Days: Initially focused on manual threat detection and basic intelligence gathering.
Modern Era: With the advent of big data and machine learning, CTI now includes automated data collection and real-time analysis, allowing for faster and more accurate threat detection.
Key Objectives and Benefits of CTI
Enhancing Security Posture
CTI strengthens your security posture by:
Predicting Threats: By analyzing trends and threat patterns, CTI helps you anticipate and prepare for potential attacks.
Proactive Defense: It enables you to implement security measures and strategies before threats can exploit vulnerabilities.
Supporting Decision-Making and Risk Management
CTI is invaluable for making informed security decisions and managing risks:
Informed Decisions: Provides actionable insights that guide your security policies and strategies.
Risk Assessment: Helps identify and prioritize risks, ensuring that you focus on the most critical threats.
Visuals and Examples
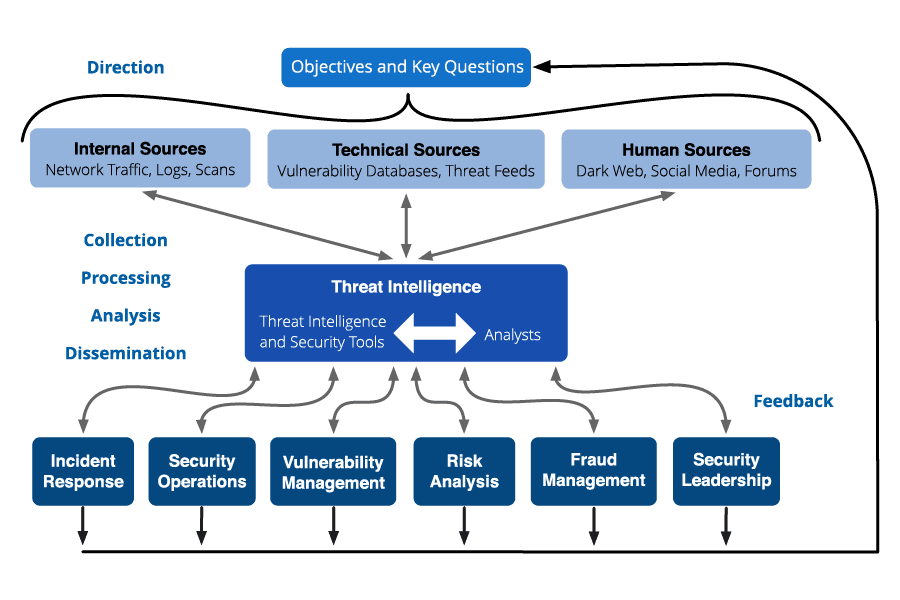
The 6 steps Threat Intelligence Lifecycle
Example Scenario: Ransomware Attack
"On May 7, 2021, a ransomware attack targeted the Colonial Pipeline Company, the largest pipeline system for refined oil products in the United States."
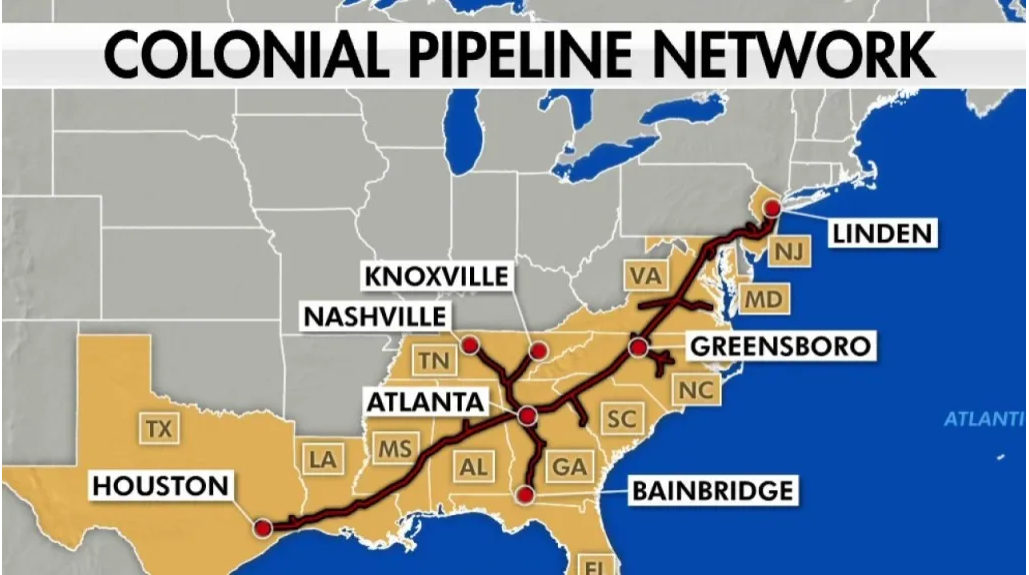
image source
Let’s take the 2021 Colonial Pipeline ransomware attack as an example. Effective Cyber Threat Intelligence (CTI) could have been a game-changer in this situation.
By providing early warnings about the specific ransomware variant and its associated tactics, CTI could have enabled the pipeline to implement preventive measures and respond swiftly, potentially mitigating the attack’s impact and avoiding widespread disruption.
This underscores the critical role of CTI in not just identifying but also proactively defending against evolving threats, so that organizations can implement preventive measures and mitigate the impact of the attacks.
Summary and Key Takeaways
In summary, Cyber Threat Intelligence is like having a high-resolution map of the cyber threat landscape. It helps you anticipate threats, enhance your security posture, and make informed decisions, which will certainly saves your organization a lot of money in case something went south.
The evolution of CTI reflects technological advancements, making it a critical component of any robust cybersecurity strategy.
Additional Resources
Book: "The Hunters Handbook"
https://github.com/0x4D31/awesome-threat-detection/blob/master/docs/The-Hunters-Handbook.pdf
Awesome lists:
Practice CTI on TryHackMe:
References:
Final questions
How has Cyber Threat Intelligence impacted your cybersecurity strategy and overall perception?
Have you encountered any real-life instances where CTI played a key role in preventing or addressing threats?
We’d love to hear your experiences and insights—drop a comment below!
Subscribe to my newsletter
Read articles from Chfix directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Chfix
Chfix
i am a simple cyber threat intelligence analyst, feel free to reach out.