Exploring Podman and Beyond: Open Source Alternatives to Docker for Secure Containerization
 Metta Surendhar
Metta Surendhar
Attending the CNCF Chennai Meetup was an enlightening experience, particularly with the insightful talk by Ram, Chief Evangelist at the Cloud Foundry Foundation. His presentation, titled "Cloud Native Containers: Myth, Truth, or Marketing?," provided a comprehensive overview of the evolution of containers, the rise of Docker, and the emergence of modern, efficient, open-source alternatives. This blog summarizes and expands on Ram's talk, delving into the world of container technology and exploring the tools developers can use today to build and manage containers more securely and effectively.
Podman: The Leading Open Source Docker Alternative
As Docker gained popularity, the demand for more flexible, secure, and open alternatives also grew. Enter Podman—an open-source container engine developed by Red Hat that has quickly become a preferred choice for many developers and organizations. Podman offers many of Docker’s features but introduces significant enhancements tailored to meet the needs of today’s security-conscious and compliance-driven environments.
Exploring Podman
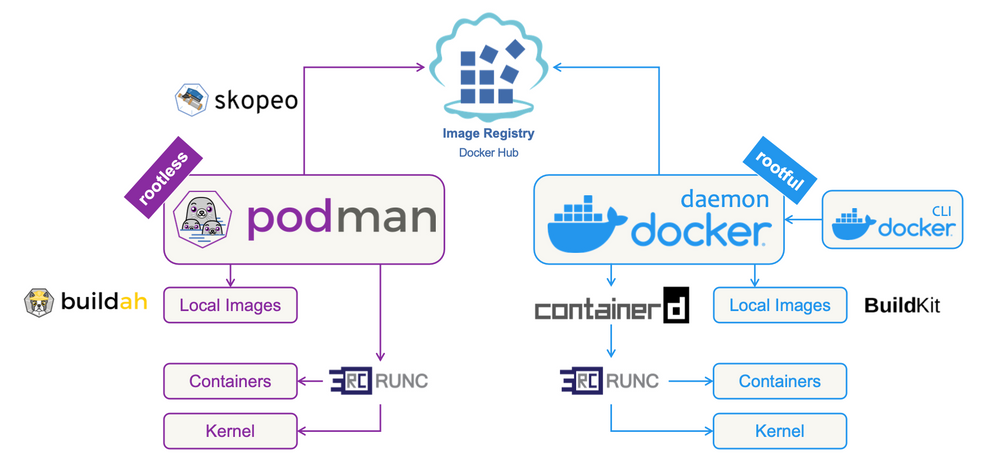
Podman provides a comprehensive, daemonless container management solution that is fully compatible with the Open Container Initiative (OCI) standards. This ensures that it can interoperate seamlessly with Docker images and other OCI-compliant tools.
Key features of Podman include:
Daemonless Architecture: Unlike Docker, which relies on a central daemon to manage containers, Podman operates without a long-running background process. Each container is managed as an individual process by the user who initiated it. This approach not only improves resource efficiency but also enhances security by reducing the attack surface—there’s no single point of failure or a privileged process that can be exploited.
Rootless Operation: Security is at the heart of Podman’s design. By default, Podman runs containers as non-root users, minimizing the risk of privilege escalation attacks. This is a crucial advantage over Docker, where the daemon typically requires root privileges, posing potential security risks. While Docker can be configured to run in a rootless mode, Podman makes rootless operation the standard, ensuring a safer environment by default.
CLI Compatibility with Docker: Podman’s command-line interface (CLI) is designed to be nearly identical to Docker’s, making it easy for developers to switch from Docker to Podman without having to learn new commands. This compatibility even extends to Docker Compose, thanks to the
podman-composetool, which replicates Docker Compose functionality using Podman.
These features make Podman a compelling alternative for developers and organizations looking to enhance security, reduce dependency on privileged processes, and maintain compatibility with existing container workflows.
Top Open Source Tools for Container Builds
Beyond Podman, several other open-source tools offer unique features and capabilities for container builds. These tools are integral to modern DevOps practices, providing flexibility and efficiency in container creation and management.
1. Unleashing Buildah
Buildah is the backbone of Podman for building container images.
It allows users to create images from scratch or customize existing ones.
Offers the flexibility to build images without needing a Dockerfile.
Compliance with OCI standards ensures compatibility with any OCI-compliant container runtime.
Makes Buildah a powerful and versatile tool for developers looking to streamline their image-building process.
2. Kaniko: Building in Kubernetes
Kaniko is a build tool designed to run within Kubernetes clusters.
It enables developers to build container images inside containers or Kubernetes pods without requiring privileged access to the host.
This is particularly useful in CI/CD pipelines, where security is paramount, and running builds without elevated privileges is a best practice.
Kaniko’s integration with Kubernetes makes it a go-to choice for teams leveraging Kubernetes as their primary platform.
3. The Efficiency of BuildKit
BuildKit is a highly efficient and modern toolkit for building container images, originally developed as part of the Moby project.
It’s now widely used within the Docker ecosystem and beyond.
BuildKit supports advanced features like parallel builds, build caching, and multi-stage builds, significantly speeding up the image-building process.
Its flexibility and performance enhancements make it a robust option for developers looking to optimize their container build workflows.
4. NixOS: A Unique Approach
NixOS is an innovative Linux distribution that takes a declarative approach to system configuration.
While not a traditional container tool, NixOS’s ability to perform VM work through containers offers an unparalleled level of reproducibility and isolation.
This makes NixOS ideal for developers who need a highly controlled and consistent environment for their applications.
It is especially useful in scenarios where precise environment replication is critical.
5. Ko: Tailored for Go Developers
Ko is a specialized tool designed for Go developers.
It simplifies the process of building and deploying Go applications as container images.
Ko eliminates the need for a Dockerfile.
It automates the creation of optimized, small container images directly from Go source code.
This tool is particularly valuable for microservices architecture.
Efficient and rapid deployment of Go applications is essential with Ko.
6. Apko: Minimal and Secure
Apko, developed by Chainguard, focuses on building minimal and secure container images.
It emphasizes simplicity and ease of auditing, making it an excellent choice for security-conscious organizations.
Apko’s approach to container image creation helps minimize the attack surface, which is crucial in environments where security is a top priority.
7. Buildpacks: Simplifying Container Creation
Buildpacks offer a higher-level abstraction for building container images.
Originally developed by Heroku and now part of the Cloud Native Buildpacks project.
Developers can create optimized container images without writing Dockerfiles.
Buildpacks automatically detect the language and dependencies of an application.
They generate a container image tailored to the application's needs.
Support rebasing, allowing for base image updates without rebuilding the entire application.
Save time and resources in the deployment process.
Building Containers: Reproducibility, Isolation, and Security
As container usage grows, the importance of reproducible, isolated, and secure builds becomes increasingly clear. Here are some critical considerations for achieving these goals:
Reproducibility: A reproducible container build process ensures that the same container image can be generated consistently, with identical content, regardless of when or where it is built. This is vital for debugging, auditing, and maintaining compliance with regulations.
Isolation: Containers should be isolated not only during runtime but also throughout the build process. This prevents potential conflicts and ensures that the build environment does not influence the final container image, leading to more reliable and predictable deployments.
Parameter Less Builds: To enhance build reliability, containers should be built without relying on external parameters or environment variables, which can introduce variability and unpredictability into the build process.
Provenance: Understanding the origin of every component within a container is essential for security and compliance. Provenance tools help track and verify the source of software components, ensuring that your containers are built from trusted and secure sources.
Embracing the Future of Container Technology
The container technology landscape has evolved significantly since the early days of Docker. Developers now have access to a wide array of open-source tools, each offering unique features that cater to different aspects of containerization. Whether you’re seeking a secure, rootless container engine like Podman or specialized build tools like Buildah, Kaniko, or Buildpacks, the open-source community has created robust alternatives that can meet the diverse needs of modern software development.
As you explore these tools, it’s crucial to align them with your specific requirements—be it security, performance, ease of use, or integration with your existing CI/CD pipeline. By selecting the right tool for the job, you can ensure that your containerized applications are built and deployed efficiently, securely, and with minimal overhead.
Subscribe to my newsletter
Read articles from Metta Surendhar directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Metta Surendhar
Metta Surendhar
Interned as a Platform Engineer specializing in Observability and Gen AI, passionate about open-source contributions and real-world solutions. Currently pursuing an MSc in Integrated IT at CEG (2024-26), SAASCEG'24, CTF'24. I'm exploring LLMs, Haystack, Retrieval-Augmented Generation (RAG), and Gen AI, focusing on building conversational AI bots. Diving into new tools to enhance chatbot performance and interaction quality!