OWASP Top 10: A Deep Dive into Web Application Security
 Harshal Shah
Harshal Shah
The Open Web Application Security Project (OWASP) is a non-profit foundation dedicated to improving software security. One of its most influential initiatives is the OWASP Top 10, a regularly updated report outlining the most critical security risks for web applications. This blog will delve into the OWASP Top 10 for 2021, providing a comprehensive understanding of each risk, its potential impact, and mitigation strategies.
Understanding the OWASP Top 10
The OWASP Top 10 is a standard awareness document for developers and web application security. It represents a broad consensus about the most critical security risks to web applications.
While not an exhaustive list of all possible vulnerabilities, it serves as a valuable starting point for organizations to focus their security efforts. The 2021 update introduced significant changes, reflecting the evolving threat landscape.
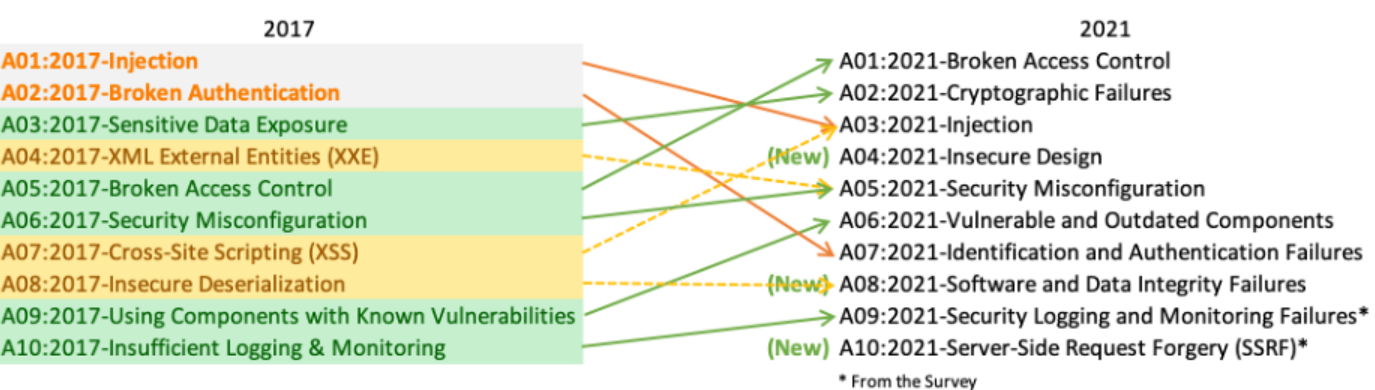
A01: Broken Access Control
Description: This occurs when applications improperly implement access control, allowing users to access resources they shouldn't.
Impact: Unauthorized data viewing, modification, or deletion; account takeover; escalation of privileges.
Example: A user can access another user's account by manipulating URL parameters or session cookies.
Mitigation: Implement strong authentication and authorization mechanisms, enforce the principle of least privilege, and conduct regular access control reviews.
A02: Cryptographic Failures
Description: Weak or misconfigured cryptographic algorithms, improper implementation, or key management errors can compromise data confidentiality, integrity, and availability.
Impact: Data breaches, unauthorized access, identity theft, and financial loss.
Example: Using weak encryption algorithms or storing cryptographic keys insecurely.
Mitigation: Use strong cryptographic algorithms, implement proper key management practices, and stay updated with cryptographic best practices.
A03: Injection
Description: Injection attacks occur when untrusted data is sent to an interpreter as part of a command or query.
Impact: Data loss, system damage, unauthorized access, and denial of service.
Example: SQL injection, where malicious code is inserted into SQL queries.
Mitigation: Employ input validation, output encoding, and parameterized queries to prevent injection attacks.
A04: Insecure Design
Description: Weak security requirements as part of the software development lifecycle can lead to system failures.
Impact: Data loss, system failures, unauthorized access, and denial of service.
Example: Building applications without considering security from the outset.
Mitigation: Conduct thorough threat modeling, adhere to secure coding practices, and perform regular security reviews.
A05: Security Misconfiguration
Description: Improper security configurations of software, frameworks, and hardware can lead to vulnerabilities.
Impact: Unauthorized access, data exposure, system instability, and denial of service.
Example: Default configurations on web servers or databases.
Mitigation: Follow security best practices, use up-to-date software and configurations, and regularly review and update system settings.
A06: Vulnerable and Outdated Components
Description: Using components with known vulnerabilities can expose applications to attacks.
Impact: Data breaches, unauthorized access, system compromise, and denial of service.
Example: Using outdated libraries with known vulnerabilities.
Mitigation: Maintain component inventories, regularly check for vulnerabilities, and update components promptly.
A07: Identification and Authentication Failures
Description: Weak identity and authentication mechanisms can lead to account takeover, impersonation, and unauthorized access.
Impact: Identity theft, financial loss, data breaches, and reputation damage.
Example: Weak password policies or lack of multi-factor authentication.
Mitigation: Implement strong password policies, use multi-factor authentication, and protect sensitive authentication data.
A08: Software and Data Integrity Failures
Description: Insufficient integrity checks can lead to data corruption, unauthorized modification, and system failures.
Impact: Data loss, system failures, and loss of trust.
Example: Not verifying the integrity of downloaded software or data.
Mitigation: Implement data integrity checks, use digital signatures, and regularly verify data integrity.
A09: Security Logging and Monitoring Failures
Description: Inadequate logging and monitoring can hinder threat detection and incident response.
Impact: Delayed incident response, loss of sensitive data, and reputational damage.
Example: Lack of detailed logs or ineffective log analysis.
Mitigation: Implement robust logging and monitoring, analyze logs regularly, and have incident response plans in place.
A10: Server-Side Request Forgery (SSRF)
Description: SSRF attacks occur when an application processes untrusted data as a URL without validating it.
Impact: Internal system exposure, data exfiltration, and denial of service.
Example: An application allowing users to input arbitrary URLs that are then processed by the server.
Mitigation: Validate all user-supplied URLs, restrict network access, and implement input validation.
Mitigating the OWASP Top 10
Addressing the OWASP Top 10 requires a multifaceted approach:
Secure by Design: Incorporate security into the development lifecycle from the outset.
Developer Training: Educate developers about secure coding practices and the OWASP Top 10.
Code Reviews: Conduct regular code reviews to identify vulnerabilities.
Security Testing: Employ various testing methodologies (penetration testing, vulnerability scanning, etc.)
Incident Response: Develop a comprehensive incident response plan.
Stay Updated: Keep up with the latest security trends and updates to the OWASP Top 10.
Benefits of the OWASP Top 10
The OWASP Top 10 is a valuable resource for organizations aiming to enhance their web application security. It offers numerous benefits, including:
Prioritization of Security Risks
Focus on critical issues: By highlighting the most prevalent and impactful vulnerabilities, the OWASP Top 10 helps organizations allocate resources effectively.
Risk-based approach: It enables a structured approach to security, allowing organizations to prioritize mitigation efforts based on the potential impact of each risk.
Improved Security Posture
Reduced vulnerabilities: Addressing the OWASP Top 10 can significantly reduce the number of vulnerabilities in web applications.
Enhanced resilience: A more secure application is better equipped to withstand attacks and protect sensitive data.
Compliance: Many regulatory frameworks reference the OWASP Top 10, making it a valuable tool for achieving compliance.
Enhanced Reputation and Trust
Customer confidence: Demonstrating a commitment to security can build trust with customers and partners.
Brand protection: Preventing data breaches and other security incidents safeguards the organization's reputation.
Cost Reduction
Preventative measures: Addressing vulnerabilities early in the development lifecycle is often more cost-effective than remediating issues after deployment.
Reduced incident response costs: A strong security posture can minimize the financial impact of security breaches.
Industry Standard Adoption
Common language: The OWASP Top 10 provides a common language for discussing web application security, facilitating collaboration between different stakeholders.
Best practices: It offers guidance on implementing effective security measures.
Continuous Improvement
Evolving threat landscape: The OWASP Top 10 is regularly updated to reflect emerging threats, encouraging organizations to stay ahead of the curve.
Conclusion
The OWASP Top 10 provides a valuable framework for securing web applications. By understanding these risks and implementing effective countermeasures, organizations can significantly reduce their exposure to cyber threats. Remember, security is an ongoing process that requires continuous vigilance and adaptation.
Subscribe to my newsletter
Read articles from Harshal Shah directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Harshal Shah
Harshal Shah
Navigating the convergence of cybersecurity, DevOps, and cloud landscapes, I am a tech explorer on a mission. Armed with the prowess to secure digital frontiers, streamline operations through DevOps alchemy, and harness the power of the cloud, I thrive in the dynamic intersection of these domains. Join me on this journey of innovation and resilience as we sculpt a secure, efficient, and future-ready tech realm.