AWS to GCP - Workload Identity Federation - Explained
 Tanishka Marrott
Tanishka Marrott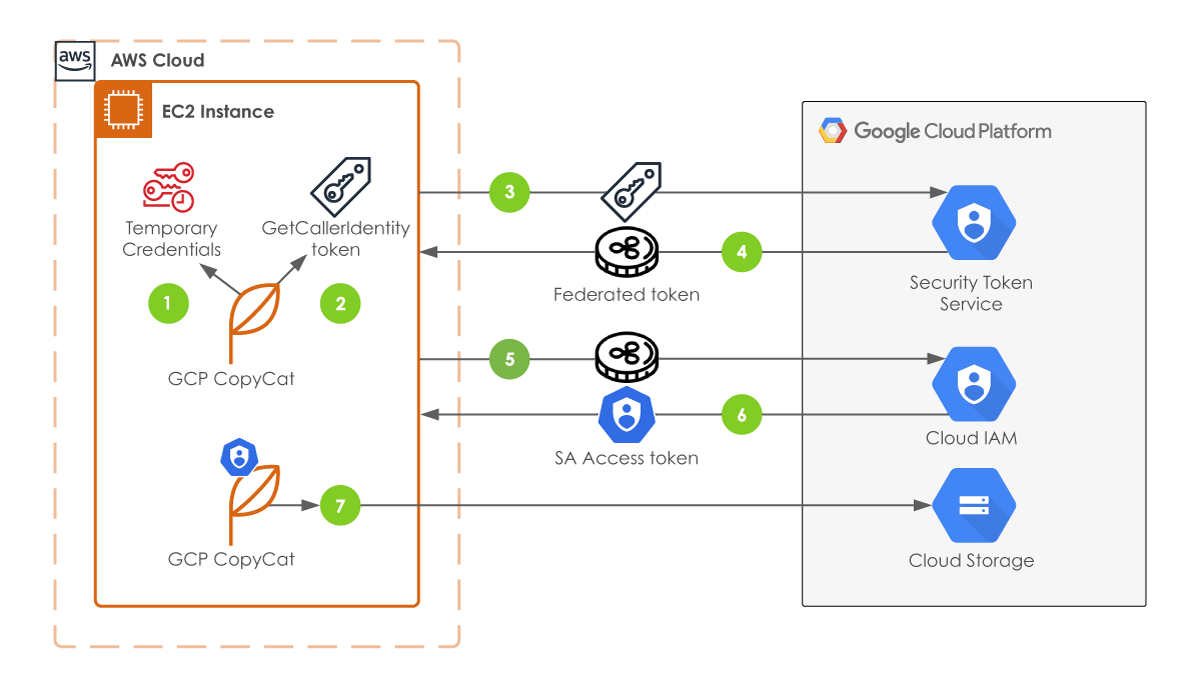
Introduction
Hey there! I'm excited to dive into Workload Identity Federation (WIF) in Google Cloud Platform (GCP). WIF is a secure method to access GCP resources without relying on static Service Account (SA) keys. Let’s explore how it works, why it’s beneficial, and how to set it up.
What is Workload Identity Federation?
Workload Identity Federation allows GCP to trust identities from external identity providers (IdPs) like AWS, Azure, or on-premises systems. This means you can use external identities to authenticate to GCP services without managing long-lived SA keys.
Why Use Workload Identity Federation?
Enhanced Security: Avoids the risks associated with long-lived SA keys.
Simplified Management: Eliminates the need to create, manage, and rotate SA keys.
Inter-Cloud Interactions: Allows seamless integration between GCP and other cloud providers like AWS.
How It Works
Here’s a simple workflow to illustrate the process:
The user or application uses an external identity from a trusted IdP (e.g., AWS IAM role).
GCP validates the external identity through Workload Identity Federation.
A short-lived token is generated for the GCP Service Account.
The token is used to access GCP resources securely.
Setting Up Workload Identity Federation
Let's set up WIF using AWS as the external IdP:
Step 1: Configure AWS IAM Role
Create IAM Role: Create an IAM role in AWS with the necessary permissions.
Trust Relationship: Set up the trust relationship to allow GCP to assume the role.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "accounts.google.com"
},
"Action": "sts:AssumeRoleWithWebIdentity"
}
]
}
Step 2: Set Up Workload Identity Pool in GCP
Create Identity Pool: Create a Workload Identity Pool in GCP.
gcloud iam workload-identity-pools create "my-pool" \
--project="my-project" \
--location="global" \
--display-name="My Pool"
Create Provider: Create a Workload Identity Provider within the pool.
gcloud iam workload-identity-pools providers create-aws "my-provider" \
--location="global" \
--workload-identity-pool="my-pool" \
--account-id="aws-account-id" \
--region="us-west-2"
Step 3: Grant IAM Permissions
Bind IAM Policy: Bind the GCP Service Account to the Workload Identity Pool.
gcloud iam service-accounts add-iam-policy-binding "my-service-account@my-project.iam.gserviceaccount.com" \
--role="roles/iam.workloadIdentityUser" \
--member="principal://iam.googleapis.com/projects/my-project/locations/global/workloadIdentityPools/my-pool/subject/aws-role-arn"
Step 4: Authenticate Using AWS Role
Assume Role: Assume the IAM role in AWS and obtain the token.
Exchange Token: Exchange the token for a GCP access token.
import google.auth
from google.auth import impersonated_credentials
from google.auth.transport.requests import Request
from subprocess import check_output
def get_impersonated_access_token(target_sa_email):
# Command to generate the impersonated access token
command = [
"gcloud", "auth", "print-access-token", f"--impersonate-service-account={target_sa_email}"
]
access_token = check_output(command).strip().decode("utf-8")
return access_token
if __name__ == "__main__":
target_sa_email = "target-sa@example.iam.gserviceaccount.com"
token = get_impersonated_access_token(target_sa_email)
print("Impersonated Access Token:", token)
Conclusion
Workload Identity Federation is a powerful tool for secure, scalable, and efficient cloud resource management. By integrating external identities with GCP, we can ensure robust security without the hassle of managing long-lived SA keys.
Feel free to explore the repository and try out the code. Let’s ensure our applications are secure and efficient!
Skills Utilized
Cloud Security: Enhanced security through federated identity management.
Python Scripting: Automated workflows with Python.
GCP Services: Leveraged GCP’s robust identity and access management features.
Subscribe to my newsletter
Read articles from Tanishka Marrott directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Tanishka Marrott
Tanishka Marrott
I'm a results-oriented cloud architect passionate about designing resilient cloud solutions. I specialize in building scalable architectures that meet business needs and are agile. With a strong focus on scalability, performance, and security, I ensure solutions are adaptable. My DevSecOps foundation allows me to embed security into CI/CD pipelines, optimizing deployments for security and efficiency. At Quantiphi, I led security initiatives, boosting compliance from 65% to 90%. Expertise in data engineering, system design, serverless solutions, and real-time data analytics drives my enthusiasm for transforming ideas into impactful solutions. I'm dedicated to refining cloud infrastructures and continuously improving designs. If our goals align, feel free to message me. I'd be happy to connect!