Secure Data and Safeguard Users an App With End-to-End Encryption
 Amos Gyamfi
Amos Gyamfi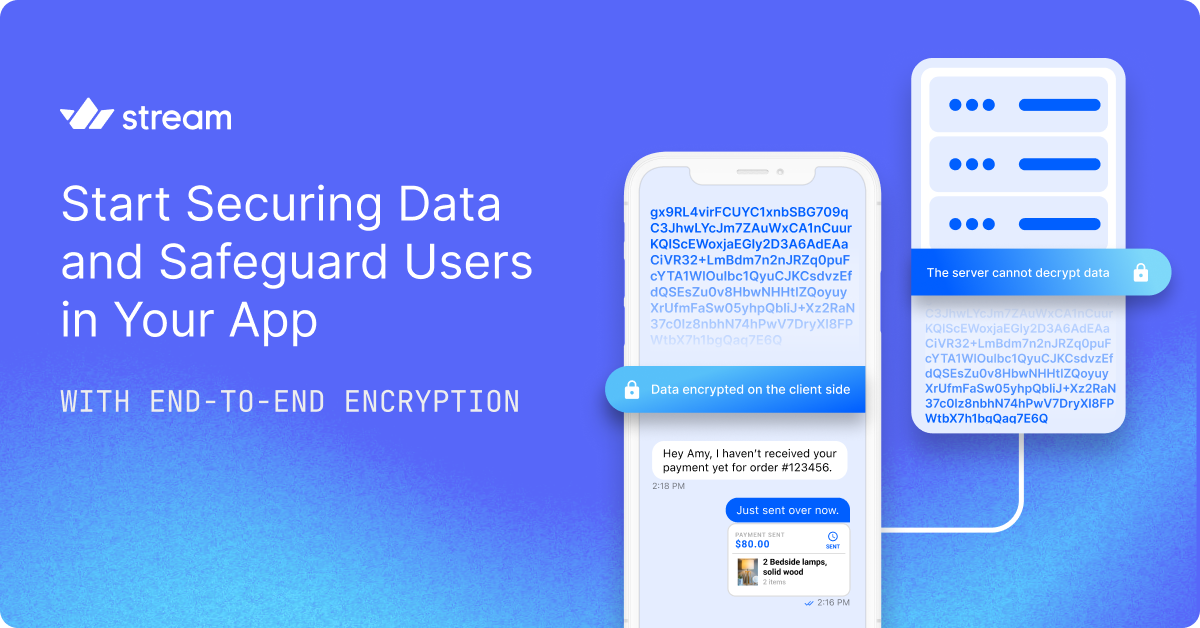
Have you ever wondered about the cost and wreaking havoc data breaches cause worldwide every year? Let’s look at how end-to-end encryption eliminates this concern.
In securing web and mobile applications, developers generally use traditional methods such as Transport Layer Security (TLS), Encryption at Rest, Encryption in Transit, etc. Although these approaches are acceptable, the methods stated here do not adequately secure data as end-to-end encryption. This article will explore everything you need to know about using end-to-end encryption (E2EE) to safeguard users and potential implementation solutions to enhance user security.
Before You Begin
In this article, you will learn an overview of E2EE, its challenges, and why you should implement it to provide world-class security for your app's users. To see end-to-end encryption implementation in action, keep an eye out for another tutorial that focuses on integrating E2EE into a web app using Stream Chat’s React SDK and Seald E2EE SDK. Although we cover general E2EE concepts in this article, we illustrate most of the E2EE examples for chat messaging.
Continue reading 📖 to unlock 🔓 how end-to-end encryption works under the hood.
What is App Encryption?
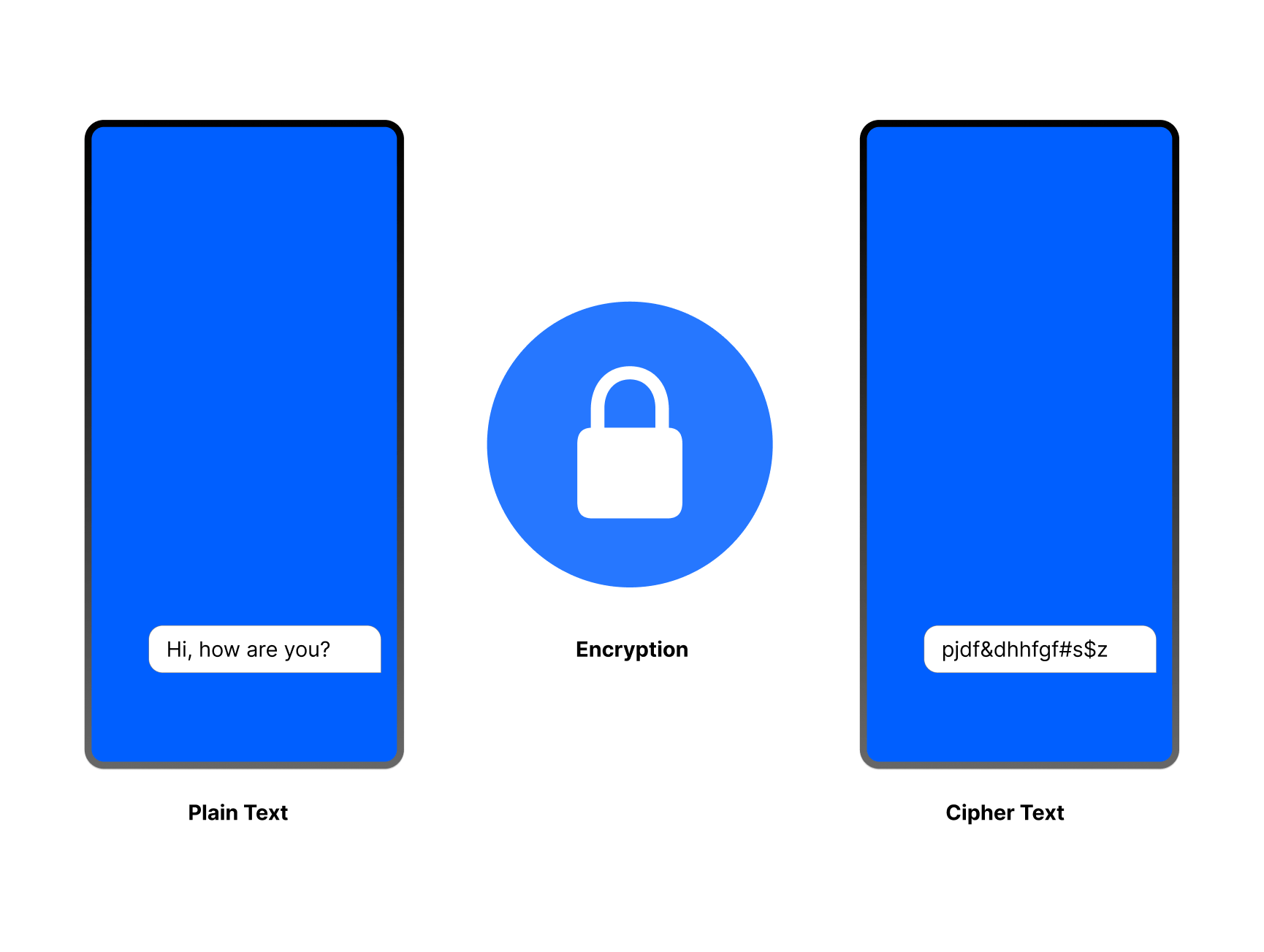
Encryption secures an app’s data to ensure user privacy and application safety. The users’ information can be text and voice messages, media attachments (photos, documents, audio, images), profiles, and more. Encryption keeps them secure by changing data at a source or when transmitting it from a user into a form that cannot be read. As the image above demonstrates, an encrypted message transmitted from a source will appear as a series of text characters without meaning when it gets into the hands of unauthorized users.
Encryption Tools
Encryption uses different methods to convert plain text communication into ciphertext. Below are some ways developers can encrypt web, mobile, and desktop applications.
Encryption in Transit: Encryption in transit works similarly to Transport Layer Security (TLS). It secures a "pipe" and protects everything inside it. Nothing is protected before and after the pipe.
Encryption at Rest: Encryption at rest (such as hard disk, database, or object storage encryption) secures data when unused. If someone breaks into the building housing, the hard disks containing the data, and steals them, they won't be able to do anything with them. On the other hand, if someone gains access to the backend (via an application vulnerability, for example), they'll have access to everything.
End-to-end Encryption: End-to-end encryption, on the other hand, protects data from the sender's device, the first "end" to the final recipient's device, and the second "end" without interruption. This ensures that data can only be accessed by the sender and the final recipient. Not even the data host, the application developer, any administrator or government, and any malicious person attacking one or more of these intermediaries will be able to access the data. End-to-end encryption is much stricter than encryption in transit combined with encryption at rest.
A simple web or mobile application can implement encryption at rest or in transit for data security and preservation of user integrity. However, a telemedicine app with complex structures and interactions must implement end-to-end encryption for fully-fledged privacy. End-to-end encryption is particularly useful in a telehealth app with features such as appointment scheduling, real-time chat messaging, and video calling between patients and doctors. Read the weakness of encryption in transit and at rest to learn more.
End-to-End Encryption: Overview
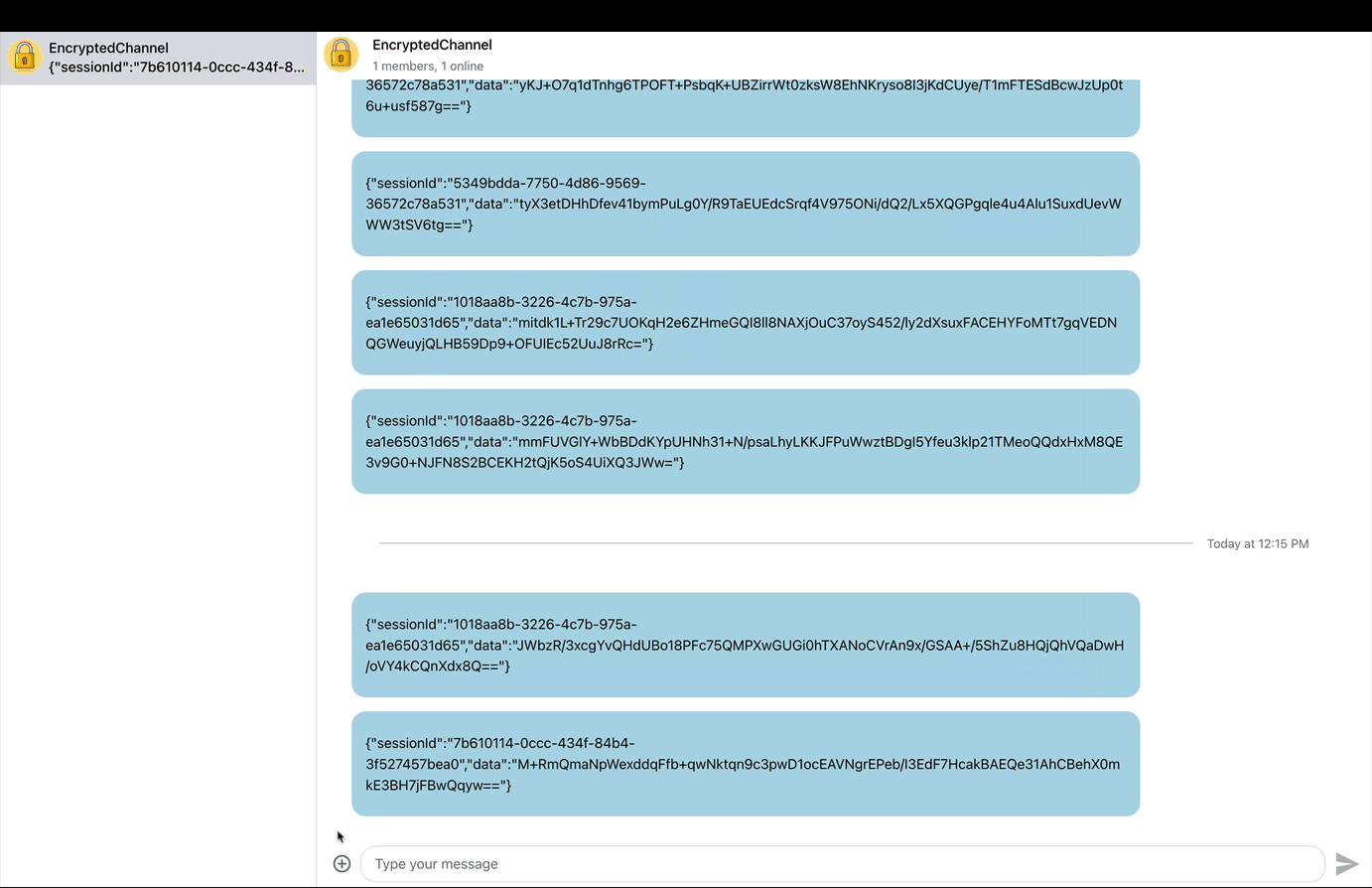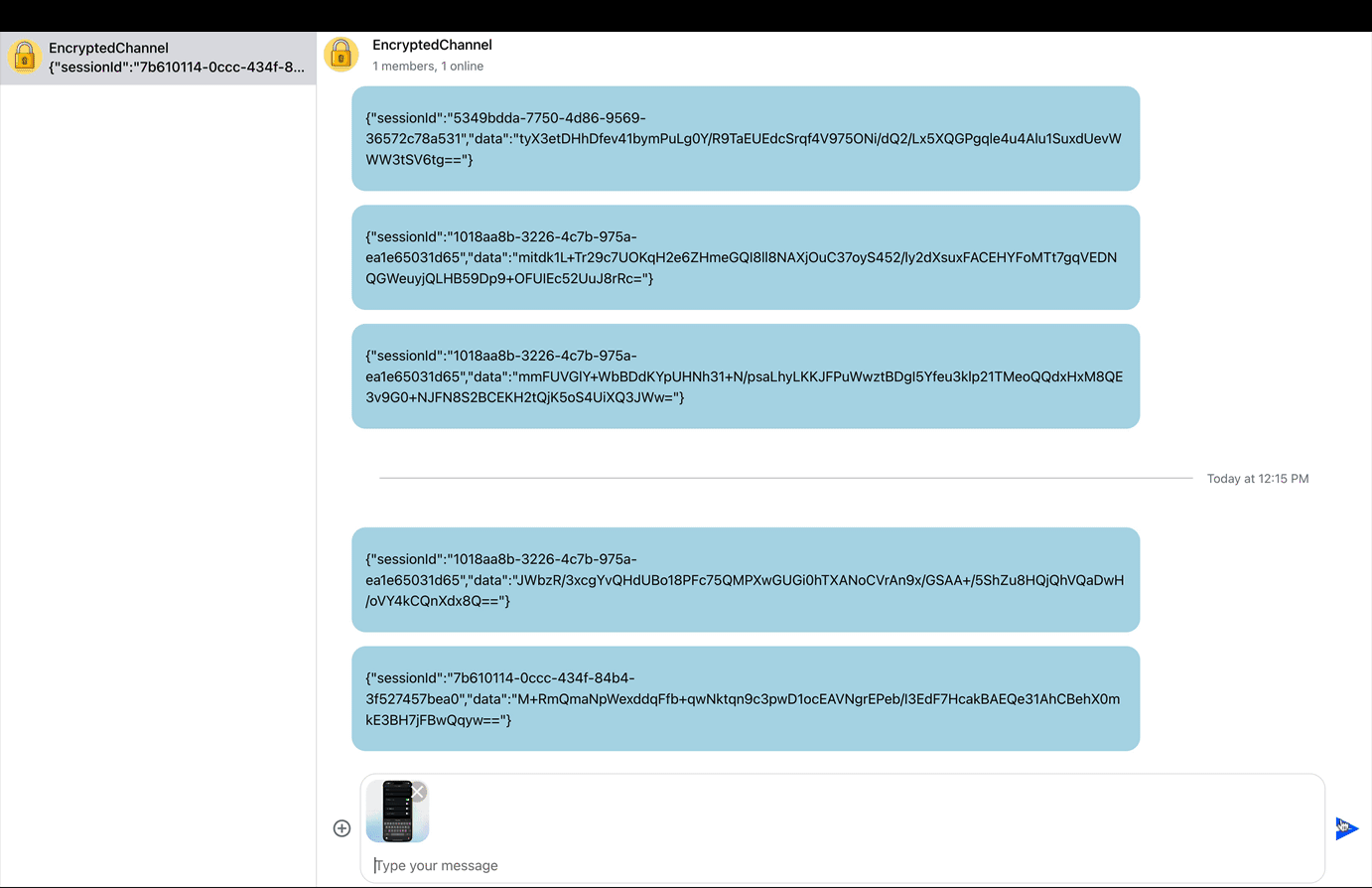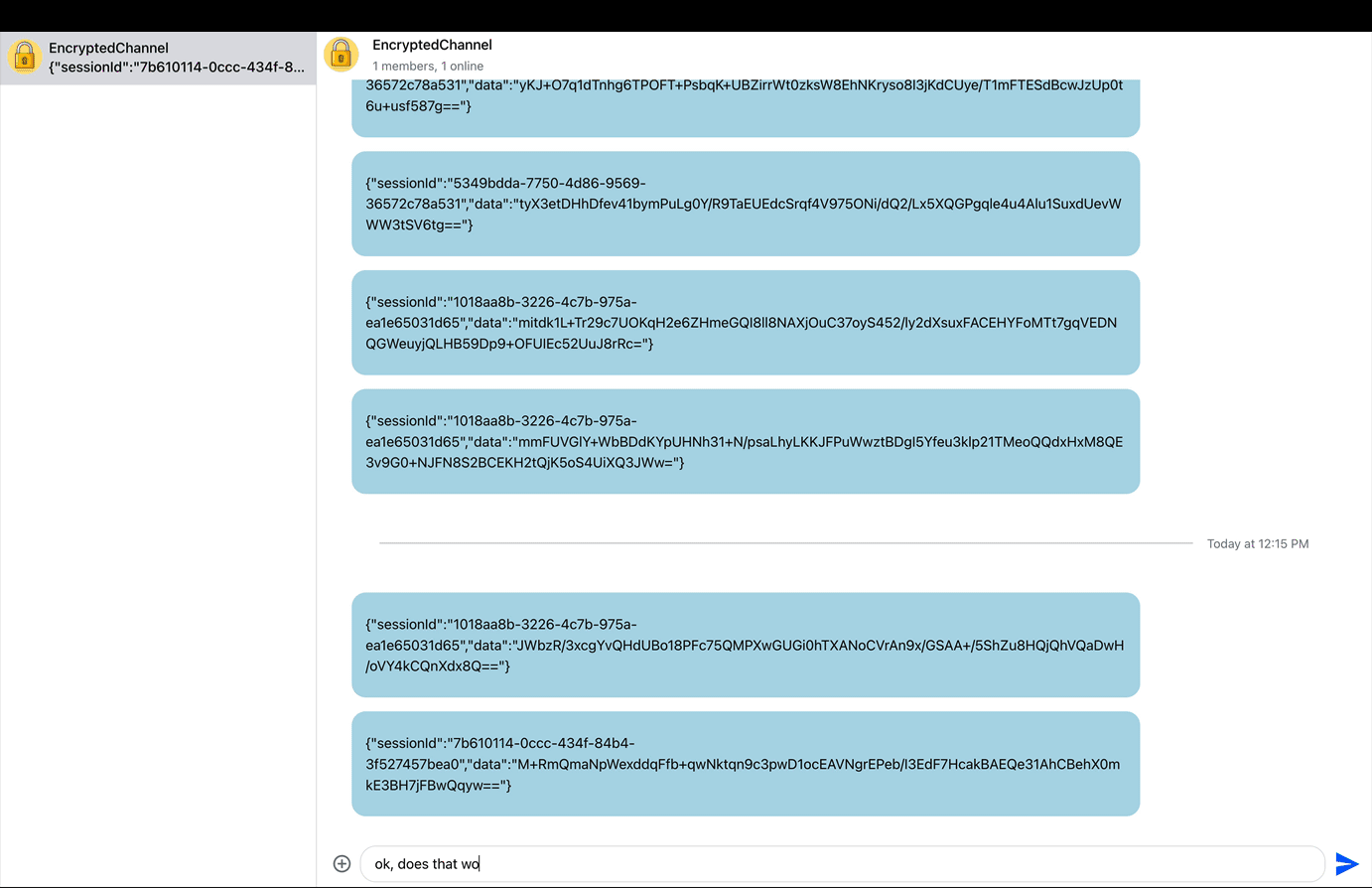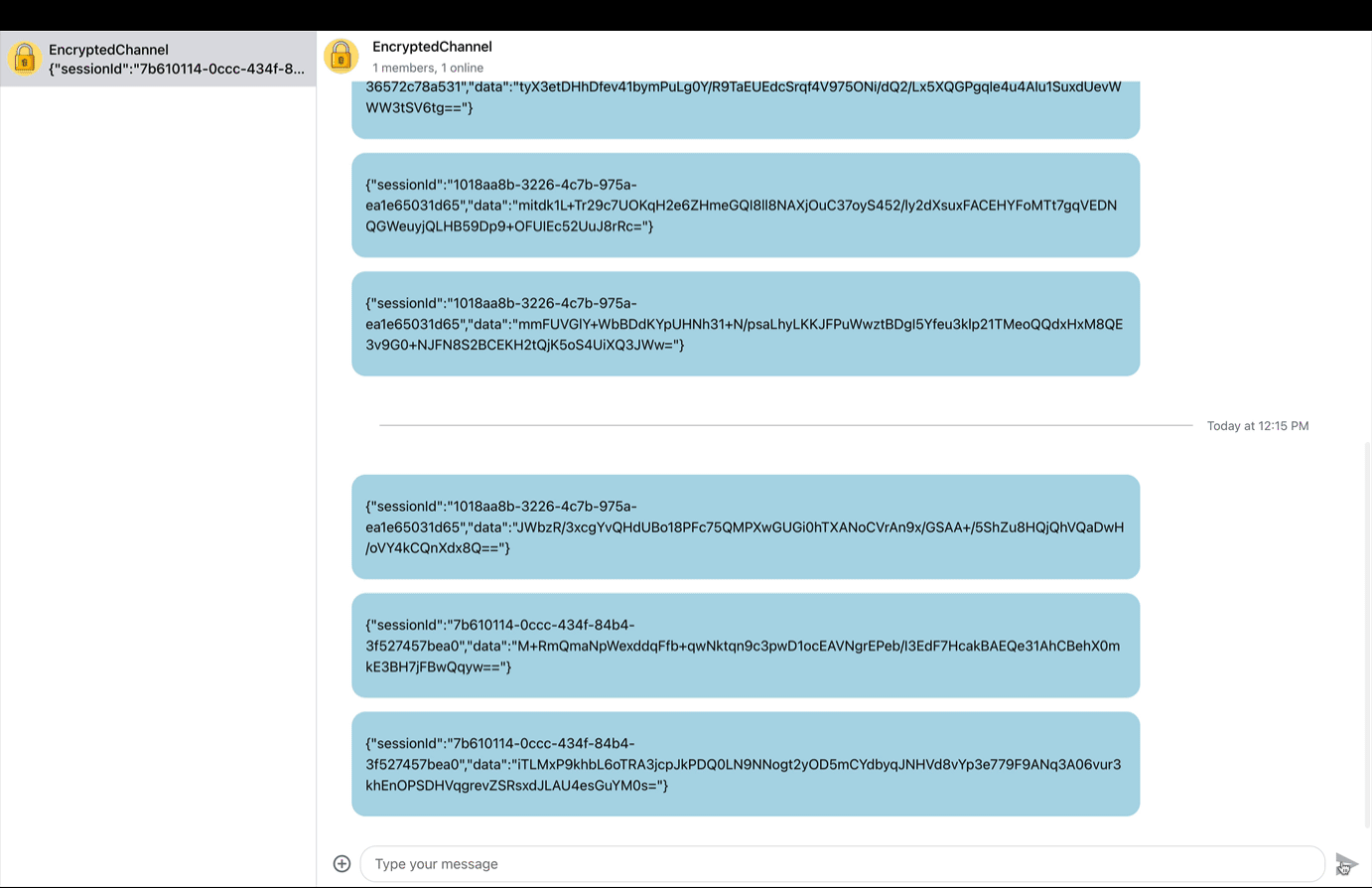
Fundamentally, end-to-end encryption uses a core concept called cryptography to secure data. In cryptography, a ciphertext is used to protect data by converting it into a non-human-readable format.
The video preview above demonstrates an end-to-end encrypted chat in action. Users need secret keys to cipher or decrypt the ciphered information into readable form. In end-to-end encryption, only intended users can access the data if the sender sends an encrypted information.
For example, when you power your messaging app with Stream’s Chat SDK and implement end-to-end encryption, nobody, including Stream’s backend servers, can see messages or listen to audio conversations users will send. All messages, including text, voice, files, video, and audio, are encrypted as they are shared among participants' devices.
How E2EE Works
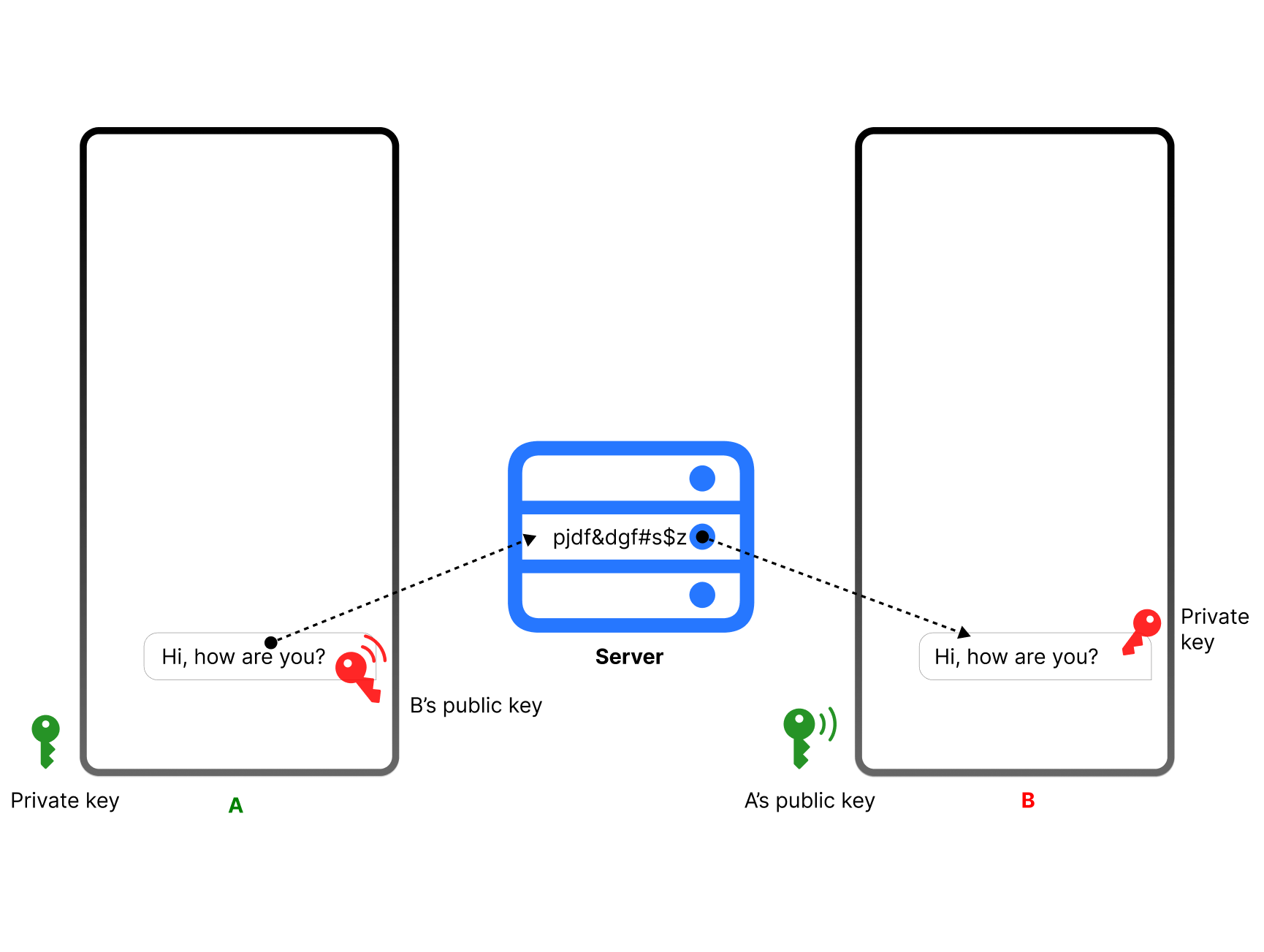
E2EE uses public and private encryption keys for its operation. A public key encrypts information, while a private key decrypts it. For example, in chat messaging, only the chat participants will hold the encryption keys in one-on-one and group chats. In case third parties or hackers gain access to a message sent between participants, they cannot decrypt it since they don't hold encryption keys. The keys disappear when the sender and receiver delete the message from their devices.
As demonstrated in the image above, when A wants to send a message to B, they exchange their public keys to connect through a server. A uses B's public key to encrypt the message before sending it via the server. Since the server does not have a private key, the message becomes non-readable on the server. The server's responsibility is to ensure seamless communication between A and B. The users' private keys are kept on their devices. Therefore, when the server sends the ciphered message to B's device, the private key of B decrypts the message to make it readable. The exact process is used when B wants to send a message to A.
E2EE Challenges
Although E2EE aims to provide the highest data security level on the client side, compared to other alternatives like encryption at rest and in transit, it is prone to the following attacks.
Backdoor Attack: With a backdoor attack, hackers can exploit an application’s vulnerabilities to bypass the encryption mechanism and authentication to access users' data.
Endpoint Attack: In E2EE, data protection occurs between endpoints. These endpoints are also prone to malicious attacks and can be compromised.
Man-in-the-Middle Attack: In this attack, an attacker can intercept a sender's message by joining the conversation or data exchange between the endpoints. For instance, if
Aintends to send a message toB, an attacker can impersonate the communication, makingBbelieve that the message is fromA.
The above challenges generally arise from E2EE implementation from scratch or using an in-house team. To eliminate these challenges when integrating E2EE in your app, consider using an E2EE SDK like Seald. The Seald SDK handles all the threats mentioned above. The SDK is built on the Zero Trust security model and handles all cryptographic complexities, such as key management, recovery of private keys, group management, and breach of user credentials.
Why Should Your App Offer End-to-End Encryption?
Data privacy and safety are increasingly critical in enterprise and community-based applications. Implementing end-to-end encryption is becoming a must and a standard. The following points out why E2EE should be integrated as a security measure.
It can help minimize cyber attacks and data breaches since attackers may not have anything accessible on the systems they attack.
It ensures customer trust and prevents reputational damage.
Password protection: A service like 1Password uses end-to-end encryption to protect users' passwords using a key.
E2EE is much stricter than its other alternatives, such as encryption at rest and encryption in transit.
What Data Should Be End-to-End Encrypted?
Developers can use different methods to encrypt an app. However, only some apps need end-to-end encryption. E2EE is the best choice when user privacy is of the utmost concern, such as in the following application areas.
Healthcare data: Patients' information should be end-to-end encrypted to prevent access from unauthorized parties and to maximize patients privacy.
Unstructured data: Users’ chat history, media storage, file sharing and data about access to personal messages from multiple devices should be end-to-end encrypted. In WhatsApp, personal messages, - video calls, and voice messages are protected with E2EE to ensure only the sender and receiver can read sent text messages and listen to audio messages.
Team conversations: When end-to-end encrypted, it will help maintain confidentiality and prevent unauthorized interception of group communications.
Marketplace information: In a marketplace setting, E2EE can safeguard proprietary information and intellectual properties of buyers and sellers from attackers.
Financial data: End-to-end encryption can help to secure sensitive financial transactions and personal information from theft.
Educational information: End-to-end encryption of educational data can ensure the confidentiality of privileged communications and sensitive educational documents.
Identifying End-to-End Encryption in Communication Apps
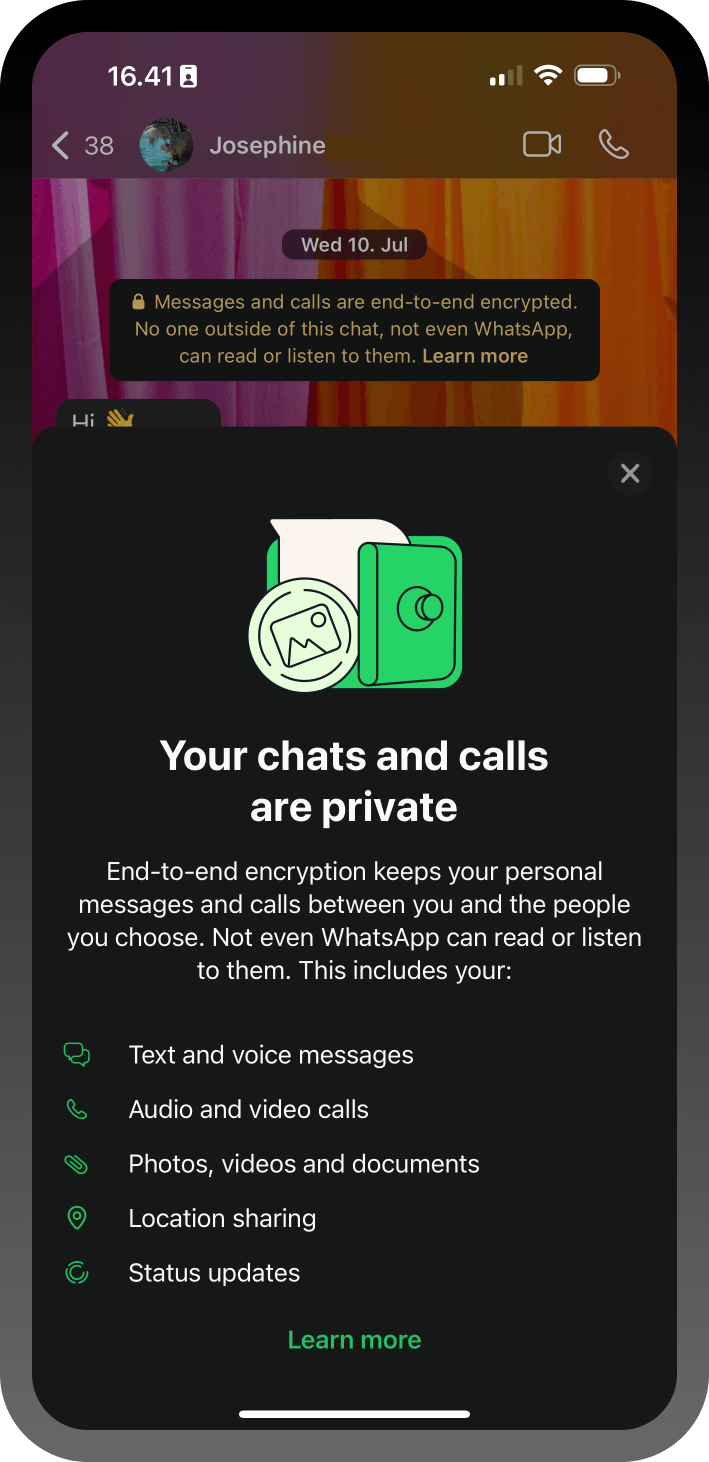
When you implement end-to-end encryption in your app, there should be a way to make users aware of this feature. As shown in the image above, when a user initiates a chat in WhatsApp, there is a notification that indicates all messages will be encrypted end-to-end. Some popular messaging applications like WhatsApp turn on end-to-end encryption by default.
Others may provide in-app settings to turn E2EE on and off like the implementation in Telegram. Users should select the option Start Secret Chat to turn on the E2EE support.
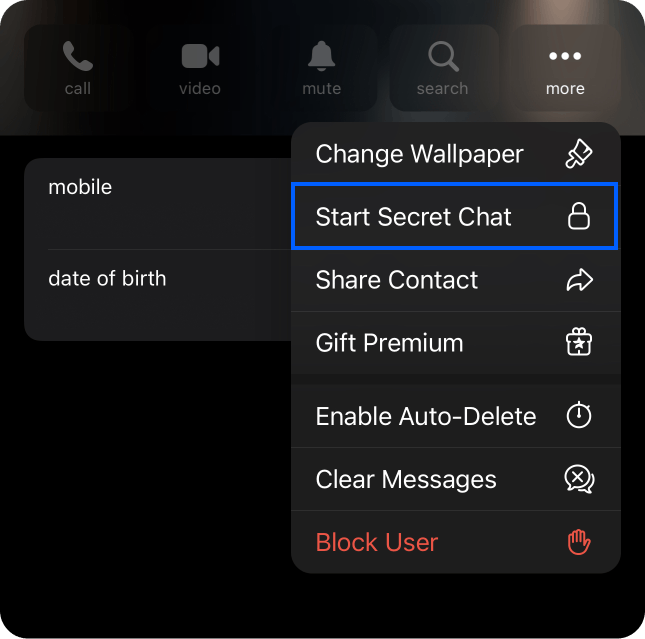
In business messaging apps like Google Messages, a lock icon appears beside the send button when users compose messages. The lock icon indicates that the chat is end-to-end encrypted.
Some messaging applications may also use other forms to indicate and notify users if the messages they send to people will be end-to-end encrypted. For instance, iMessage uses a blue bubble for message delivery to indicate that the communication is end-to-end encrypted. Apple also encrypts FaceTime conversations end-to-end.
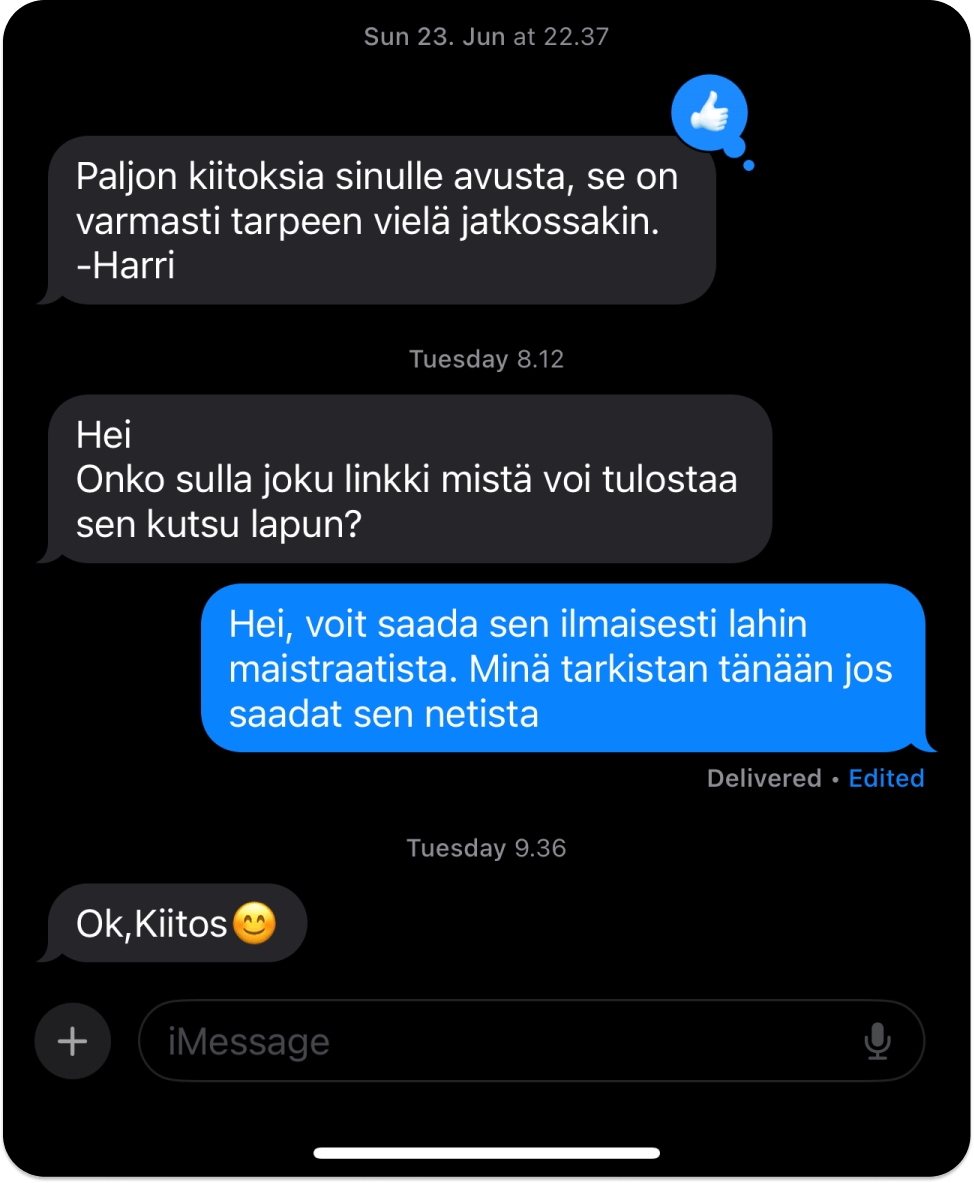
Note: The chat bubble appears blue when you send a message across Apple devices using the Messages app.
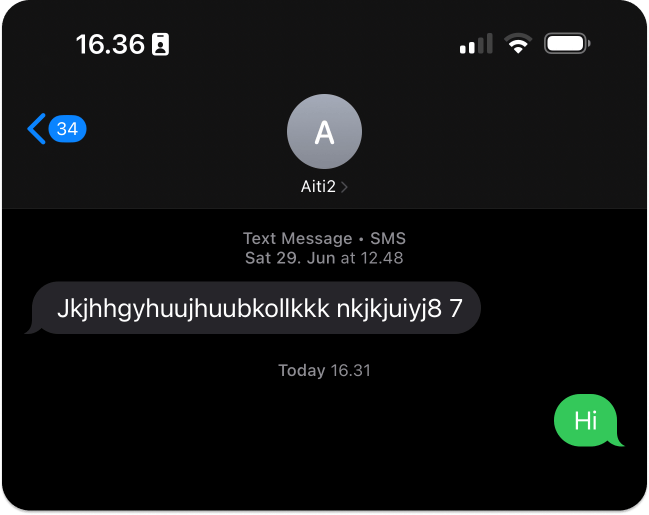
However, when you send a message with the Messages app for iOS to any Android device, the chat bubble turns green when delivered, which means it is a Short Message Service (SMS). An SMS sent with the Messages app does not have E2EE implemented.
Note: A message you send from an iPhone to an Android device is an SMS with a green chat bubble.
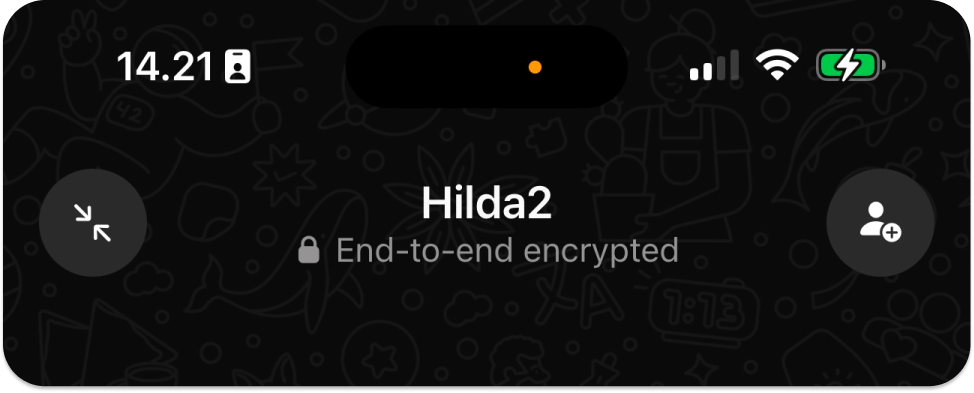
When initiating a voice call in WhatsApp, the UI shows a text indicating the call is end-to-end encrypted before establishing the connection to the other participant.
Conclusion
Congratulations! You now understand end-to-end encryption and why it is essential for ensuring the privacy and security of user data. It protects private and confidential information, such as text and voice messages, media attachments, user profiles, and more, from unauthorized access. By adopting end-to-end encryption, you demonstrate a commitment to safeguarding data privacy and ensuring users' trust.
We looked at E2EE for a single use case, providing maximum security for real-time chat messaging users. Keep an eye out for our step-by-step guide, which aims at encrypting Stream Chat end-to-end using Seald to implement the feature into your app.
Subscribe to my newsletter
Read articles from Amos Gyamfi directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
