Resolving Security Group Creation Errors and Successful EC2 Setup with AWS CLI
 Manjot Singh Bajwa
Manjot Singh BajwaI referred to the How to Use AWS CLI to Create an EC2 instance while setting up an EC2 instance. During the process, I encountered an issue with the security group creation command due to an unsupported --tag-specifications option. After troubleshooting, I successfully resolved the error and proceeded with the instance setup. Below is how I did it
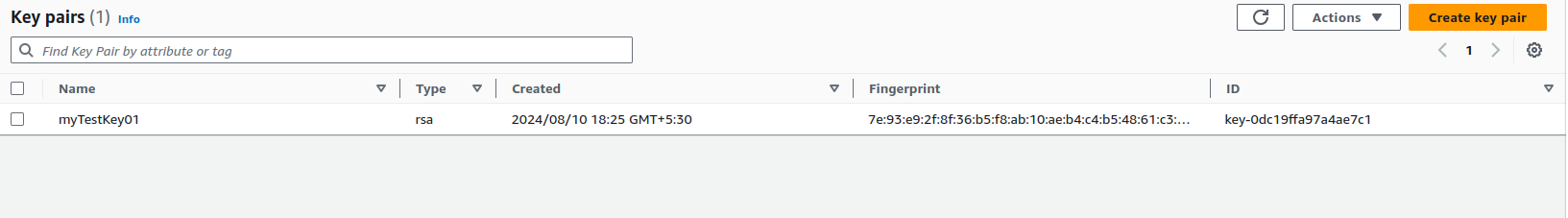
Creating a Key Pair
To create a key pair using the AWS CLI, run the following command:
aws ec2 create-key-pair \
--key-name wp-key-03 \
--query 'KeyMaterial' --output text > ~/demo-key
Make sure the ~/demo-key file path exists before executing the command.
After successfully downloading the key, set the permissions:
chmod 400 ~/demo-key
Creating a Security Group with AWS CLI
The following command in the doc i refered attempts to create a security group but will result in an error:
bashCopy codeaws ec2 create-security-group \
--group-name demo-sg \
--description "AWS EC2 CLI Demo SG" \
--tag-specifications 'ResourceType=security-group,Tags=[{Key=Name,Value=demo-sg}]' \
--vpc-id "vpc-************"
Error Explanation
The command returns an error message:
bashCopy codeusage: aws [options] <command> <subcommand> [<subcommand> ...] [parameters]
To see help text, you can run:
aws help
aws <command> help
aws <command> <subcommand> help
Unknown options: --tag-specifications, ResourceType=security-group,Tags=[{Key=Name,Value=demo-sg}]
This error occurs because the --tag-specifications option is not supported when creating a security group using the aws ec2 create-security-group command. Tags can be added to the security group after it's created.
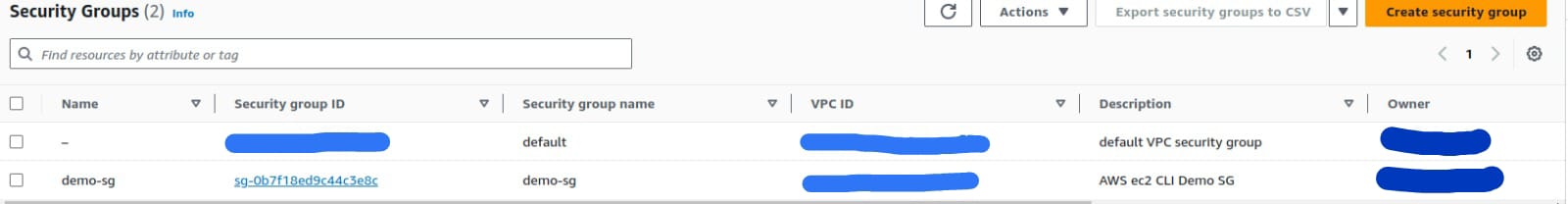
Correct Command
Here’s the correct command to create the security group without the --tag-specifications option:
bashCopy codeaws ec2 create-security-group \
--group-name demo-sg \
--description "AWS EC2 CLI Demo SG" \
--vpc-id "vpc-************"
It will return something like this:
jsonCopy code{
"GroupId": "sg-0b7f18ed9c44c3e8c"
}
After the security group is created, add tags to it using:
aws ec2 create-tags \
--resources "sg-0b7f18ed9c44c3e8c" \
--tags Key=Name,Value=demo-sg
To find the security group ID later, you can describe the security groups:
aws ec2 describe-security-groups --filters Name=group-name,Values=demo-sg
Adding Ingress Rules to the Security Group
Add inbound (ingress) firewall rules to allow SSH access:
aws ec2 authorize-security-group-ingress \
--group-id "sg-0b7f18ed9c44c3e8c" \
--protocol tcp \
--port 22 \
--cidr "0.0.0.0/0"
Creating an EC2 Instance with AWS CLI
You'll need the following information:
VPC ID:
vpc-************Subnet ID:
subnet-************AMI ID:
ami-************Security Group ID:
sg-************
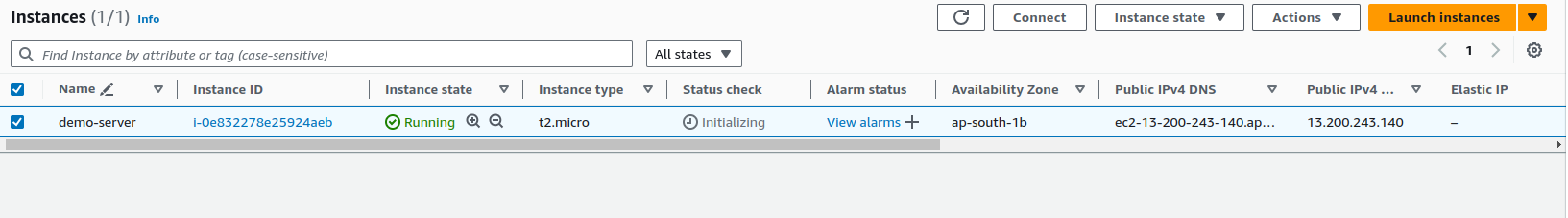
Use the following command to create an EC2 instance:
aws ec2 run-instances \
--image-id ami-************ \
--count 1 \
--instance-type t2.micro \
--key-name myTestKey01 \
--security-group-ids sg-0b7f18ed9c44c3e8c \
--subnet-id subnet-************ \
--block-device-mappings "[{\"DeviceName\":\"/dev/sdf\",\"Ebs\":{\"VolumeSize\":30,\"DeleteOnTermination\":false}}]" \
--tag-specifications 'ResourceType=instance,Tags=[{Key=Name,Value=demo-server}]' 'ResourceType=volume,Tags=[{Key=Name,Value=demo-server-disk}]'
The command will return information about the instance, including the Instance ID and other details.
Connecting to the EC2 Instance
To log in to the instance via SSH, use the following command:
ssh -i "demo-key" ubuntu@13.200.243.140
You can replace 13.200.243.140 with the public IP address of your instance
By following the steps outlined and troubleshooting the encountered issues, I successfully set up an EC2 instance using the AWS CLI.
Subscribe to my newsletter
Read articles from Manjot Singh Bajwa directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Manjot Singh Bajwa
Manjot Singh Bajwa
I'm experienced in designing scalable software architecture on a higher level and lower level implementation. Ensures the smooth functioning of technical operations by monitoring and evaluating staff progress. Involved in the training and recruitment process, works for company goals, and ensures overall client satisfaction.