What Is The Difference Between Authentication And Authorization
 ADELEKE OLUWAFUNMILAYO
ADELEKE OLUWAFUNMILAYO
Authentication and authorization are two key concepts in the world of security, often used together but serving different purposes:
Authentication:
Purpose: Verifies the identity of a user or system.
Example: When you log into your email account, you enter your username and password. The system checks these credentials to ensure you are the rightful owner of the account.
Authorization:
Purpose: Determines what resources or actions an authenticated user is allowed to access.
Example: After logging into your email, you can read and send emails, but you might not have access to administrative settings unless you are an admin.
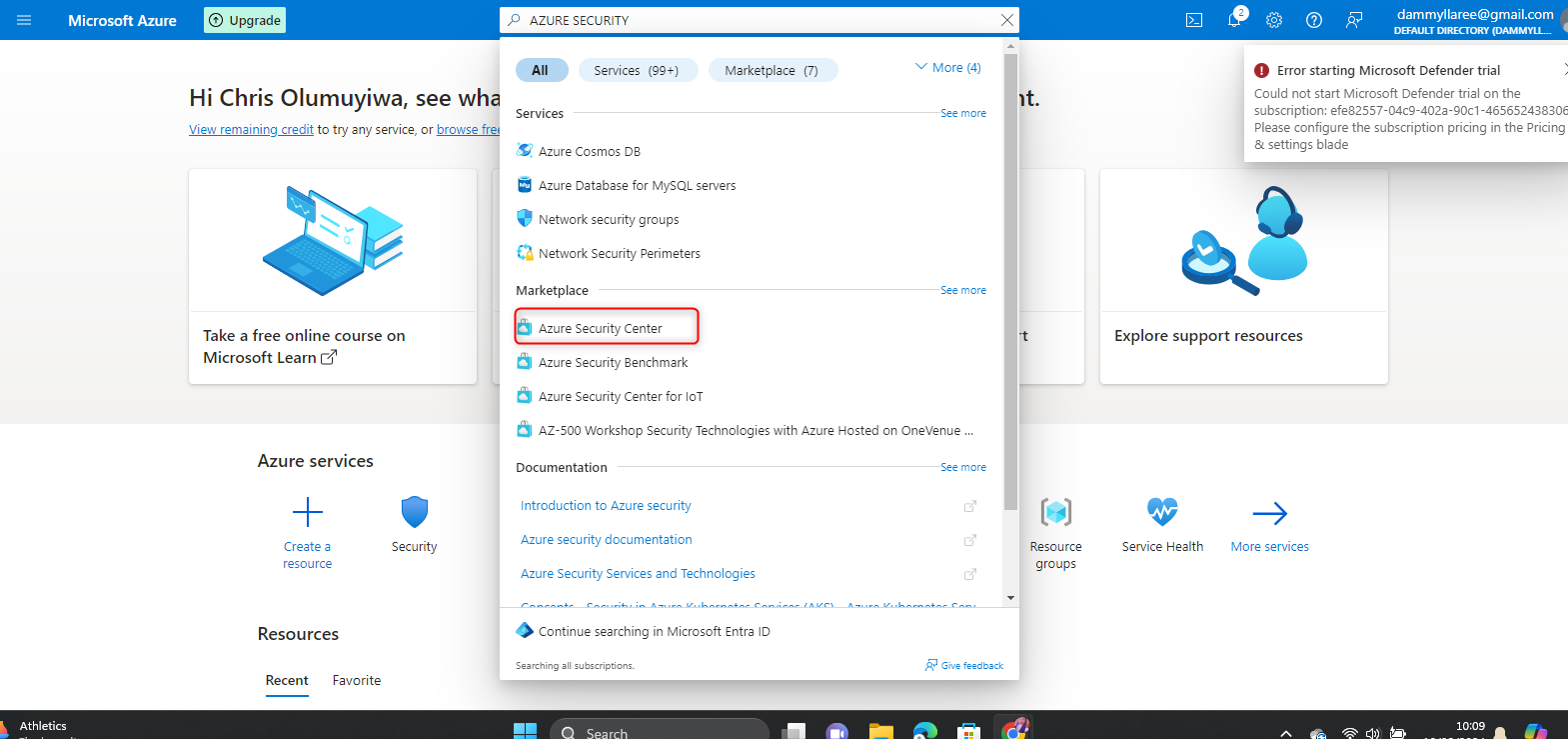
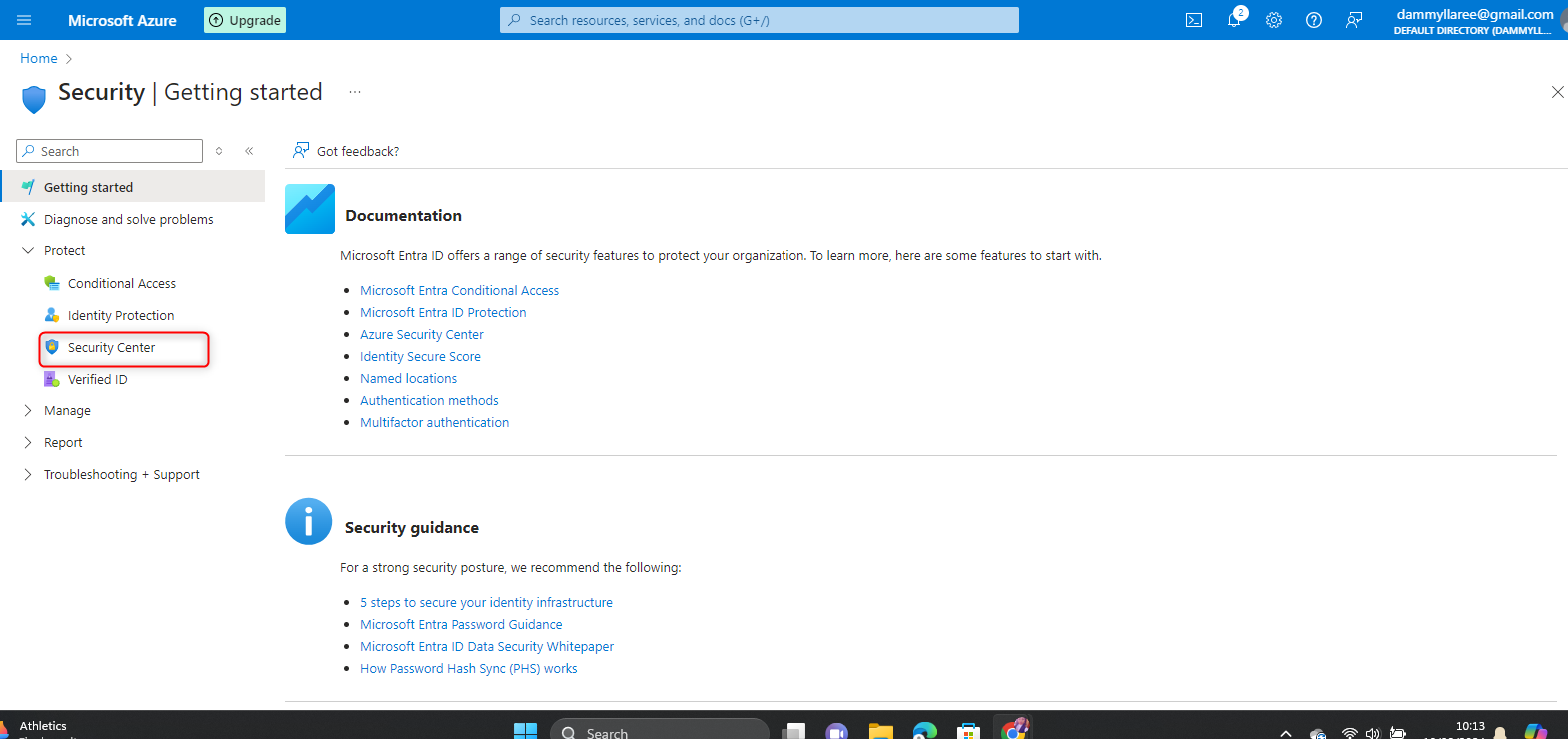
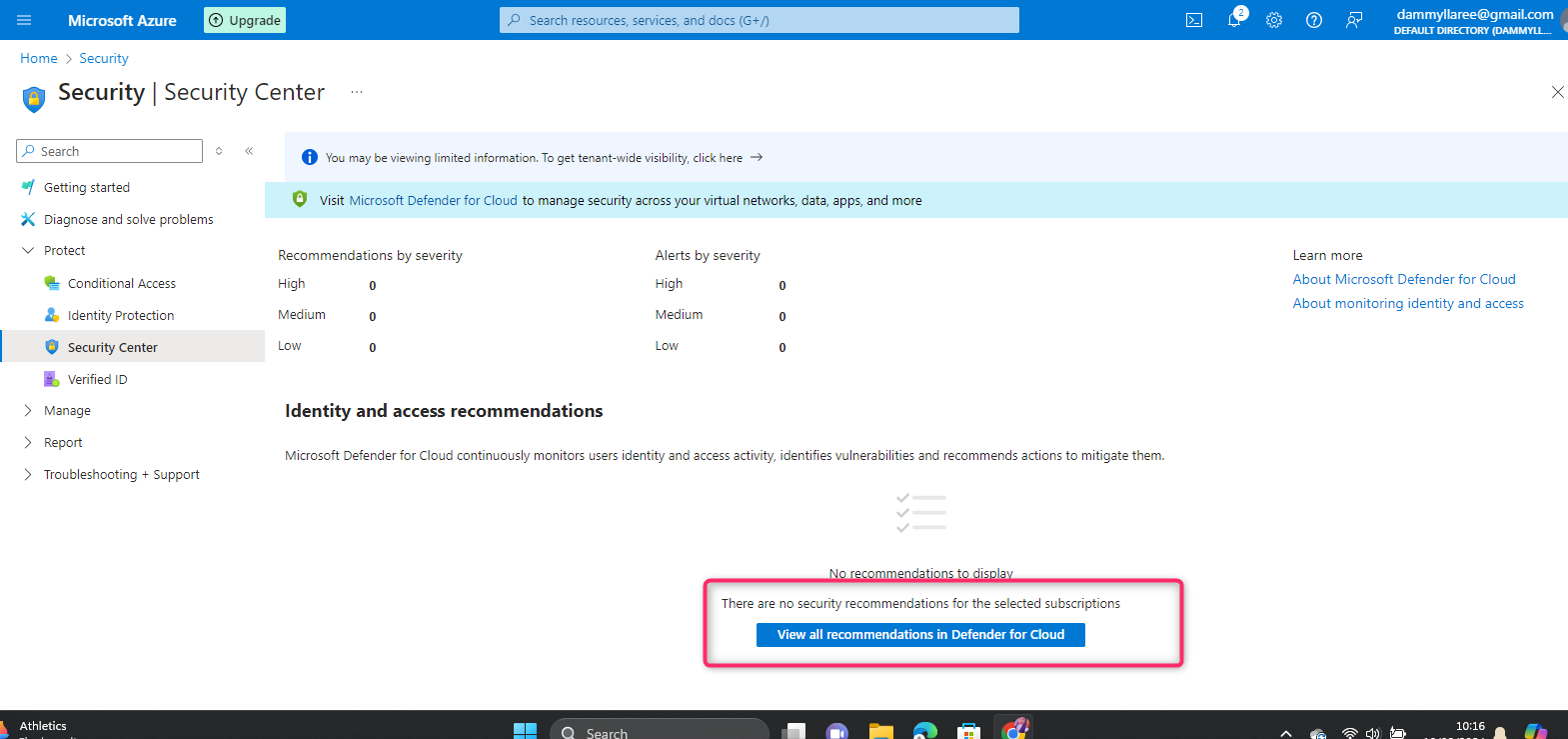
WHAT IS SECURITY POLICY IN SECURITY CENTRE?
A security policy in a security center, such as Azure Security Center, defines the desired configuration and set of controls for your resources to ensure they meet your company’s security requirements and regulatory standards. Here are some key points:
Purpose:
Ensures that your workloads comply with security standards and regulatory requirements.
Helps in maintaining the confidentiality, integrity, and availability of your data.
Components:
Security Standards: Define rules and compliance conditions for your resources.
Application:
Benefits:
Continuous monitoring and assessment of your security posture.
Automated recommendations and remediation steps to address security issues.
WHAT ARE THE TYPES OF LOCKS YOUN HAVE IN AZURE\
In Azure, there are two main types of resource locks that help prevent accidental changes or deletions:
Read Only (Read-only) Lock*:*
Purpose: Prevents any modifications to the resource.
Effect: Authorized users can read the resource but cannot delete or update it.
Can Not Delete (Delete) Lock*:*
Purpose: Prevents the resource from being deleted.
Effect: Authorized users can read and modify the resource but cannot delete it.
These locks can be applied at different scopes, including subscriptions, resource groups, and individual resources. When a lock is applied at a higher scope, all child resources inherit the same lock
Subscribe to my newsletter
Read articles from ADELEKE OLUWAFUNMILAYO directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
