How /etc/shadow Enhances Linux Security
 D V Shashidhar Reddy
D V Shashidhar Reddy
The /etc/shadow file in Linux plays a crucial role in system security by storing hashed passwords and related information for user accounts. Unlike the older the /etc/passwd file, which holds user account details in plain text, /etc/shadow ensures that sensitive password data remains protected from unauthorized access. Understanding the structure and function of the /etc/shadow file is essential for administrators and anyone interested in Linux security, as it provides an additional layer of defense against potential breaches and vulnerabilities.
In this article, we will delve into the structure of the /etc/shadow file, exploring its components and how it contributes to the overall security of Linux systems. By comprehending the mechanisms behind this file, you will gain insights into best practices for managing and securing user accounts in a Linux environment.
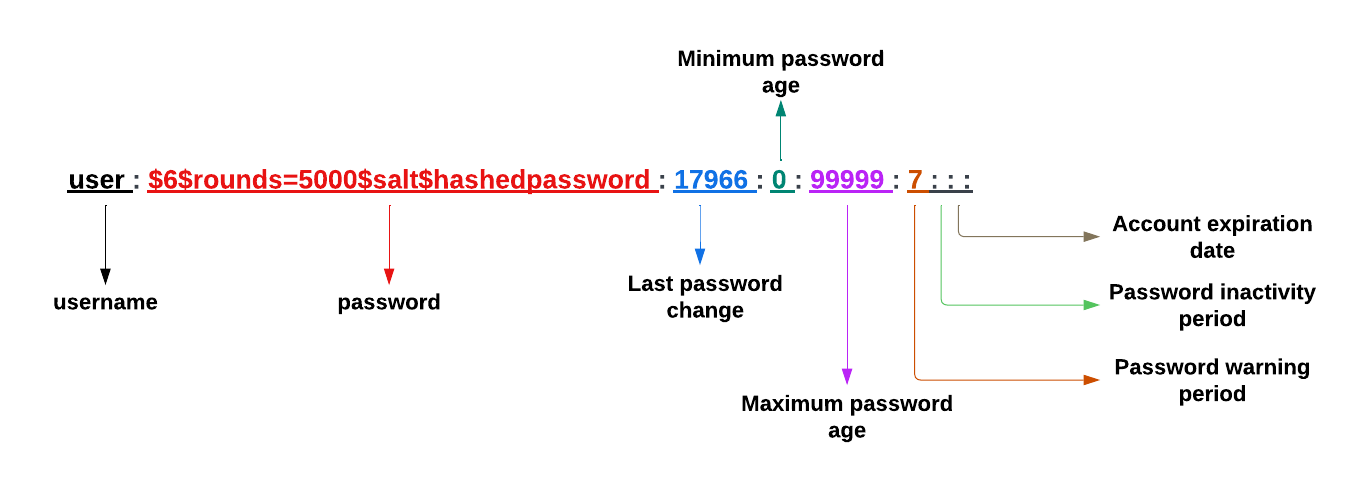
Fields in /etc/shadow:
The /etc/shadow file consists of several fields that are crucial for managing user account security in Linux. Each line in the file corresponds to a single user account and includes the following fields:
Username: This is the user's login name. It corresponds directly to the username found in the
/etc/passwdfile and serves as a unique identifier for each user account.Password: This field contains the user's hashed password. Rather than storing plain text passwords, which would be a major security risk, Linux uses hashing algorithms to encrypt passwords. If a password is not set, this field might be empty or contain a placeholder, such as
!or*, to indicate that no password is associated with the account.Last password change: This field records the last password change date. The date is typically represented as the number of days since January 1, 1970 (the Unix epoch). This information helps track how frequently passwords are updated, which is important for maintaining good security practices.
Minimum password age: This specifies the minimum number of days required between password changes. It ensures that users do not change their passwords too frequently, which could undermine the security policy by allowing users to cycle back to an old password.
Maximum password age: This field sets the maximum number of days a password remains valid. After this period, the user must change their password. This policy helps ensure that passwords are periodically updated, reducing the risk of compromised passwords being used indefinitely.
Password warning period: This indicates the number of days before the password expires that the user receives a warning to change their password. Advanced notice helps users prepare and avoid being locked out of their accounts unexpectedly.
Password inactivity period: This field defines the number of days of inactivity after a password expires before the account is locked. It provides a grace period for users who may have missed the password expiration warning but still need access to their account.
Account expiration date: This field specifies the date when the user account expires. Like the password change date, it is typically represented as the number of days since January 1, 1970. Account expiration is useful for temporary accounts or ensuring that inactive accounts do not remain open indefinitely.
Salt and Hashing:
In the context of password security, salt and hashing are critical techniques used to protect user passwords from being easily compromised.
Salt: A random value added to a password before hashing. It ensures that identical passwords have unique hashes, preventing attackers from using precomputed tables (rainbow tables) to crack passwords.
Hashing: Converts a password into a fixed-size string of characters. Hashing algorithms like SHA-256, bcrypt, or PBKDF2 create a unique hash for each password.
Example:
Without Salt:
- Two users with the same password ("password123") will have the same hash if no salt is used.
With Salt:
User 1’s salt:
salt1User 2’s salt:
salt2Combined strings:
salt1password123andsalt2password123The resulting hashes will be different, even with the same password.
In /etc/shadow:
The file stores the salt and hashed password. For example,
username:$6$salt$hashed_password:...Here,
$6$indicates the SHA-512 hashing algorithm,saltis the random value andhashed_passwordis the hashed result.By using salt and hashing, Linux systems enhance password security and protect against attacks.
Rainbow Table Attacks:
Rainbow table attacks are a method used by attackers to crack password hashes efficiently. A rainbow table is a precomputed table of hash values for a range of possible passwords, designed to reverse-engineer password hashes quickly.
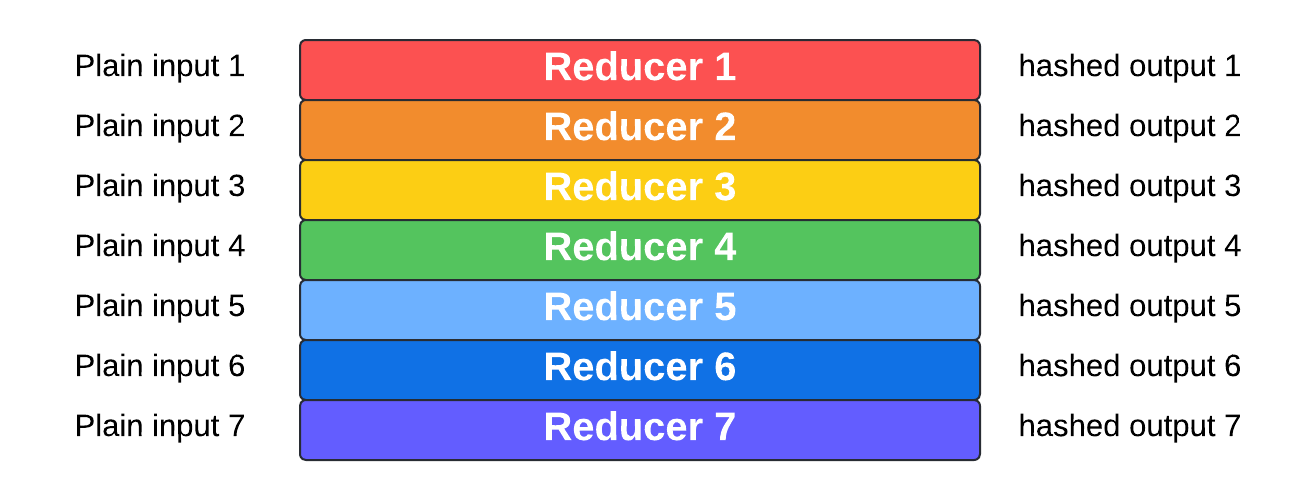
How It Works: Instead of performing a brute-force attack or using a dictionary attack (both of which can be time-consuming), attackers use a rainbow table to look up the hash of a password. The table contains hashes of numerous potential passwords, allowing attackers to quickly find a match for the hash they are trying to crack.
Advantages for Attackers: Rainbow tables simplify the process of cracking passwords by reducing the need for repeated hash calculations. Once a rainbow table is generated, attackers can use it to crack many passwords in a short amount of time, making it a popular tool for cybercriminals.
Countermeasures: To defend against rainbow table attacks, systems use techniques like salting. Adding a unique salt to each password before hashing ensures that even if two users have the same password, their hashes will be different. This makes precomputed rainbow tables ineffective, as attackers would need a separate table for each possible salt.
By understanding rainbow table attacks, you can better appreciate the importance of strong hashing practices and salting in securing password data.
How Salts Help:
Salts play a crucial role in enhancing password security by preventing attackers from effectively using rainbow tables. Here’s how they make a difference:
Without Salts:
When two users have the same password, their password hashes will be identical. For example, if both users set the password "password123", the hash stored in the
/etc/shadowfile will be the same for both users.This uniformity makes it easier for attackers to use rainbow tables, which are precomputed lists of hash values for common passwords. An attacker only needs to look up the hash in the rainbow table to find the original password.
With Salts:
Salts introduce a unique, random value added to each password before hashing. Even if two users have the same password, the unique salt ensures that their hashed values will be different.
For instance, if User 1 has a salt of
saltAand User 2 has a salt ofsaltB, their hashes for the same password "password123" will be different:saltA+password123andsaltB+password123, respectively.This approach makes rainbow table attacks impractical because attackers would need a separate rainbow table for each possible salt value. Given the vast number of possible salts, creating and maintaining such tables is infeasible.
Salting effectively mitigates the risk of rainbow table attacks by ensuring that even identical passwords result in different hashes. This added layer of security makes it significantly harder for attackers to compromise user passwords.
Pluggable Authentication Modules (PAM)
PAM is a flexible framework used in Linux systems to handle authentication tasks. It allows administrators to configure authentication policies and integrate various authentication methods, such as passwords, biometrics, or smart cards, into a unified system.
Purpose: PAM provides a modular approach to authentication, enabling the use of different authentication mechanisms without modifying the application code. This modularity helps streamline the management of authentication methods and enhances security by allowing easy updates and integration of new technologies.
Components: PAM consists of modules that can be plugged into the system to handle different authentication methods. Each module manages a specific aspect of the authentication process, such as verifying passwords or handling account expiration.
Configuration: PAM is configured through the
/etc/pam.d/directory, where system administrators can define authentication policies for various services and applications. Configuration files specify which PAM modules to use and in what order.
Example Scenario: User Authentication with PAM
User "sassy" logs in with their password. The /etc/shadow entry is:
sassy:$6$randomsalt$hashedpassword
Authentication Process:
PAM Reads /etc/shadow: PAM retrieves the salt (
randomsalt) and hashed password (hashedpassword).Combine and Hash: PAM combines the entered password with the salt, hashes the result, and compares it with the stored hash. If they match, "sassy" is authenticated.
Security Enhancements:
Salt: Ensures unique hashes for the same password, preventing easy attacks using rainbow tables.
Hashing: Protects passwords by storing only hashed values, not plain text.
Rainbow Table Attacks: Mitigated by unique salts, making precomputed tables ineffective.
PAM: Manages authentication by integrating these security measures with
/etc/shadow.
Conclusion
The /etc/shadow file is vital for securing Linux systems by storing hashed passwords and managing user account details. It ensures that sensitive credentials are protected from unauthorized access. Key features such as hashed passwords and password expiration dates help in maintaining secure authentication practices.
Key Takeaways:
Salts: Salts enhance security by adding a unique element to each password hash, effectively preventing rainbow table attacks and making password cracking more difficult for attackers.
Hashing Techniques: Proper hashing techniques convert passwords into secure, non-reversible hashes, safeguarding password data against unauthorized access.
PAM (Pluggable Authentication Modules): PAM provides a flexible framework for enforcing robust authentication policies. It allows for the integration of various authentication methods and policies tailored to specific organizational needs.
Best Practices:
Implement Salts and Hashing: Ensure that all passwords are salted and hashed to protect against common attack vectors.
Leverage PAM: Utilize PAM to enforce strong and configurable authentication policies across your Linux environment.
Regular Updates and Reviews: Continuously review and update authentication practices to keep up with evolving security threats.
For businesses managing diverse user bases, implementing these practices is crucial to mitigating risks associated with weak password security and protecting sensitive data. Adhering to these best practices will significantly enhance your system’s resilience against cyber threats.
Consult additional resources and guides to deepen your understanding of secure password management and strengthen protection for your Linux systems.
Further Reading
For those interested in exploring this topic further, the following resources provide in-depth information and practical guides:
Official Documentation:
Security Guides:
Tools and Utilities
☕ Enjoyed the content?
If my blog fueled your curiosity or helped you, consider fueling my caffeine addiction too! 😂
Subscribe to my newsletter
Read articles from D V Shashidhar Reddy directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

D V Shashidhar Reddy
D V Shashidhar Reddy
I'm a passionate DevOps Engineer with DevSecOps, Cloud, and SDLC expertise. I specialize in CI/CD pipelines, containerization, and infrastructure as code, and love sharing my knowledge.
