AWS IAM Guide: Creating Groups and Setting Up Identity Policies
 Vandana Pandit
Vandana PanditTable of contents
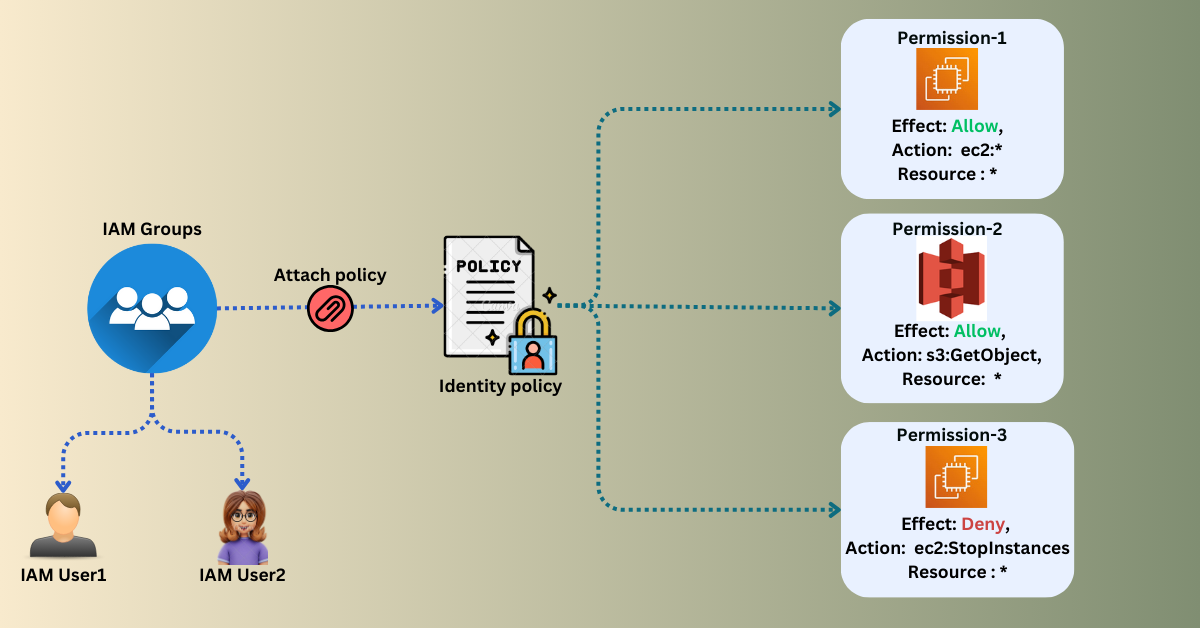
IAM Groups:
IAM Groups are used to manage users.
Here are some best practices for IAM Groups:
Simplify User Management: IAM Groups make managing users easier.
Descriptive Names: IAM Groups should have descriptive names.
Similar Roles: Add users with similar roles to the same group.
Policy: Assign policies to the group so that users in the group have specific permissions.
Steps to create groups:
Open IAM services and select "User groups" from the left panel on the IAM Dashboard page.
Click on "create group" button on the IAM User groups page
Give group name , select user and attach policy as shown below. Click on "Create user group" button.
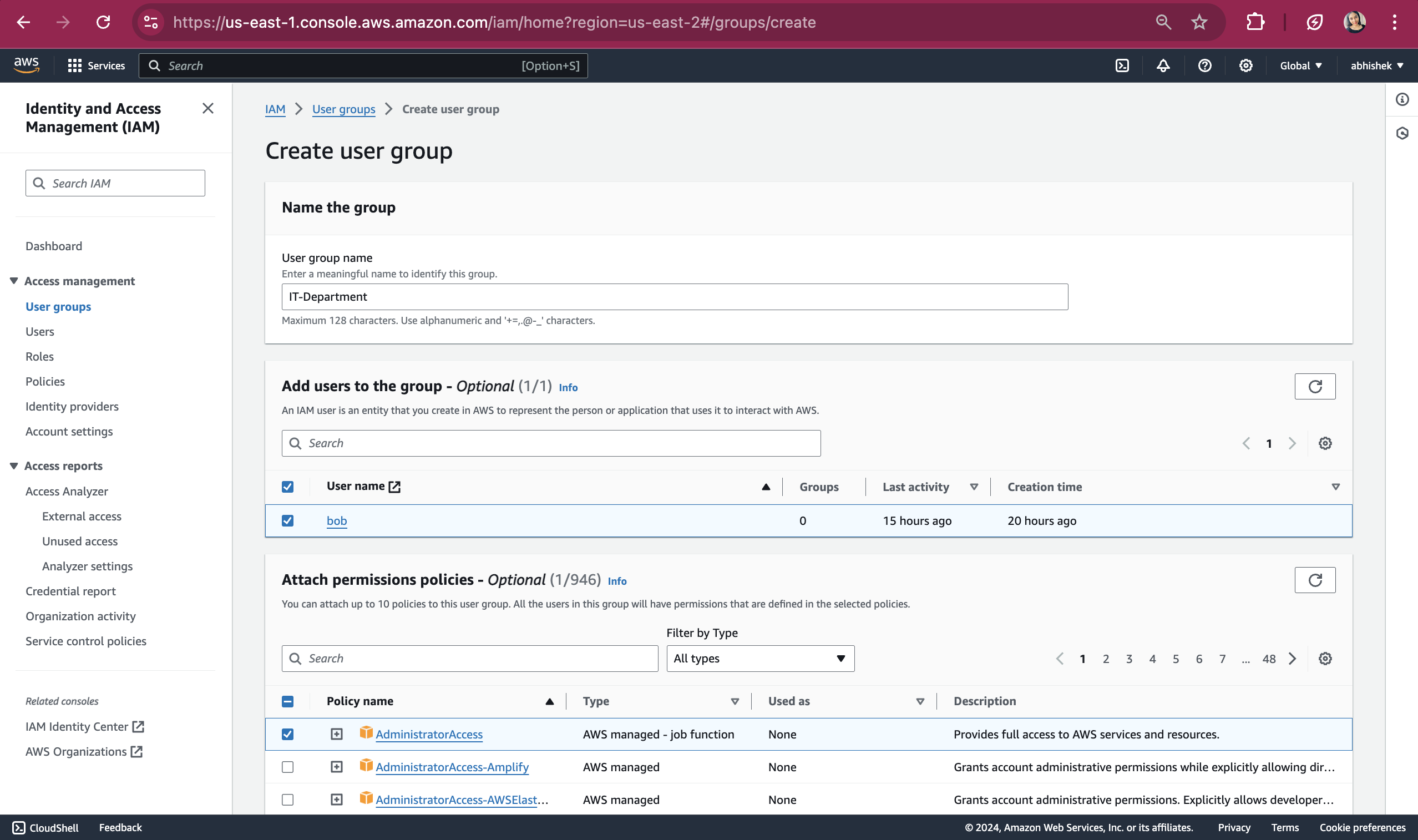
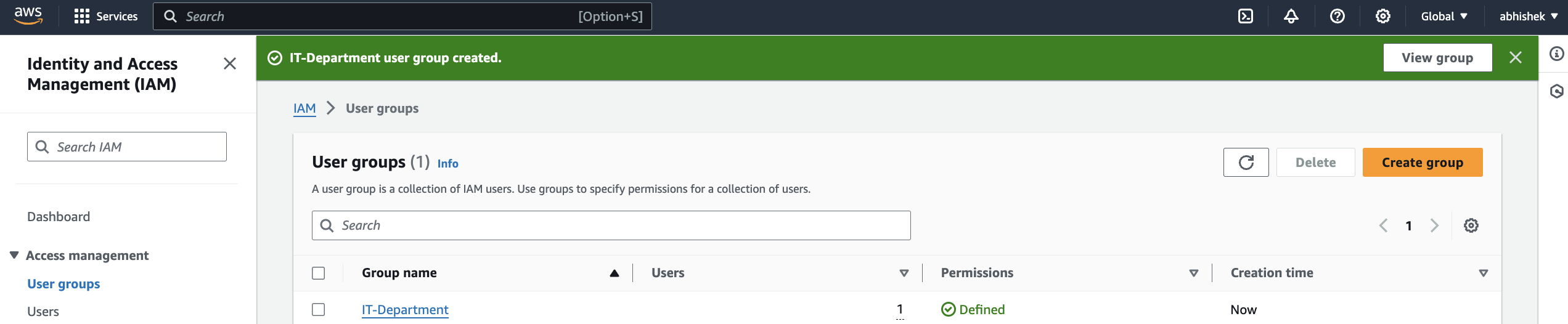
An IAM group named "IT-Department" has been successfully created with the user Bob, who is a solution architect and has an administrative access policy. This policy provides full access to AWS services and resources.
IAM Policies and permission:
Before we dive into policies, we need to understand a very important concept: the "Principle of Least Privilege."
Principle Of Privilege:
If your users needs access to do their job, give them the access, but take away the access they don't need.
IAM Permissions:
IAM permissions provide fine-grained control over the actions performed on AWS services and resources.
For Example:
EC2:StartInstances --> This permission is an action to start an AWS EC2 instance
S3:GetObject --> This permission is an action of getting an object from S3 bucket
SQS:CreateQueue --> This permission is an action of creating a queue inside a SQS service.
SNS:DeleteTopic --> This permission is an action of deleting an SNS topic
A collection of these permissions together is called a policy.
IAM Policies:
Manage access and permissions in AWS.
Policies define permissions and actions for identities or resources.
Rules specify what resources an entity can access and what operations they can perform.
IAM policies provide fine-grained access control over services and resources.
Categorising IAM Policies:

Identity Policies:
Policies that are attached to users, groups, or roles.
If I have 5 users, I can either attach the policy to each user individually, or if all 5 users have the same role, I can add them to a group and attach the policy to the group. If I have an EC2 instance running an application, that instance can assume a role. This role has specific permissions defined in the policy attached to it. My application will have the permissions defined in the policy attached to it.
Steps to create an Identity policy and attach it to a group:
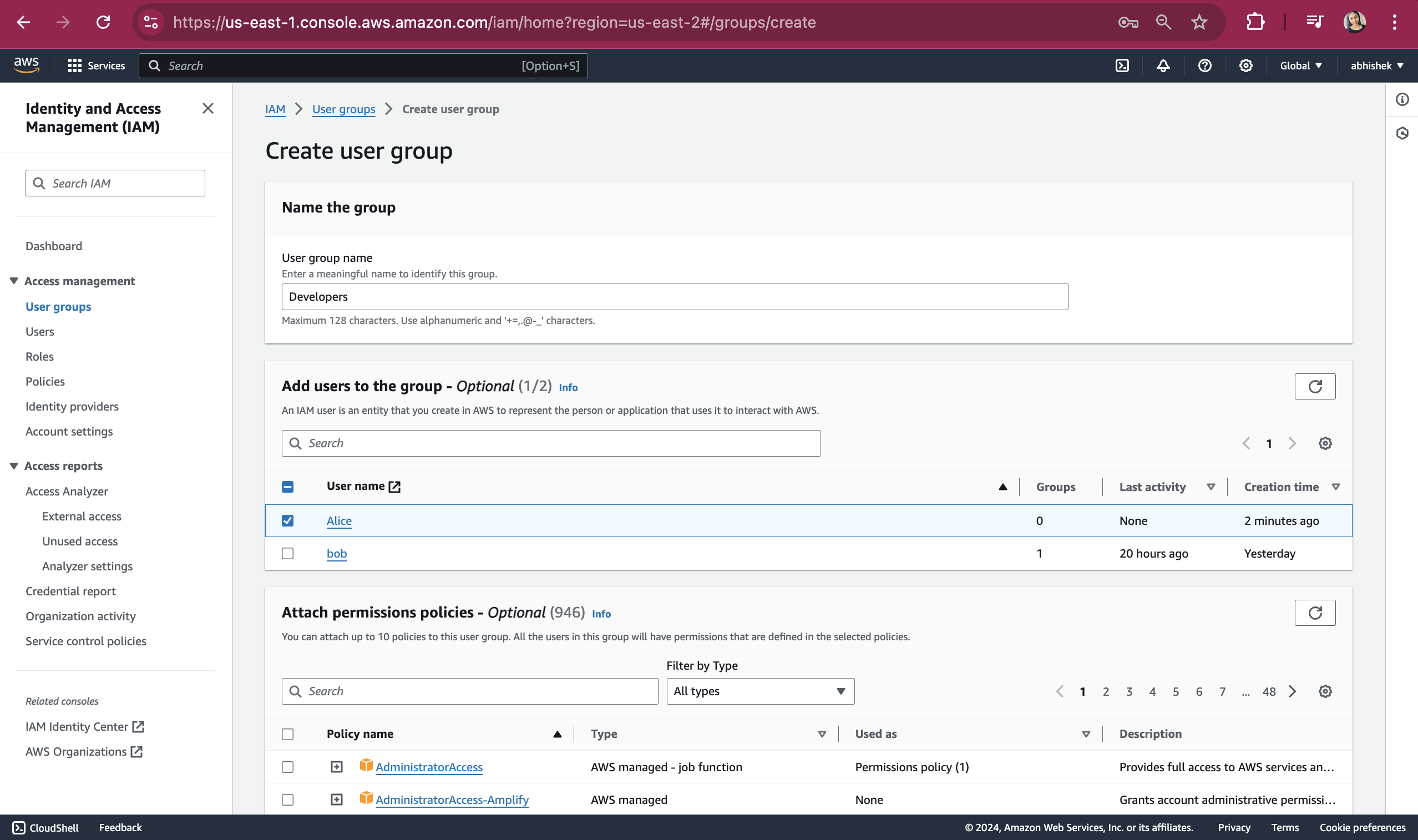
First, we will create a group for Developers and add Alice to the group. We will not attach the policy yet. Click on the 'Create User group' button.
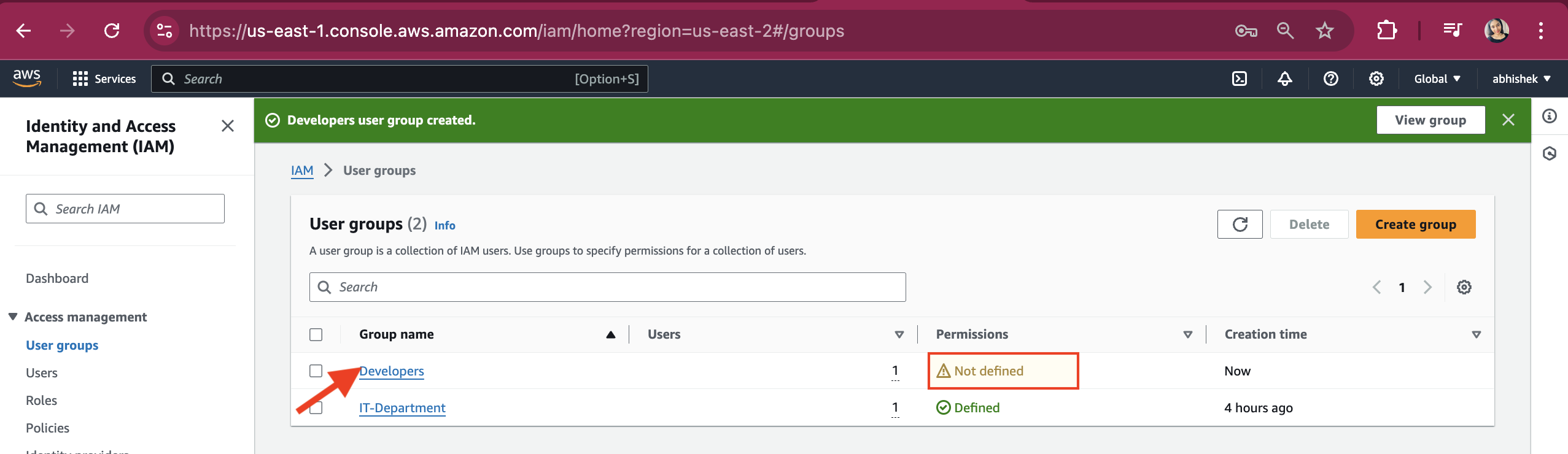
As we can see, the Developers group was created, but the permissions are not defined yet.
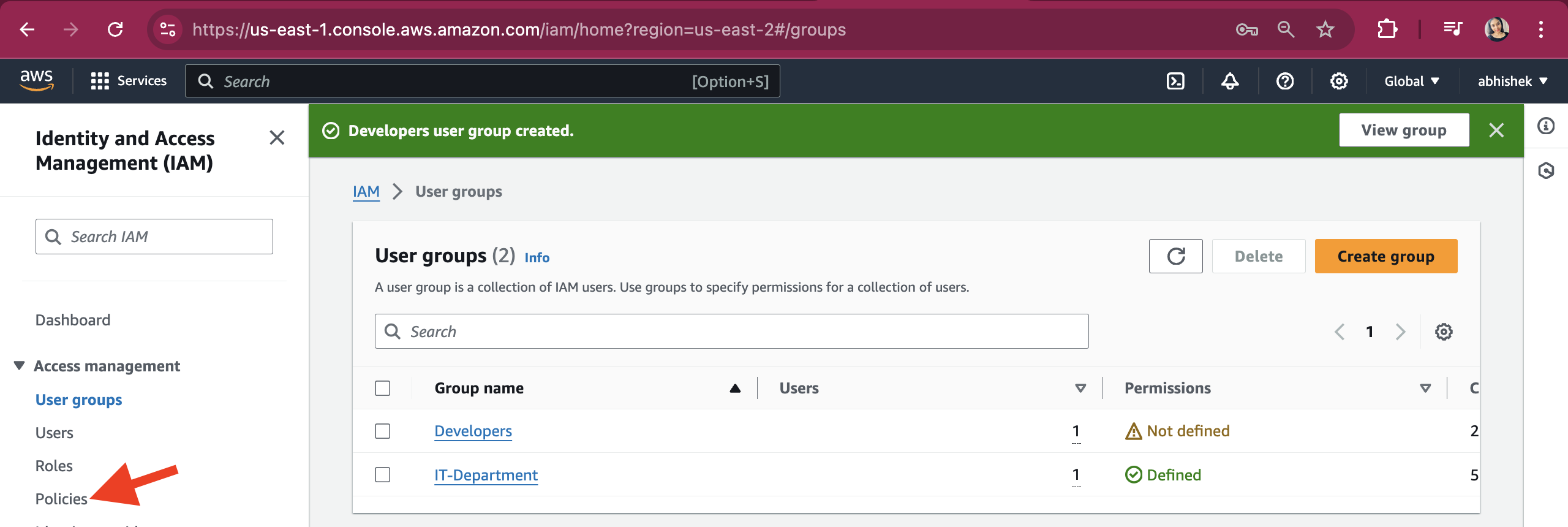
To create the identity policy, click on "Policies" in the left panel.
On Policies page click on "Create policy" button.
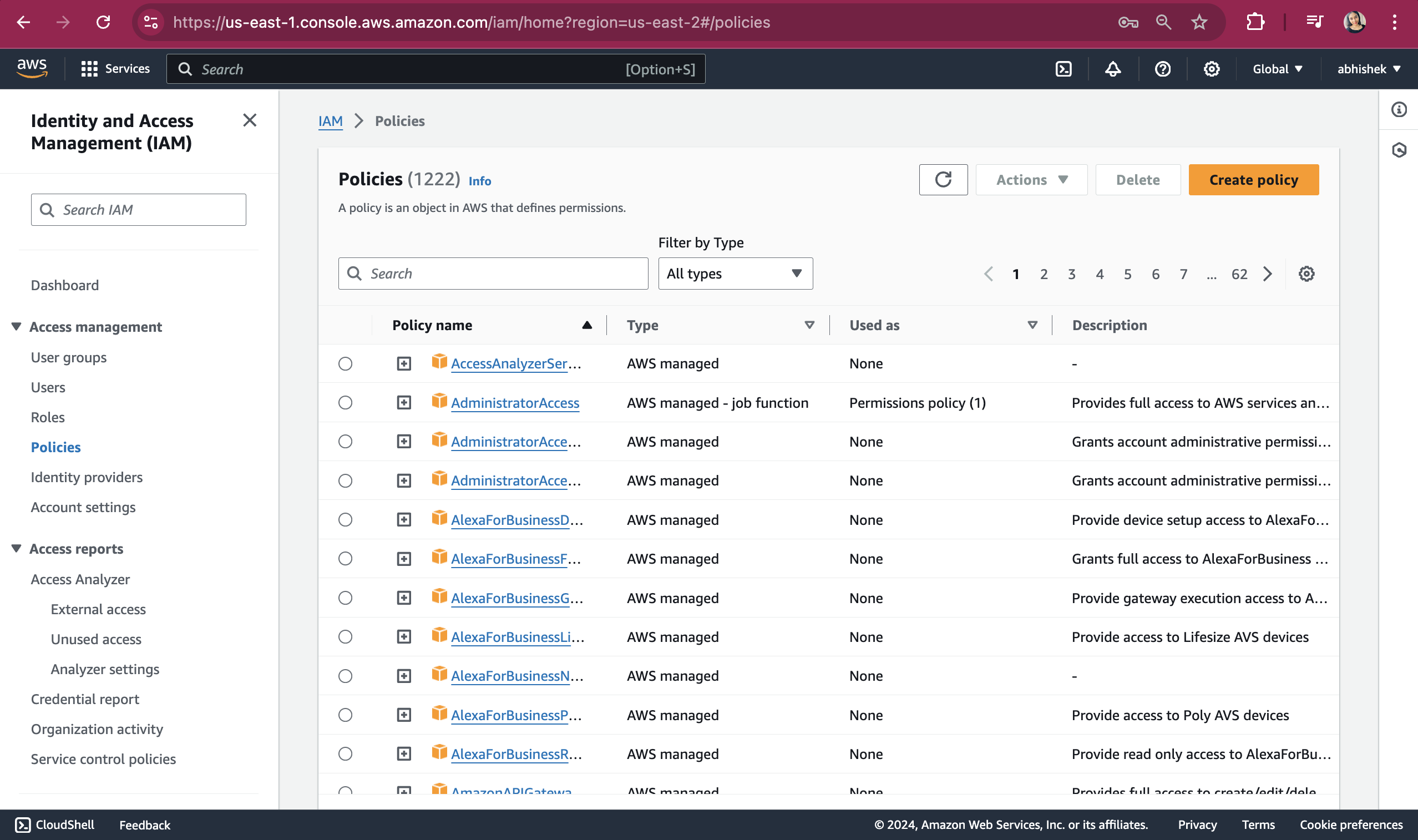
On clicking create policy button it will take you to this page
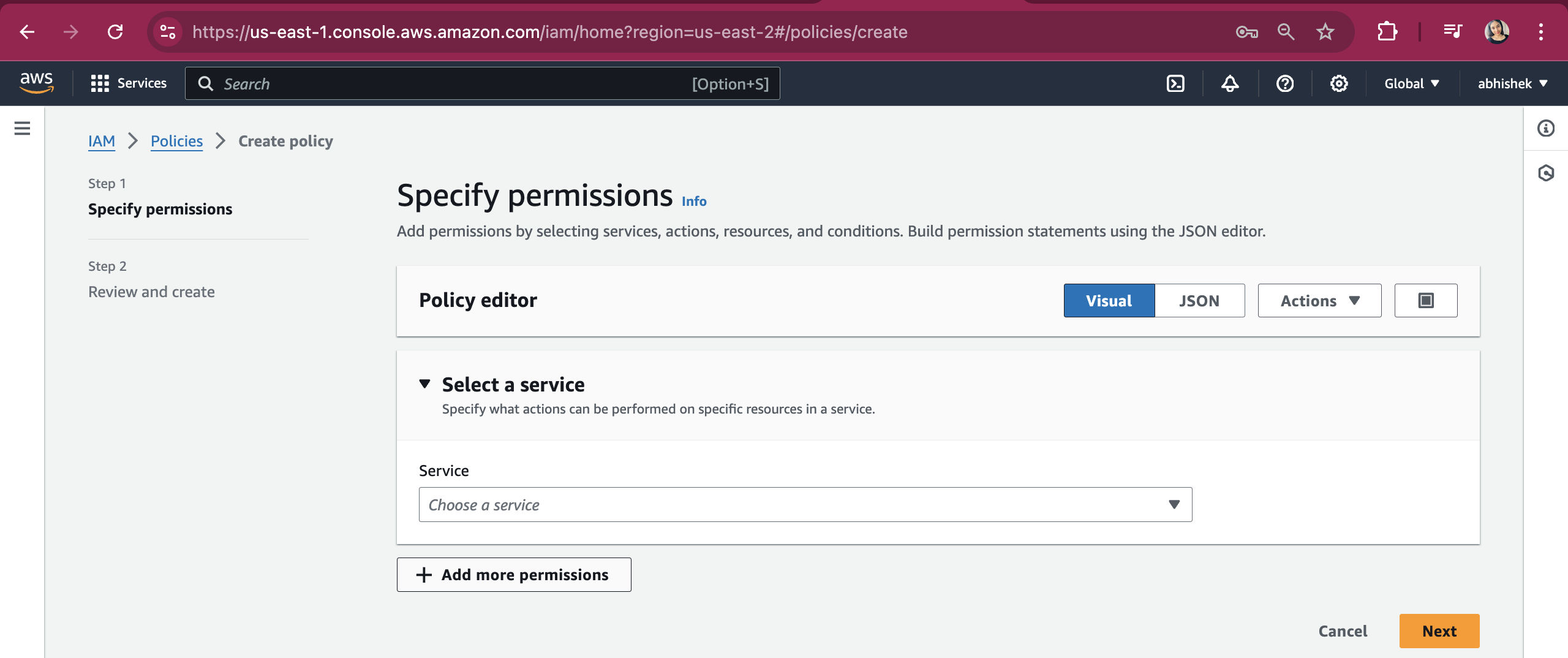
Select the S3 service from the service dropdown. Ensure that the Effect is set to Allow.
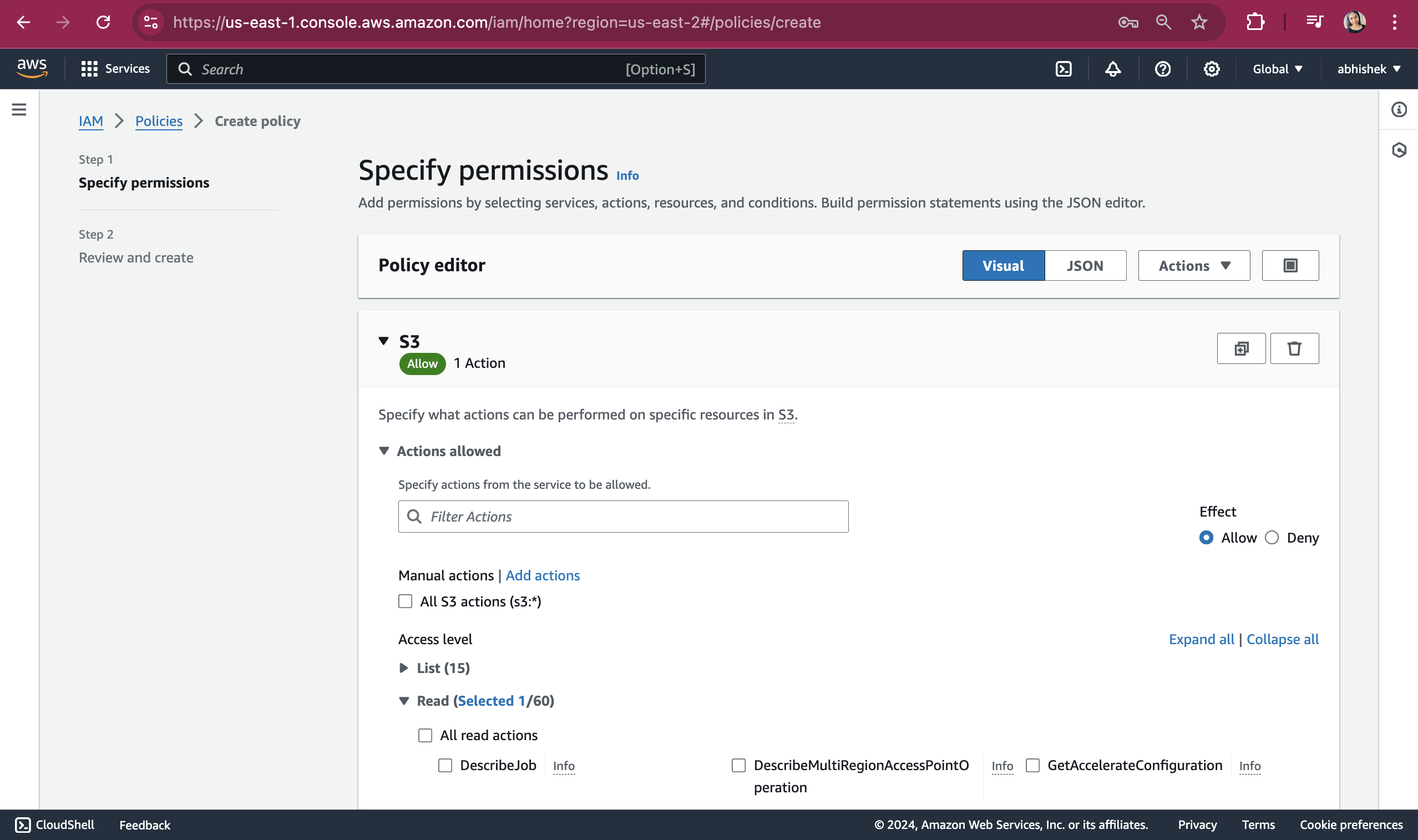
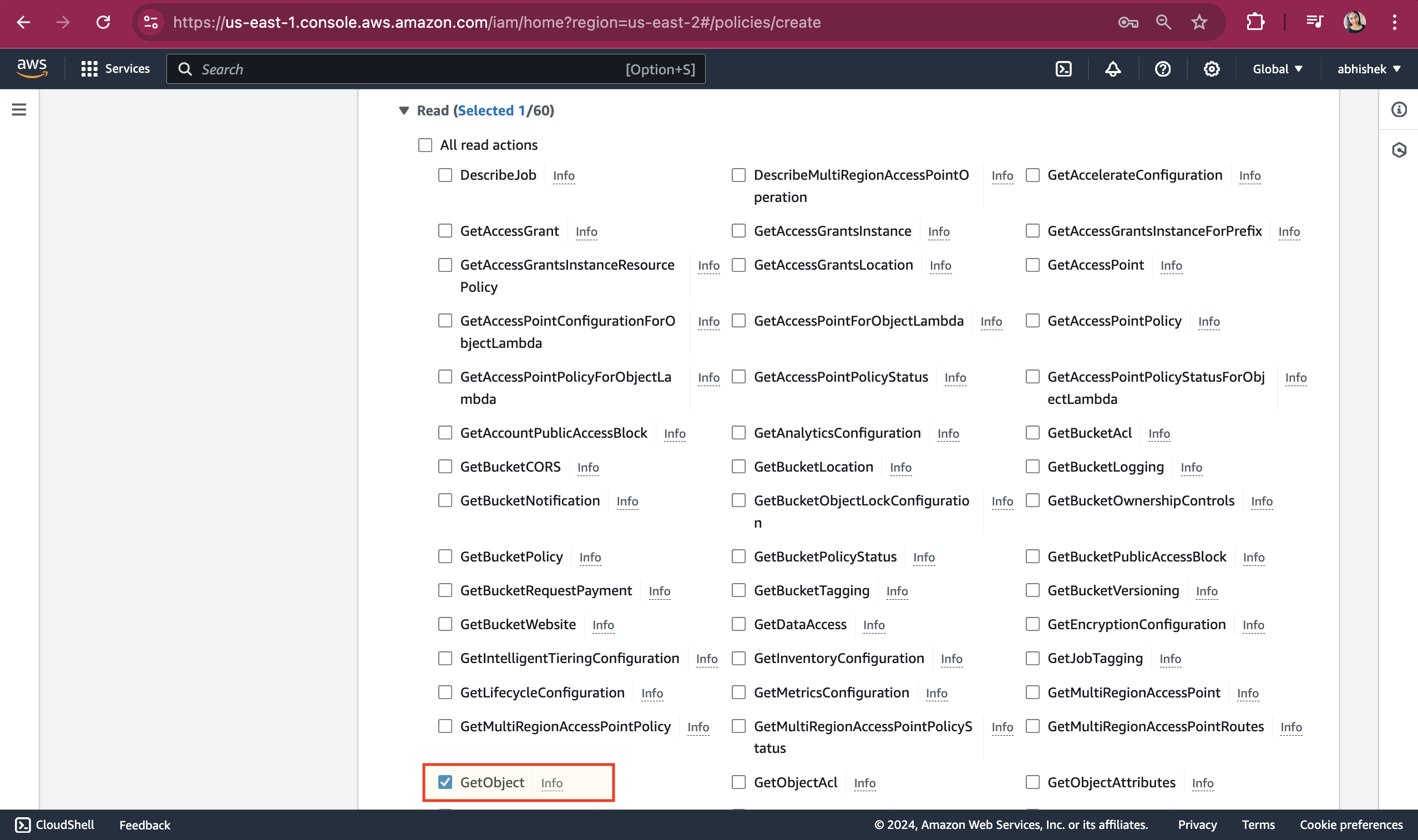
Click on Read dropdown and select GetObject.
Under Resource section , click on "Add ARNs"
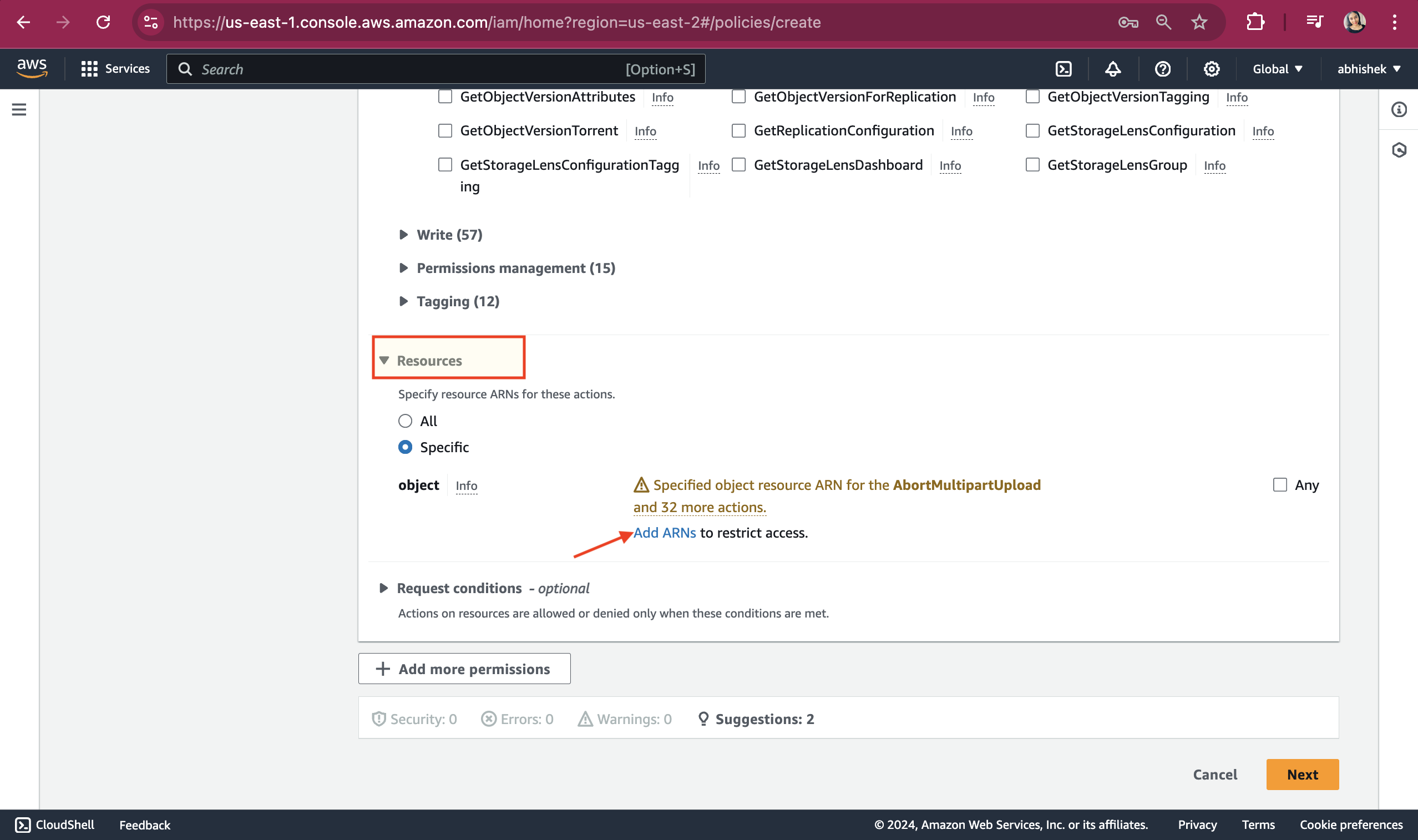
Give the bucket name that the Developers have access to and select the checkbox for "Any object name." See the "Resource ARN" is autogenerated. Click on "Add ARNs."
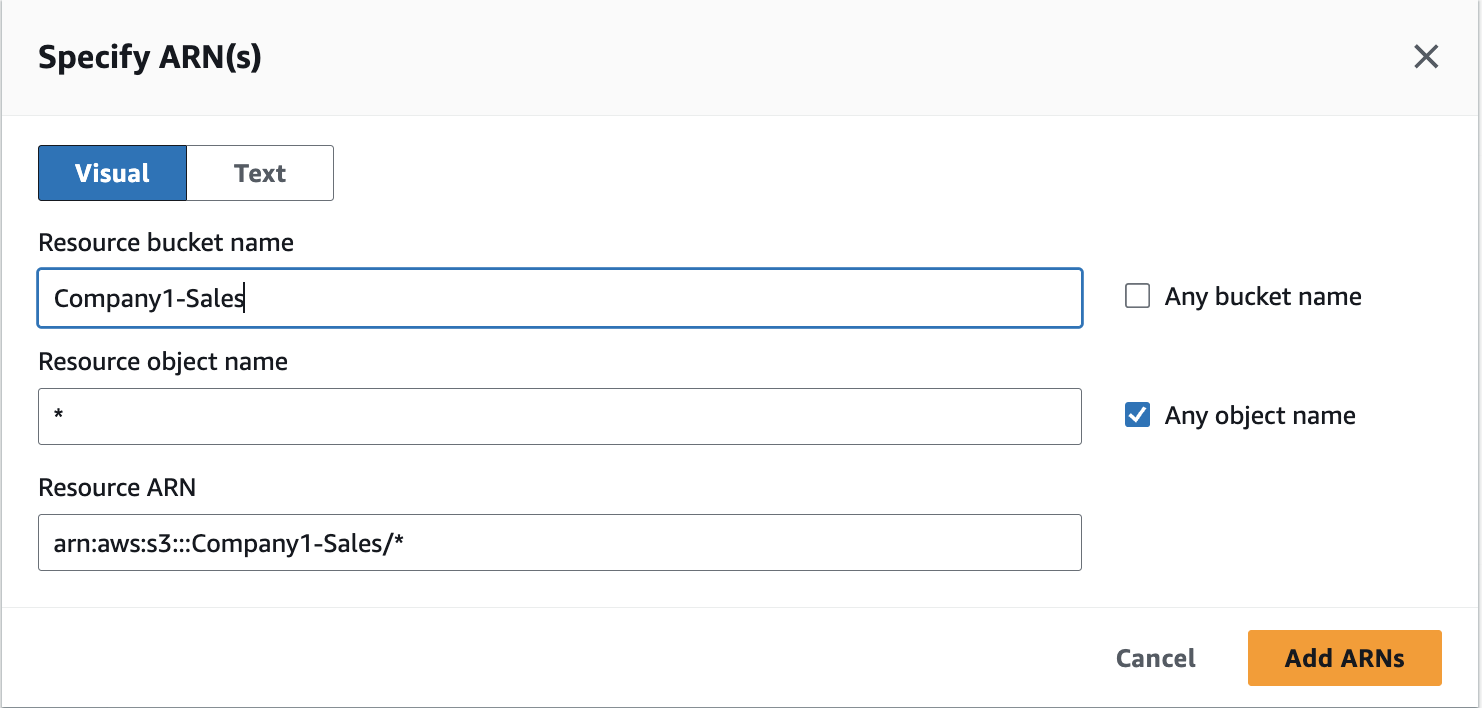
Check if the ARN is auto populated. Click on "Add more permissions" button.
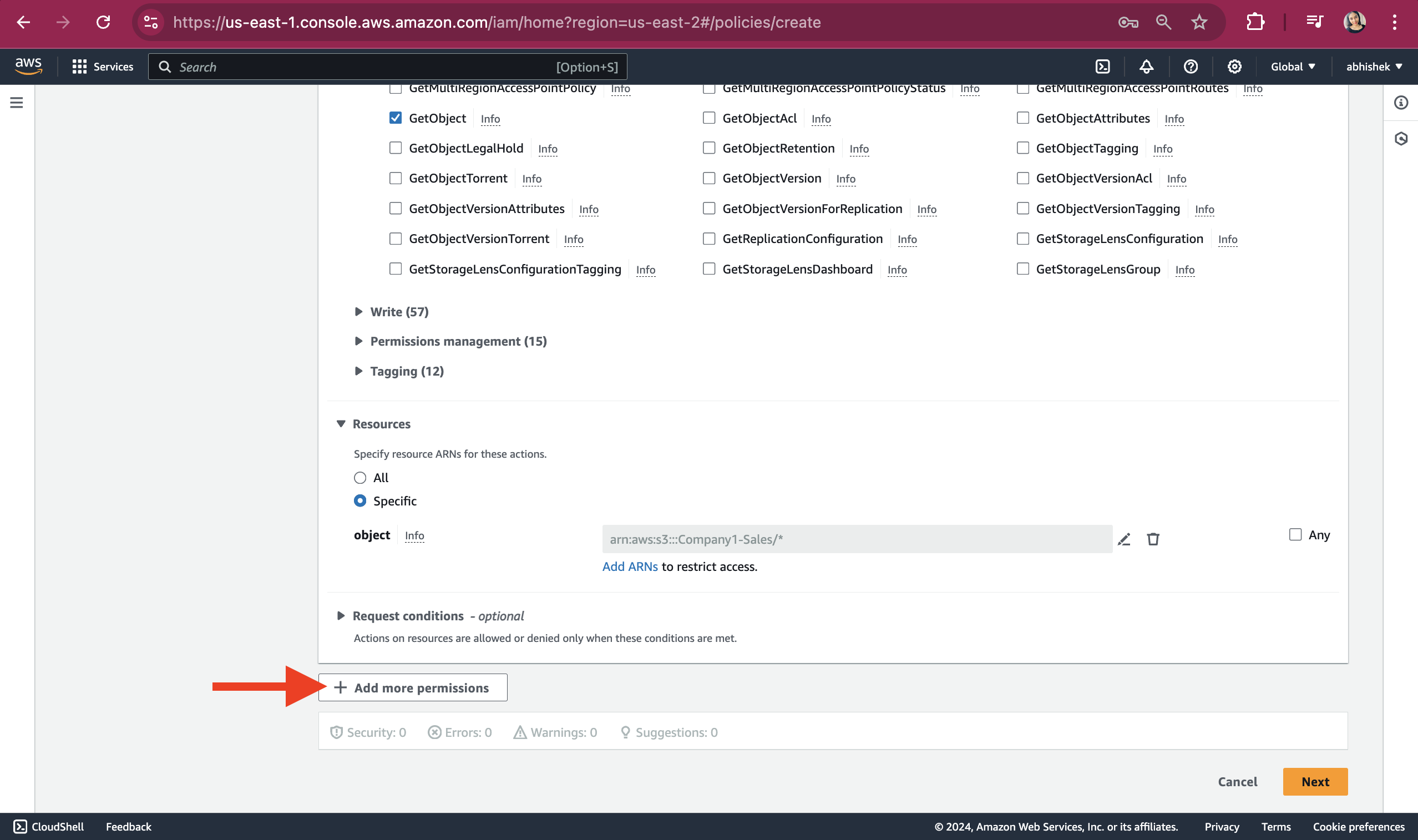
Select the service as 'EC2' and under manual actions, check the box for "All EC2 actions." In the Resources section, select the radio button for All.
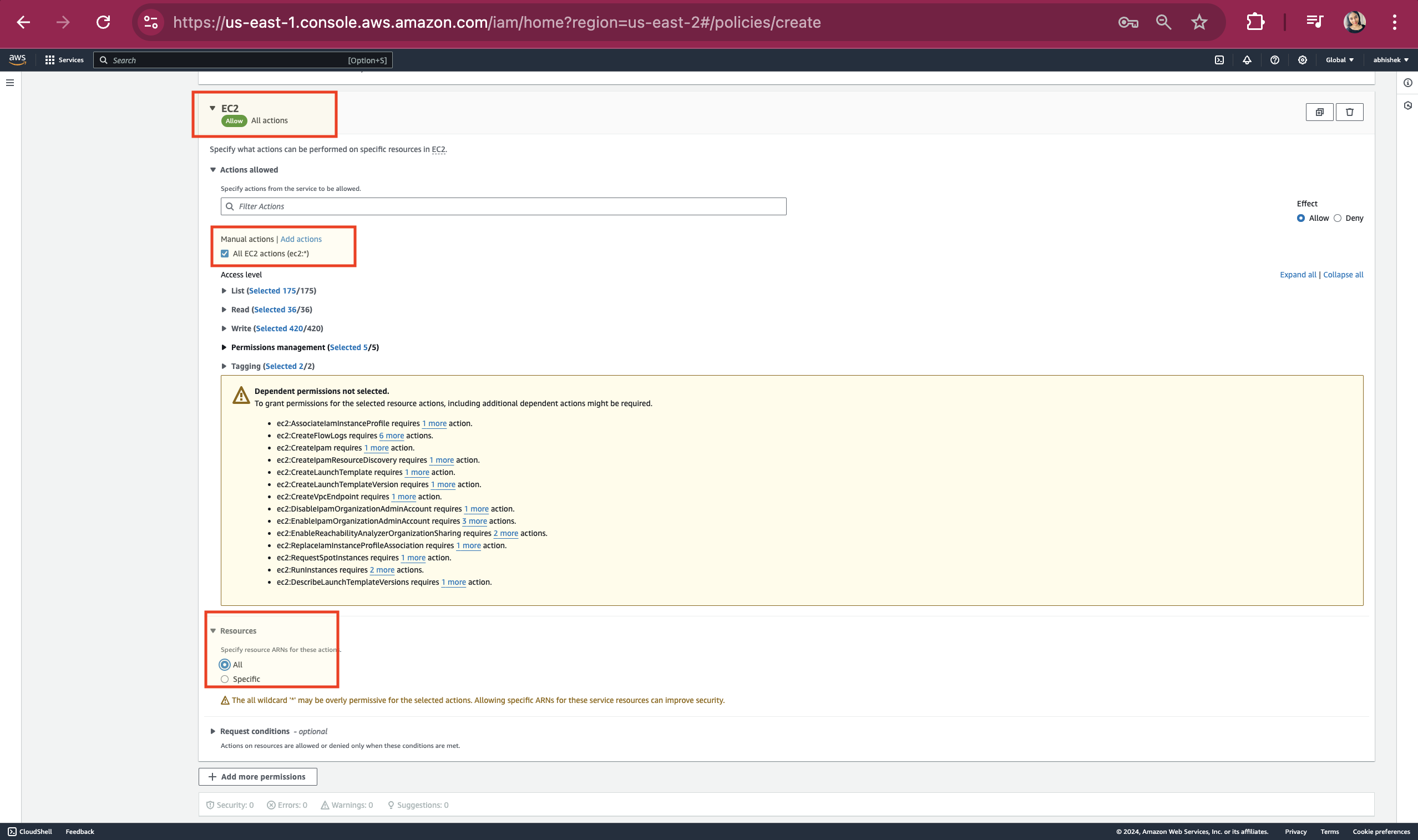
Scroll up and click on JSON. On click JSON, the below screenshot will be displayed.
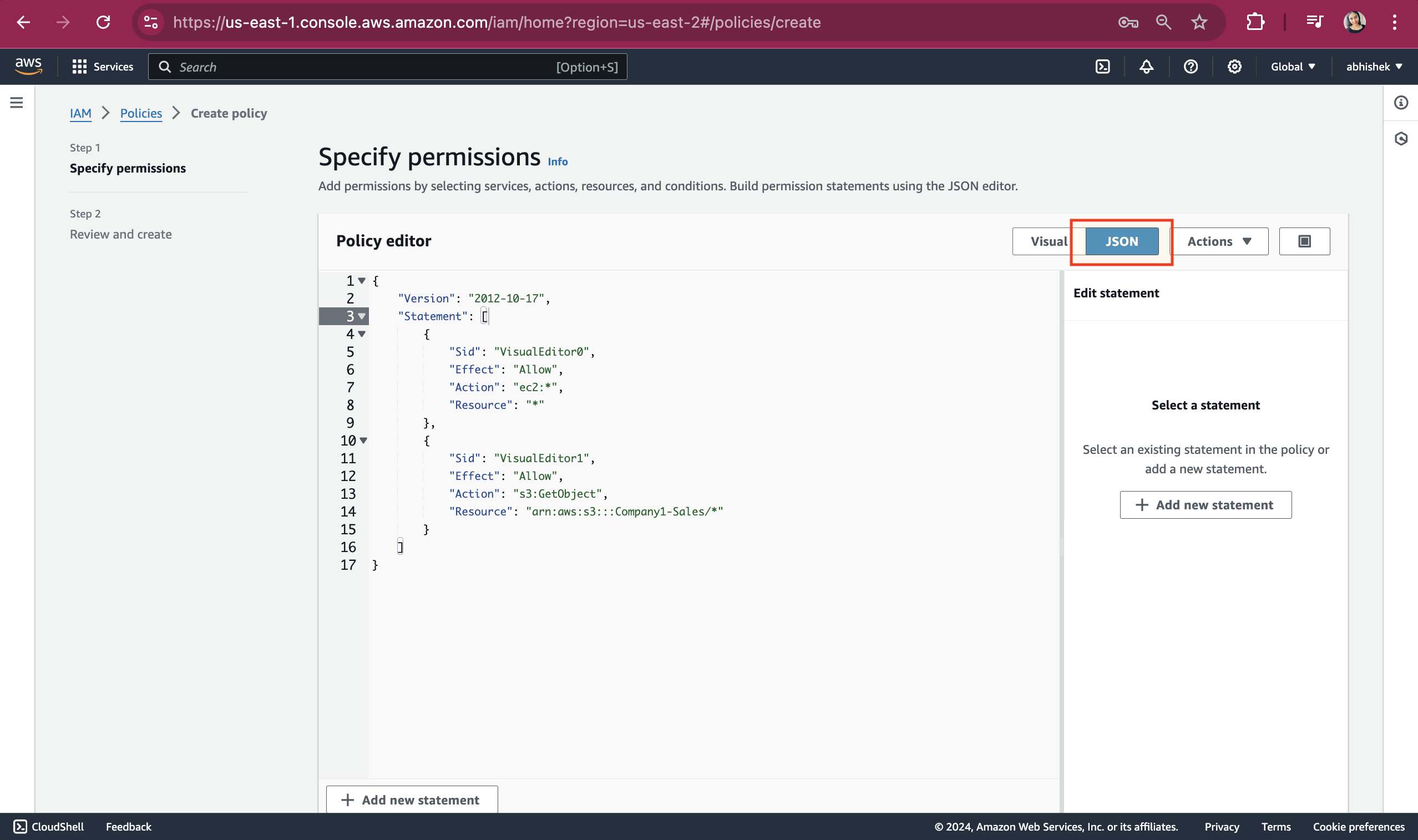
Add the highlighted part in your json editor.
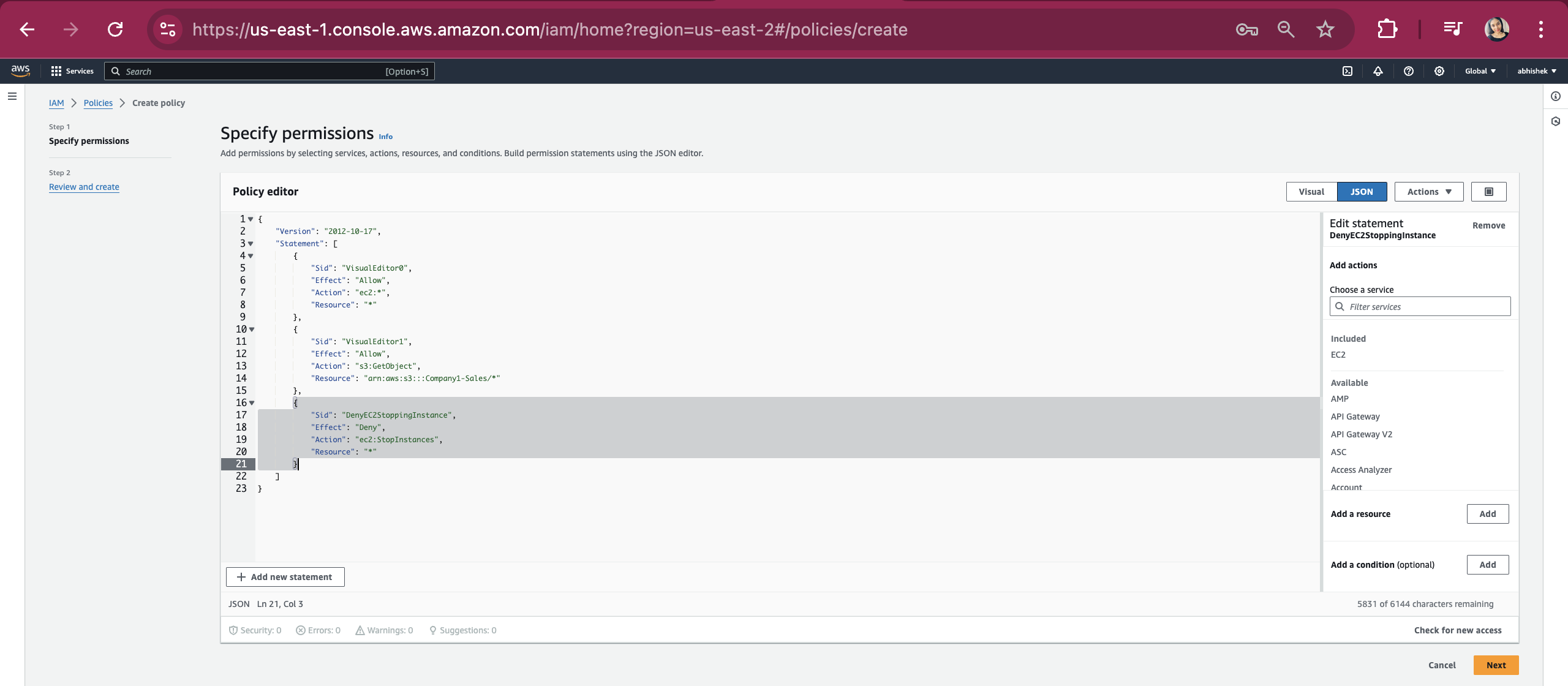
Click Visual and check if we have all 3 permissions listed, 2 Allow and 1 Deny. Once done click on Next button
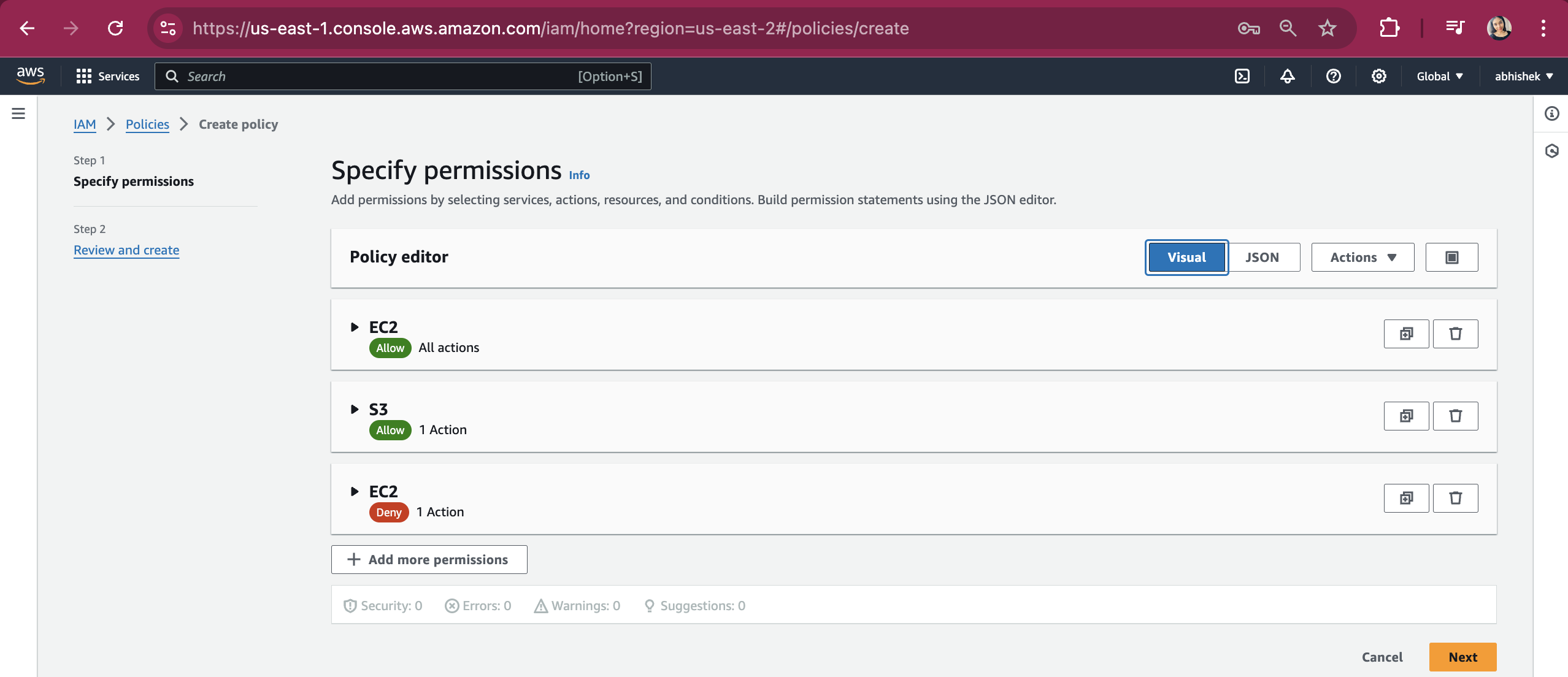
Provide Policy name and click on "Create policy" button
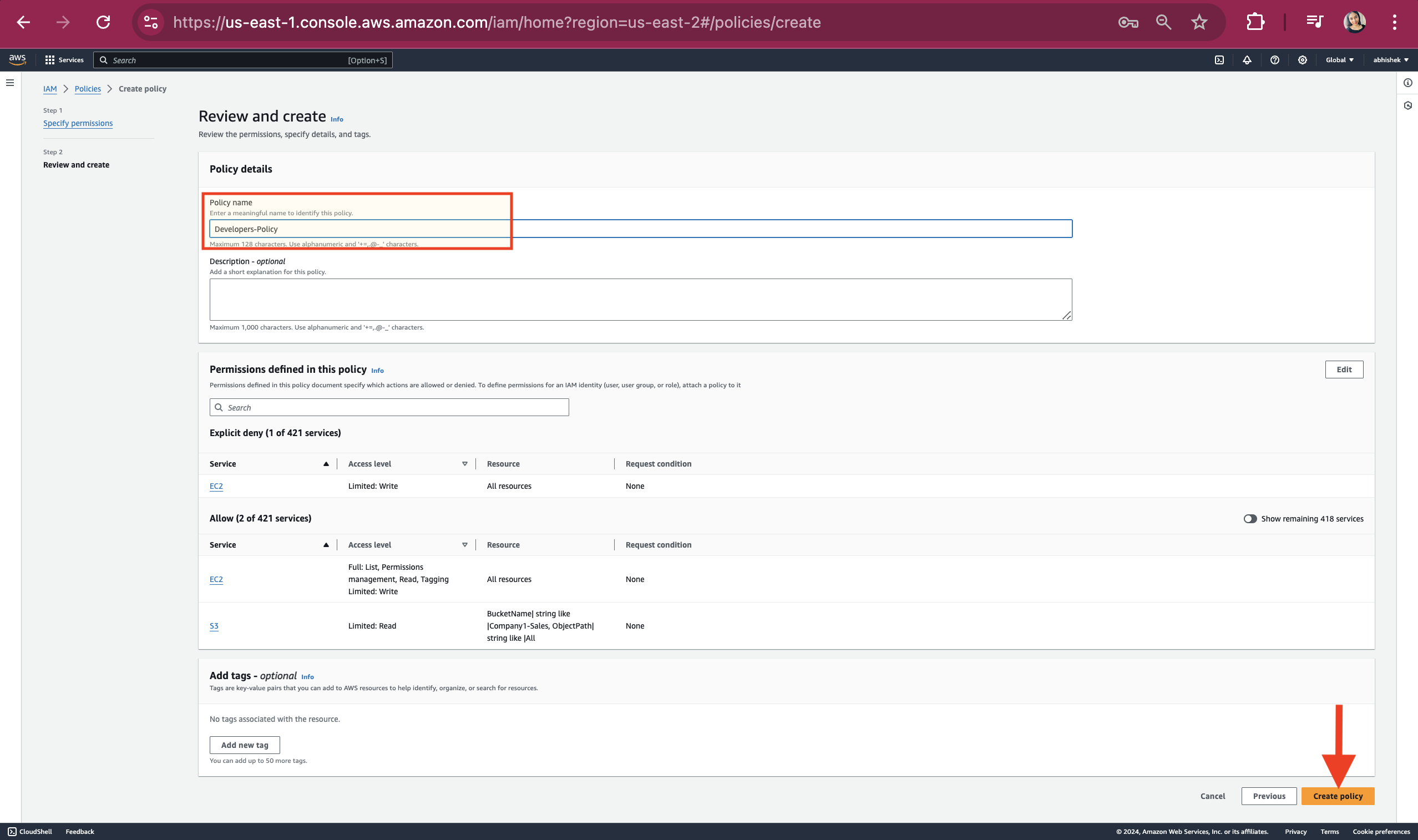
Here we can see our Policy has been created sucessfully
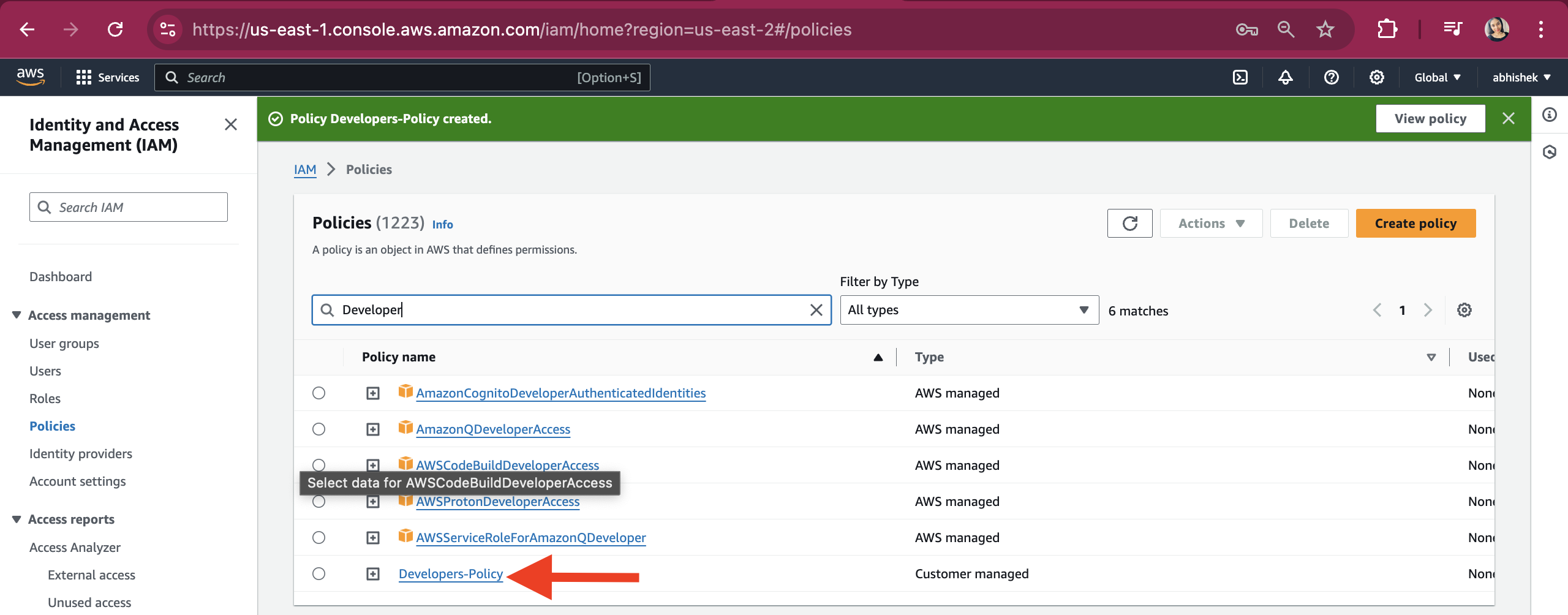
Now we can add this policy to our "Developers" group. Go to the User group page. Select the Developers group and, under the Permissions section, click on "Attach policies."
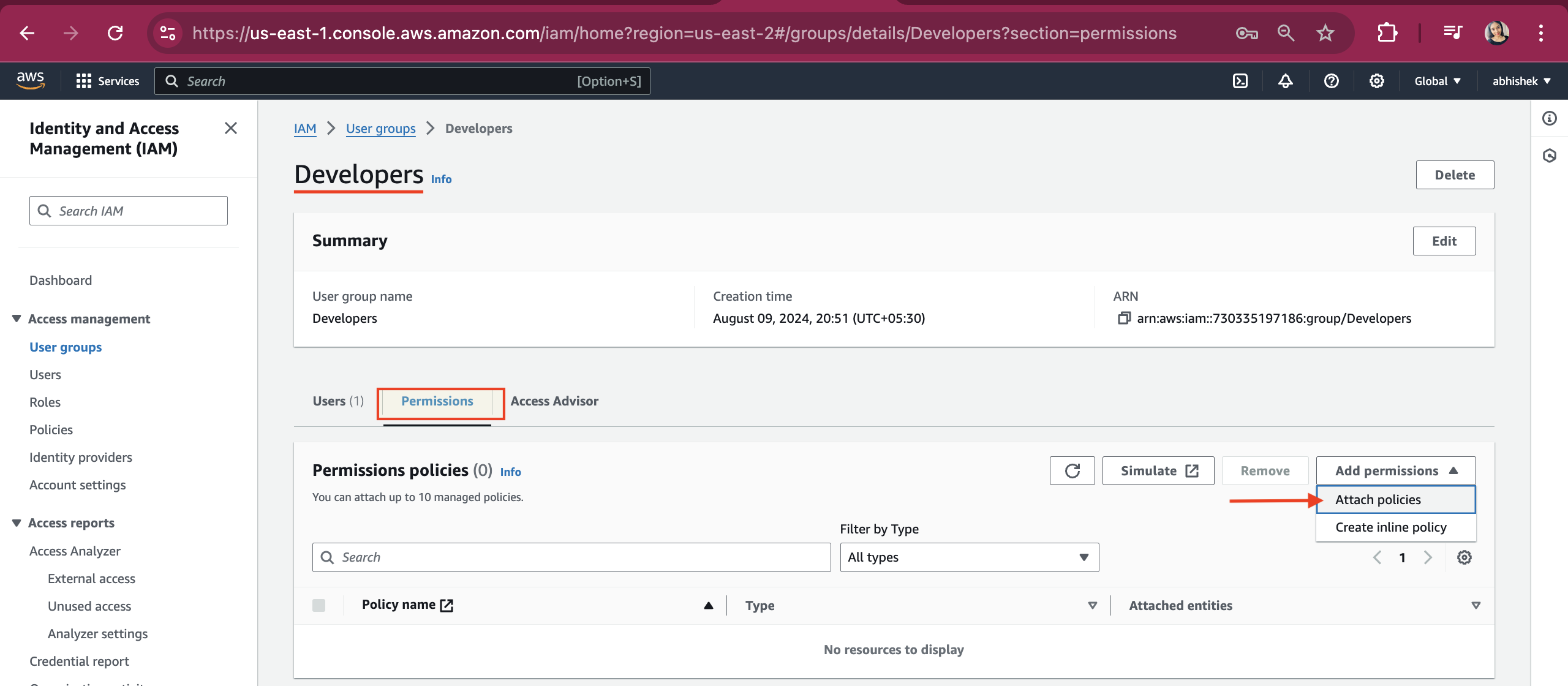
Search for Developers-Policy, check the checkbox for this policy, and click on the "Attach policies" button.
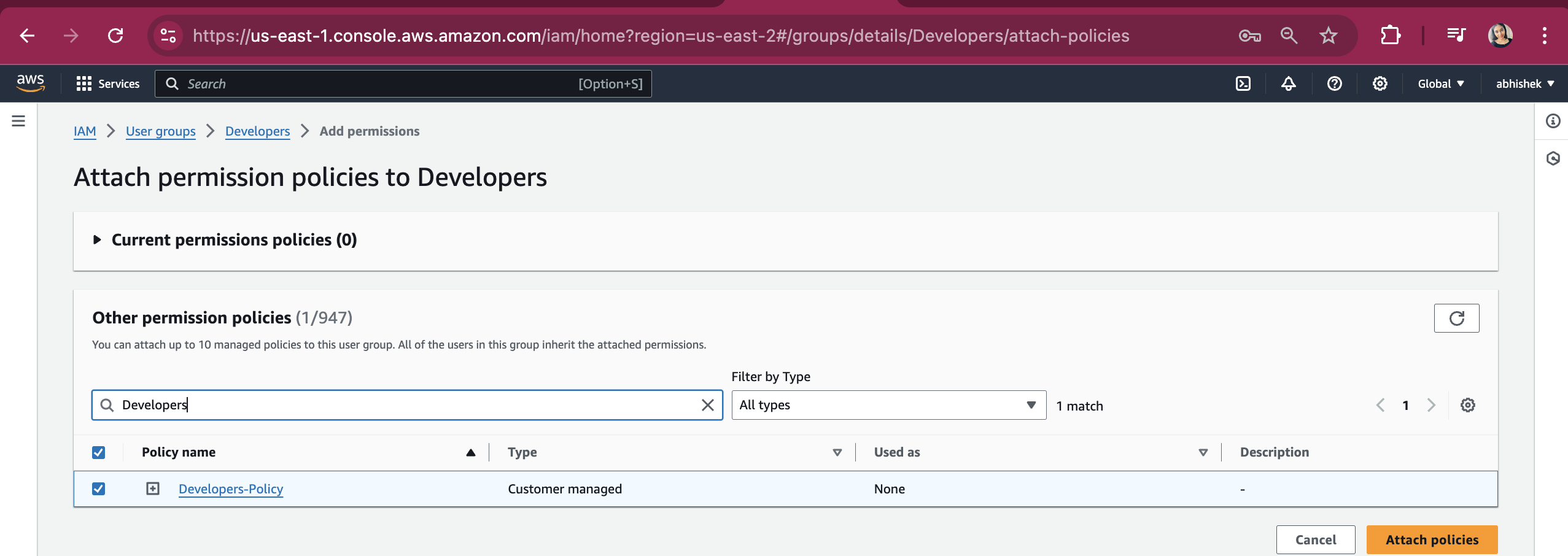
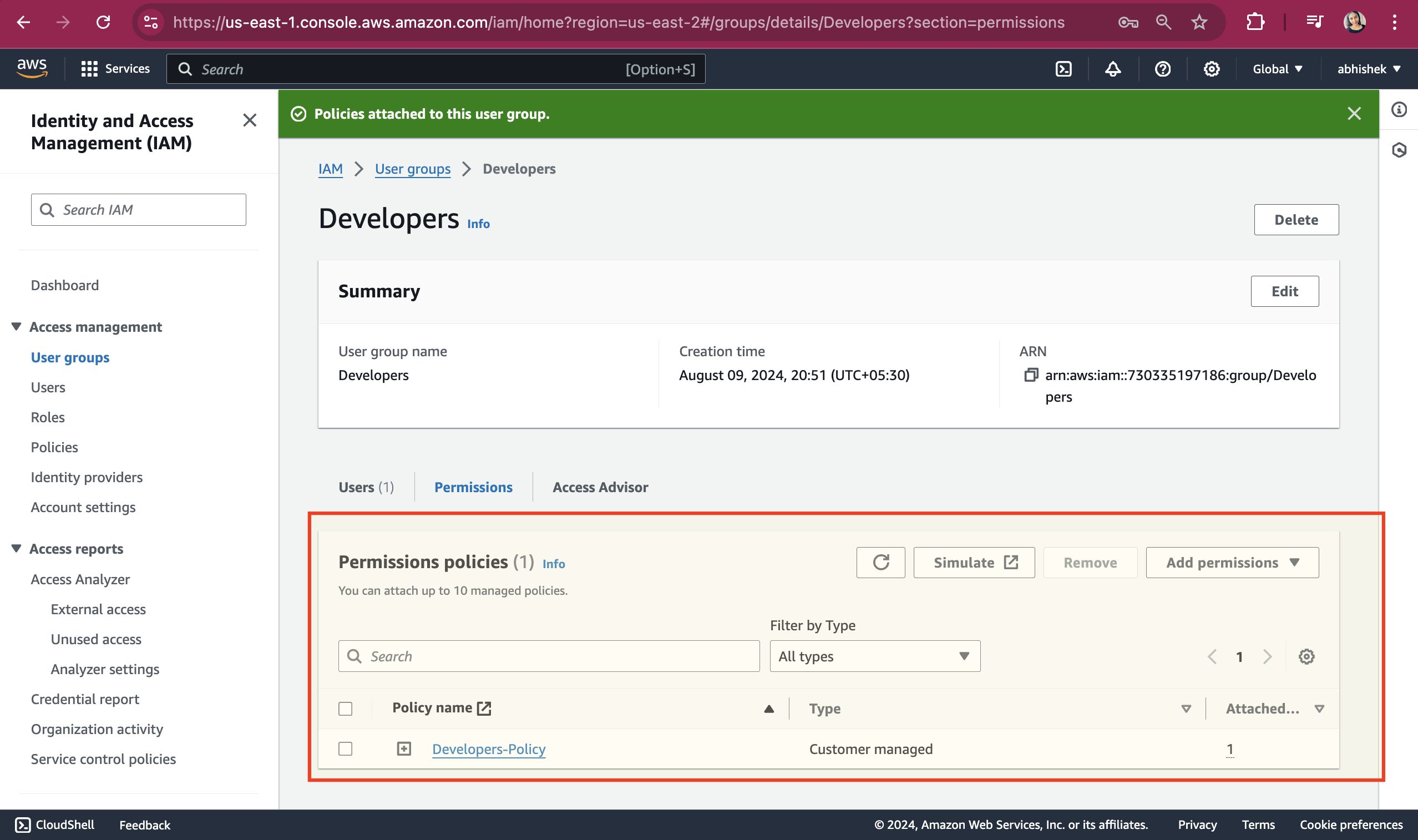
The Developers-Policy has been successfully attached to the Developers Groups.
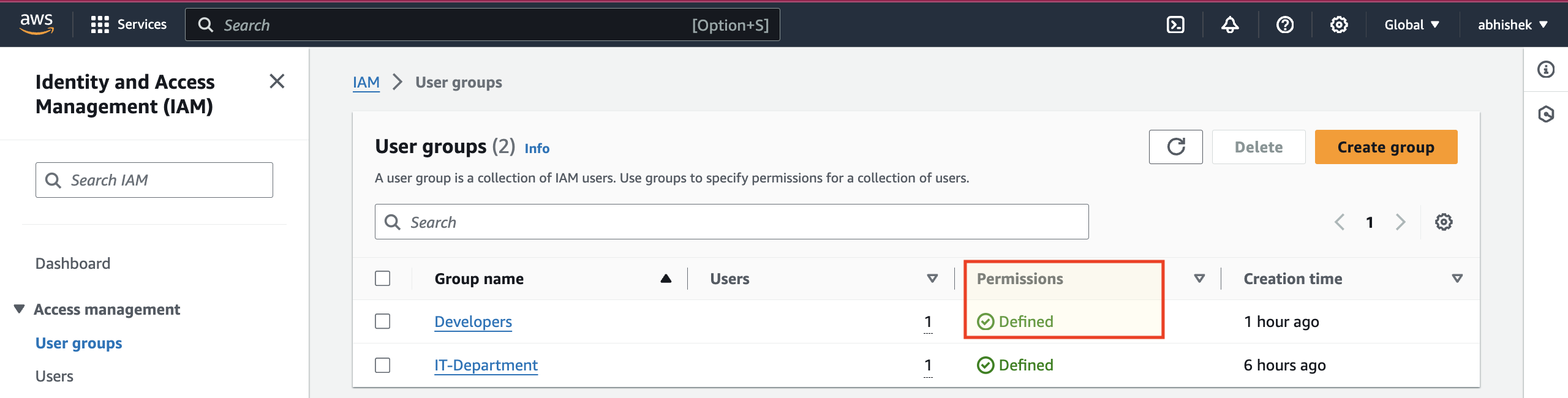
Resource based policies:
Policies attached to AWS resources, for example s3 bucket or lambda service.
This will be covered in another article: https://vandanapandit.hashnode.dev/aws-resource-policies-simple-steps-to-build-resource-based-policies
Subscribe to my newsletter
Read articles from Vandana Pandit directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Vandana Pandit
Vandana Pandit
👩💻 I am currently working as Infrastructure Engineer. 🔭 I’m currently preparing for CKA certification. 📝 Do check my linked post I keep posting articles related to DevOps