Configure CIDAAS as an Identity Provider in Software AG Cloud for Single sign-on
 TECHcommunity_SAG
TECHcommunity_SAG
Product versions - {Software AG Cloud: 11.0.x and CIDaaS v3.100.14}
Introduction
Setting up SSO in the Software AG Cloud (SAG Cloud) with CIDAAS as the IDP is a process that requires some setup in both environments. It requires information from both environments, so it makes sense to open two browser windows from the start in order to follow the process.
The documentation related to the topic at hand is scattered across sites (CIDAAS and Software AG) and some information is seemingly mentioned only in passing without concrete examples - something that can lead one to misconfigure it and then have to spend time researching and fixing it.
With this short article, I hope to condense all relevant information into one location. The links under the “Useful links| Relevant resources” section contain all the background and further information. This article is meant to provide a cheat sheet but does not replace the official documentation in any way.
The process described here has been tested with the product versions listed above.
Pre-requisite
- You require a SAG Cloud tenant and a user with admin access to the tenant. (Free Trial Tenant will suffice)|
- You require access to a CIDAAS subscription (a free edition will suffice).
References
Manuals:
- SAG WM.IO SAG Cloud: Configure Identity Providers - Software AG Cloud
- CIDDAS Manuals: https://docs.cidaas.com/
Request Free Trials:
- SAG: Sign up - Software AG Cloud
- CIDAAS: Demo - cidaas by Widas ID
How to meet our goal: Setup CIDAAS as SSO provider for SAG webMethods.IO Cloud
A guide in 10 simple steps.
Create your CIDAAS Tenant
(can be a Free trial also from Europe's #1 Customer Identity & Access Management - cidaas)Create an “Application” (Apps) in CIDAAS: Provide a name and if you like link to your company LOGO as well as use your own cooperate colors etc.
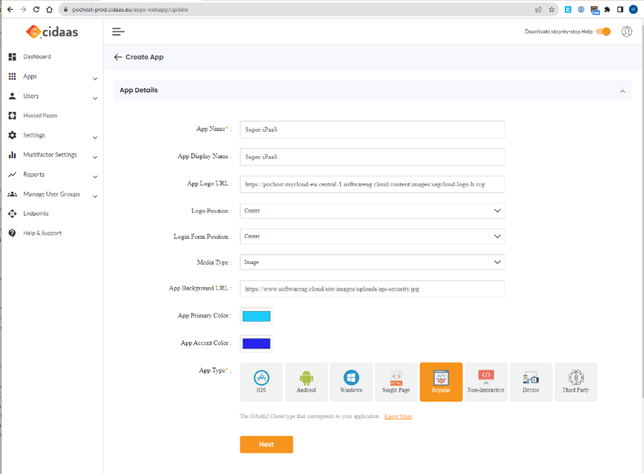
and select the 3 values we need to be exposed: email, profile and openid as scope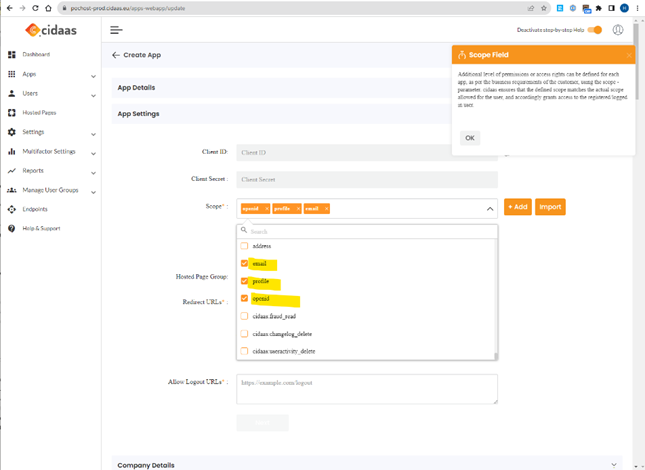
Create the “singleSignon” setup in your webMethods.IO tenant:
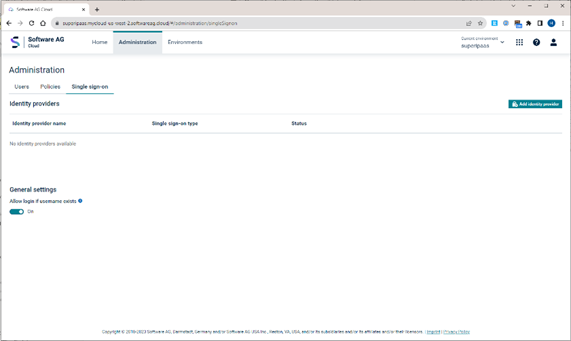
From there take the SAG IDM REDIRECT URL into the Application. Also, make sure you add your own CIDAAS system
e.g. https://pochost-prod.cidaas.eu/saml-srv/idp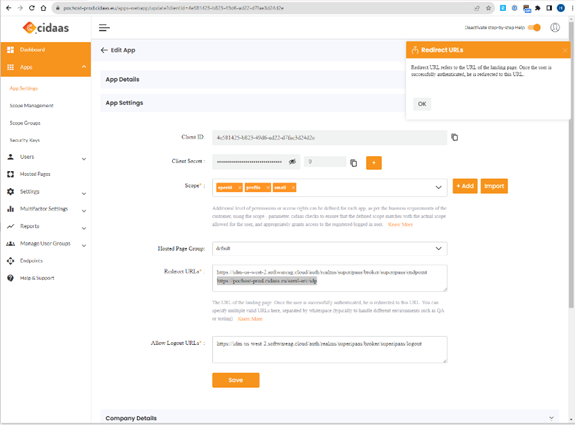
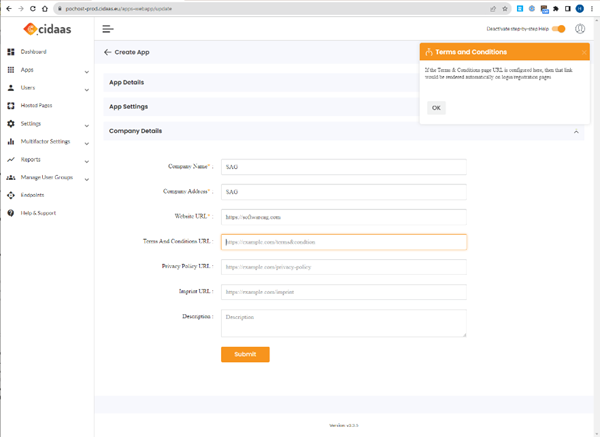
Complete some legal work (links, policy etc.) mandated by local data protection laws
Then this first part is done already:
Create the SAML IDP for your new Application and enable it.
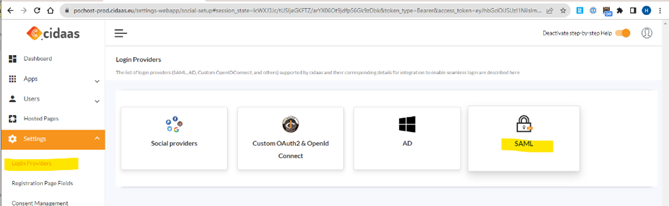
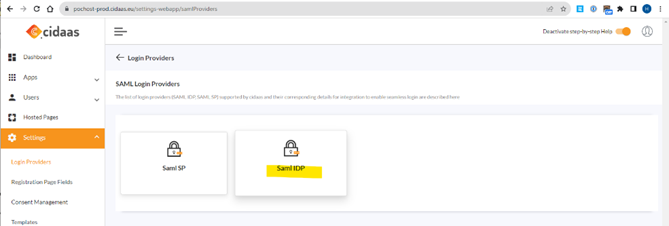
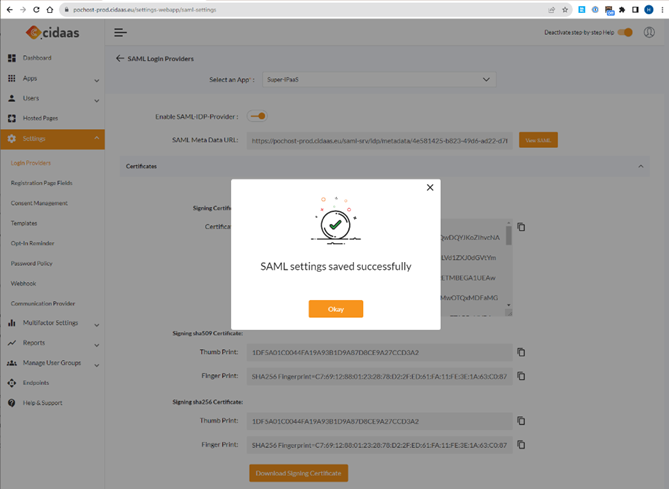
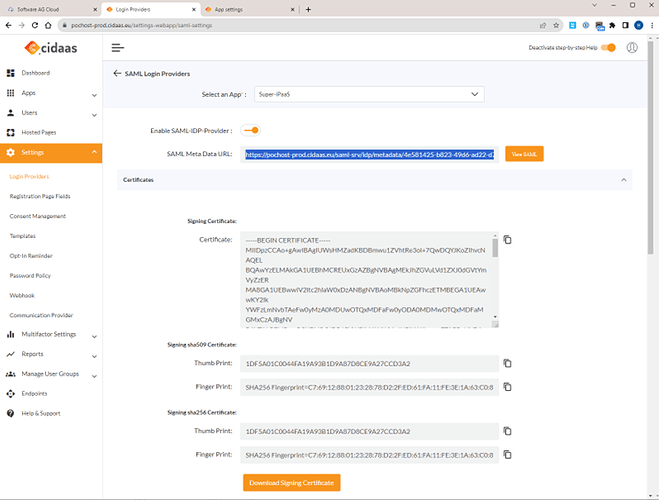
Take the META DATA link from the SAML provider back to SAG CLOUD IDM.
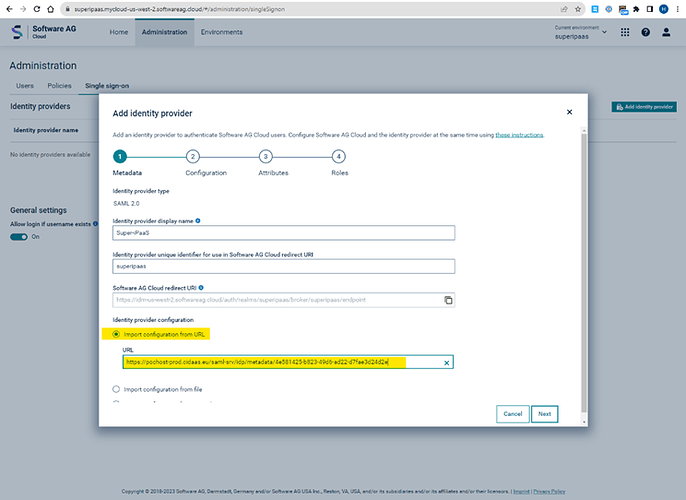
Complete the data mapping on SAG side:
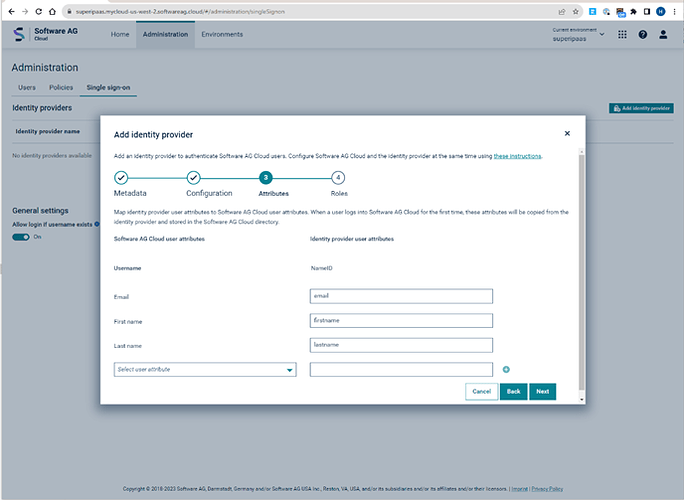 and assign roles to your needs, this is just a basic example
and assign roles to your needs, this is just a basic example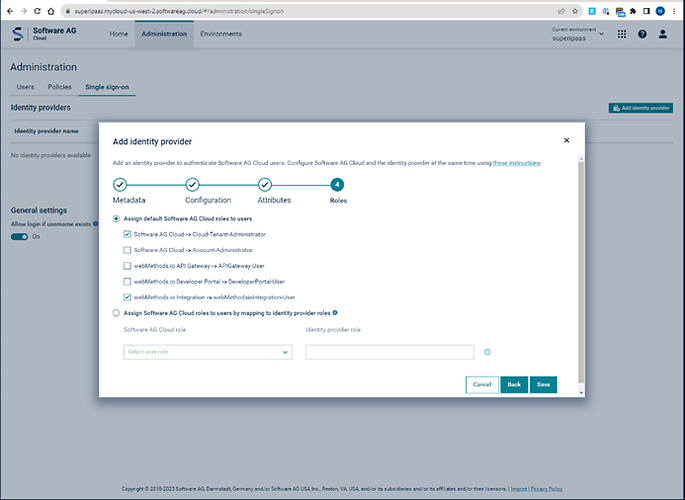 Finally, save it.
Finally, save it.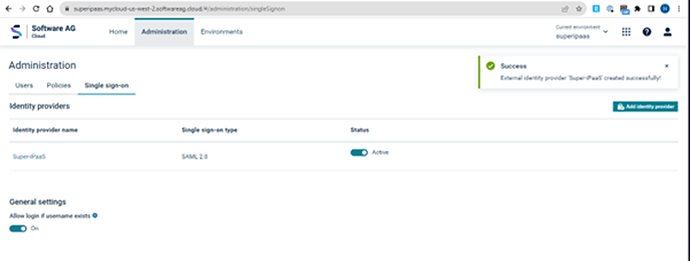
- Completing the backward link. Take the META DATA from the SAG IDM link at the bottom
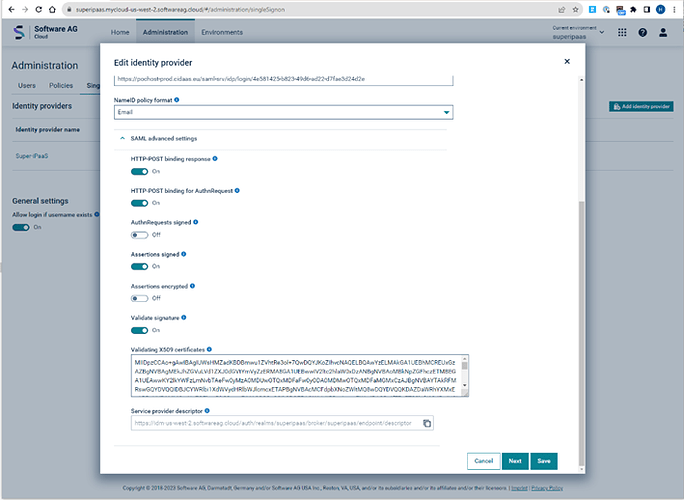 Open in the browser “view source” and copy this data into the CIDAAS Meta data field:
Open in the browser “view source” and copy this data into the CIDAAS Meta data field: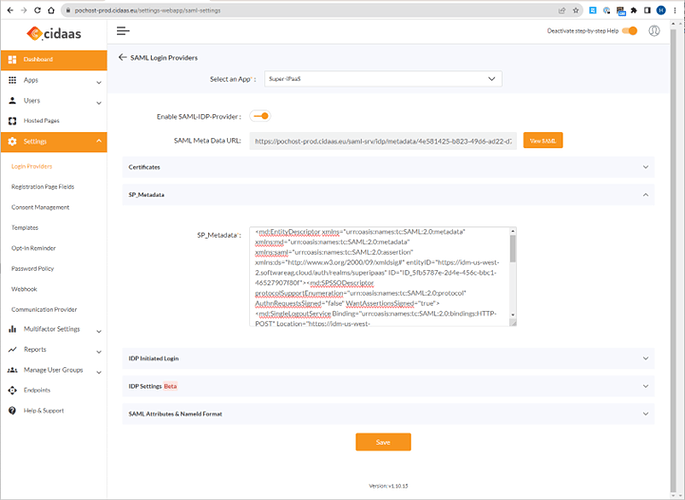
- Finalize the field mapping on the CIDAAS IDM side:
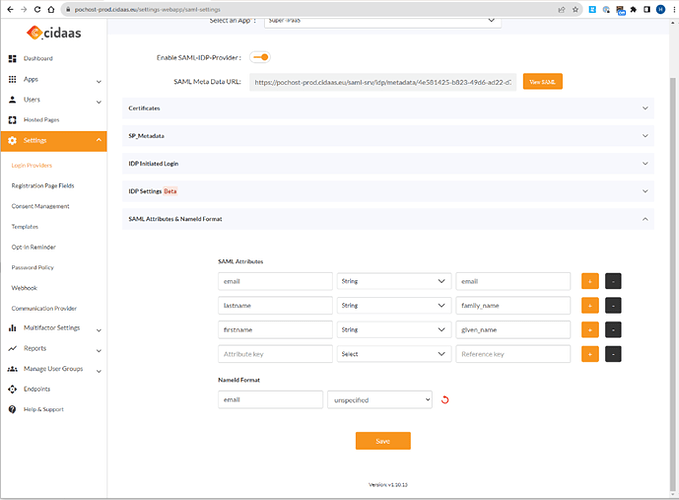 Save it and you are ready to go.
Save it and you are ready to go.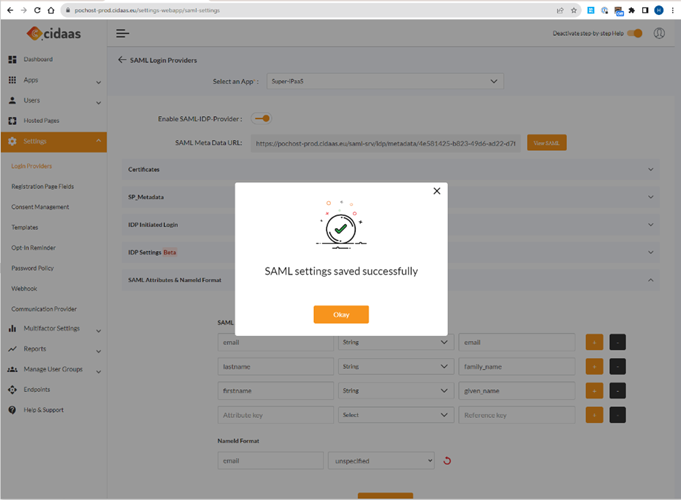
- Validate your setup from the SAG CLOUD login page.

Some more hints
a) CIDAAS allows you to enable 2FA, this is strongly recommended!
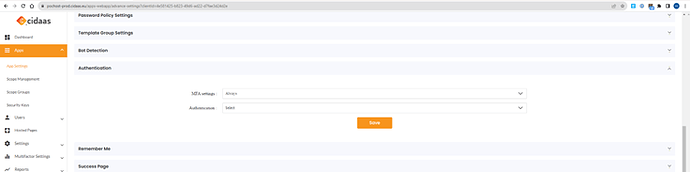
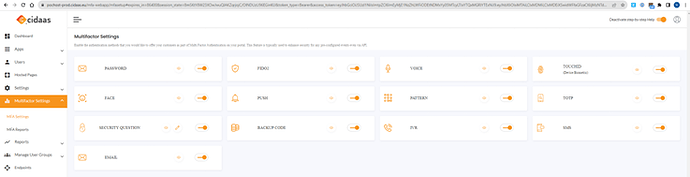
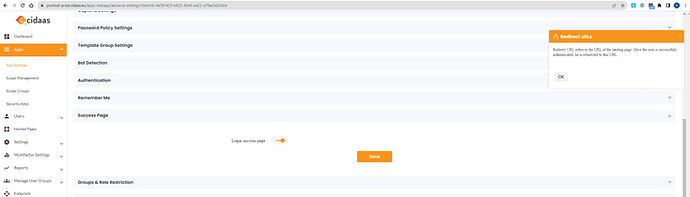
b) CIDAAS allows you to enable a “login success page”. This is also helpful.
This page as PDF:
Setup SAG CLOUD IDM with CIDAAS for SSO.pdf (1.5 MB)
Subscribe to my newsletter
Read articles from TECHcommunity_SAG directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

TECHcommunity_SAG
TECHcommunity_SAG
Discover, Share, and Collaborate with the Software AG Tech Community The Software AG Tech Community is your single best source for expert insights, getting the latest product updates, demos, trial downloads, documentation, code samples, videos and topical articles. But even more important, this community is tailored to meet your needs to improve productivity, accelerate development, solve problems, and achieve your goals. Join our dynamic group of users who rely on Software AG solutions every day, follow the link or you can even sign up and get access to Software AG's Developer Community. Thanks for stopping by, we hope to meet you soon.