Build Your Own VPN
 Diksha Jadhav
Diksha JadhavTable of contents
- BYOVPN
- INtroduction
- Why VPNs Caught My Attention
- What's an VPN, Anyway?
- What Is a VPN Connection?
- How does a VPN work
- VPN architecture
- Let's get started with BYOVPN
- A lil backstory about VPNS
- 1980s: TCP/IP and the Public's Introduction to the Internet
- 1990s: The Rise of the Web and Emergence of Early VPN Technologies
- 2000s: VPNs Evolve Alongside Cybersecurity Challenges
- Why Build Your Own VPN?
- Resources:

BYOVPN
INtroduction
you try to learn about something, you're constantly online, jumping from one interesting project to the next, because doing something and debugging seems interesting way to spend my time rather than reading the docs, i mean bleh who does that???
normally we use the internet like this
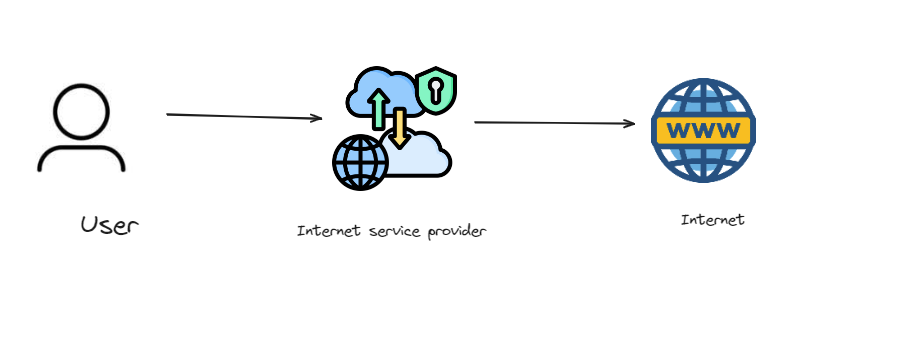
there is a user i.e you using the internet with the help of a ISP (Internet service provider) then they connect you to the internet, all your data like IP addresses and all your queries go through them.
When you use the internet, the data you send or request through a web browser to any server (for example, when Google searching), along with your request, IP address (for example, your laptop or mobile) and destination IP address (like Google) first reaches your ISP.
The ISP monitors all your activity and then forwards your request to the destination IP address and also gets back the information in the same way.
All your information travels through a middle station, your ISP. They have all your history of using the internet and how you are using the internet. But when you are using a VPN, that's not the case.
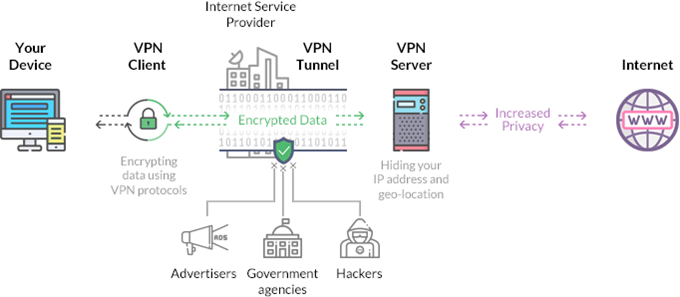
Image source
Whenever you send any request to any website or server, instead of connecting directly to the server, it first reaches the VPN server. There, all your requests and information are encrypted and then sent forward to your desired website.
Your ISP is still there to monitor things. But if you're using VPN, it will automatically change the IP address of your destination to a different IP address and encrypt the destination IP address. This way, your ISP won’t be able to read it and will assume that all your requests were going to the IP address of the VPN. So it will forward all your requests to the VPN.
When your request or information reaches your VPN, it will be decrypted, and it will forward your request to the website you wish to access. The website or server will get the VPN request and will assume that the request is coming from that VPN server. It will allow the VPN to access the website and you'll be able to visit the website without letting your ISP know.
Similarly, when you download a file, all the traffic or information flows from a web server to the VPN. The VNP encrypts all the information and then forwards it to your ISP – which will still have no idea what’s going on, as the information is encrypted.
Finally, the info gets forwarded to your laptop or mobile. When it reaches your device, it will be decrypted, and you will be able to view the website as it's available to others.
Why VPNs Caught My Attention
It all started when I was reading about cybersecurity articles, late one night (as one does at 2 AM, right?). I stumbled upon some pretty alarming stats about online privacy. I mean, think about it – we're always connected, always sharing data, but how much control do we really have over our digital footprint?
That's when I first really paid attention to VPNs – Virtual Private Networks., i mean i knew the concept fundamentally, but never really used it in real life so tried it out
What's an VPN, Anyway?
For those who aren't familiar, A virtual private network (VPN) provides you with a secure private network connection and anonymity to the public internet by encrypting your data. The added security layer helps safeguard all online activities from cybercriminals.
The purpose of a VPN is to protect your privacy online and gain complete access to worldwide content. Thanks to VPNs you can sit at any remote location, such as a cafe or at an airport, and connect to public Wi-Fi hotspots without the fear of someone stealing your sensitive data or infecting your device with malware.
With growing concerns of identity theft, fraud, and malicious attacks on the rise, more people are relying on VPNs to keep their private information safe.VPNs make browsing much safer and allow you to bypass certain restrictions such as government censorship and to stream content from sites like Netflix and YouTube when traveling. VPNs also secure sensitive data from the hands of cybercriminals.
What Is a VPN Connection?
A VPN connection creates a secure connection between you and the internet. All the data traffic you have gets routed through a virtual tunnel that is encrypted when using VPN client software.
You can establish a virtual private network VPN connection, and it will disguise your IP address, making you invisible to any prying eyes that may be lurking out there. This connection guards you against external attacks.
How does a VPN work
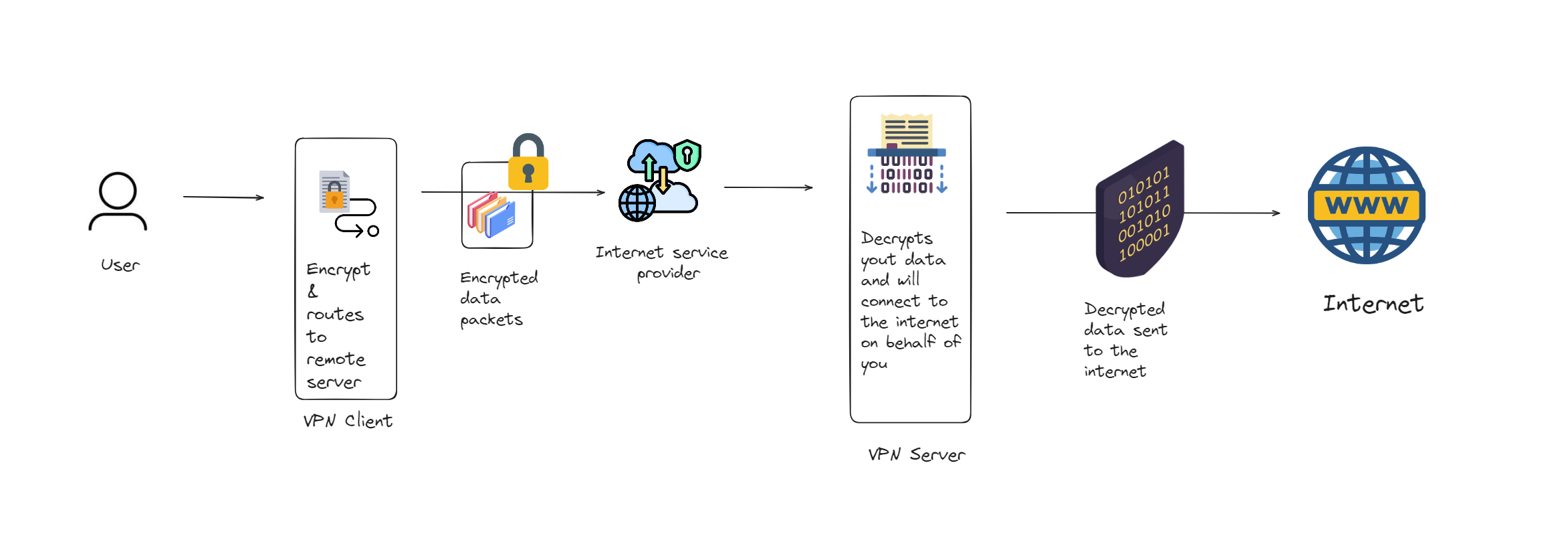
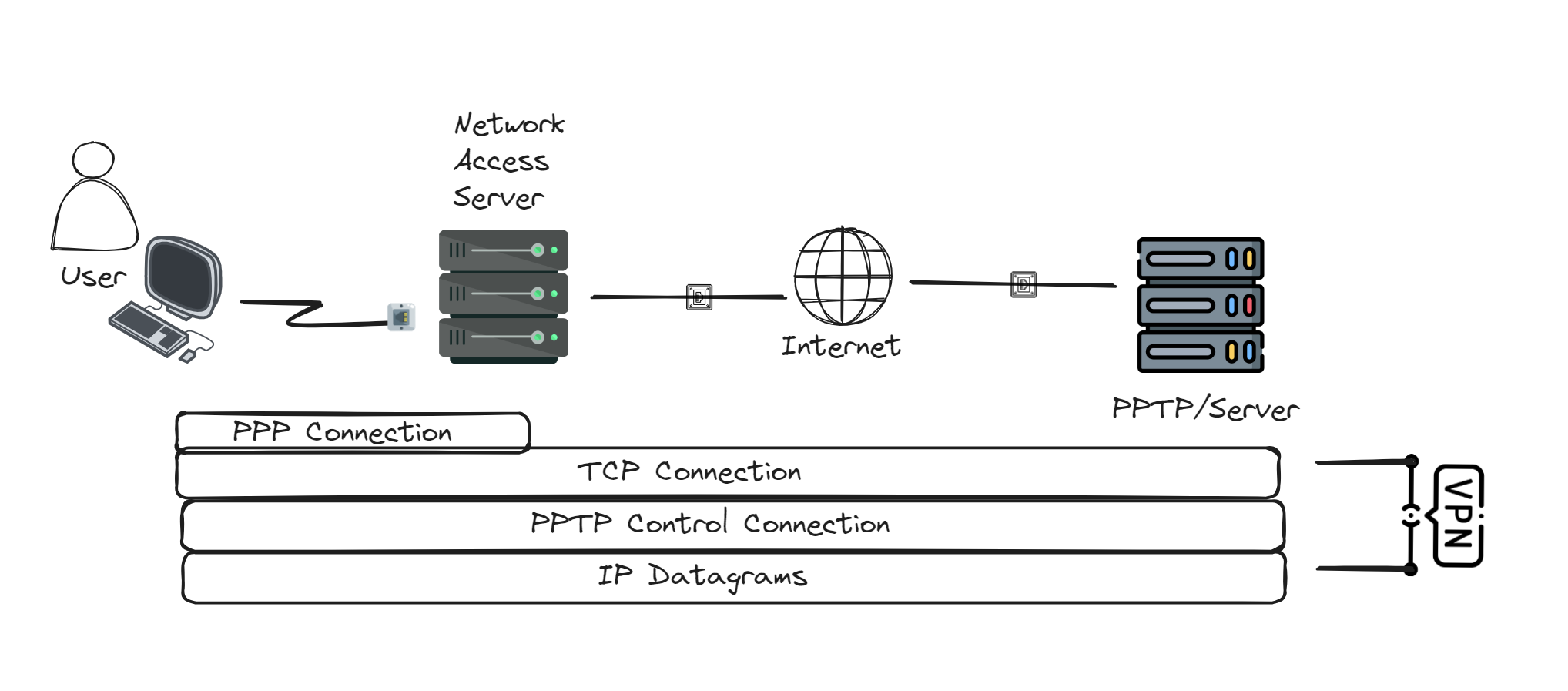
so in a particular architecture a VPN works by routing / forwarding all your data from your laptop or phone through your VPN to the internet, rather than directly through your ISP.
When you use a VPN, it encrypts all your data on the client side. Then after the data is encrypted, it's passed through a VPN tunnel which others can’t access, and then it reaches the internet.
But before going through the VPN tunnel, the request is first sent to your ISP, but as it's encrypted, ISP can’t figure out what you are trying to access. So it forwards your request to your VPN server. Then the VPN sends the request to your desired IP address or website.
VPN architecture
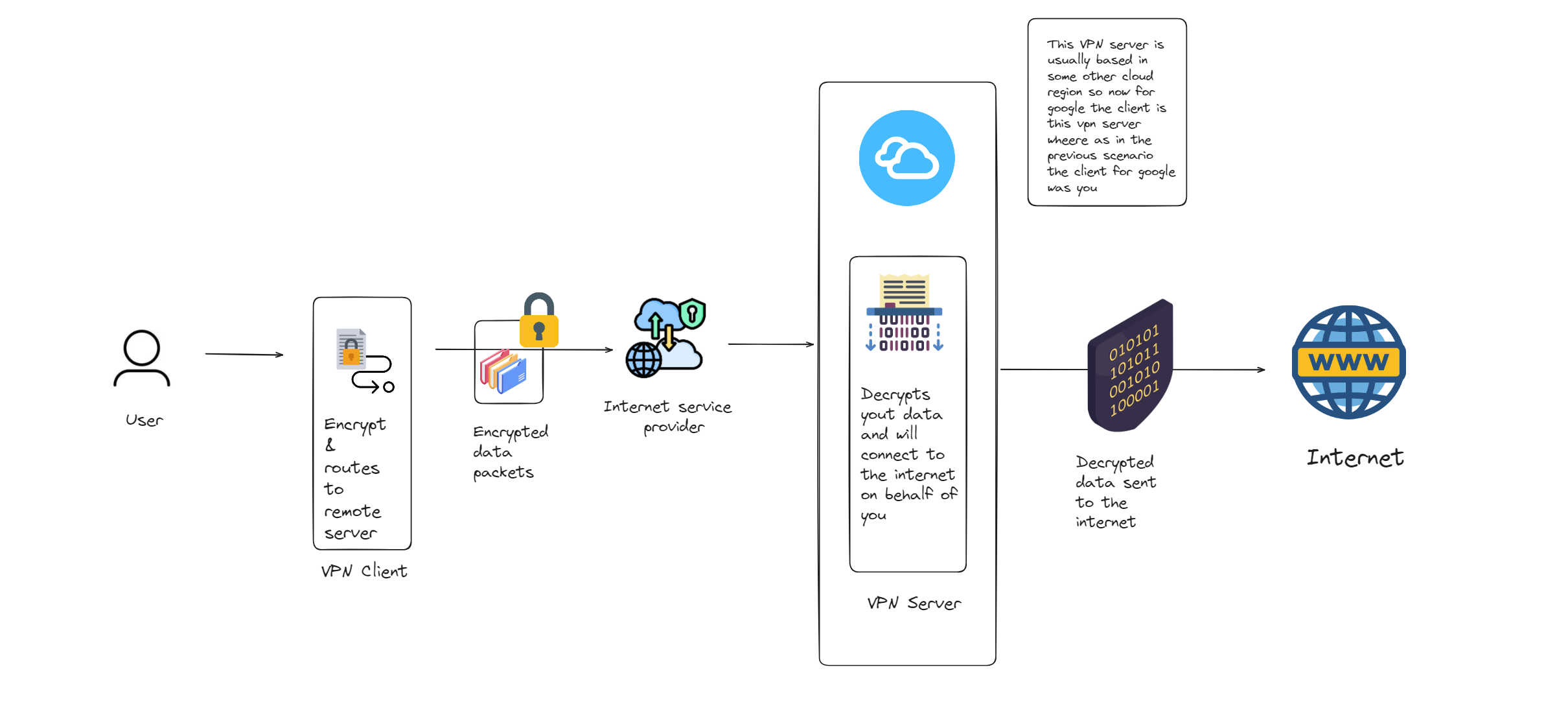
Let's get started with BYOVPN
so we can basically use a ec2 server, we are going to use Open VPN (you can self host here and its free), after doing a lot of reading and digging around
here's what you gotta do
go to Open VPN's Website and here click on resources > techincal resources > access server > documentation > installation
here you can find all about how you can install your own VPN on different linux, cloud providers, virtual machines, rasberry pi, or even docker
since we are hosting on AWS, you have to select BYOL (it stands for bring your own license) not the tiered one,
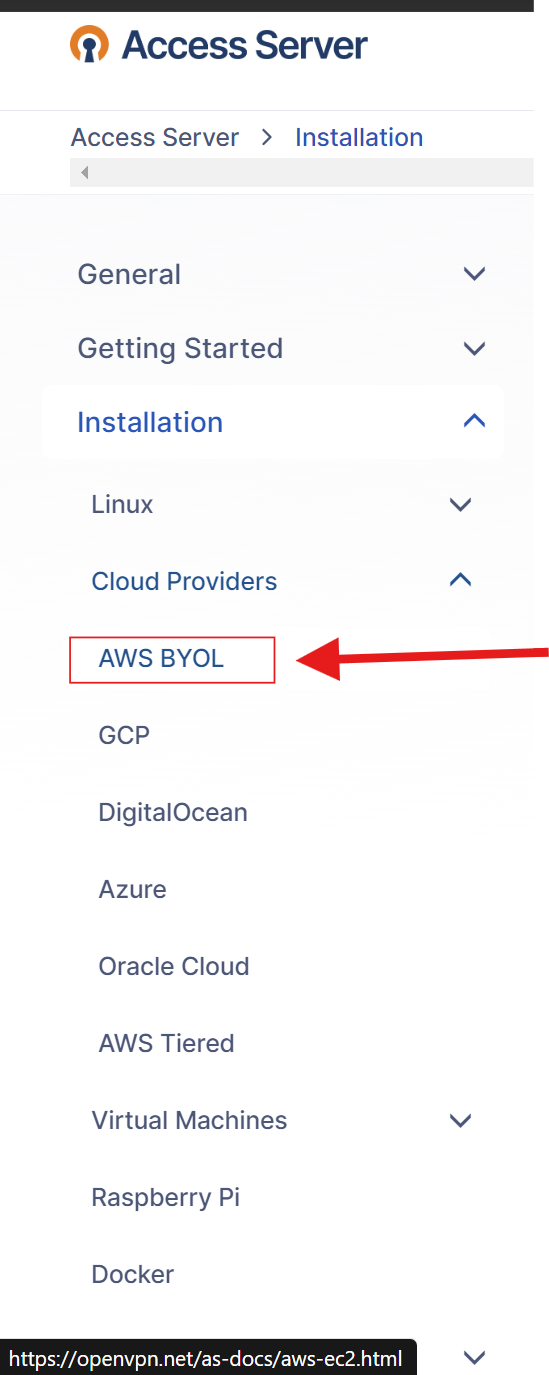
if having trouble finding click here, now here you can follow the step by step guidance so lets set it up
go to your aws console launch an ec2 instance and make sure you set up your VPN server in another cloud region
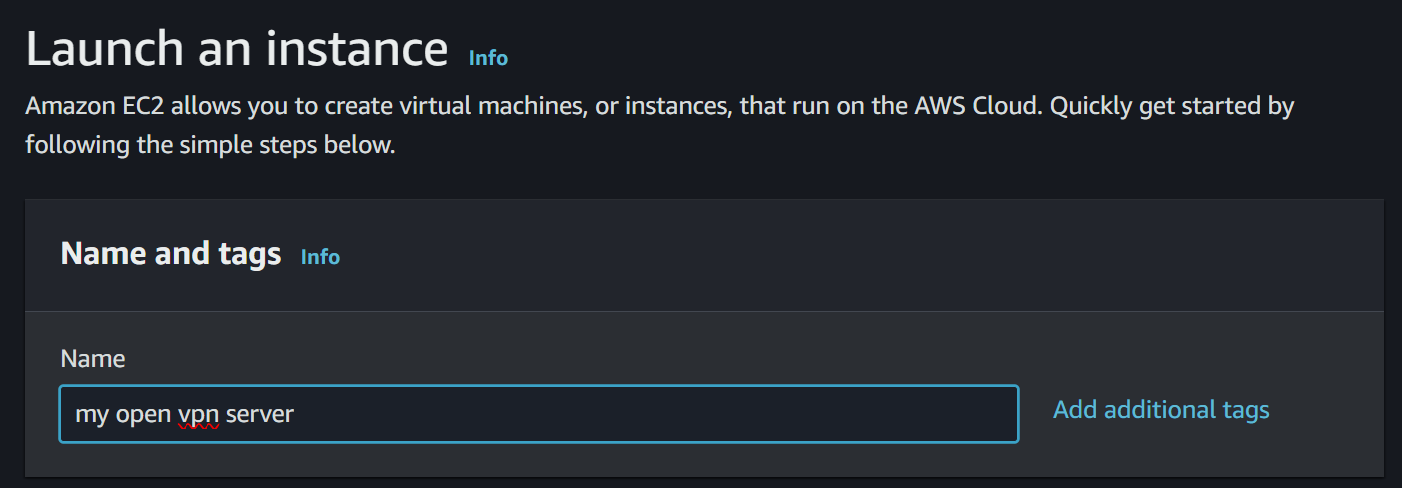
now while you are launching a instance name it acc to your will for ex "open VPN server"
and now as for selecting the AMI go to the amazon marketplace (click on browse more AMIS)
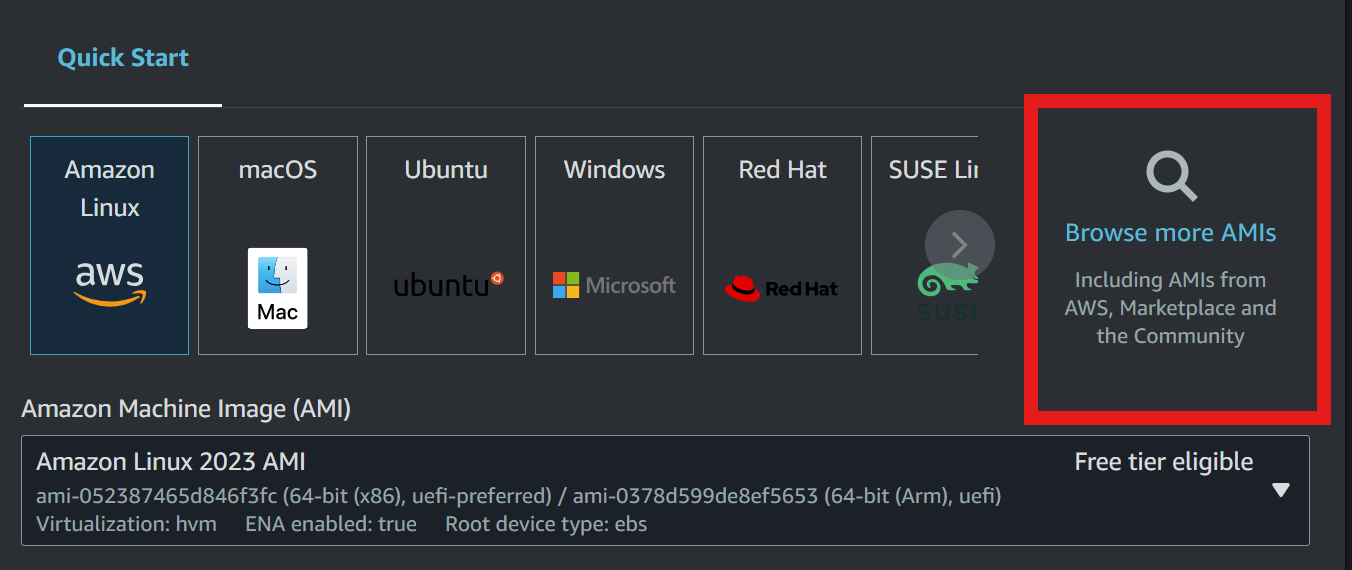
you have to search for "access server"
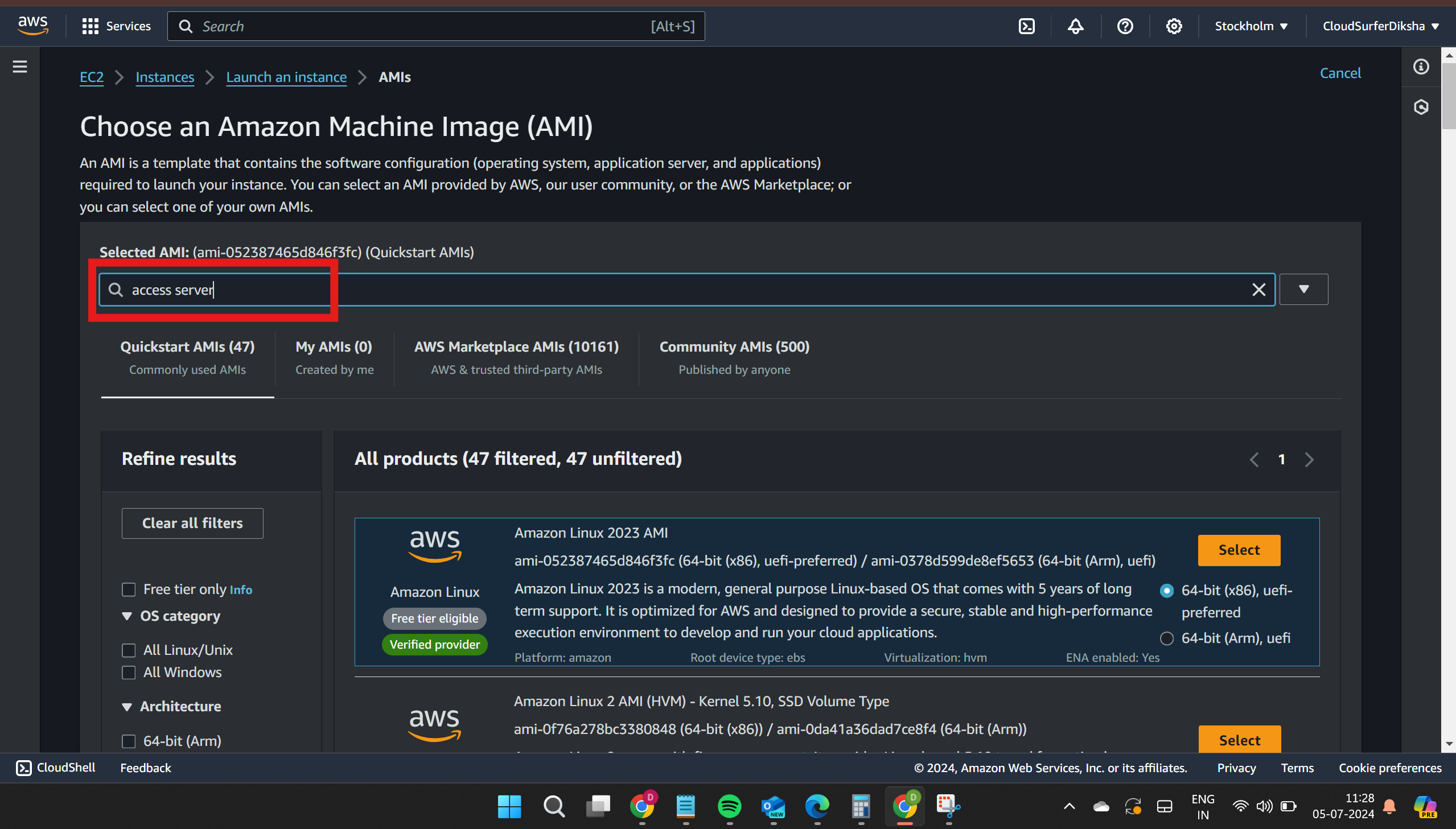
then press enter and go to the aws marketplace, you'll see a bunch of results but select the first one its free others are paid
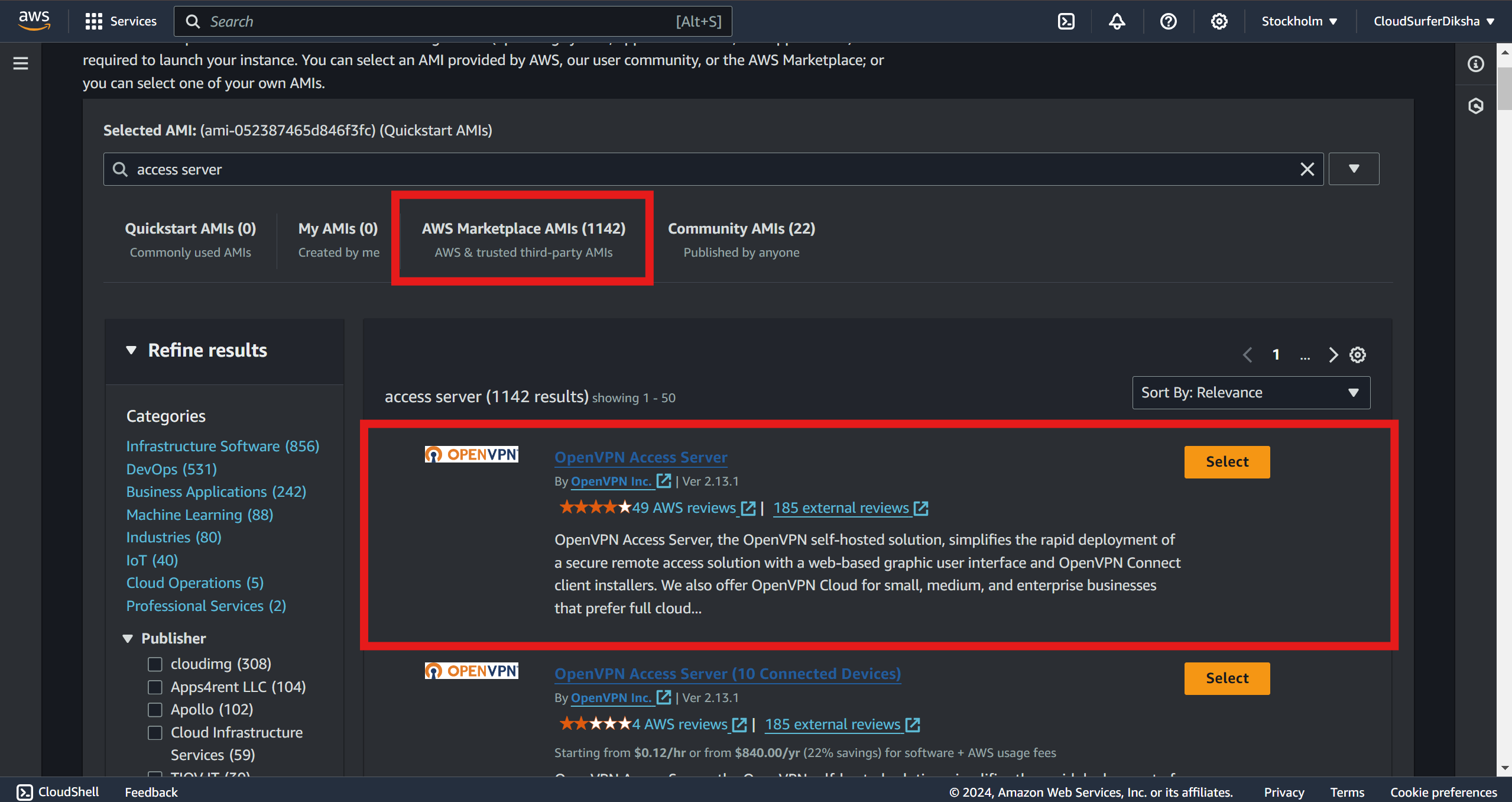
now here click on select and so subscribe now
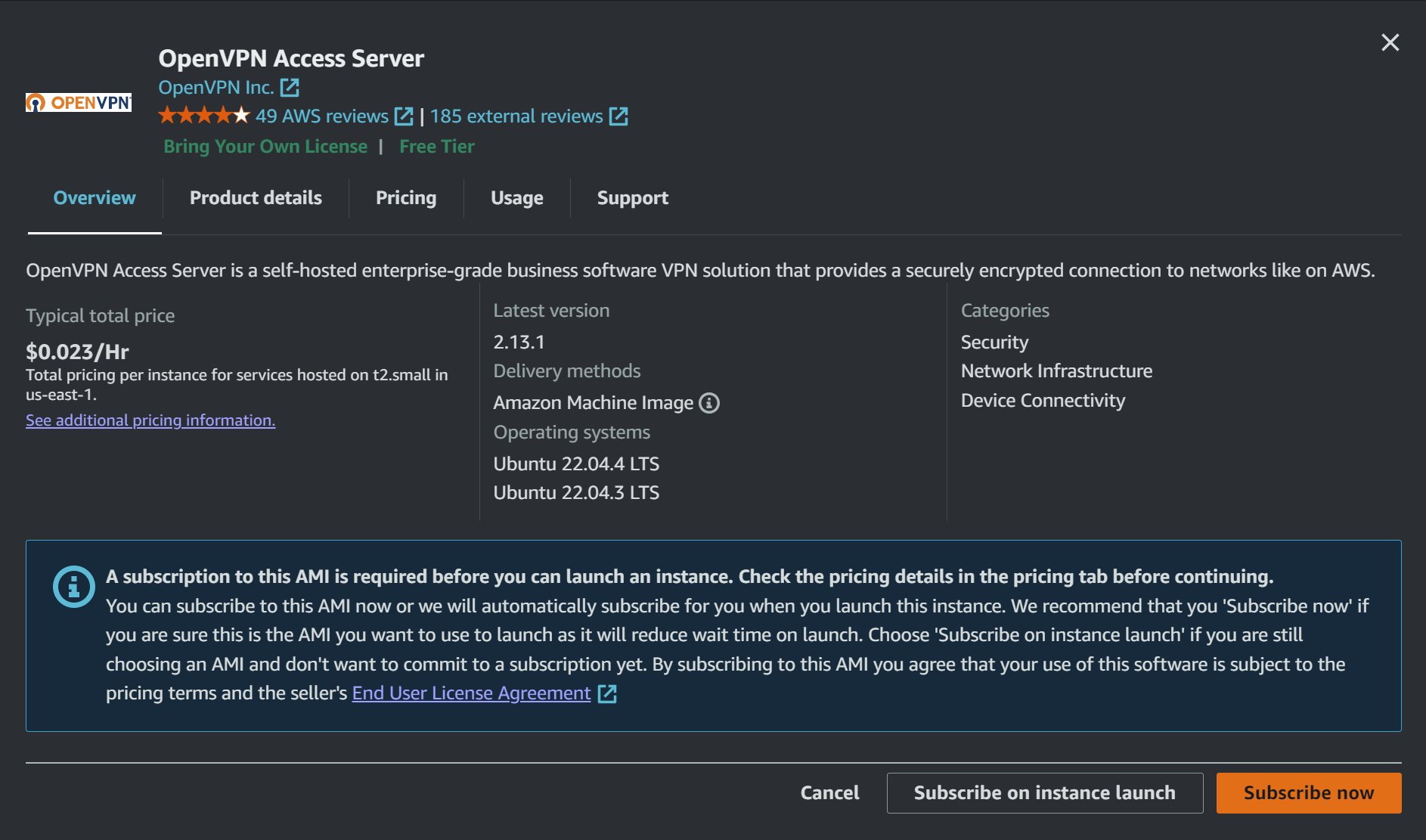
if you check out under pricing you'll find its absolutely free, and it only charges for ec2 machine and it gives you up to 2 connections, now as soon as you subscribe you'll see a subscription successful message e and details
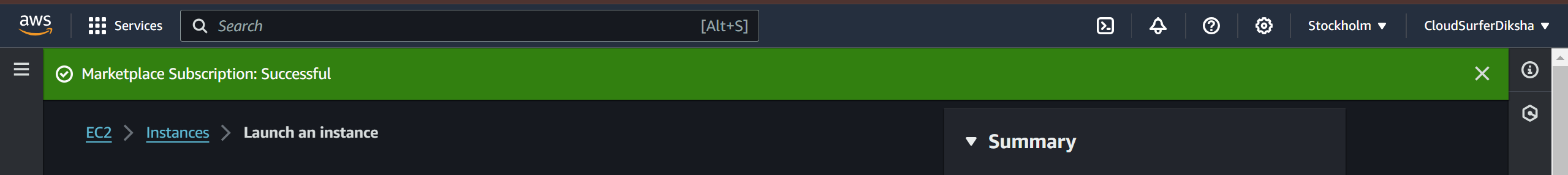
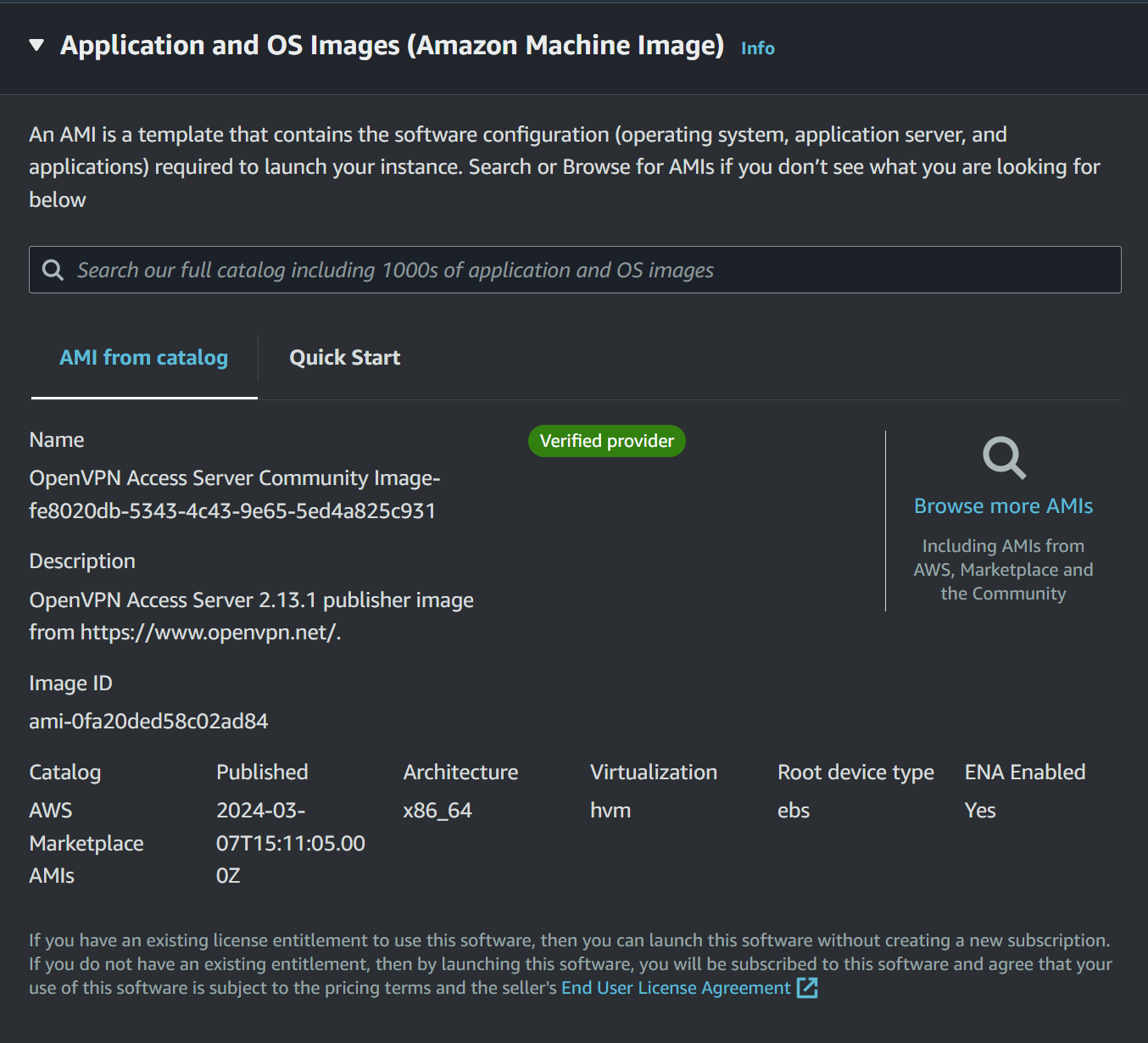
check the instance type
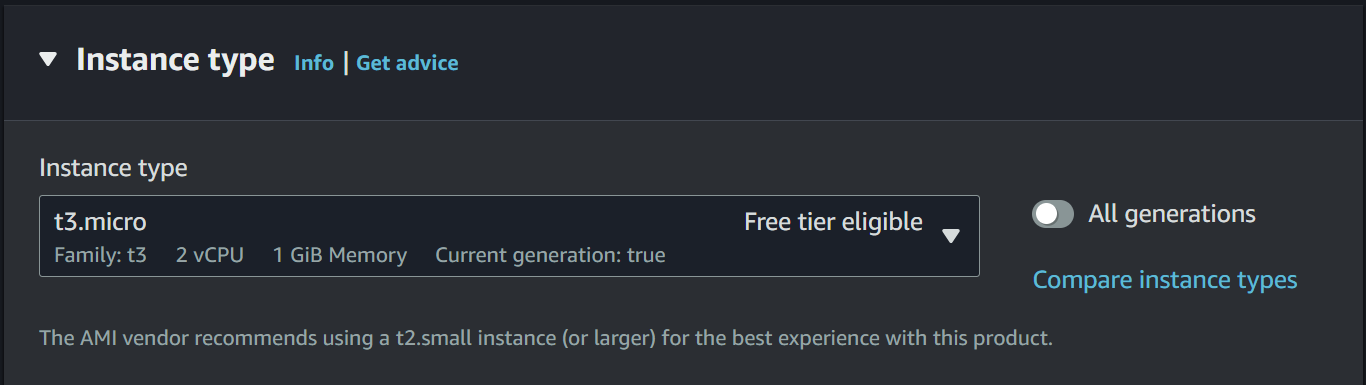
make a key pair for login and check for all the network setting and you are good to launch the instance
after launching the instance it should look something like this
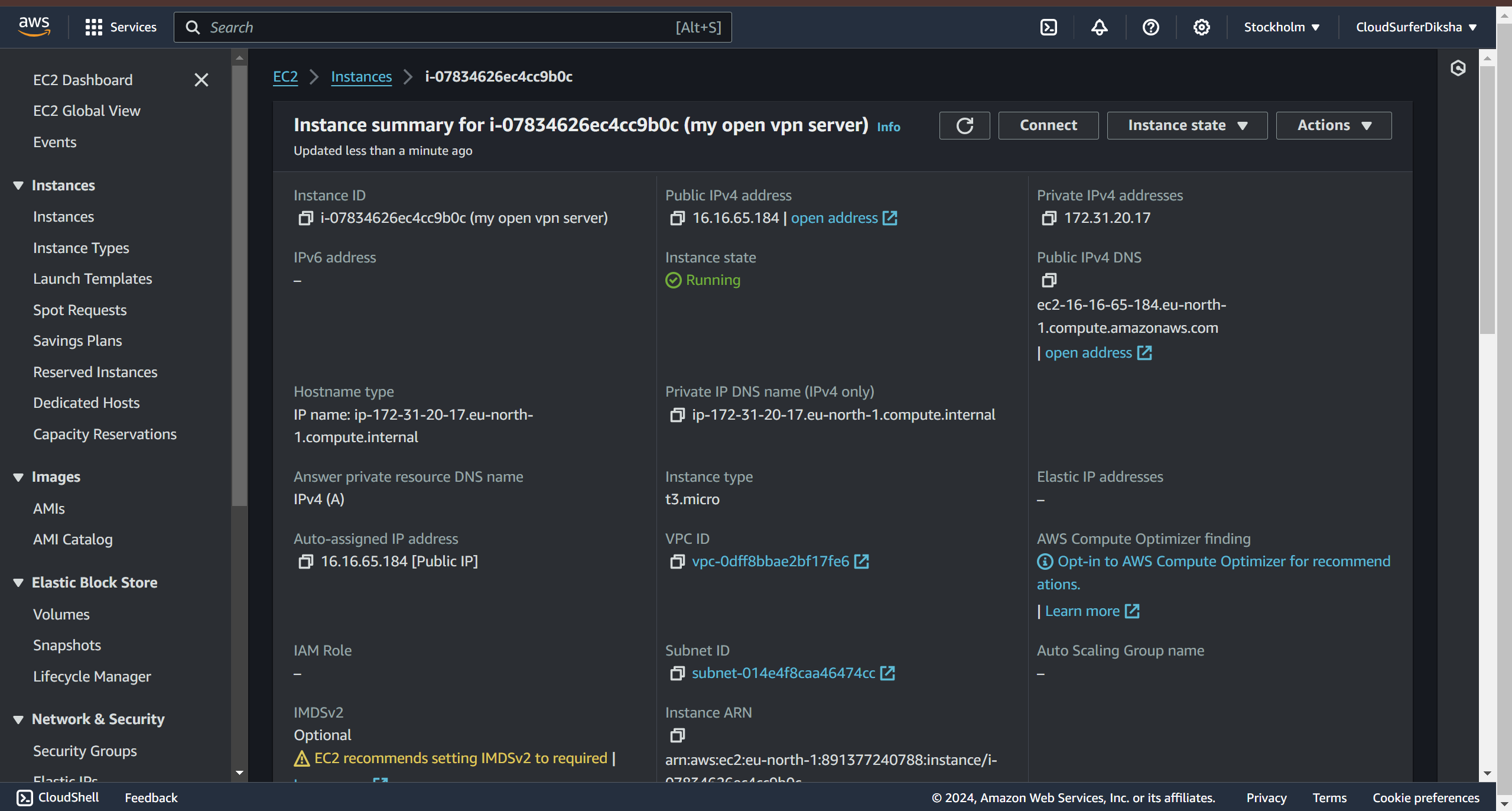
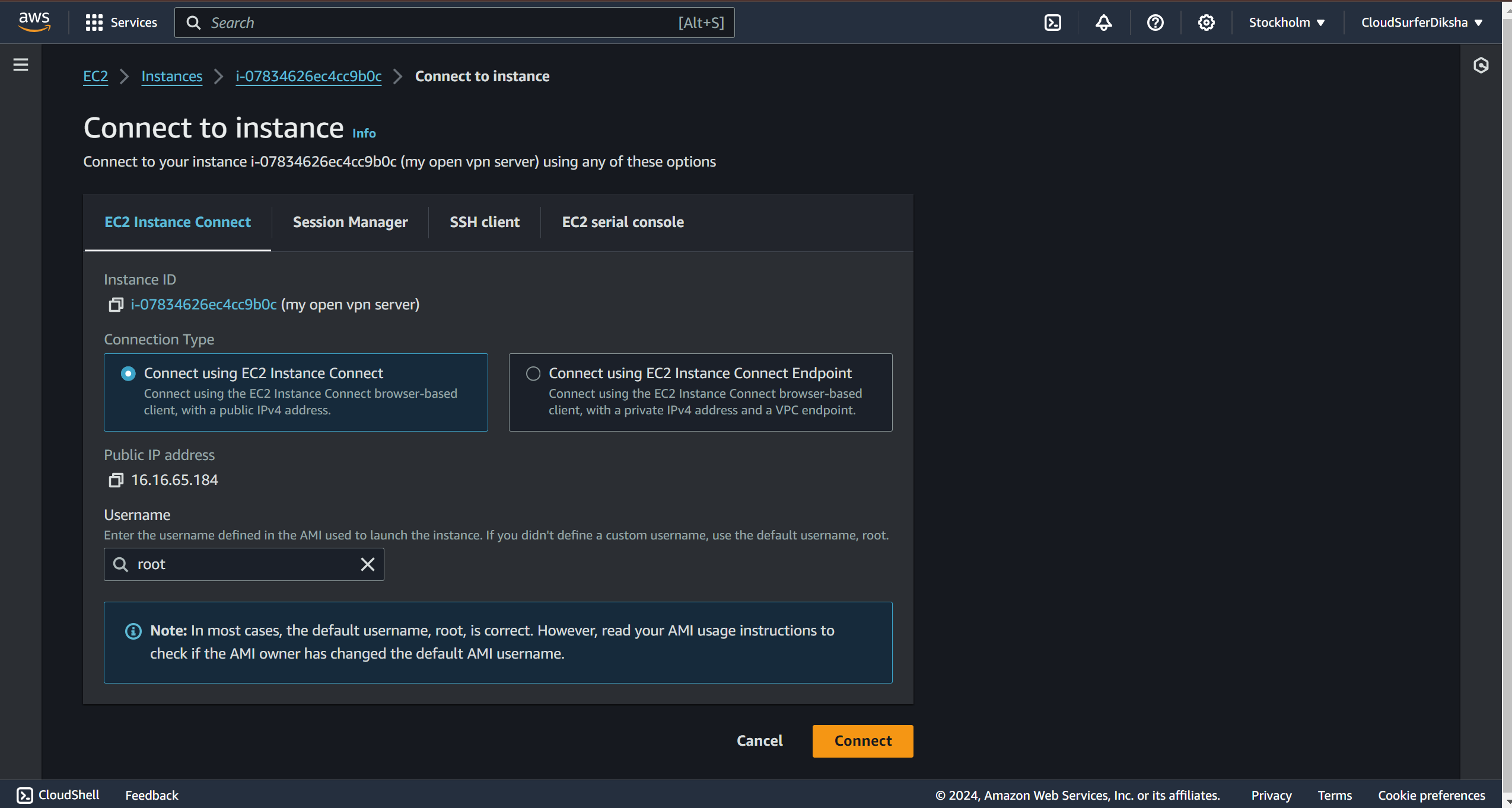
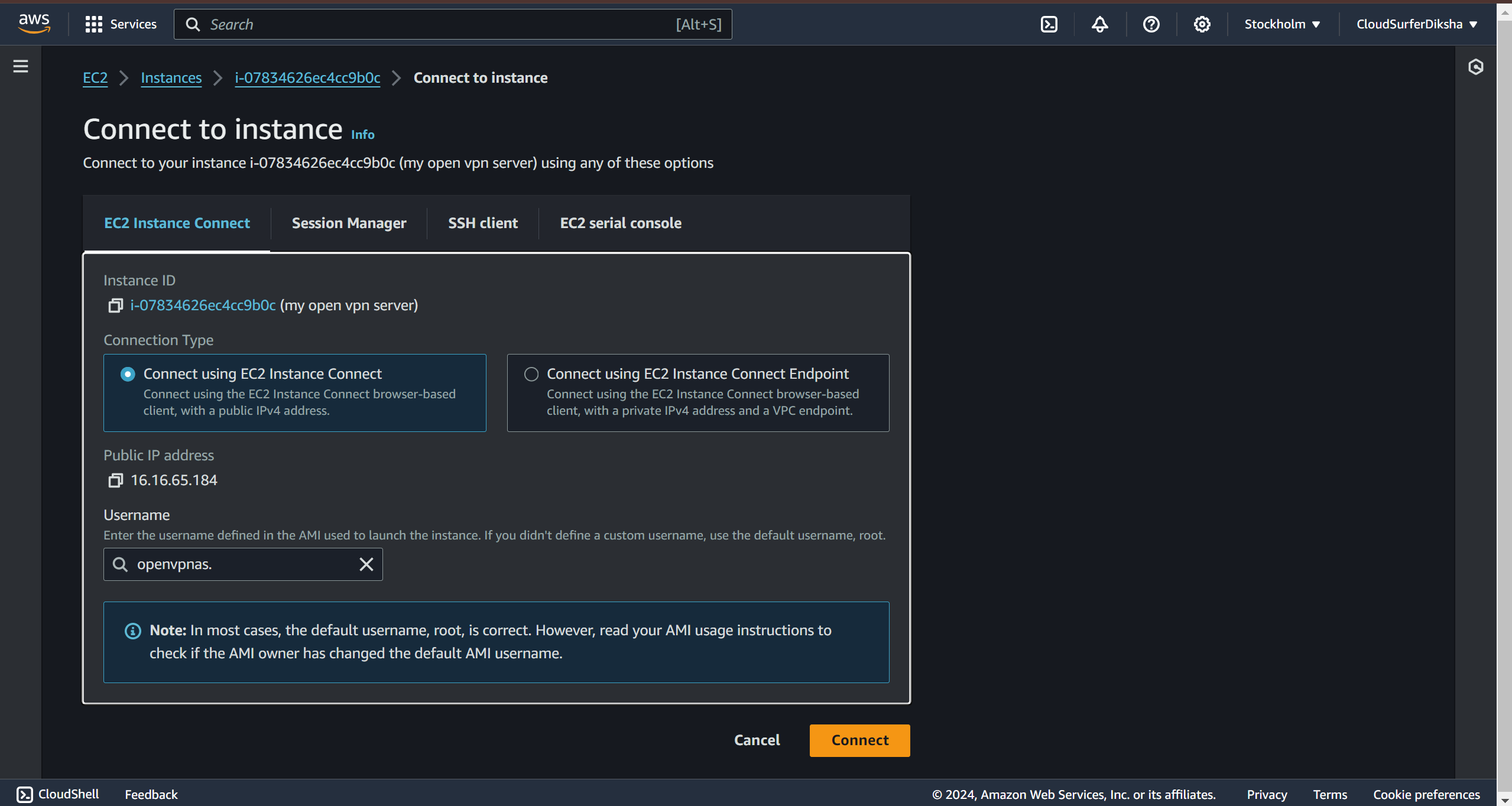
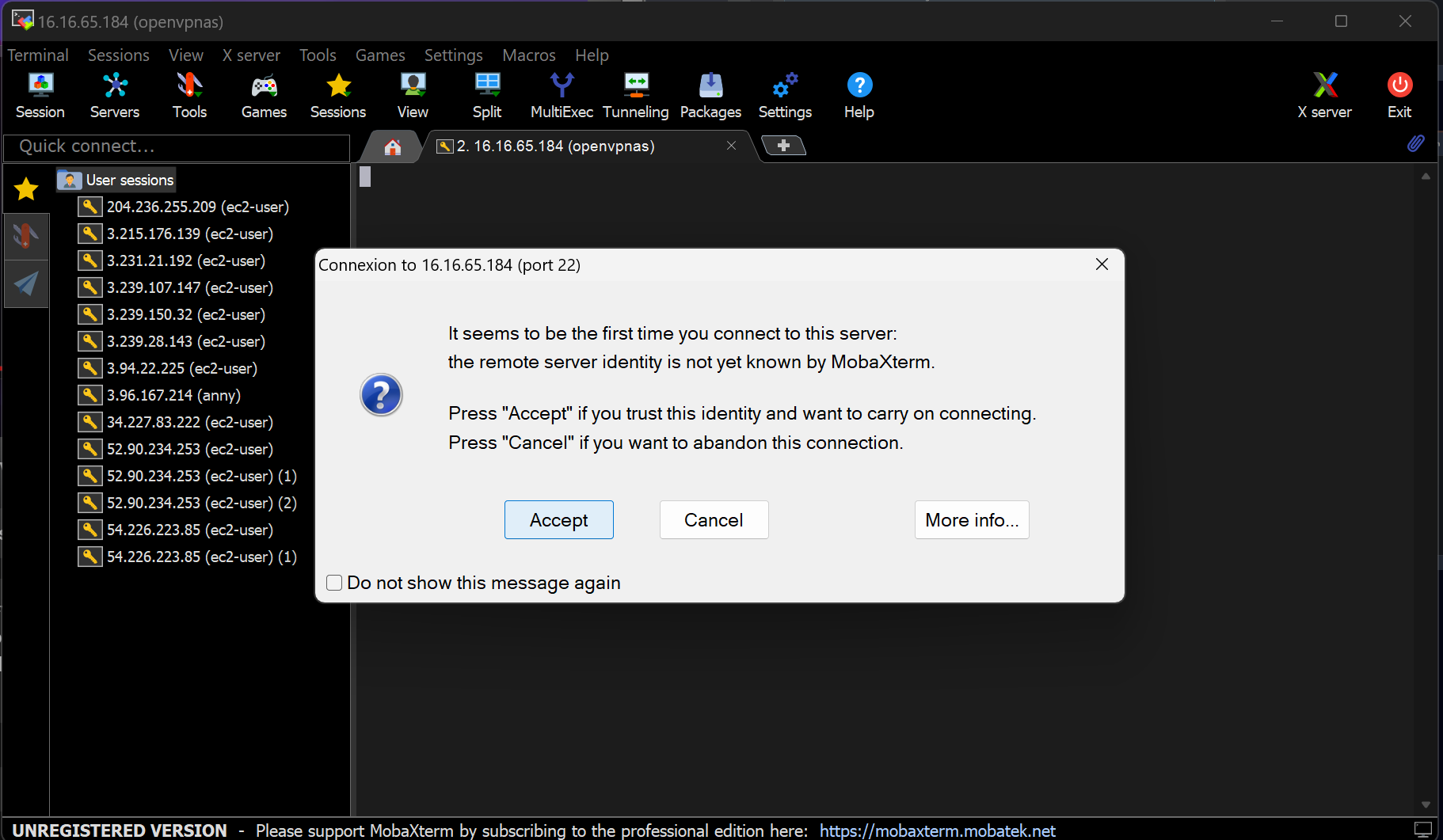
when you click on connect you'll be redirected to this page, now here in case you are using ssh to connect we have to change the instance username to openvpnas
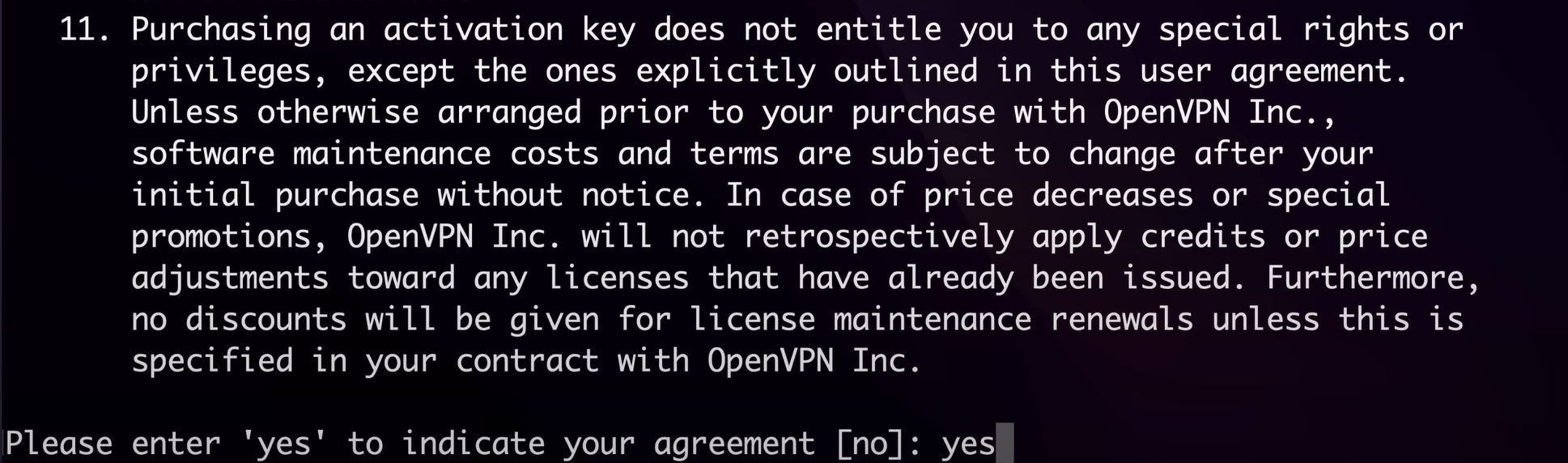
just agree to the agreement
after that it'll ask you if this is your primary access server
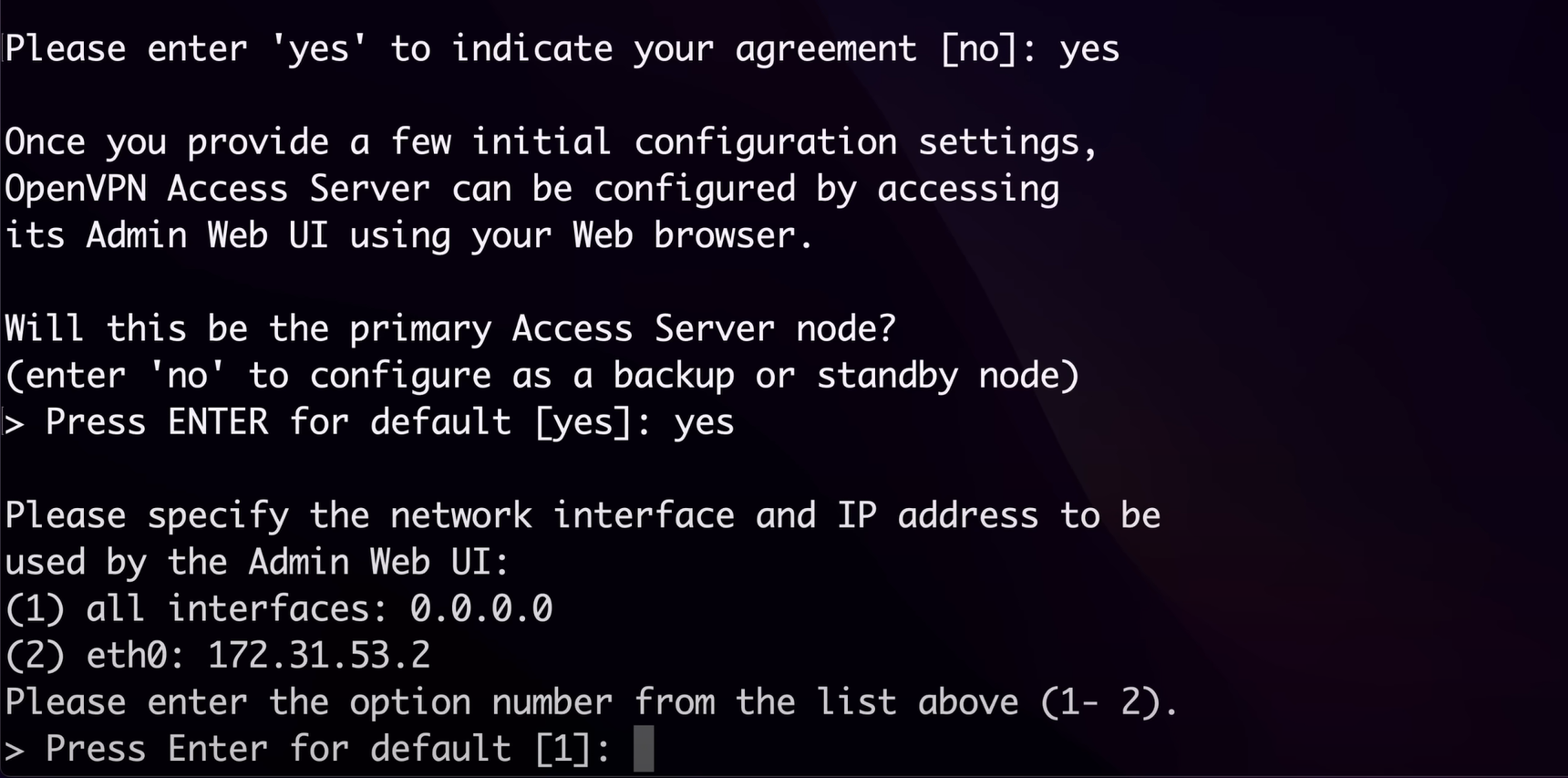
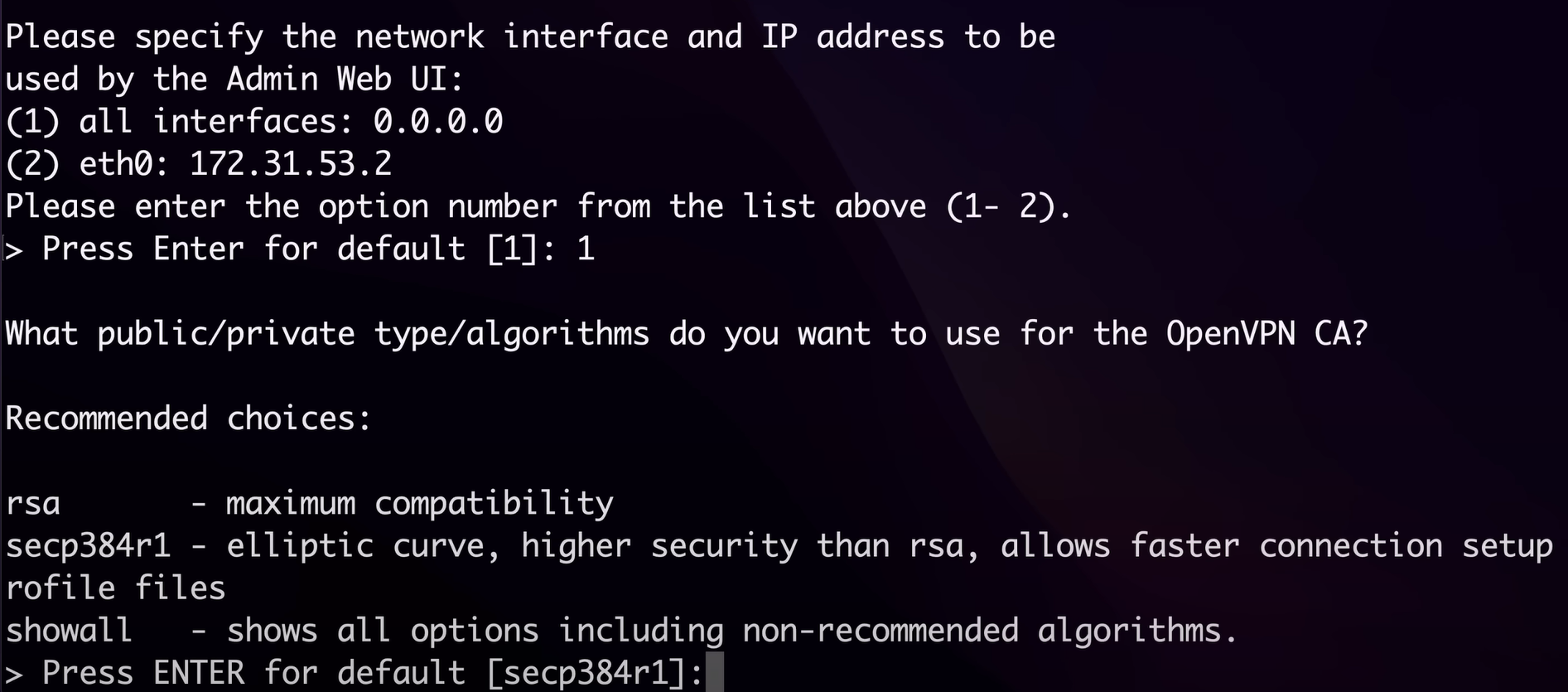
go with default settings post that just press enter for the further questions about the self signed certification and Open VPN CA algorithm
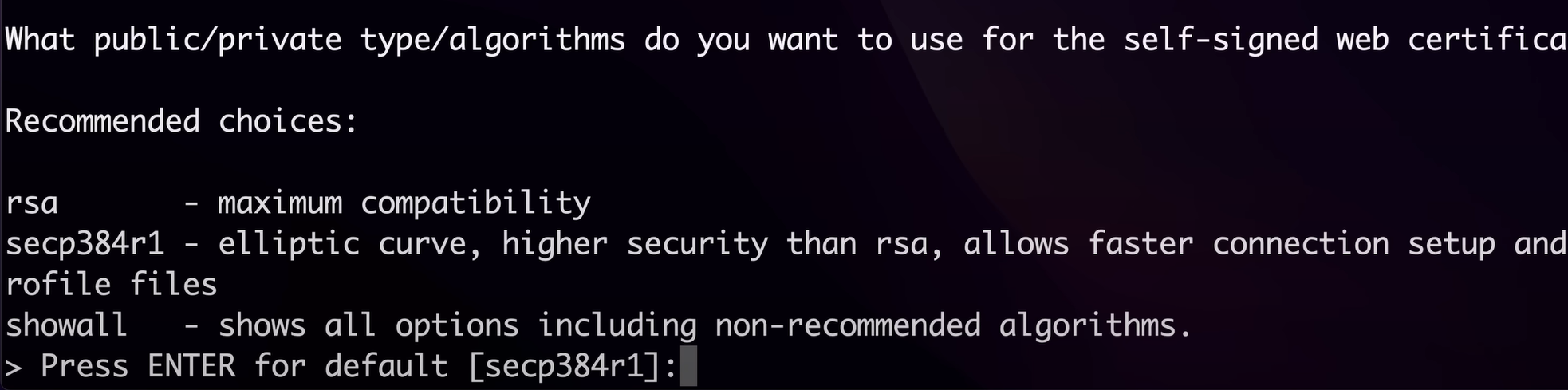
now it will ask you to specify the port number for admin web UI, you can go by the default 943
and for the TCP port number for the open VPN demon too you can go with the default 443,
then should the client traffic be routed by default through the VPN so we are gonna say yess here as we want all our traffic to go through our VPN servers, Routing all client traffic through the VPN ensures that all internet activity is encrypted and secure. This provides enhanced privacy and security, protecting users from potential eavesdropping and cyber threats,
the next question being should client DNS traffic be routed by default through VPN here we also say yes because we need our traffic to be rerouted by the VPN demon, By routing DNS traffic through the VPN, you prevent DNS leaks which can expose your browsing activity. This ensures that all DNS queries are encrypted and resolved through the VPN, maintaining user privacy and preventing tracking by external DNS servers,
then about the private subnets being accessible to clients by default we are going to say yes because allowing clients access to private subnets enables secure communication between the VPN clients and the internal network resources. This is essential for users needing to access internal applications, storing data in databases, or services that are not publicly accessible, thus maintaining the integrity and security of internal systems. (idk what to write here i mean pretty basic dumb things people should understand why tf am i even putting a blog on this)
now we need to set an username and password
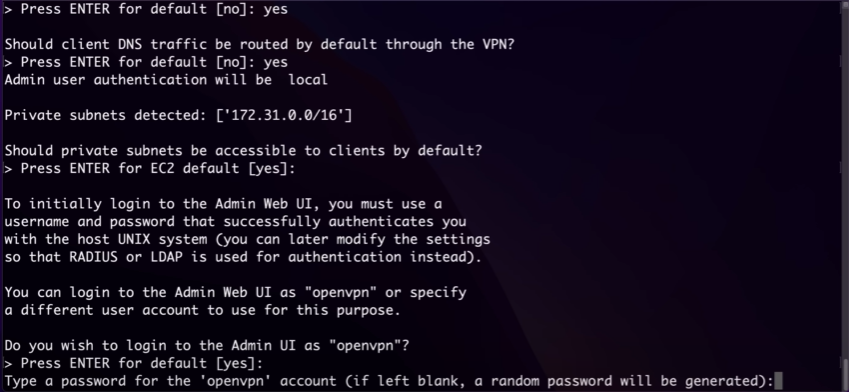
now i don't have the activation key so leaving it blank and now it'll do the configuration setups
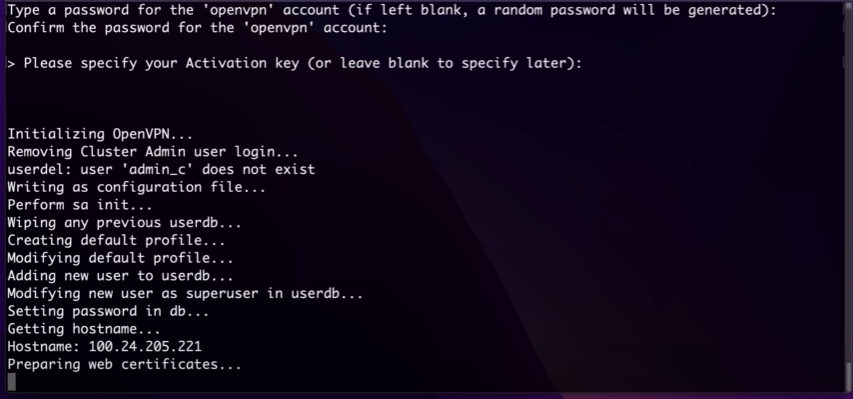
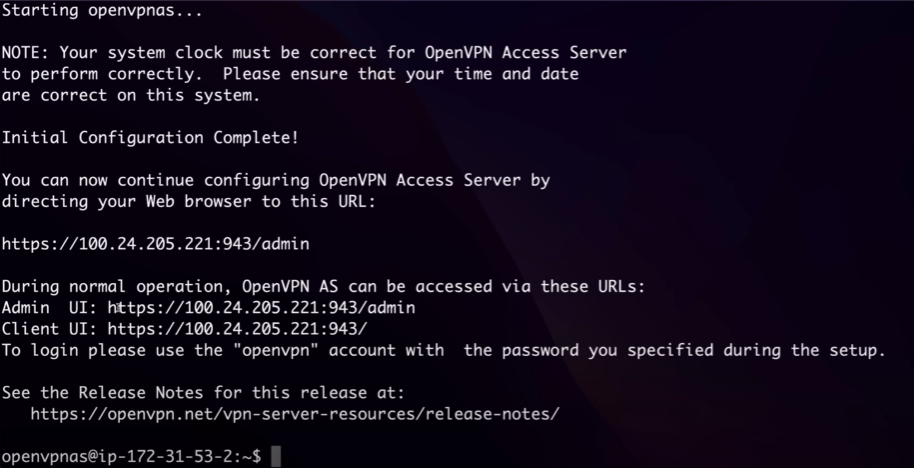
it'll give you an admin portal link, you can visit the site and sign in to access the portal
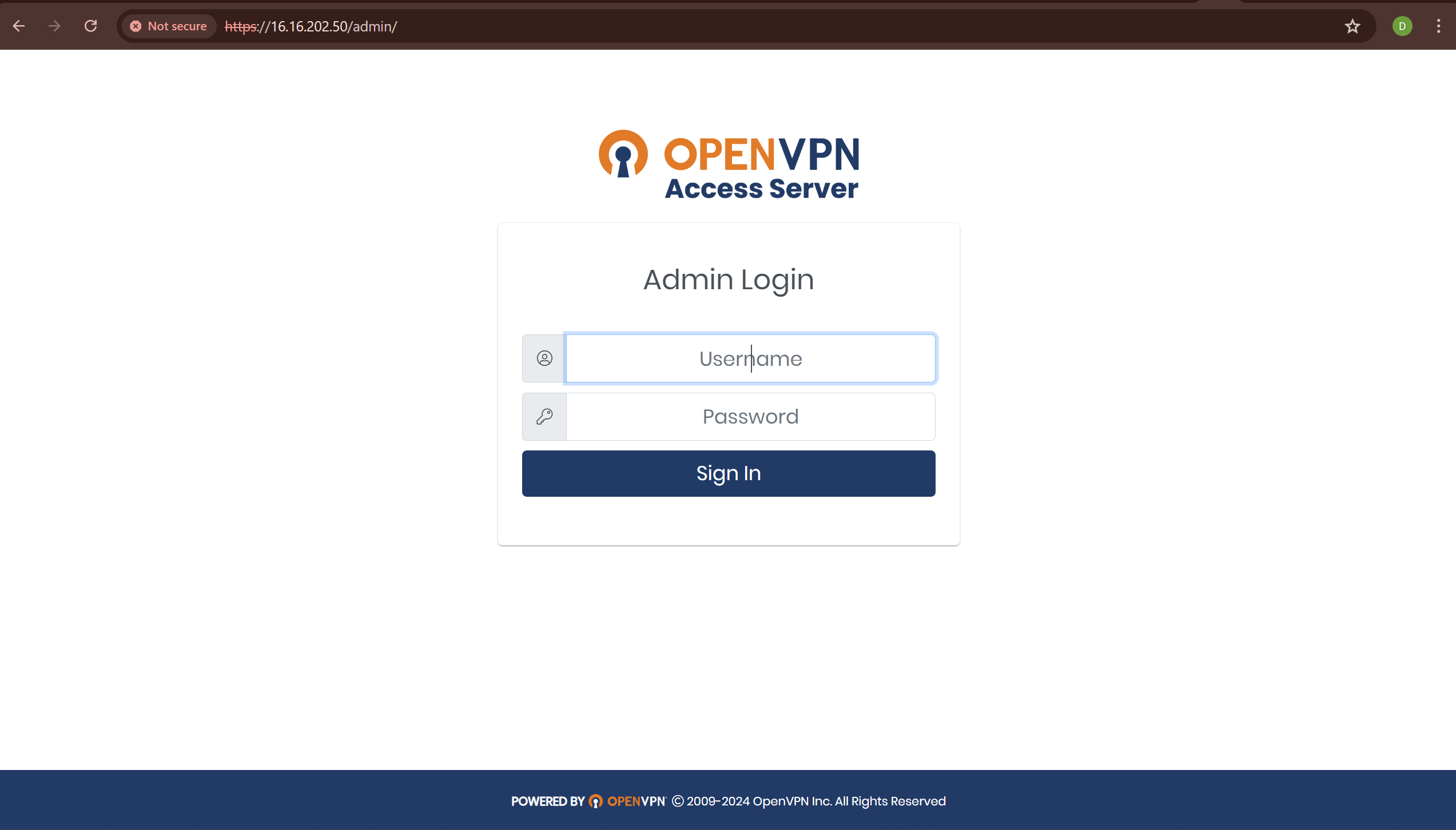
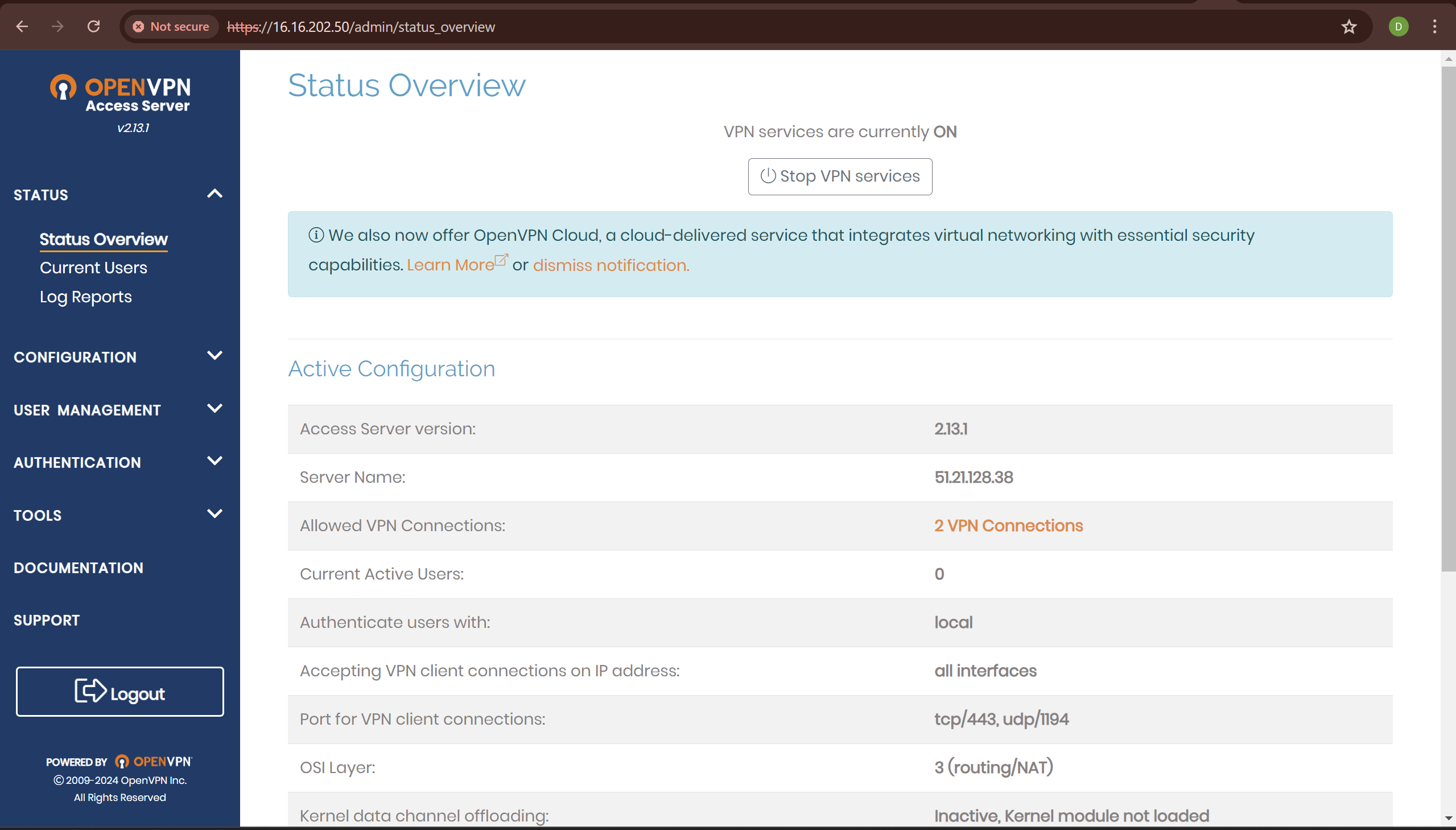
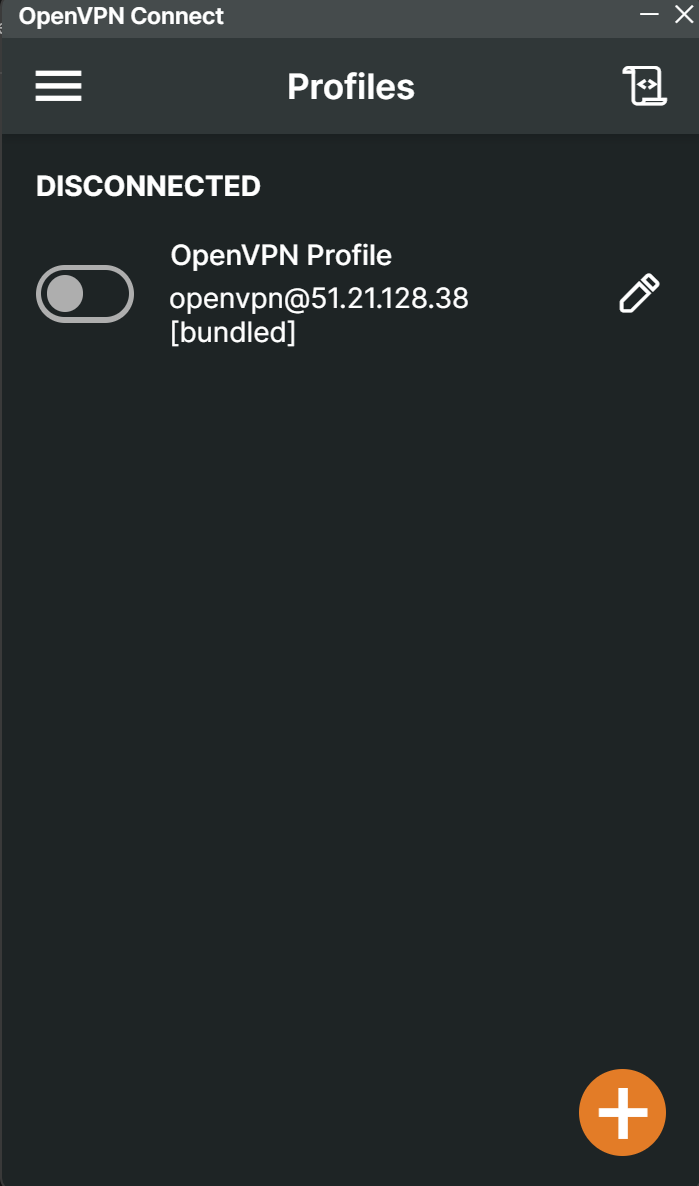
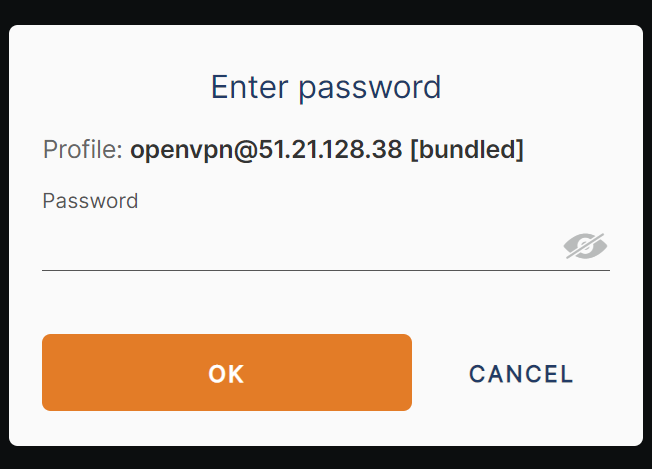
A lil backstory about VPNS
now i am curious so when i explored vpns i went back into the history digging for facts, The concept of a Virtual Private Network (VPN) has evolved over time with the development of networking and encryption technologies. The first VPN protocol, PPTP (Point-to-Point Tunneling Protocol), was developed by Microsoft in 1996 and published in 1999. PPTP allowed remote users to securely access corporate networks over the internet, but it had security vulnerabilities and encryption that wasn't strong enough to protect against modern cyber threats. In the early 2000s, the OpenVPN project was launched as an open-source alternative to PPTP, using SSL/TLS encryption that was more secure.
So the timeline goes like
1960s–1970s: The Dawn of ARPANET and the Need for Connectivity Across Different Networks
In the late 1960s, ARPA developed a method to link distant computers, introducing ARPANET in 1969. ARPANET relied on packet switching, connecting educational and research institutions, but had limitations. It operated on NCP, limiting connections to devices within the same network.The challenge was to find a way to connect devices across varied networks.
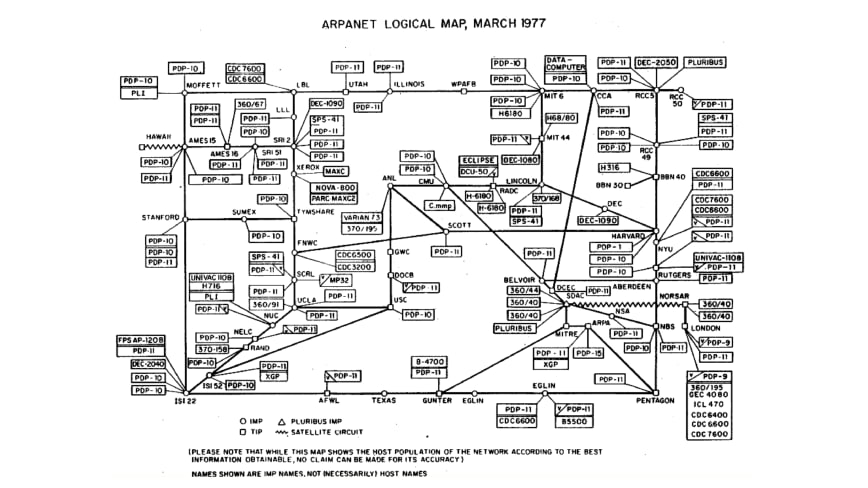
1980s: TCP/IP and the Public's Introduction to the Internet
ARPA adopted TCP/IP in the 1980s, allowing diverse device connections and this new approach transitioned from NCP to a system allowing diverse device connections, giving rise to what's now termed the internet.Accessing online resources demanded the right IP, but remembering numeric sequences wasn't convenient. So, in 1984, the Domain Name System (DNS) was born, mapping simple domain names to IP addresses. The internet expanded to the public, with America Online (AOL) launching in 1985 and commercial ISPs like "The World" emerging in 1989, offering dial-up internet connections.
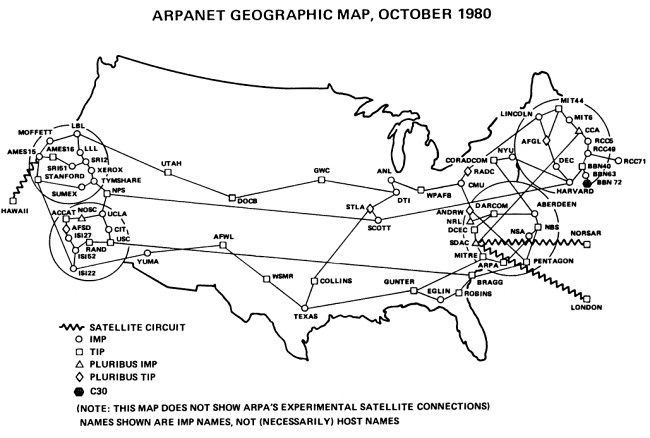
1990s: The Rise of the Web and Emergence of Early VPN Technologies
The introduction of HTTP and the World Wide Web in the early 1990s raised concerns about online security, leading to the development of IP-layer encryption and eventually virtual private networks (VPNs). IPsec, introduced in the mid-1990s, provided end-to-end security at the IP layer, while Microsoft's PPTP and Cisco's L2F protocols also emerged, followed by the collaborative L2TP protocol, which combined their strengths. These advancements paved the way for modern VPN methodologies, enabling secure data transmission over the internet.
The origins of VPNs date back to 1993, when researchers John Ioannidis and Matt Blaze developed the swipe protocol, aiming to ensure end-to-end security and authentication for network traffic. In the following years, other researchers and scientists, such as Wei Xu and Gurdeep Singh Pall, made significant contributions to the development of VPN technology, including the creation of IPsec and PPTP protocols. These advancements paved the way for modern VPN solutions, enabling secure communication over public networks and protecting remote access connections.
The experimental Swipe protocol included optional authentication. However, it was never released.

2000s: VPNs Evolve Alongside Cybersecurity Challenges
In the 2000s, the internet's growing importance led to increased cyber threats, prompting businesses and individuals to seek online security solutions. As businesses shifted online, they recognized the need for secure data transmission, initially turning to WANs but later exploring VPNs due to high costs. OpenVPN and SSL VPN emerged as prominent solutions, with James Yonan developing OpenVPN for personal use. Commercial VPNs appeared in 2005, simplifying setup processes for individual users, and third-party service providers and innovative protocols like IKEv2/IPsec and SSTP proliferated. By the end of the decade, VPNs had become essential tools for online privacy and security.
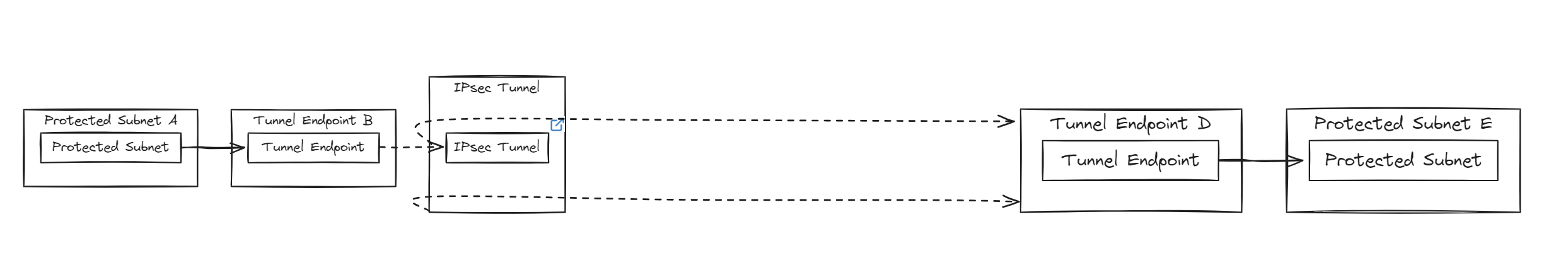
- The diagram illustrates a secure communication setup using VPNs (Virtual Private Networks) to connect two protected subnets over an IPsec tunnel. Protected Subnet A represents the starting internal network within an organization. Data from this subnet is sent to Tunnel Endpoint B, where it is encapsulated and encrypted before entering the VPN tunnel. The IPsec Tunnel then ensures the secure transmission of this encrypted data, providing integrity and confidentiality through the IPsec protocol. Upon reaching Tunnel Endpoint D, the data is decrypted and decapsulated before entering Protected Subnet E, which is another internal network within a different segment or another organization.
Historical Context of VPN Development:
2000s: The internet's growing importance led to increased cyber threats, prompting businesses and individuals to seek online security solutions.
Shift to Online: As businesses shifted online, they recognized the need for secure data transmission, initially turning to WANs but later exploring VPNs due to high costs.
Emergence of OpenVPN and SSL VPN: OpenVPN and SSL VPN emerged as prominent solutions, with James Yonan developing OpenVPN for personal use.
Commercial VPNs: Commercial VPNs appeared in 2005, simplifying setup processes for individual users.
Proliferation of Third-Party Service Providers and Innovative Protocols: Third-party service providers and innovative protocols like IKEv2/IPsec and SSTP proliferated.
End of the Decade: By the end of the decade, VPNs had become essential tools for online privacy and security.
Why Build Your Own VPN?
Learning Experience: As a DevOps enthusiast, I'm always looking to expand my skillset. Building a VPN from scratch? That's networking, security, and infrastructure all rolled into one project!
Customization: I wanted something tailored to my specific needs. Commercial VPNs are great, but I was curious about crafting a solution that was uniquely mine.
Trust Issues: Let's face it, in the world of cybersecurity, trust is a big deal. By building my own VPN, I know exactly what's going on under the hood.
The Challenge: Honestly? Part of me just wanted to see if I could pull it off. There's nothing quite like the thrill of bringing a complex project to life.
Learning Experience: As someone passionate about DevOps and cloud technologies, I saw this as an opportunity to deepen my understanding of networking and security concepts.
Customization: Building my own VPN allows me to tailor it to my specific needs and preferences.
Hands-on Project: I believe in learning by doing. This project lets me apply my knowledge in a practical way.
Privacy Control: By creating my own VPN, I have a better understanding and control over my online privacy.
Resources:
Resources:
Subscribe to my newsletter
Read articles from Diksha Jadhav directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Diksha Jadhav
Diksha Jadhav
Just starting my journey in the tech world! As a beginner programmer, I'm eager to learn and grow in the field. I'm excited to connect with others in the tech community and see where this journey takes me.