Understanding Phishing Attacks: How to Recognize and Avoid Them
 Maxwell Antwi Bosiako
Maxwell Antwi Bosiako
In today's digital age, phishing attacks have become a prevalent threat to our online security. In the first quarter of 2024, online industries were most targeted by phishing attacks, with over 37% of these attacks on social media. These deceptive attempts to steal sensitive information can have negative consequences for individuals and businesses alike. These threats rise with notable events such as presidential campaigns, cultural festivals like music festivals or when public figures are launching a project or celebrating birthdays. Threat actors use these events as an opportunity to look for vulnerabilities to steal sensitive data or spread malware.
What is a Phishing Attack?
Phishing is a type of cybercrime where attackers act as legitimate entities to trick victims into revealing sensitive information such as passwords, credit card details, or social security numbers. According to the FBI's Internet Crime Complaint Center, phishing was the most common type of cybercrime in 2020, with over 241,342 reported incidents. Just in the first quarter of 2024, over 963,000 phishing sites were detected worldwide. These sites are usually used to make money or get access to systems.
How Phishing Works
The criminal gets contact information of the target organisation or individual and send phishing messages via SMS, E-mails or voice call. In most cases, attackers use tone of urgency, which trick victims to reply with sensitive data or click on a link. If the victim clicks on a link, they will be directed to a fake website that looks like original, designed for identity theft.
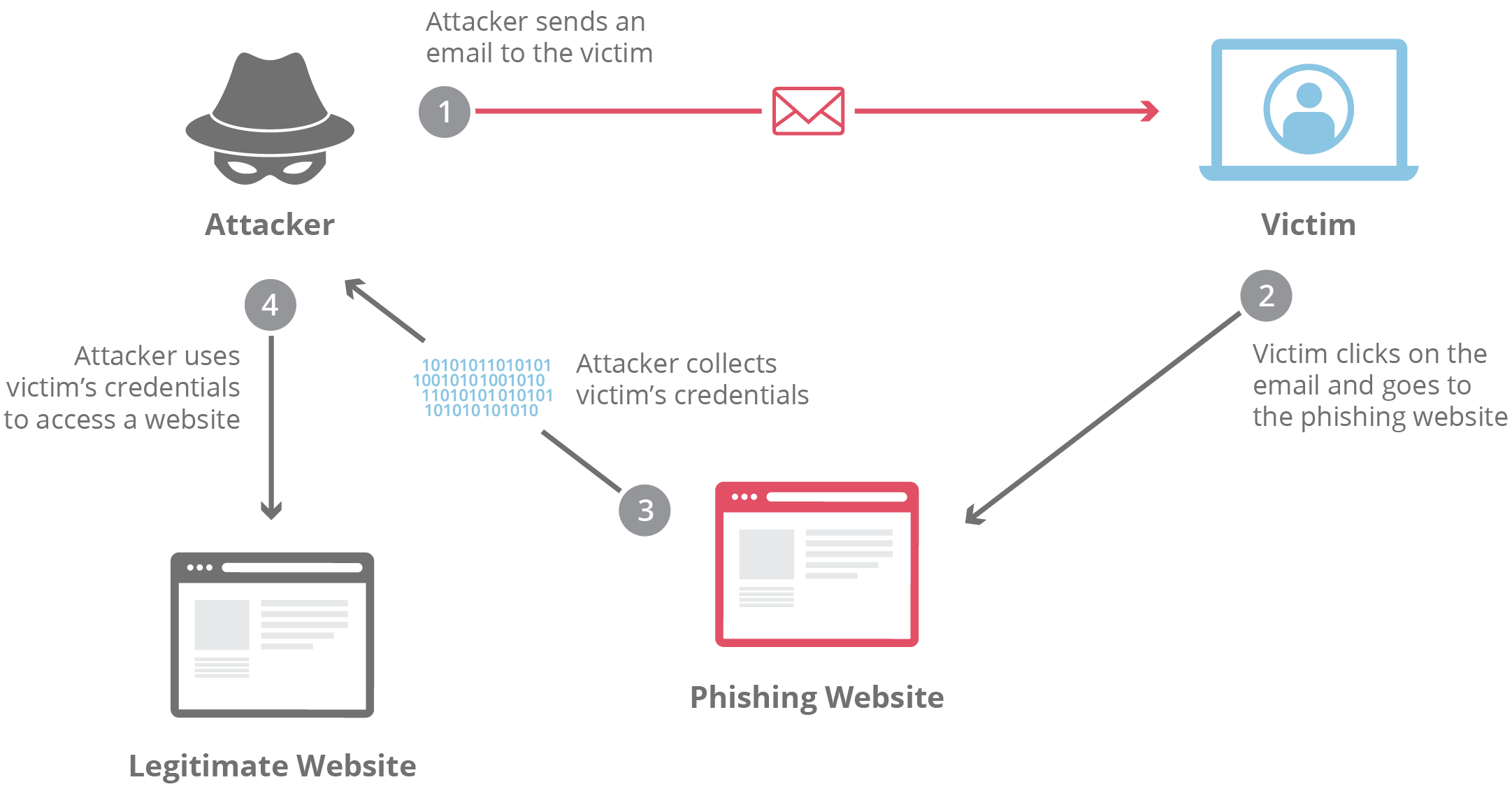
Common Types of Phishing Attacks
Phishing comes in various forms, each targeting victims through different channels:
Email phishing: The most common type, involving fraudulent emails.
Spear phishing: Targeted attacks on specific individuals or organizations.
Whaling: Attacks aimed at high-profile targets like executives and CEOs.
Smishing: Phishing via SMS text messages.
Vishing: Voice phishing using phone calls.
Search engine phishing: Creating fake websites to appear in search results.
Social media phishing: Using social platforms to spread scams.
How to Recognize Phishing Attempts
Be on the lookout for these red flags:
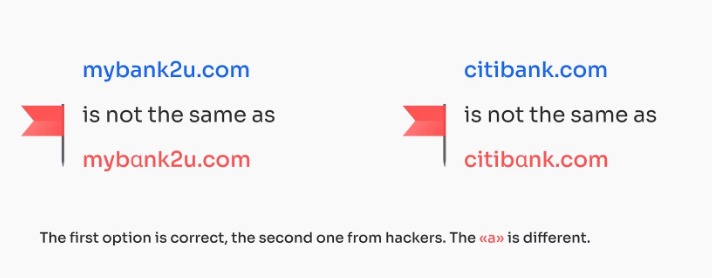
Carefully examine sender email addresses for slight misspellings.
Check for a sense of urgency or fear
Look for grammatical errors or odd phrasing
Hover over links before clicking to reveal the true destination. Ensure the link is at least https and not http.
Be cautious of unexpected attachments
Offering deals that seem “too good to be true”.
How to Protect Yourself Against Phishing
Use robust email filters and spam protection to automatically detect known spammers
Install anti-phishing browser extensions
Enable two-factor authentication on all accounts
Update security software regularly
Never click on suspicious links
Don't download unexpected attachments
Be cautious about sharing personal information online
Verify requests through official channels (e.g., calling your bank directly)
Conclusion
Phishing attacks continue to pose a significant threat in our interconnected world. By staying informed, vigilant, and following best practices, we can greatly reduce the risk of falling victim to these scams. Remember, if something seems suspicious, it probably is. Trust your instincts and always err on the side of caution when it comes to your personal information. There are many resources available online to help you stay informed about the latest phishing tactics. By working together, we can create a safer online environment for everyone.
Take a phishing quiz
"Think you're a phishing pro? Prove it! Can you spot the red flags? Share your quiz score and let's see who's the ultimate phishing fighter! Take the quiz: Google Phishing Quiz
Subscribe to my newsletter
Read articles from Maxwell Antwi Bosiako directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Maxwell Antwi Bosiako
Maxwell Antwi Bosiako
I am a cybersecurity enthusiast passionate about protecting digital landscapes. Join me as I explore and share the latest in cybersecurity news, trends, and educational content to help you stay informed and secure in the digital world.