How to Perform Mobile Static Analysis with Scrounger
 Nabeela
Nabeela
Howdy y’all,
In this article, we will explore how to perform static security analysis of mobile applications using a Metasploit-like framework called Scrounger.
Static Security Testing involves examining an application’s components without executing them, by analyzing the source code either manually or automatically. Frameworks like Scrounger help analyze the static information of an app using a single tool, thereby saving time and effort compared to using multiple tools and techniques.
It is touted to be the one stop framework for static analyzing android and iOS devices, having 2 modes; CLI and console.
Installation:
Before installing the framework, make sure all scripts and necessary dependencies are met to ensure smooth operation. The package requirements are listed on the Scrounger Github page
P.S: Issues have been observed when downloading Python dependencies like paramiko, apktool, and cryptography. If you use pip to install these dependencies, add the extra string --no-cache-dir.
Scrounger Console:
Before starting the framework, ensure the device is connected using adb. (For those unfamiliar, adb is a versatile command-line tool that lets you communicate with a device. It is used to bridge communication between an emulator instance (Android device) and the background running daemon process.)
After connecting, start the framework by typingscrounger-console
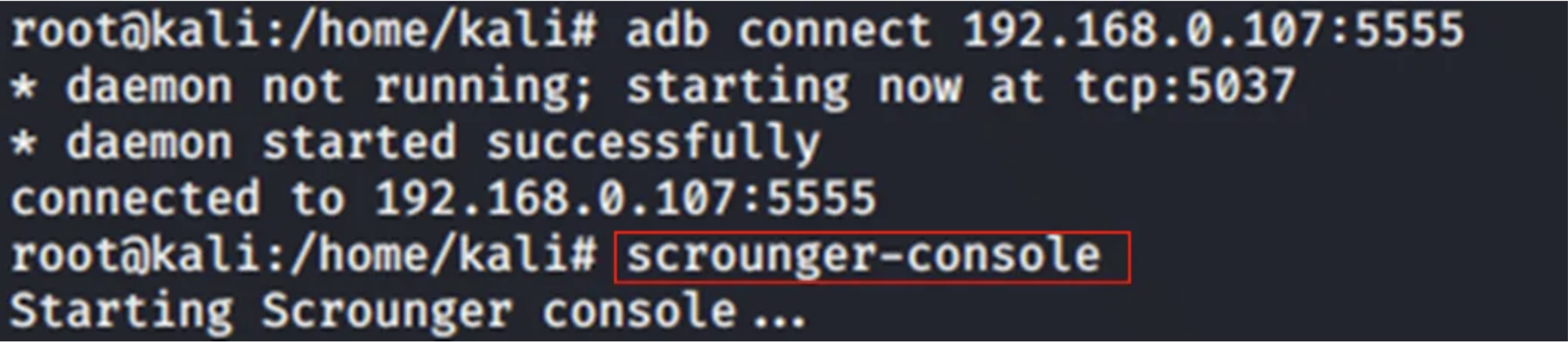
Next, assign an output filename, for example, “./final”. Since this parameter will be needed in multiple modules, it is recommended to set it as a global parameter to avoid entering the same details repeatedly. You can do this by typing
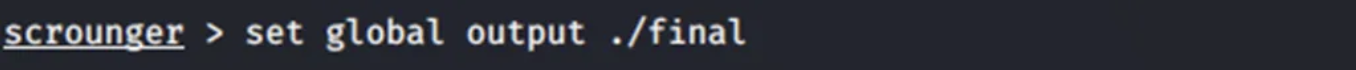
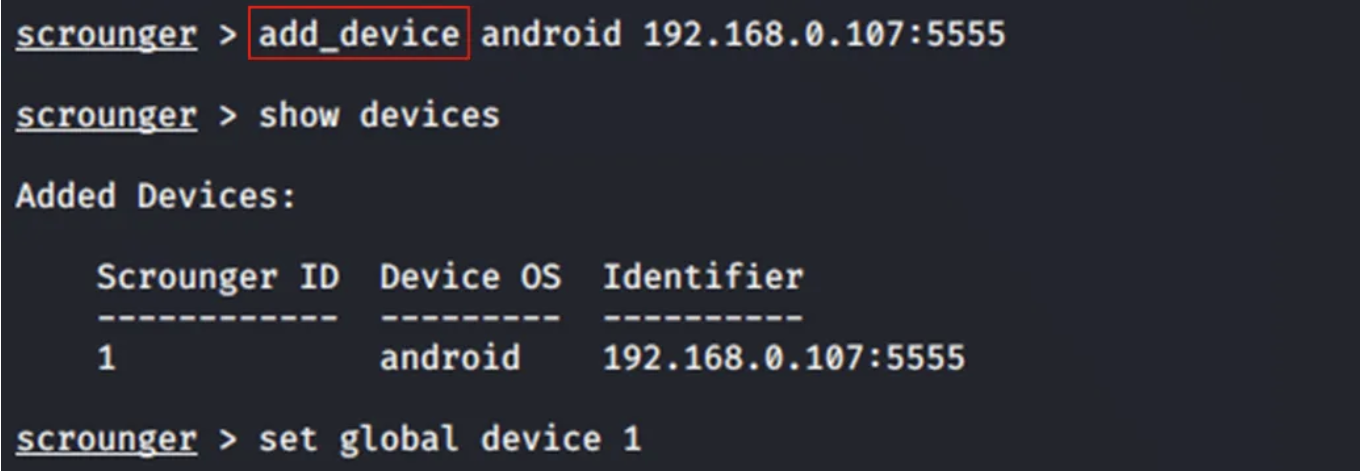
Next logical step is to add the device details in the framework.add_device android “IP of android device:port no”
To check the types of modules available for analyzing Android checks, typelist android
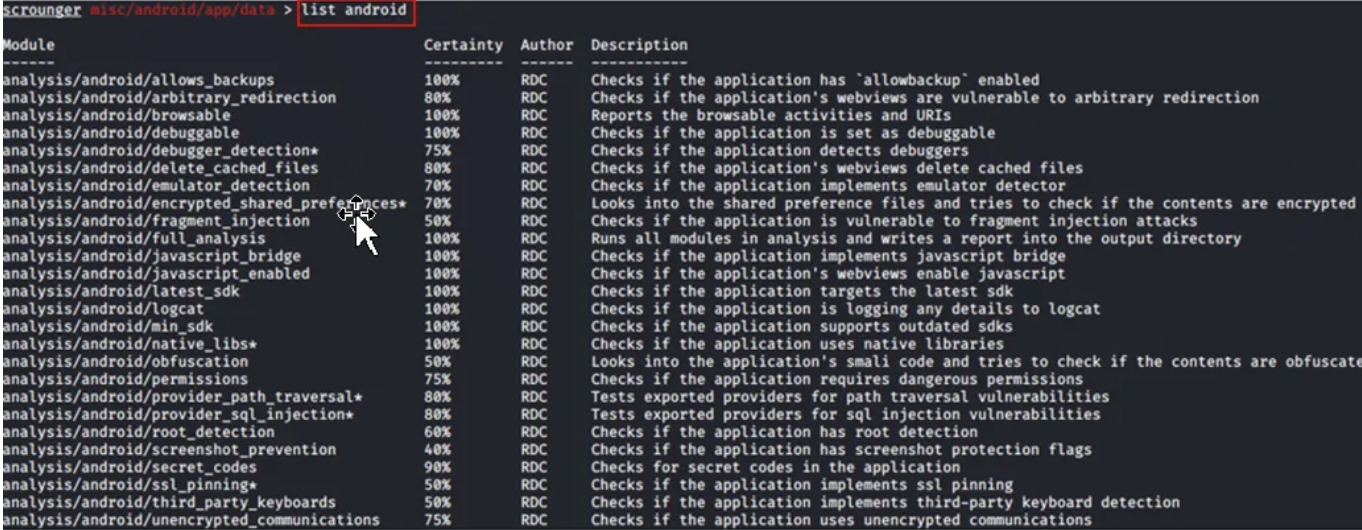
We will test a few console examples from the list above to understand how they work in more detail.
I. Decompiling an apk
In order to decompile an apk using this tool, type
use misc/android/decompile_apk
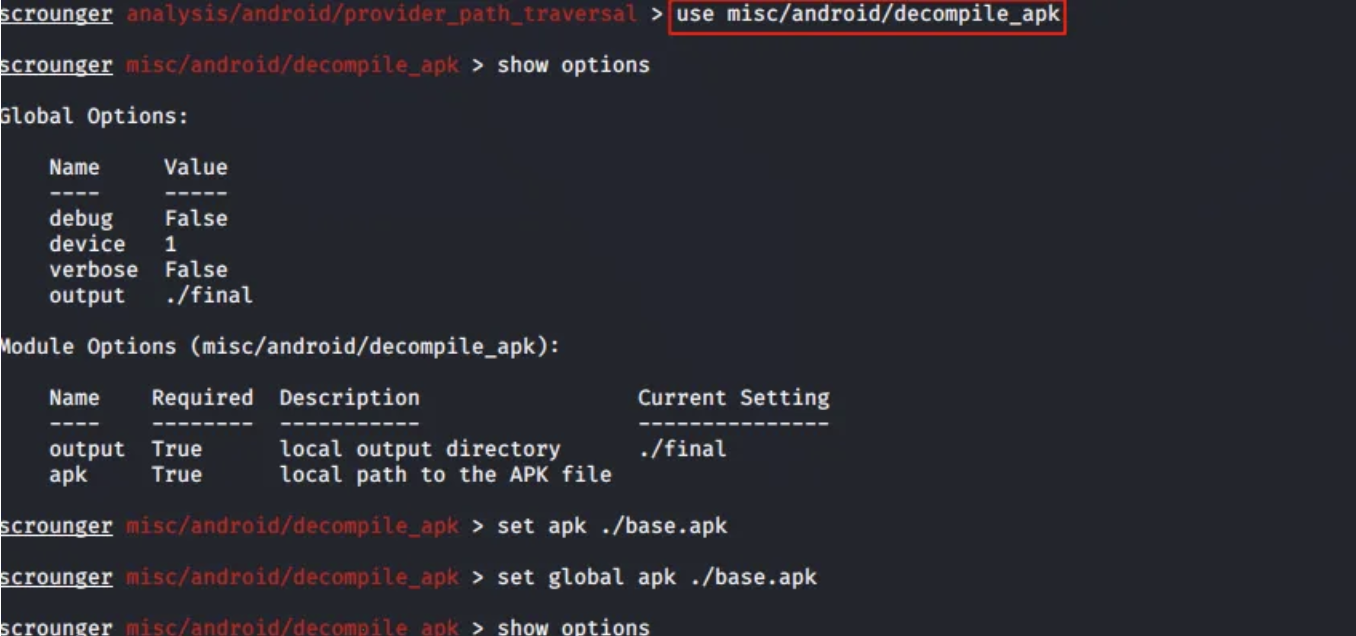
After selecting the module, type show options to see the additional details needed to run it. In this case, the apk base path was added and set as a global parameter. Since the device was already set as a global parameter, the device section in the results parameter is automatically set to 1.
After assigning and adding the necessary file paths and locations, type run to start the module exploit.
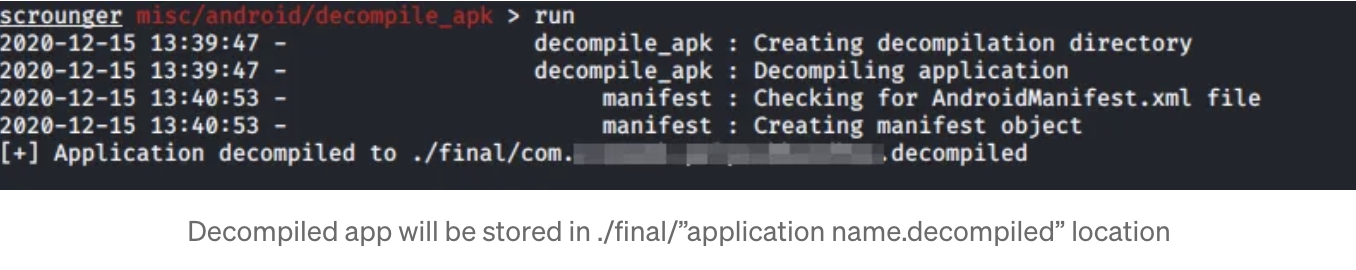
Helpful tip: Before running any other module, the first step should be to decompile the APK. Make sure to note the location of the decompiled APK, as it will be needed to test and run other modules in the framework.
II. Secret code checks.
Many iOS applications contain some form of jailbreak detection. Similarly, secret code checks can be tested by typinguse analysis/android/secret_codes
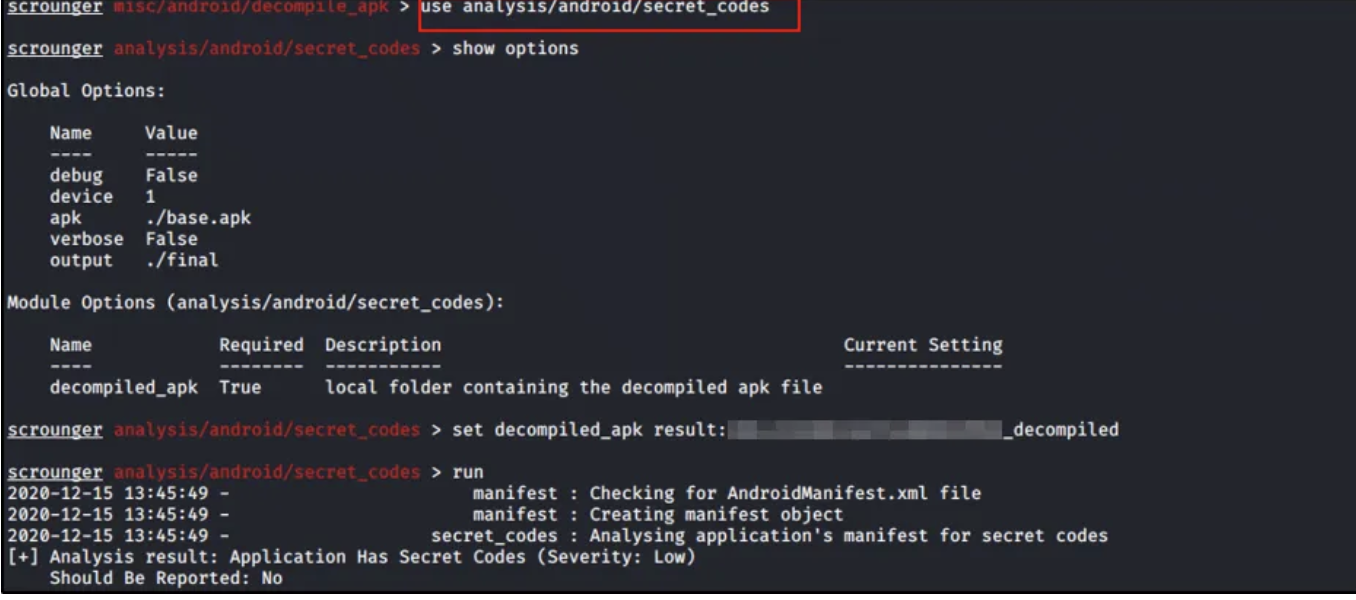
Before running a new module, type show options to verify the paths and locations required to run the module. In this case, an additional parameter named "decompiled_apk" is needed. You can easily get this by adding the decompiled location obtained earlier.
set decompiled_apk result:application_name_decompiled
III. Root Detection enabled check
This module will check if the target application has a root detection mechanism implemented in the APK. It will then display the severity of the vulnerability if it is present.
use analysis/android/root_detection
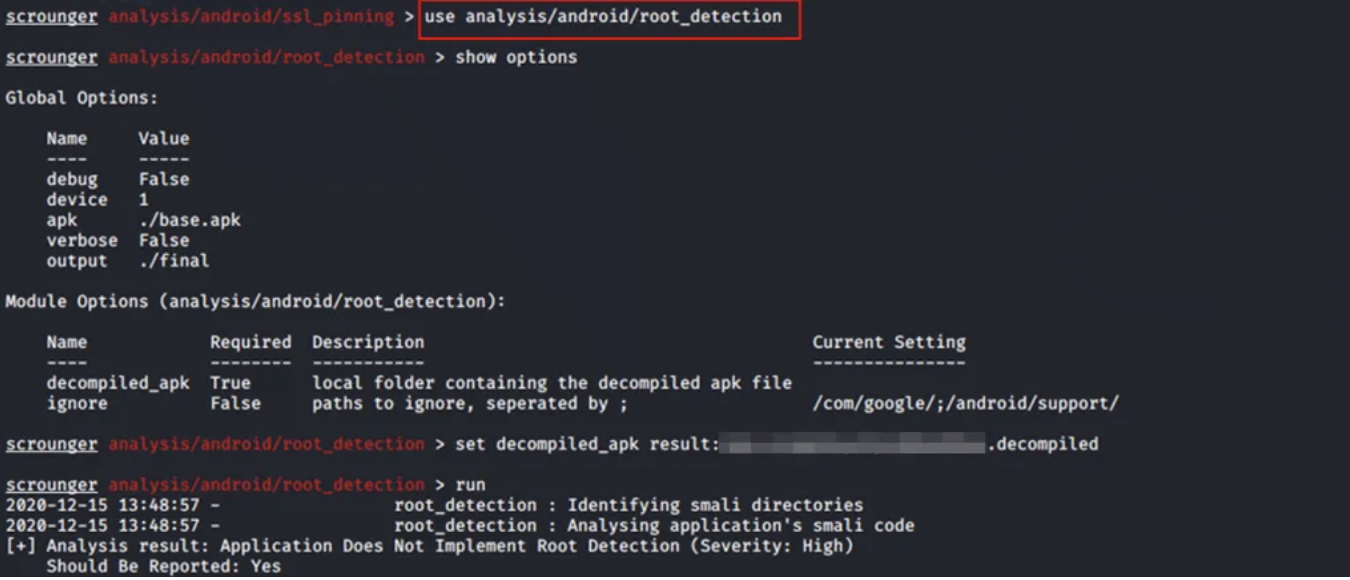
If you want to see the actual result of the application, based on which the framework provides a "Yes or No" result, type the following command in the terminal:
set global verbose true
IV. Dumping jar files.
Apart from performing security checks, you can also retrieve decompiled jar files from the APK by running the following command.
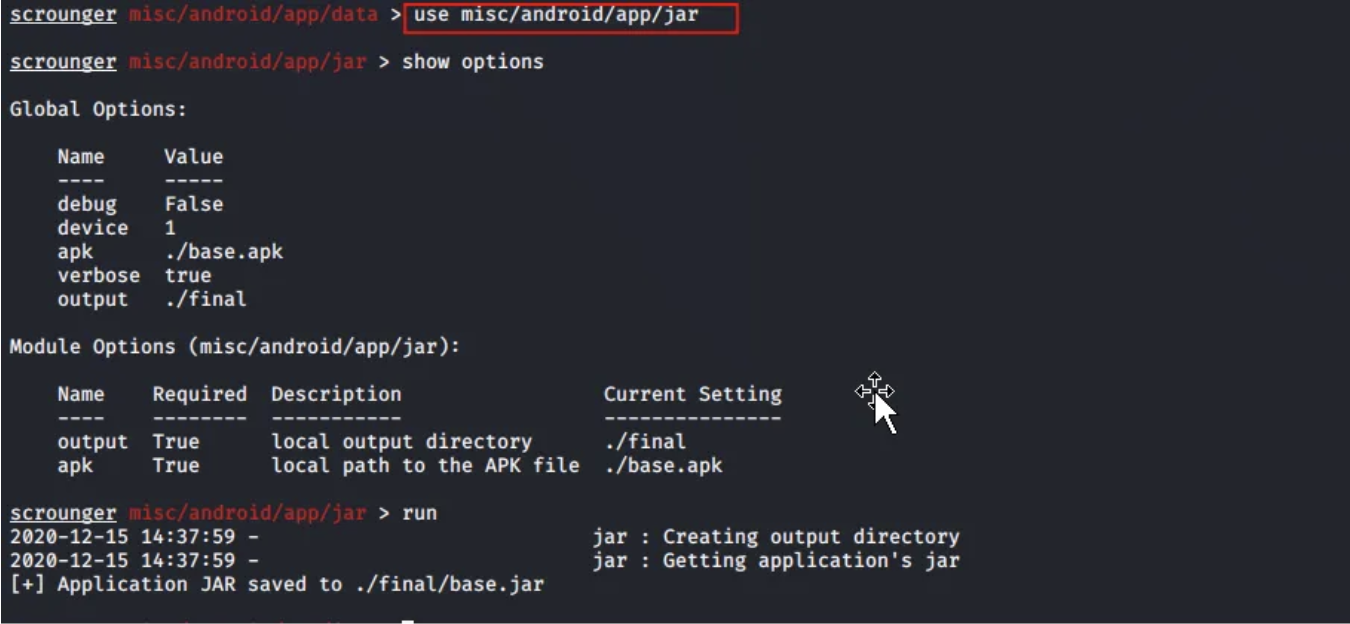
The above are just a few console examples to help you get started with analyzing the application using Scrounger.
I hope this article helped you understand and start your static code analysis using this framework.
Thank you for reading!
Subscribe to my newsletter
Read articles from Nabeela directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Nabeela
Nabeela
This is Nabeela, a seasoned security engineer from India, exploring and sharing insights. Specializing in Mobile and API Security, with occasional dives into other security realms.