This self-hosted password manager changes everything!
 Evan
Evan
Introduction
Google's Chrome browser is great, but I have some issues with it. The feature I used the most was the password manager. Combined with the iCloud keychain on my iOS and macOS devices, I had a haphazard system for saving my credentials. However, using multiple Google accounts for different activities and devices quickly became a disorganized mess.
Google's password manager is per account, and I often found myself searching for credentials in another account. This was especially annoying on iOS, where switching accounts required logging out and back in. Sometimes, none of my saved passwords worked because, in my hurry from the last login session, I failed to update them properly.
I kept telling myself I'd fix this one day, but it took some time before I finally found the right solution.
Vaultwarden as a self-hosted option
I wanted to self-host my password manager for security reasons. Sure, I had already let Google and Apple handle my sensitive data because it was easy and built-in (and hard to avoid these days quite honestly). But, I wasn't ready to trust another company like Nord or LastPass to do that for me, and I definitely wasn't interested in paying for this kind of service.
After some research, I found the Vaultwarden project on GitHub.
I was very pleased to see clear documentation and an active community of users. I found out that my Vaultwarden server would be hosted in a docker container. That server would communicate with Bitwarden clients via the implementation of its API so that I can access my passwords from any browser or mobile device. I would need to set up a Bitwarden account to use the clients (but Bitwarden will not see my sensitive data).
That sounded good to me. After reviewing the installation instructions, I went ahead and attempted to deploy this solution for myself.
Preparation for Installation
I planned on using one of my Linux Debian virtual instances for this project.
I didn't have Docker installed on that instance so I had to take care of that first.
Once I ensured that the Docker engine was working ...
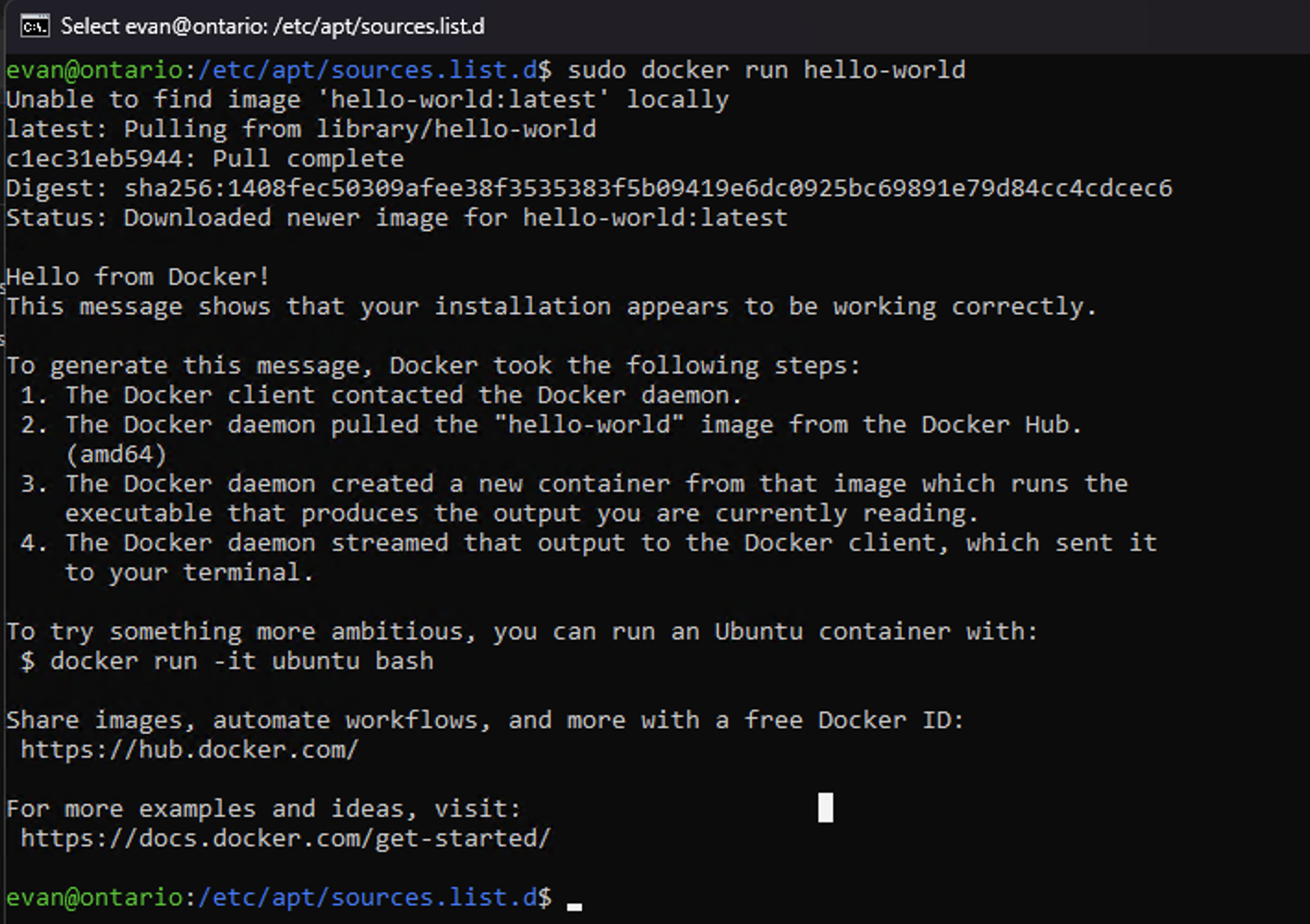
... it was time to set up the Vaultwarden container.
Vaultwarden installation
You can install Vaultwarden by running the docker command as specified in the Github. This will pull the container image and mount the volume for the container. The --restart unless-stopped option is a Docker restart policy that ensures a container is automatically restarted unless it is explicitly stopped by the user.
Vaultwarden will map to port 80 on the host machine.
docker pull vaultwarden/server:latest
docker run -d --name vaultwarden -v /vw-data/:/data/ --restart unless-stopped -p 80:80 vaultwarden/server:latest
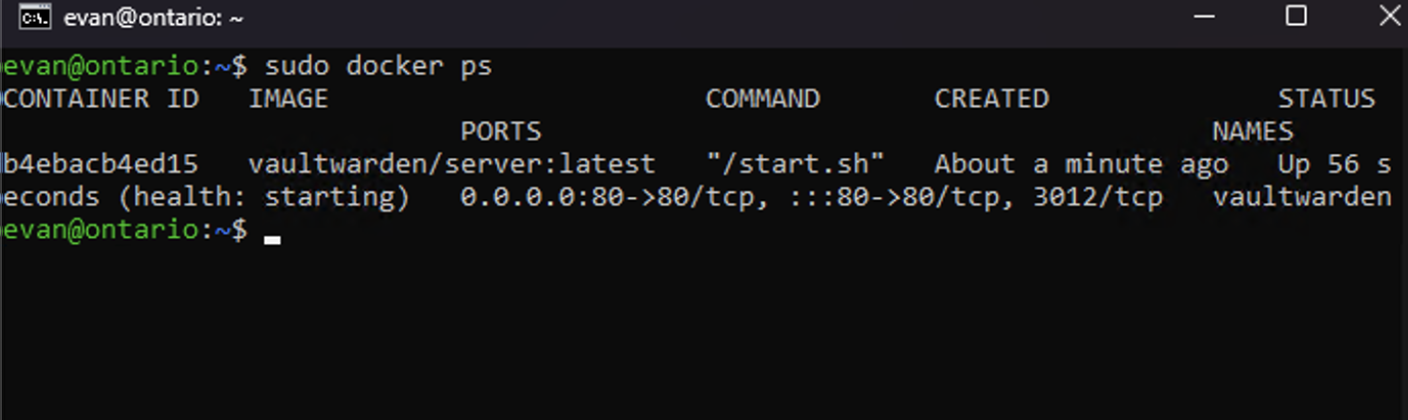
Running sudo docker ps showed that Vaultwarden was up and running.
Sure enough, when I went to port 80 on my host I saw the login screen.
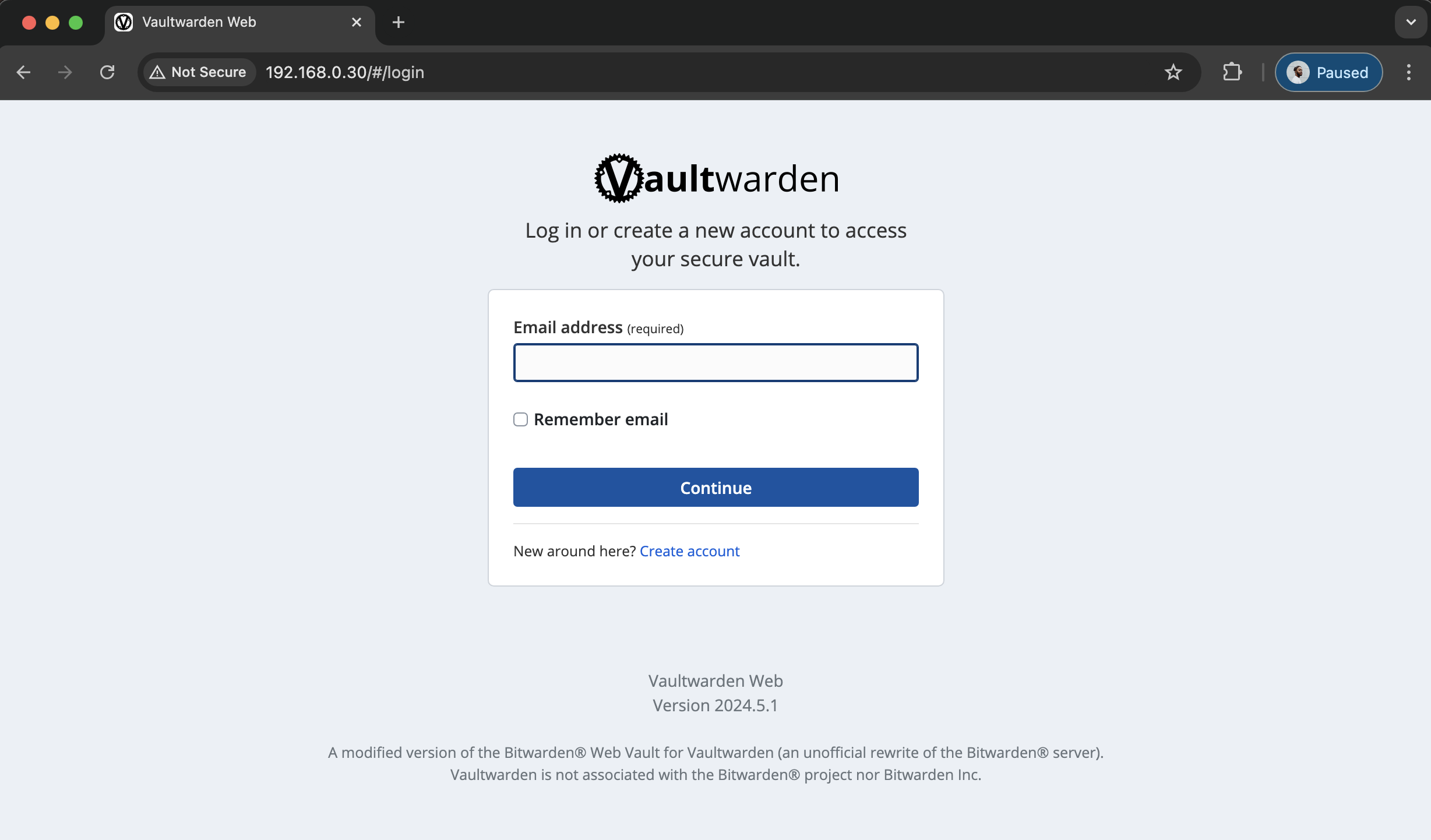
So far, so good.
Configuring an HTTPS proxy
I clicked on the option to create my Bitwarden account at the bottom. After entering my user info, I got an error.
"This browser requires HTTPS to use the web vault"
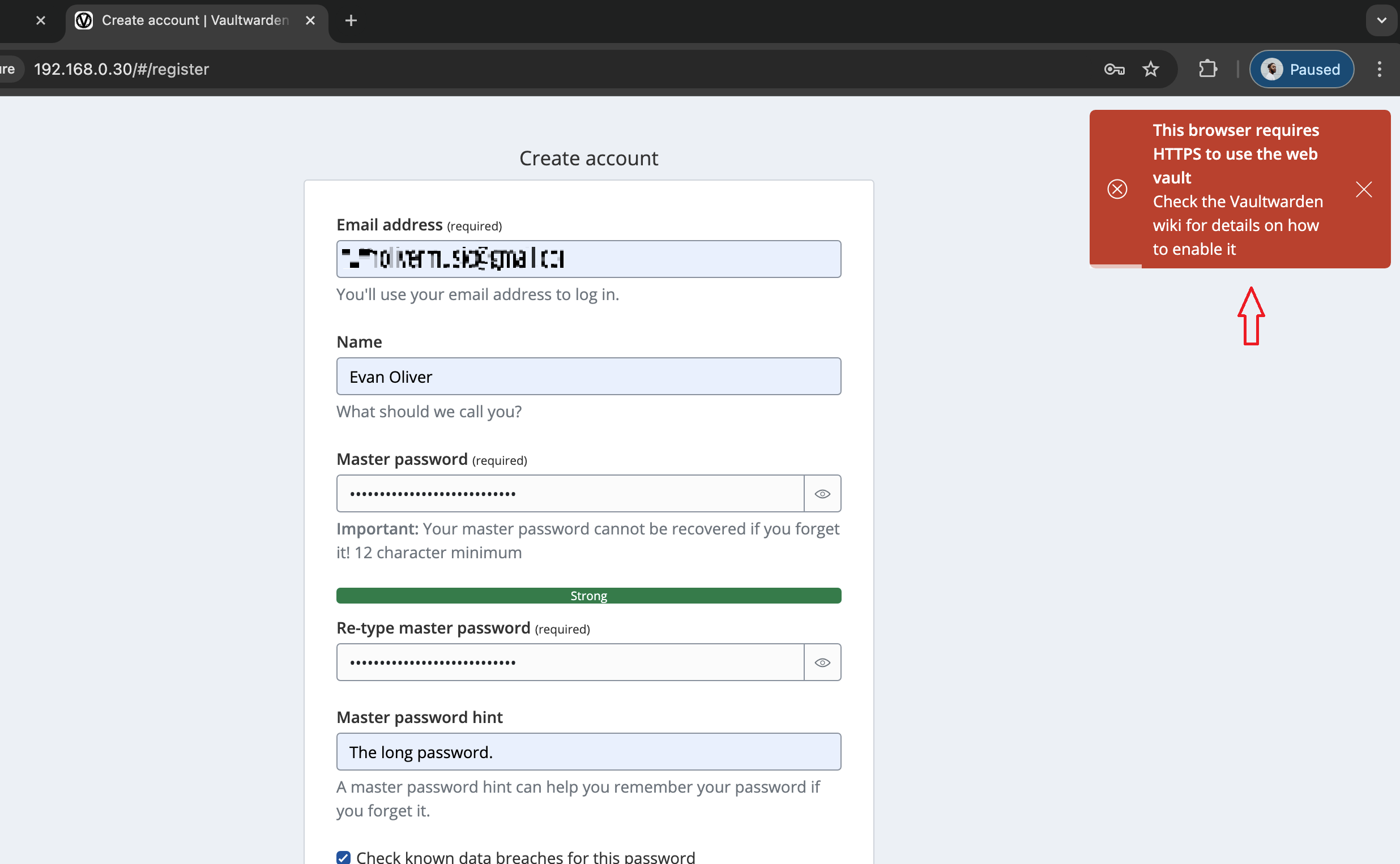
The wiki explains the error:
"For proper operation of vaultwarden, enablingHTTPSis pretty much required nowadays, since the Bitwarden web vault usesweb crypto APIsthat most browsers only make available in HTTPS contexts."
This explanation is alluding to the solution which is an HTTPS-to-HTTP reverse proxy. In fact, the wiki mentions services like CloudFlare for proxying the traffic. I went about this a bit differently.
I have set up a hub-and-spoke VPN with Tailscale that connects many of my devices in my homelab securely on my own mesh VPN. This was working great for remote access without exposing these devices to the public web. However, for this project, I would need to expose the container to web.
Tailscale Funnel works beautifully for this. The funnel allows you to route traffic from the wider internet to a local service running on a machine and there is a reverse proxy mode.
There are some important things you need to take care of first and if you want to use Funnel in Tailscale. I am not going to be covering Tailscale in this post. You can reference their excellent documentation (linked above) if you want to learn more.
I had already enabled Funnel on my node so I didn't need to do those steps again.
sudo tailscale funnel 3000 creates the funnel and you will see this output with the domain name if it the command is successful:
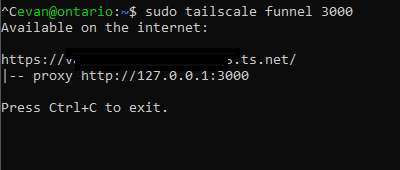
However, I later found out that the best way to do this is run the command with the
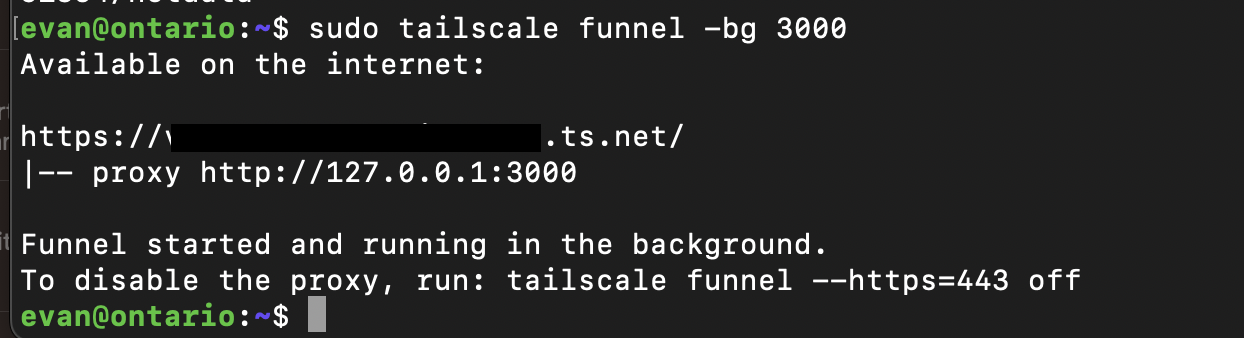
-bg option to ensure that the process will run in the background. Otherwise, sending SIGTERM (Ctrl + C) to recover your prompt in the shell will immediately close your funnel.
So I adjusted the command to sudo tailscale funnel -bg 3000
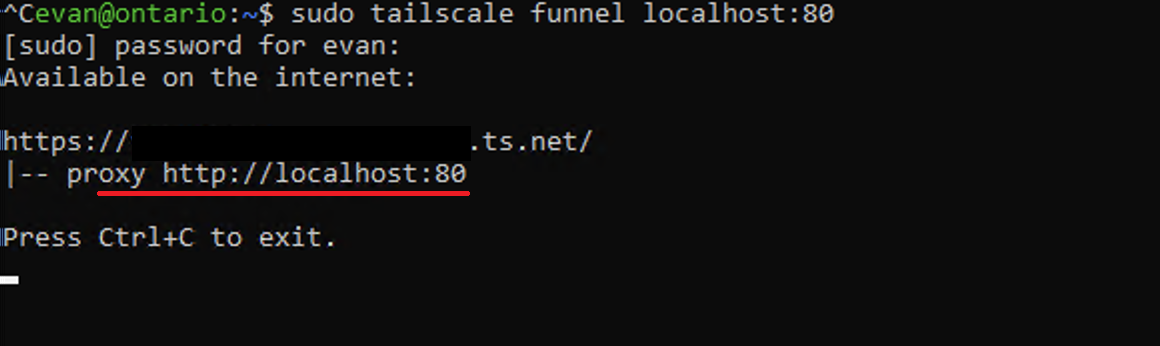
sudo tailscale funnel -bg localhost:80 enables the reverse proxy to the container.
With that done, I could successfully reach the container via HTTPS. I went on to create my Bitwarden account and view my empty vault.
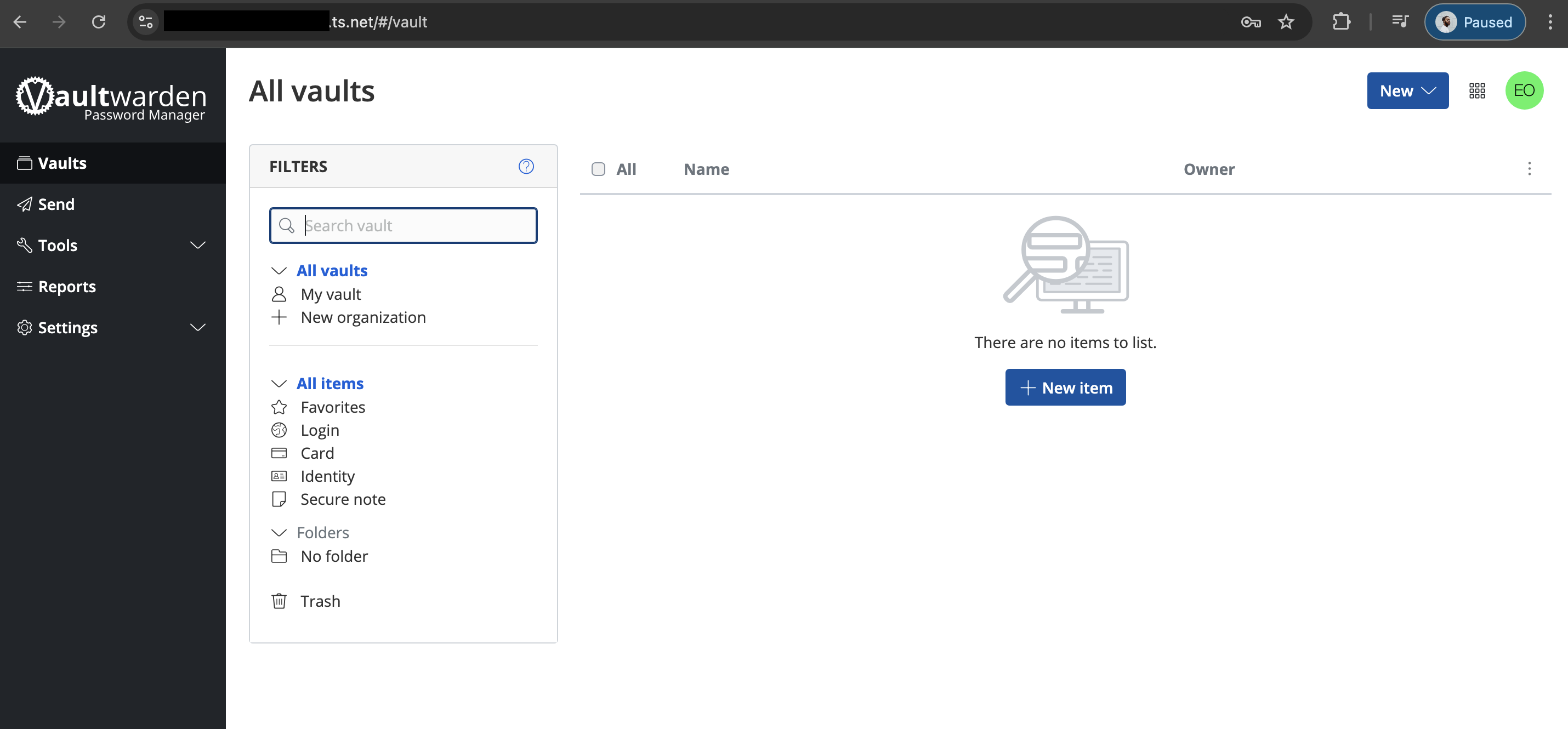
Success!
This is part 1 of the tutorial. In part 2, I will continue where I have left off with configuring and setting up the vault.
Coming soon...
Subscribe to my newsletter
Read articles from Evan directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Evan
Evan
Hi, I’m Evan — an engineer with a passion for automation, security, and building resilient cloud infrastructure. I spend a lot of time in the weeds solving real-world problems, whether that’s through client work or experiments in my homelab. This blog is where I document those lessons, not just to keep track of what I’ve learned, but to share practical insights that others in the field can apply too. My focus is on bridging the gap between security best practices and operational efficiency, using tools like Ansible, Docker, and AWS to make systems both secure and manageable. Whether you’re planning your infrastructure, hardening environments, or just learning the ropes, I hope these posts give you something useful to take with you. I’m always learning too, and this blog is as much about sharing the process as it is the results. Thanks for stopping by — let’s keep learning and building together.