Learn like a Baby - Analysing Azure for Hunting 2 - Azure Kill chain
 raja mani
raja mani
all of the information are taken from, Necessary for the part 2 of the learning like a baby
Whats the attack Path in Azure Cloud ?
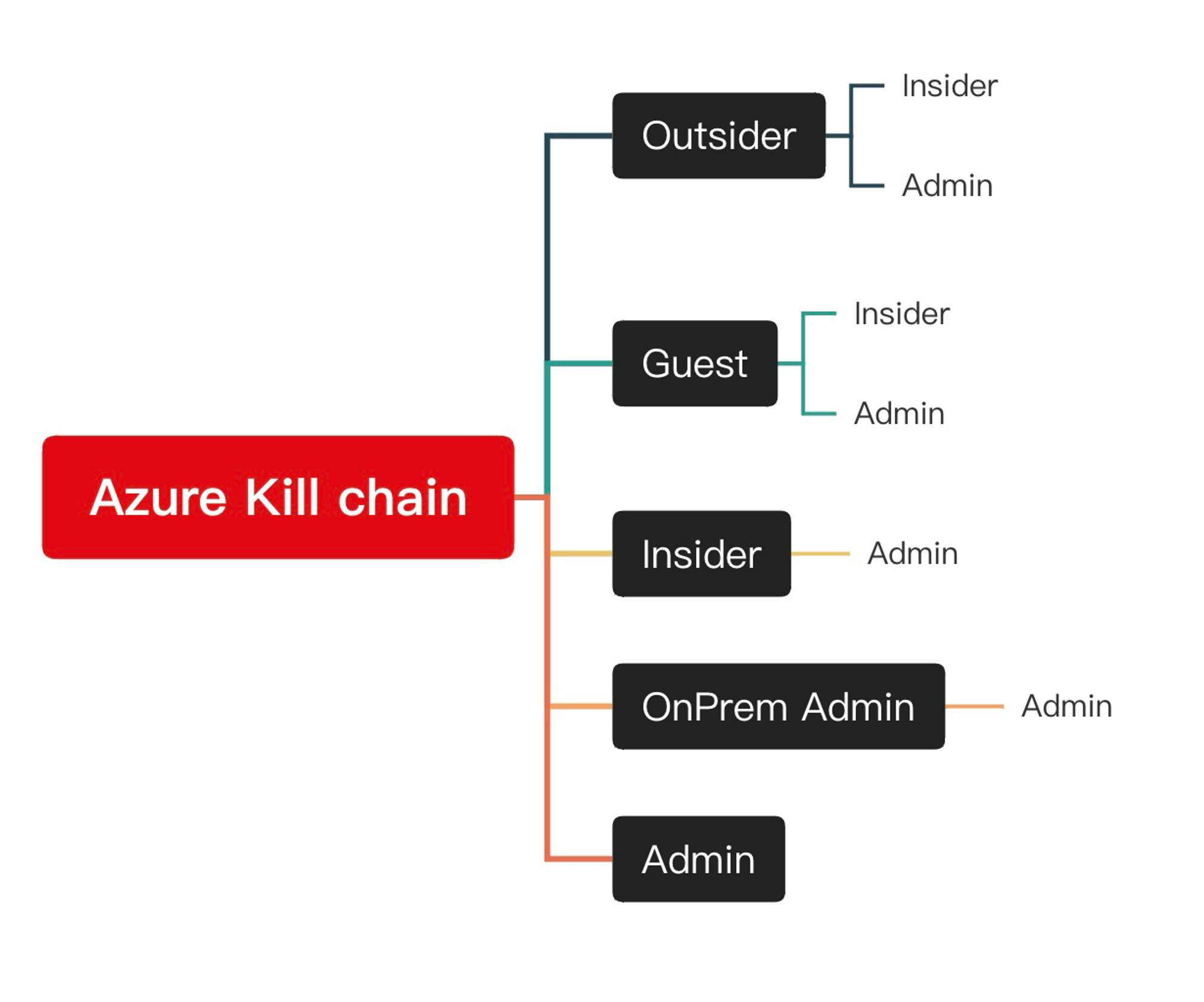
The kill chain consists of five different roles: outsider, guest, insider, admin, and on-prem admin. Typically, outsiders are aiming for guest, insider, or admin roles. Similarly, guests are aiming for insider or admin roles. Insiders can already do much harm, but to get “keys to the kingdom” they often are aiming for (cloud) admin role. This is same for the on-prem admin.
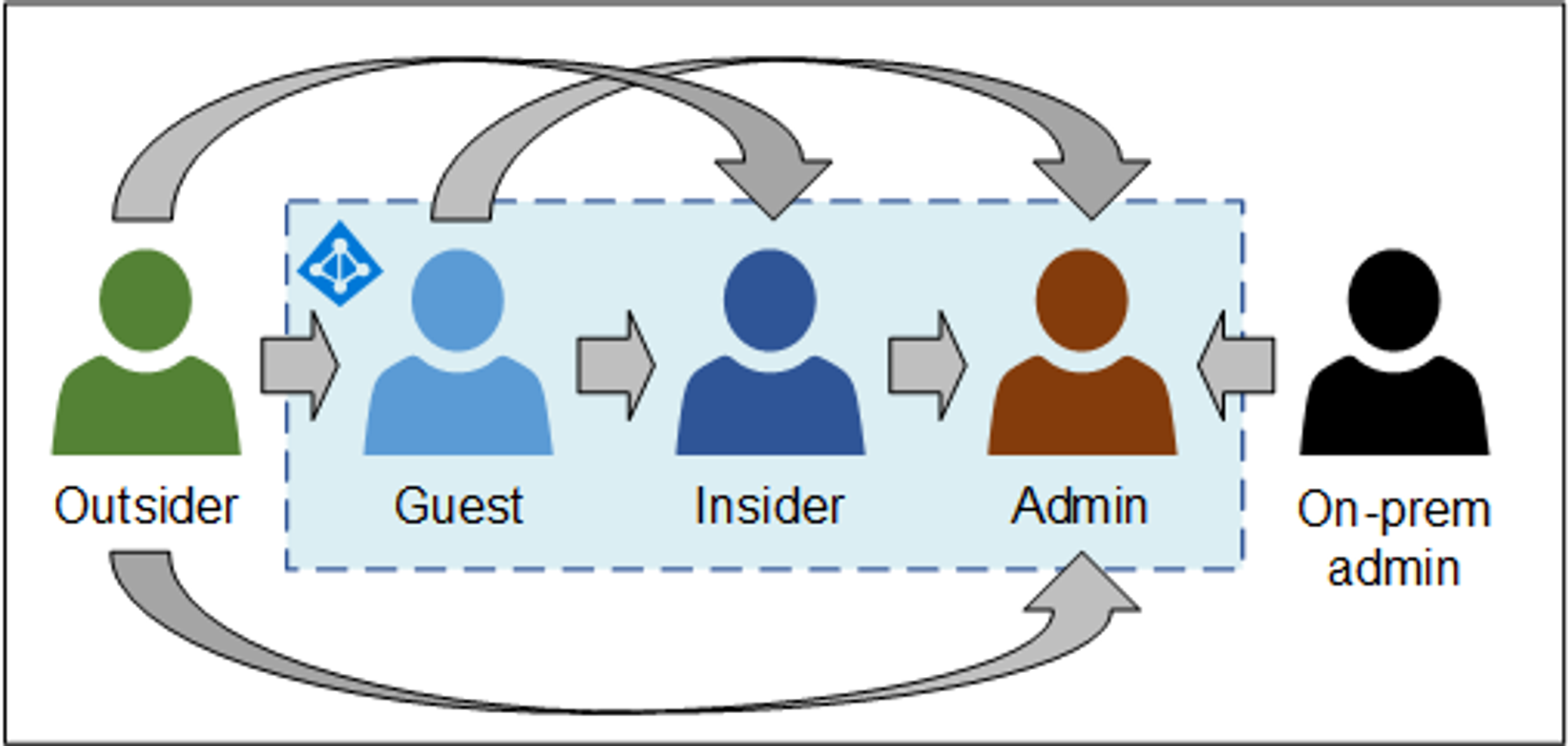
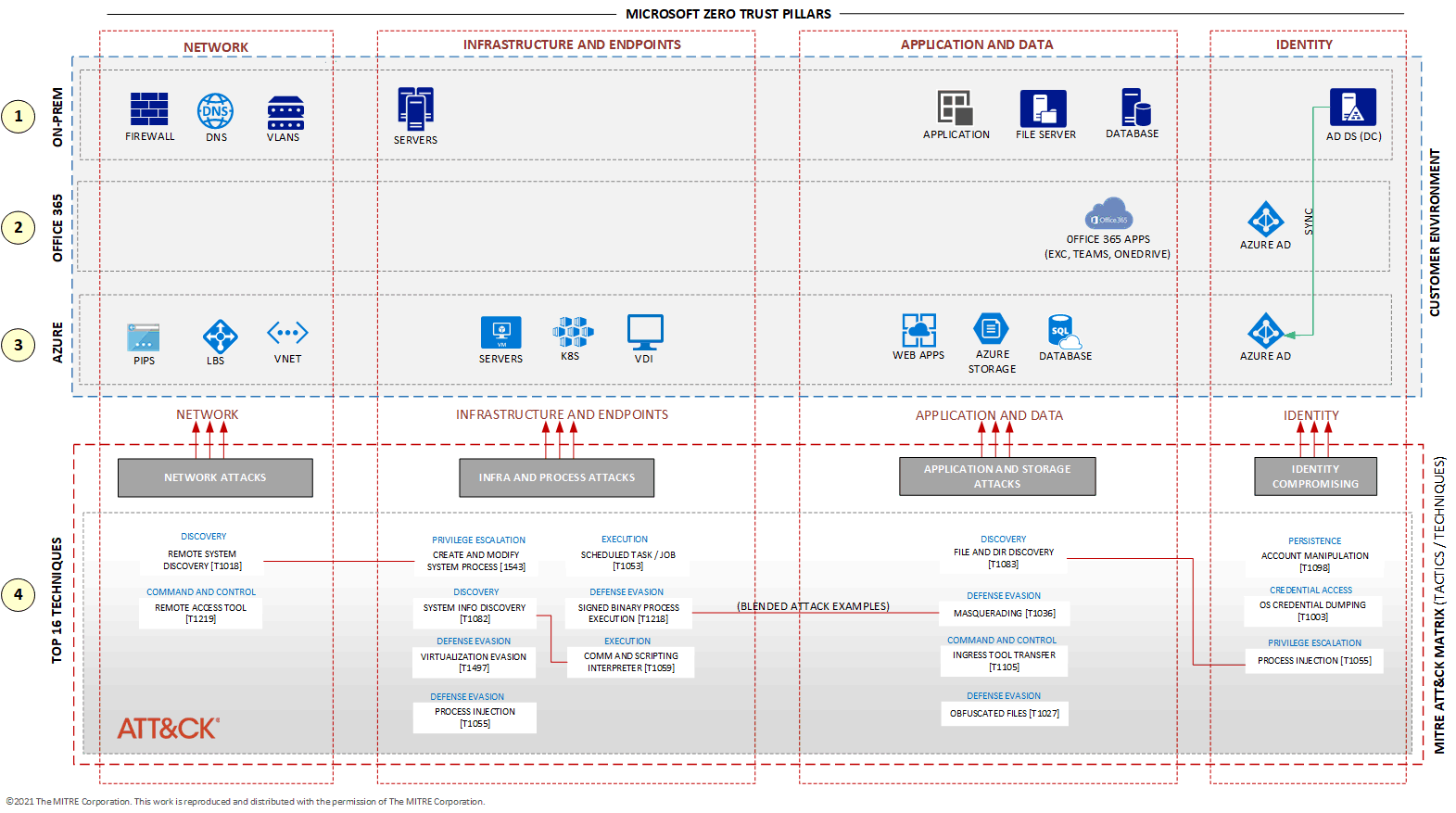
another representation
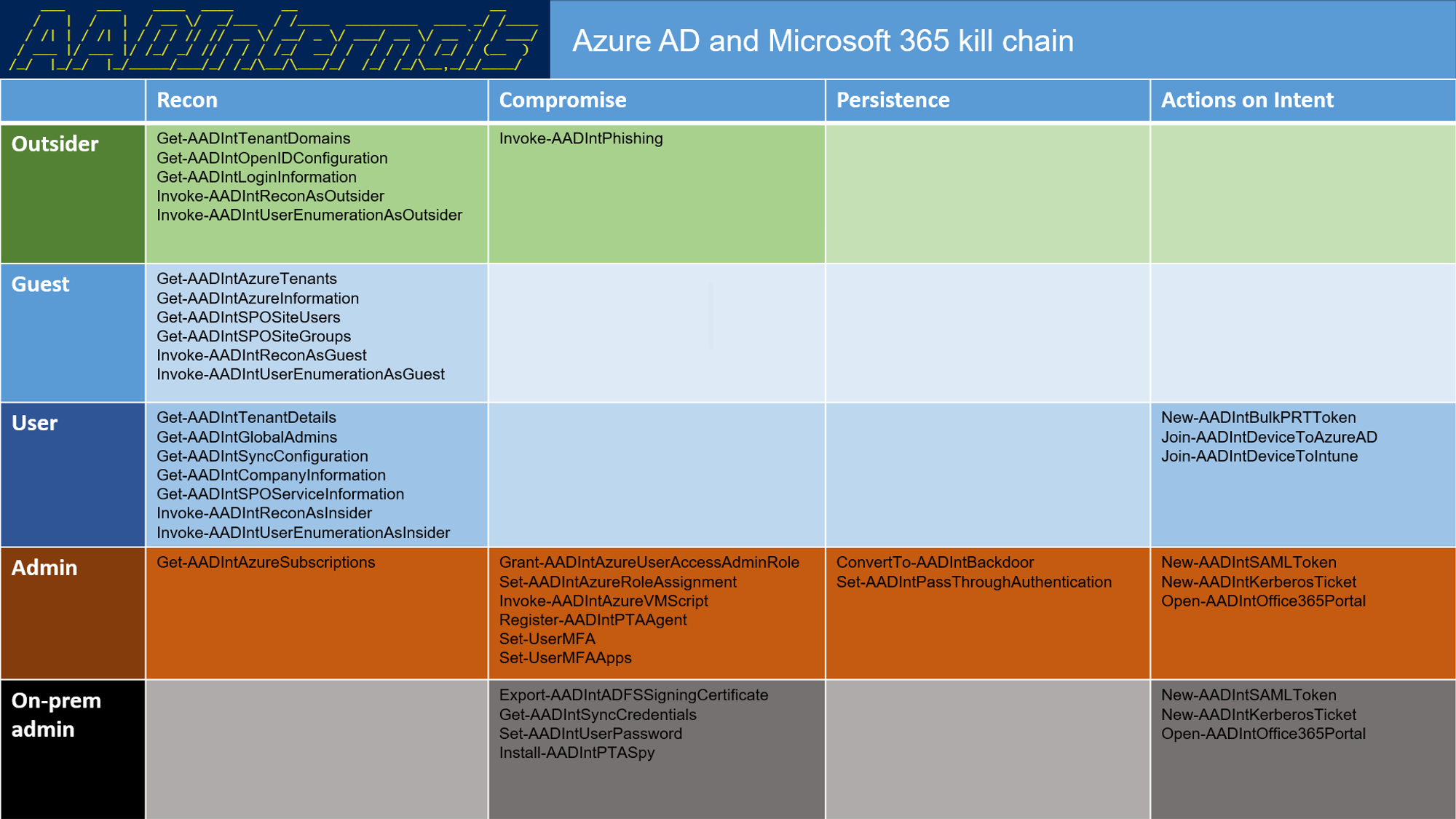
Also look below the AAD internals offense tools mapping on their commands
Outsider
Outsider refers to an user who has no access to the tenant of the target organisation.
Outsiders can extract information from any tenant using publicly available APIs and DNS queries.
The ultimate goal of an outsider is to gain guest, user, or admin role.
Guest
Guest refers to an user who has guest access (external user) to the target tenant. These users have a restricted access to Azure AD, but they can gather a lot of information from tenant using various APIs provided by Microsoft. For instance, guests can easily read the whole Azure Active Directory (AAD) using MS Graph API.
User (insider)
User refers to “normal” users of the tenant. They have read-only access to practically all information in AAD. However, users are also able to invoke Denial-of-Service (DoS) attacks against their own tenant by filling the Azure AD with user or device objects, making it practically unusable.
Admin
Admin refers to a Global Administrator role. Global admin has an unlimited access to all settings in the tenant. As such, they can change security settings, access any data, and create back doors.
On-prem admin
On-prem admin refers to an administrator who is administering on-prem servers running Azure AD Connect, Active Directory Federation Services (AD FS), or Active Directory.
On-prem admins doesn’t have direct access to the cloud, but they can dump Azure AD Connect credentials and gain admin rights to cloud.
If organisation is using Desktop SSO (also known as Seamless SSO), on-prem admin can dump the MD4 hash of AZUREADSSO computer account password and create Kerberos tickets to login as any user of the tenant.
Similarly, If organisation is using identity federation, on-prem admin can export the token signing certificates and sign in as any user of the tenant and bypass MFA!
Hold your Breath! Now comes the total kill chain for an Hybrid infrastructure :)
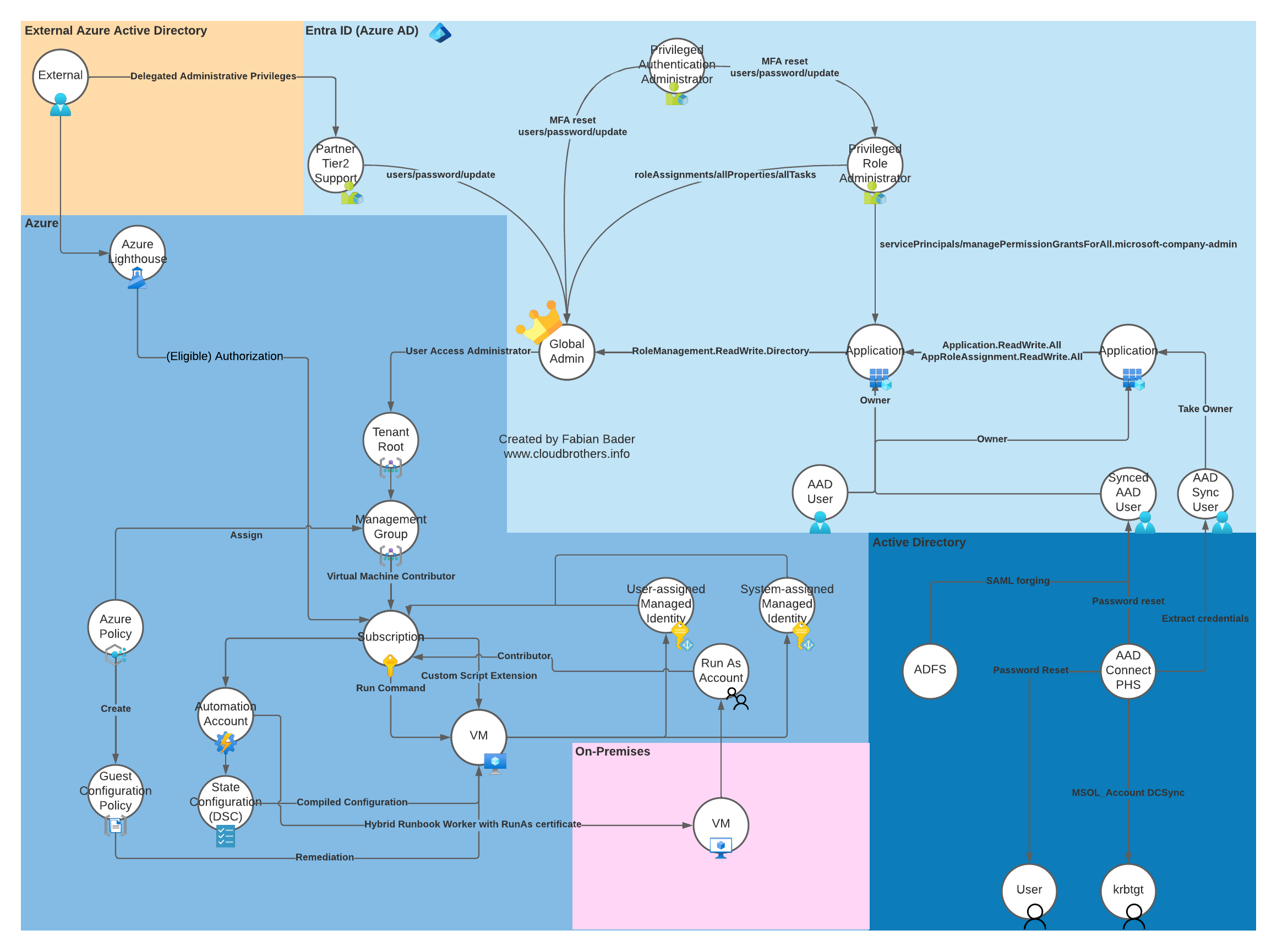
Onprem to Global Admin
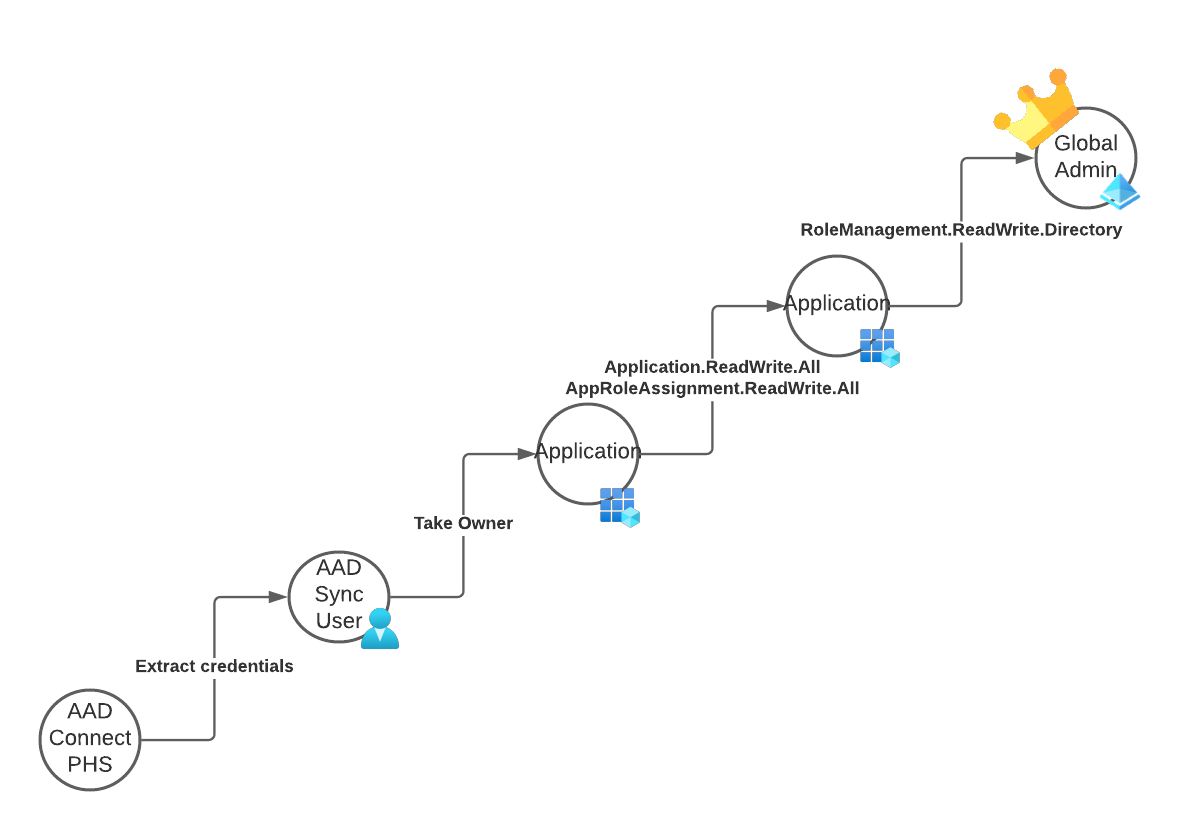
another example of cloud to endpoint movement using ruler exploit

Subscribe to my newsletter
Read articles from raja mani directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

raja mani
raja mani
✨🌟💫Threat Hunter 💫🌟✨