How to Easily Set Up a Kubernetes Cluster
 Sachin Yalagudkar
Sachin Yalagudkar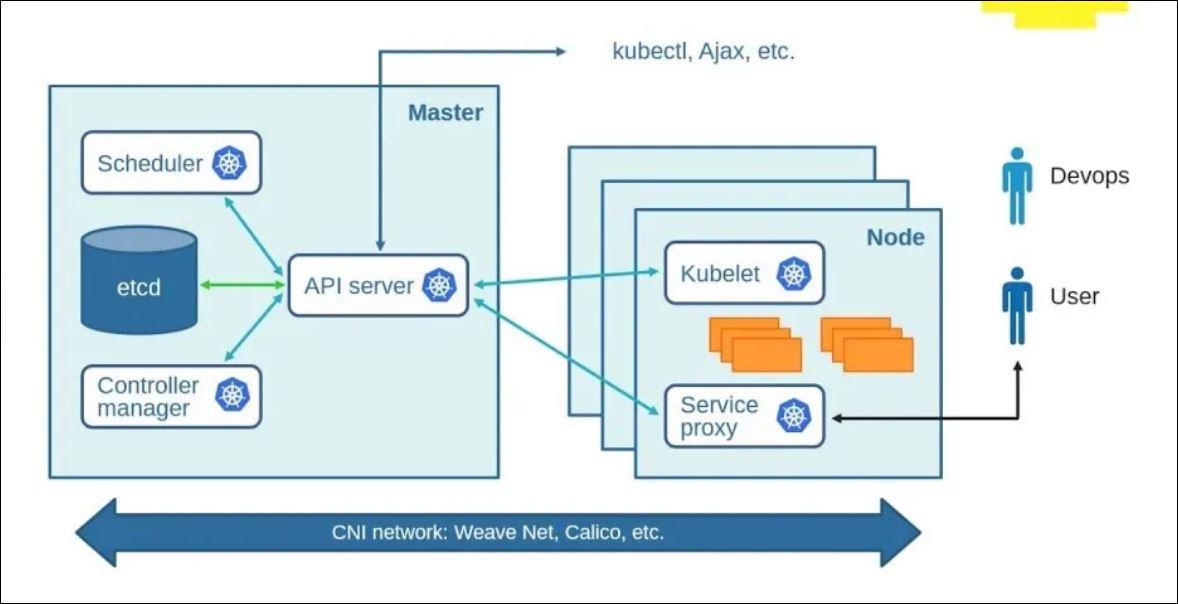
Minikube Installation
This guide offers detailed steps for installing Minikube on Ubuntu. Minikube enables you to run a single-node Kubernetes cluster locally, ideal for development and testing.
Step 1: Update System Packages
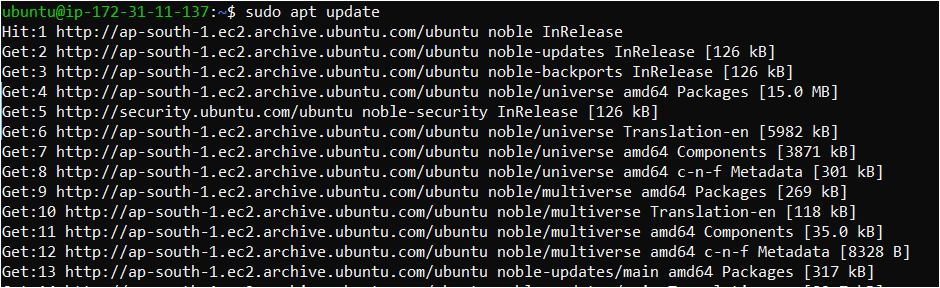
Launch ubuntu virtual machine and update the package list.
sudo apt update
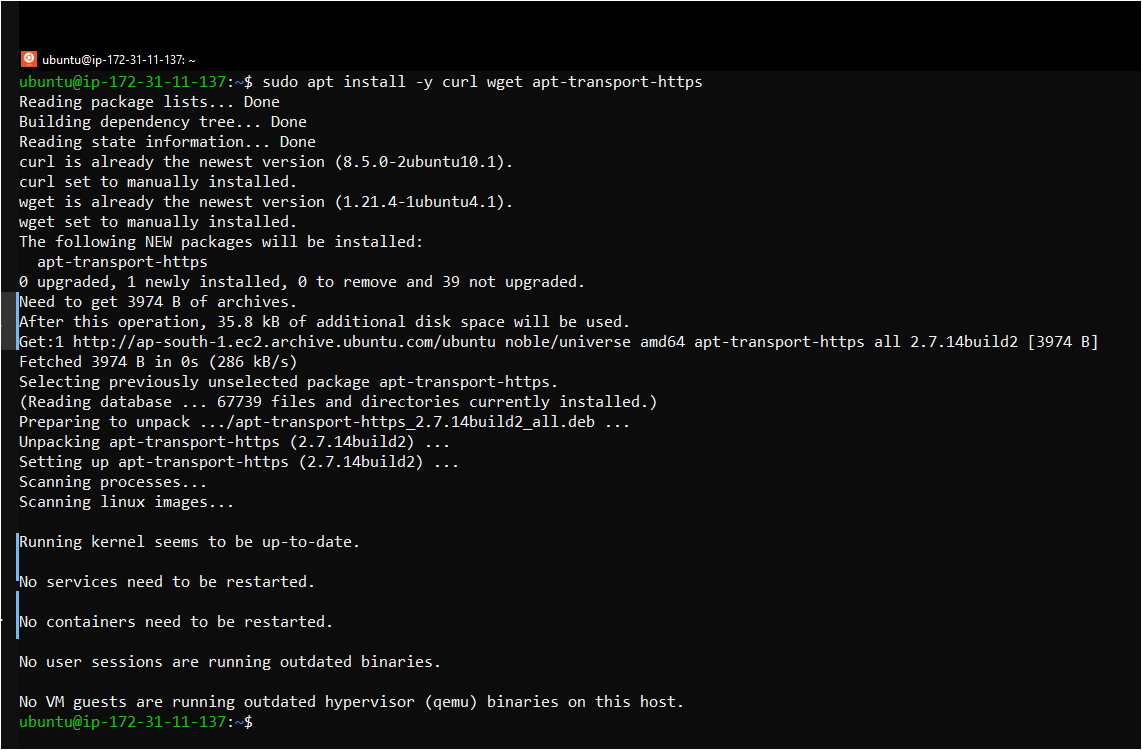
Step 2: Install Required Packages
sudo apt install -y curl wget apt-transport-https
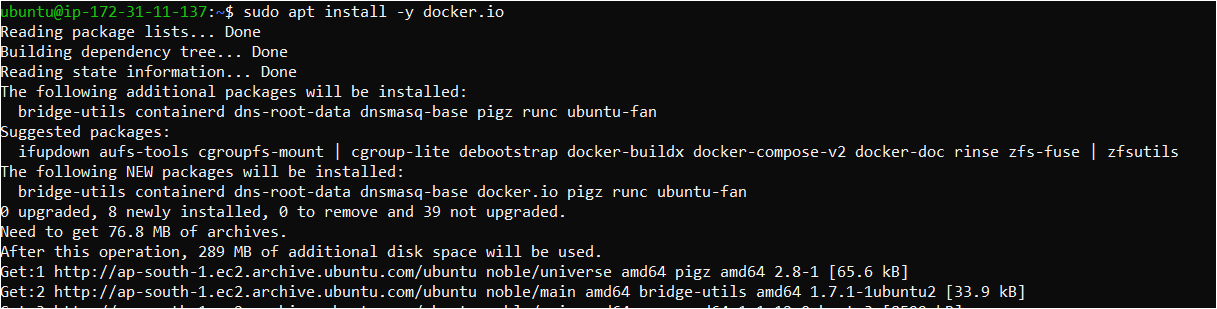
Step 3: Install Docker
sudo apt install -y docker.io
Start and enable Docker.
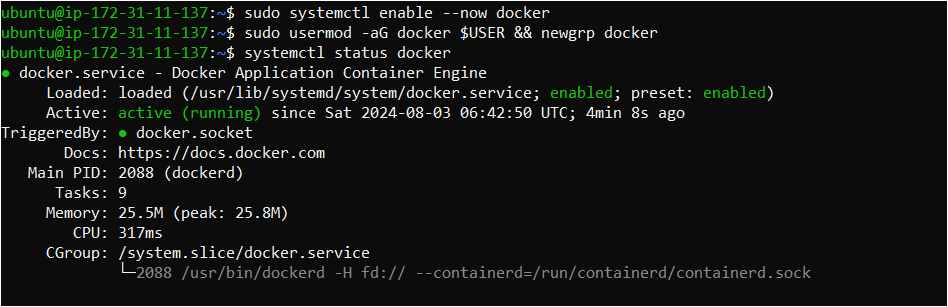
sudo systemctl enable --now docker
Add current user to docker group (To use docker without root)
sudo usermod -aG docker $USER && newgrp docker
Step 4: Install Minikube
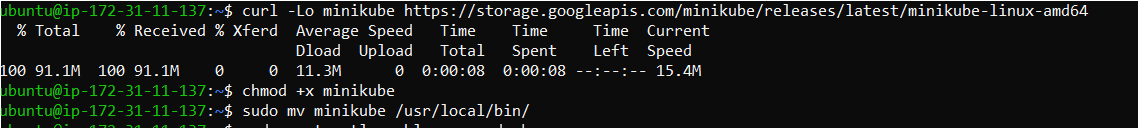
First, download the Minikube binary using curl:
curl -Lo minikube https://storage.googleapis.com/minikube/releases/latest/minikube-linux-amd64
chmod +x minikube
sudo mv minikube /usr/local/bin/
Step 5: Install kubectl
Download kubectl, which is a Kubernetes command-line tool.
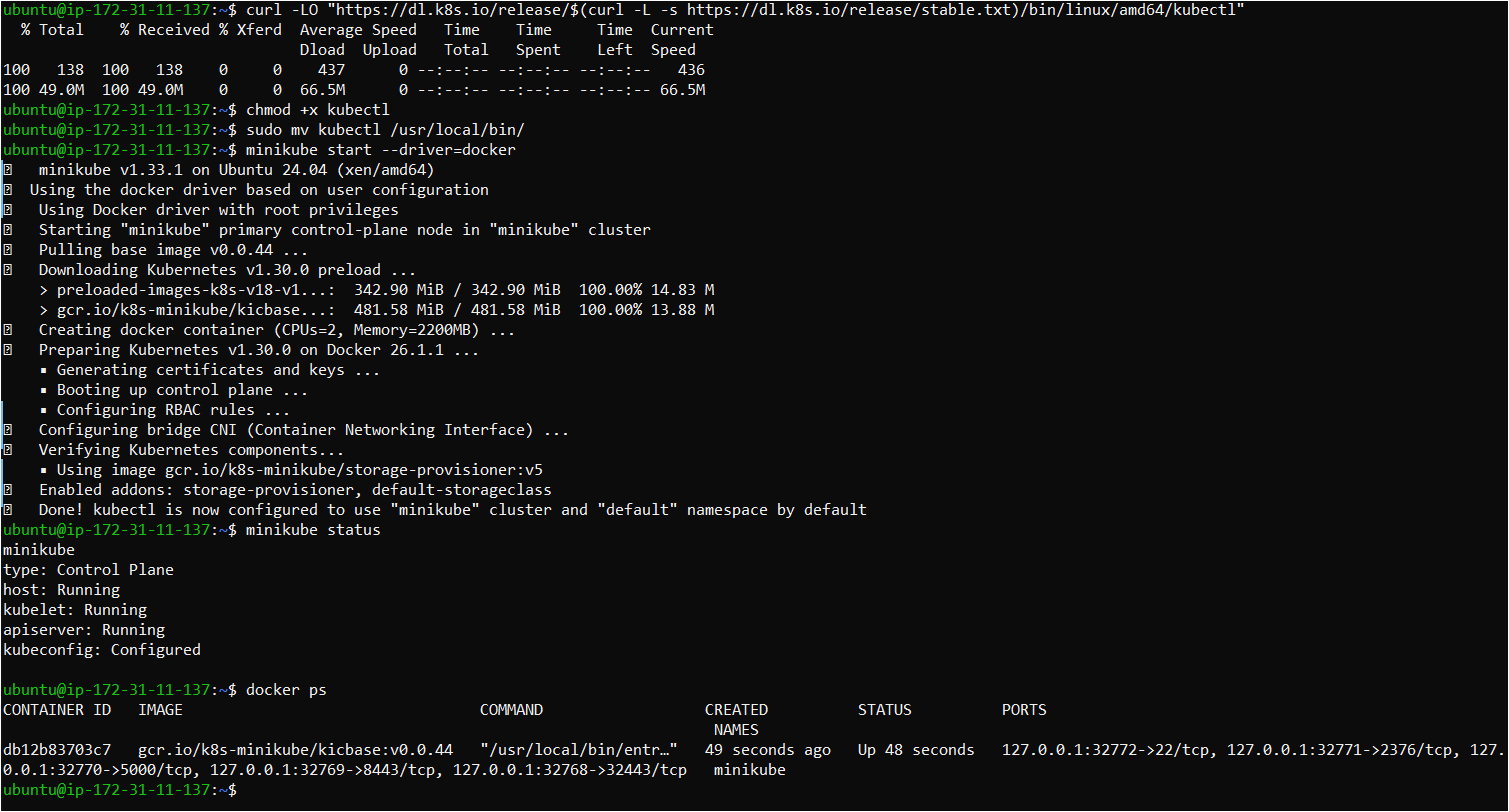
curl -LO "https://dl.k8s.io/release/$(curl -L -s https://dl.k8s.io/release/stable.txt)/bin/linux/amd64/kubectl"
chmod +x kubectl
sudo mv kubectl /usr/local/bin/
Step 6: Start Minikube
minikube start --driver=docker
minikube status
You can also use kubectl to interact with your cluster:
kubectl get nodes
Step 8: Stop Minikube
When you are done, you can stop the Minikube cluster with:
minikube stop
Optional: Delete Minikube Cluster
minikube delete
Setup Self-Hosted Kubernetes Cluster: Master & Worker Node Architecture
Kubeadm Installation Guide
This guide explains how to set up a Kubernetes cluster using kubeadm.
Pre-requisites
Ubuntu OS
sudo privileges
t2.medium instance type or higher
AWS Setup
Ensure all Instances are in the same security group.
Expose port 6443 in the Security group, so that worker nodes can join the cluster.
Execute on Both "Master" & "Worker Node"
#update the packages.
sudo apt-get update -y
# Create the .conf file to load the modules at bootup
cat <<EOF | sudo tee /etc/modules-load.d/k8s.conf
overlay
br_netfilter
EOF
sudo modprobe overlay
sudo modprobe br_netfilter
# sysctl params required by setup, params persist across reboots
cat <<EOF | sudo tee /etc/sysctl.d/k8s.conf
net.bridge.bridge-nf-call-iptables = 1
net.bridge.bridge-nf-call-ip6tables = 1
net.ipv4.ip_forward = 1
EOF
# Apply sysctl params without reboot
sudo sysctl --system
## Install CRIO Runtime
sudo apt-get update -y
sudo apt-get install -y software-properties-common curl apt-transport-https ca-certificates gpg
sudo curl -fsSL https://pkgs.k8s.io/addons:/cri-o:/prerelease:/main/deb/Release.key | sudo gpg --dearmor -o /etc/apt/keyrings/cri-o-apt-keyring.gpg
echo "deb [signed-by=/etc/apt/keyrings/cri-o-apt-keyring.gpg] https://pkgs.k8s.io/addons:/cri-o:/prerelease:/main/deb/ /" | sudo tee /etc/apt/sources.list.d/cri-o.list
sudo apt-get update -y
sudo apt-get install -y cri-o
sudo systemctl daemon-reload
sudo systemctl enable crio --now
sudo systemctl start crio.service
echo "CRI runtime installed successfully"
# Add Kubernetes APT repository and install required packages
curl -fsSL https://pkgs.k8s.io/core:/stable:/v1.29/deb/Release.key | sudo gpg --dearmor -o /etc/apt/keyrings/kubernetes-apt-keyring.gpg
echo 'deb [signed-by=/etc/apt/keyrings/kubernetes-apt-keyring.gpg] https://pkgs.k8s.io/core:/stable:/v1.29/deb/ /' | sudo tee /etc/apt/sources.list.d/kubernetes.list
sudo apt-get update -y
sudo apt-get install -y kubelet="1.29.0-*" kubectl="1.29.0-*" kubeadm="1.29.0-*"
sudo apt-get update -y
sudo apt-get install -y jq
sudo systemctl enable --now kubelet
sudo systemctl start kubelet
Execute ONLY on "Master Node"
sudo kubeadm config images pull
->If Multiple CRI endpoints on the host issue encountered<-
Solution:sudo kubeadm config images pull --cri-socket unix:///var/run/crio/crio.sock
sudo kubeadm init
->If Multiple CRI endpoints on the host issue encountered<-
Solution:sudo kubeadm init --cri-socket unix:///var/run/crio/crio.sock
mkdir -p "$HOME"/.kube
sudo cp -i /etc/kubernetes/admin.conf "$HOME"/.kube/config
sudo chown "$(id -u)":"$(id -g)" "$HOME"/.kube/config
#Network Plugin = calico
kubectl apply -f https://raw.githubusercontent.com/projectcalico/calico/v3.26.0/manifests/calico.yaml
kubeadm token create --print-join-command
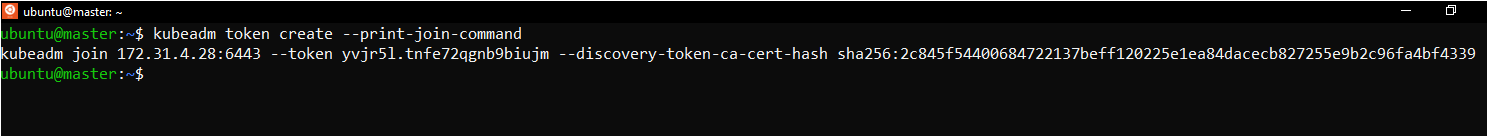
Execute on ALL of your Worker Node's
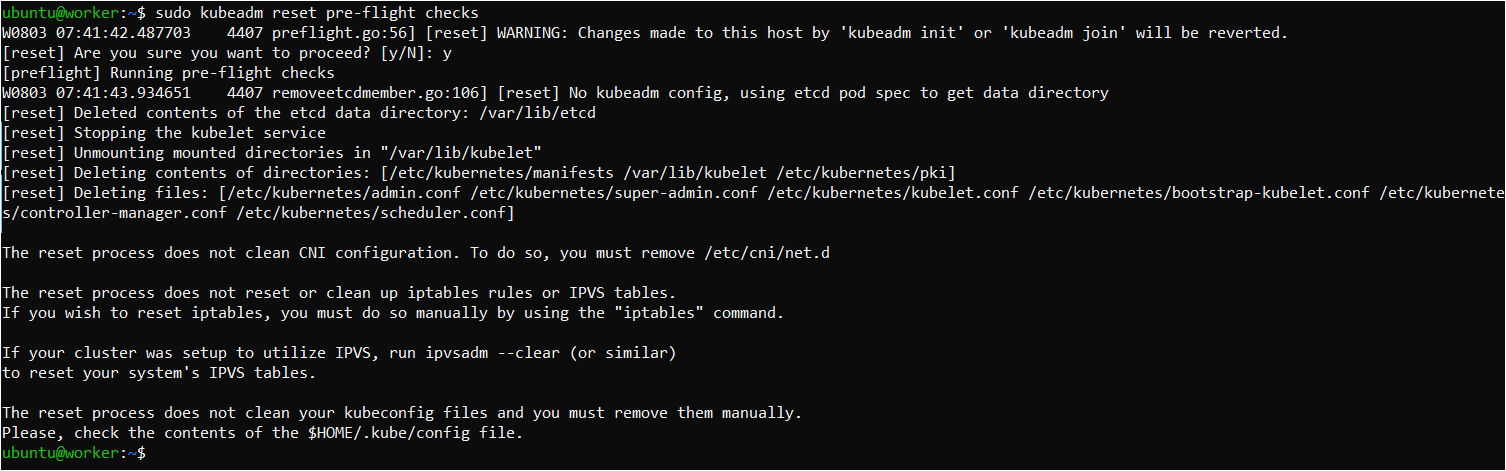
Perform pre-flight checks
sudo kubeadm reset pre-flight checks
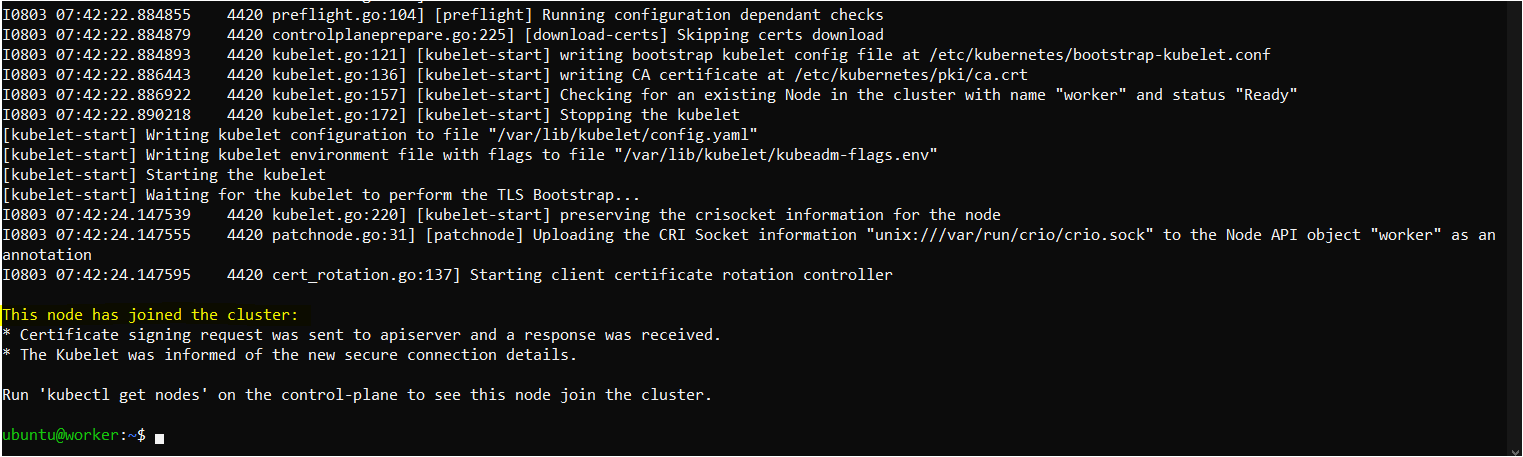
Paste the join command you got from the master node and append --v=5 at the end.
sudo your-token --v=5
#For Example: sudo kubeadm join 172.31.4.28:6443 --token yvjr5l.tnfe72qgnb9biujm --discovery-token-ca-cert-hash sha256:2c845f54400684722137beff120225e1ea84dacecb827255e9b2c96fa4bf4339 --v=5
If you have two Runtime Interface running in your servers, such as containerd Or crio` then use below commands:
Using Containerd:
sudo your-token --cri-socket unix:///var/run/containerd/containerd.sock --v=5
#Example: sudo kubeadm join 172.31.4.28:6443 --token yvjr5l.tnfe72qgnb9biujm --discovery-token-ca-cert-hash sha256:2c845f54400684722137beff120225e1ea84dacecb827255e9b2c96fa4bf4339 --cri-socket unix:///var/run/containerd/containerd.sock --v=5
Using CRIO:
sudo your-token --cri-socket unix:///var/run/crio/crio.sock --v=5
#Example: sudo kubeadm join 172.31.4.28:6443 --token yvjr5l.tnfe72qgnb9biujm --discovery-token-ca-cert-hash sha256:2c845f54400684722137beff120225e1ea84dacecb827255e9b2c96fa4bf4339 --cri-socket unix:///var/run/crio/crio.sock --v=5
To verify if all Kubernetes component containers and worker nodes on Master are created commands:
#:#Verify Containers created:
- For Containerd: sudo ctr -n k8s.io containers list
- List all tasks (running containers): sudo ctr -n k8s.io tasks list
##For CRI-O List all containers: sudo crictl ps -a
- List running containers: sudo crictl ps
## Verify Cluster Connection: **On Master Node:**
kubectl get nodes
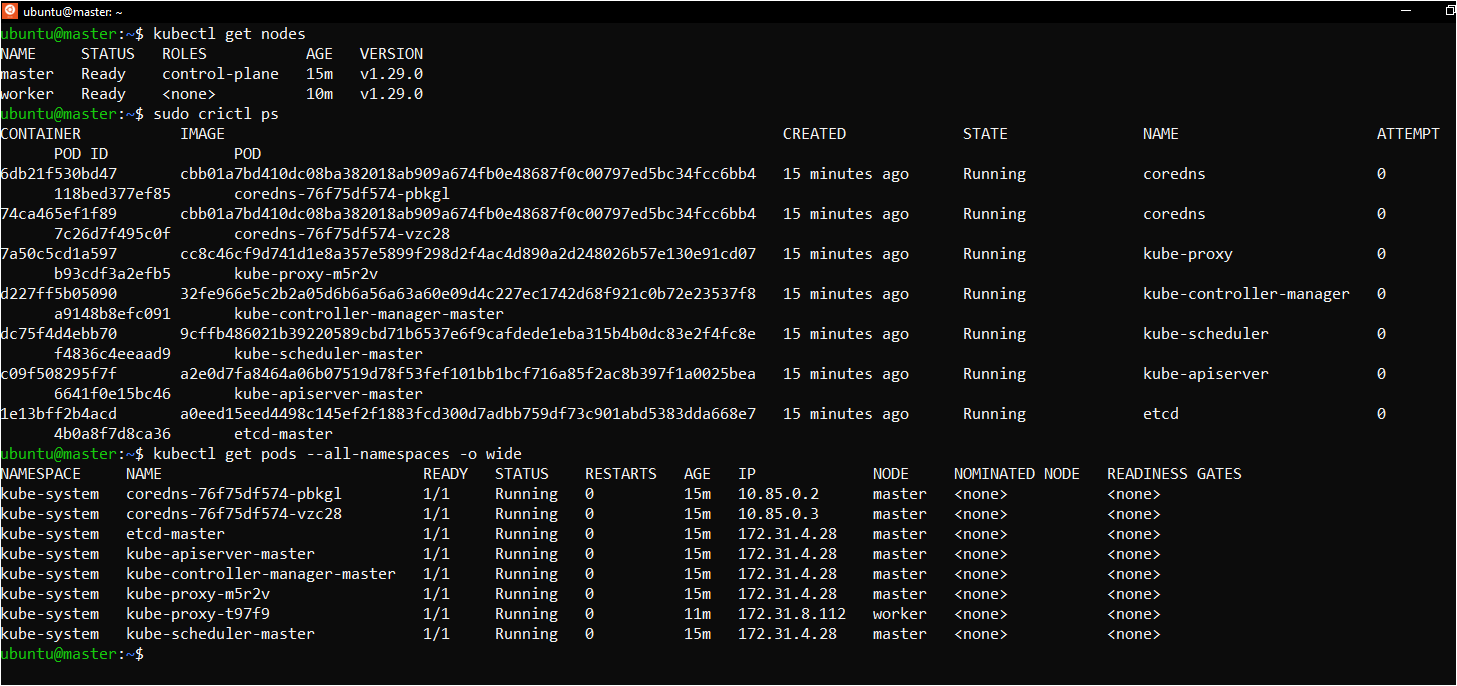
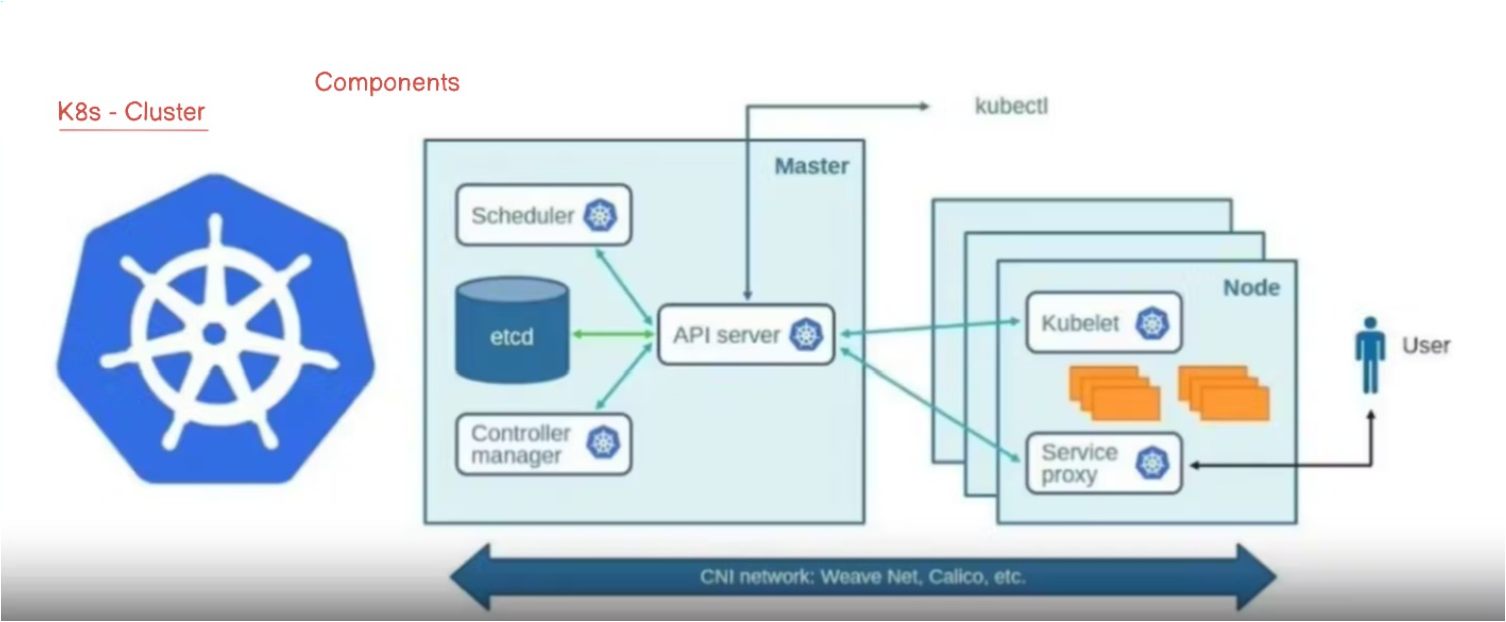
#This is a simplified overview of the components that make up Kubernetes architecture. Enjoy Kubernetes!#
Subscribe to my newsletter
Read articles from Sachin Yalagudkar directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
