Deep Dive into Linux Namespaces: Building Your Own Containers
 Kelvin Parmar
Kelvin Parmar
In the development of software, containerization has changed how software is deployed in the application system. Again, this has been made easier and more efficient by technologies such as Docker, although many developers might not fully comprehend the container technologies. Critical to this technology is Linux namespaces, with the focus being isolation for processes as well as resources.
In this blog, we will know about the creation of basic containers from Linux namespaces. This article will examine how these namespaces function, the procedure of creating a container environment, advantages, and disadvantages of this framework. From a new developer anticipating what containerization is and its application, or an experienced developer who desires a study on the contemporary approaches toward application deployment, this guide should serve to be informative in simplifying the fundamentals in the field.
Nowadays
Docker is of course one of the leading technologies for containerization. However, knowing the details of the inner workings of the software can be a source of great ideas for the optimization of your containerization strategy. This blog post is about whether or not the future or benefits of such containers could be made if they were built from scratch with the usage of Linux namespaces.
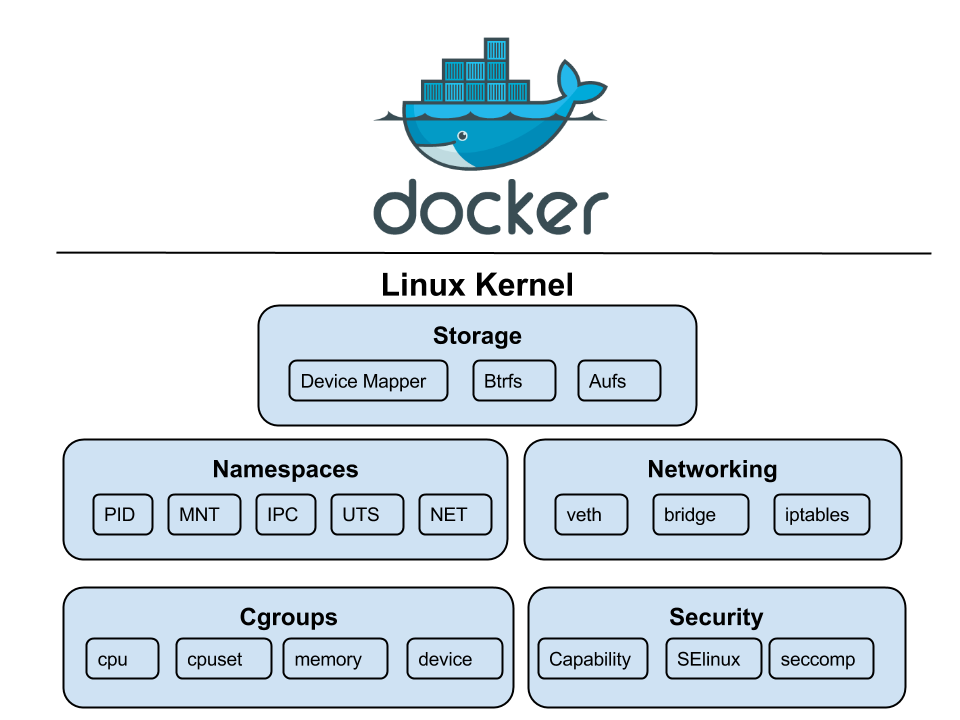
Understanding Linux Namespaces
At the heart of containerization are Linux namespaces. They are the ones that make it possible to isolate system resources such as process IDs, network stacks, file systems, and so on. By doing so, we can create parallel systems within a hosting server. In other words, the CPU, memory, and other resources are bent to the will of the container like pieces on a chessboard but without interference with the host or other containers.
Key namespaces for containerization:
PID namespace:
By isolating the process IDs, we can fake a number of parallel processes that seem to be independent of each other.
Network namespace:
With this technology, separate stacks of the network are formed, hence containers can have their own IP address and network interface.
Mount namespace:
With mount namespaces, it is possible to create isolated mount points, which means a certain filesystem is only visible in some containers.
UTS namespace:
UTS namespaces encapsulate the hostname and domain name, so every container has its own isolated identity.
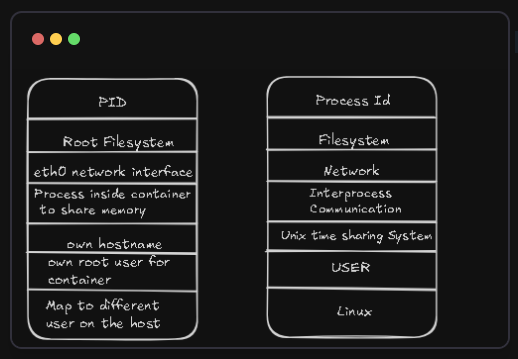
Building a Container from Scratch
While in theory perceived and basically possible, the construction of a container from its foundations up by using the so-called Linux namespaces seems to be quite a hard and energy-sapping task. It involves:
Creating a new process: Inject a new process by calling the clone system command and setting a process with the given namespace settings as the child.
Configuring namespaces: Process ID, Network, Mount, and UTS names will be the settings that will be made in the process namespace.
Mounting the root filesystem: creating a disk space as storage for reading words that point to the root filesystem of the virtual machine.
Managing process lifecycle: Taking care of the process creation, termination, and the proper management of all the resources are still the things that should be done within that container.
Challenges and Considerations
Complexity: Manually handling namespaces, system calls, and proper use of resource allocation are both volatile and complicated processes.
Security: A deep understanding of Linux security mechanisms, such as proper isolation and security, is vital for securing security mechanisms in Linux.
Performance: Achieving the best possible performance is not a simple task when container runtimes are not optimized like Docker.
Tooling and Ecosystem: Electron, similar to Docker and other container runtimes, has become a widely used and very user-friendly program, which is great for controlling system overheads.
When to Consider Building from Scratch
In spite of the difficulties, certain cases may still necessitate the construction of containers from zero.
Extreme performance: In the case of highly tuned tasks, the precise name space enforcement may be accessed to create some speed improvements.
Security-critical applications: In the case of a security-conscious circumstance where the environment is highly secure, the management of such resources through constructing containers from scratch is possible.
Educational purposes: Sound knowledge of the fundamentals of containerization is indispensable for learning and experimentation.
Conclusion
While technically feasible, building containers from scratch using Linux namespaces is generally not recommended for most use cases. Mature container runtimes like Docker offer a more efficient and reliable approach. However, understanding the underlying concepts can be beneficial for troubleshooting, optimization, and advanced containerization scenarios.
In most cases, using a mature container runtime like Docker is the preferred approach.
Subscribe to my newsletter
Read articles from Kelvin Parmar directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Kelvin Parmar
Kelvin Parmar
I am B.tech Graduate who is Passionate about Tech and Open Source. Programmer with a good sense of design. Learning and sharing in Public and helping the tech communities. I write about my experiences, tech and tools. Educating and Helping people get into Tech and Open Source through my Content.