2.Docker Networking
 Amrit Poudel
Amrit PoudelDocker networking is a core aspect of containerization, enabling seamless communication between containers and the external environment. It plays a critical role in data transfer between containers, applications, and external services, making it vital for container orchestration and microservices architecture.
Advantages of Docker Networking
Isolation: Docker networking offers network isolation. Each container has its own network stack and IP address, preventing interference between containers.
Flexibility: Docker networking allows the design of networks tailored to your application’s needs. You can create custom networks, connect containers to external networks, and utilize various network drivers.
Simplified Deployment: Networking in Docker simplifies application deployment. Containers can be deployed on different hosts but communicate smoothly through networks.
Docker Network Models
Docker provides several network models to enable communication between containers and external entities. The three primary network models are:
Bridge Networks
The bridge network is Docker’s default network, connecting containers through a virtual bridge called docker0. Containers on the same bridge network can communicate with each other, while containers on different bridge networks are isolated.
Understanding the Docker Bridge Network
Distinct Networks: Containers and the host machine are on different networks.
docker0Interface: Acts as a bridge, connecting the container network to the host’s network.Communication: Containers can communicate with each other and the host via the
docker0interface.Internet Access: Containers use the host’s internet connection through the
docker0interface.Port Mapping: To access a container from outside, you need to map its internal ports to the host’s ports.
# Create a Docker container attached to a bridge network
docker run -d --name app-container --network bridge my-app-image
Host Networks
In the host network model, containers share the host’s network stack, allowing them to directly access the host’s network while bypassing the docker0 bridge.
Understanding the Docker Host Network
Shared IP Address: The container shares the same IP address as the host machine.so if you inspect the container and try to see ip ,it will be empty.
Direct Network Access: The container uses the host’s network interface (
eth0) directly, avoiding the Docker bridge network and NAT.Accessing Services: Services running in the container can be accessed using
hostIP:port. Be cautious about port conflicts as both the host and container share the same network namespace.
# Create a Docker container using the host network
docker run -d --name web-container --network host my-web-image
Overlay Networks
Overlay networks facilitate communication between containers on different Docker hosts, particularly useful in multi-host environments and cluster orchestration.
Details of Docker Overlay Network
Cross-Host Communication: Allows containers on different Docker hosts to communicate as if on the same local network.
Virtual Networking Layer: Creates a virtual network that spans multiple Docker hosts, abstracting the underlying physical network.
Service Discovery: Offers integrated service discovery within the overlay network, allowing containers to be accessed using service names instead of IP addresses.
Security: Uses encryption to secure data transmitted between containers across different hosts.
Deployment: Overlay networks are automatically managed and configured by orchestrators like Docker Swarm or Kubernetes.
# Create an overlay network in Docker
docker network create -d overlay my-distributed-network
Custom Docker Networks
While Docker sets up a default bridge network, it has limitations, such as no DNS resolution between containers and no communication across different hosts. Creating custom networks overcomes these limitations, offering greater control over communication, DNS resolution, and container connectivity.
# Create a custom Docker network
docker network create my-custom-network
Connecting Containers in Docker Networks
In Docker networks, containers can be connected seamlessly and communicate directly using their container names as DNS names.
# Create two containers connected to the same network
docker network create app-network
docker run -d --name database-service --network app-network my-database-image
docker run -d --name backend-service --network app-network my-backend-image
Working with External Networks
Docker containers can interact with external networks. Containers can be attached to the host network or linked to user-defined networks, allowing them to access external services or the host system.
# Create a container connected to the host network
docker run -d --name host-connected-container --network host my-image
Multi-Host Networking with Overlay Networks
For distributed applications spanning multiple hosts, Docker offers overlay networks. These networks enable containers on different hosts to communicate as if they were on the same local network.
# Create an overlay network in Docker
docker network create -d overlay my-global-network
Security and Isolation in Docker Networking
Security is crucial when working with Docker networks. Docker enforces security by isolating containers through network namespaces, ensuring that containers are kept separate from each other and the host system.
Summary
In the world of containerization, Docker networking is an indispensable component that enables applications to interact seamlessly while maintaining isolation and security. The advantages of Docker networking are evident in its scalability, flexibility, and ability to simplify deployment, making it a critical tool in the toolkit of modern software developers. As you explore the dynamic field of Docker networking, you’ll discover that its utility extends to diverse use cases, from microservices architecture to multi-host container orchestration.
practical (i did more but main networking is shown below)
creating custom network
create 4 different contaniers with 2 in default bridge network and 2 on custom bridge network here difference was i was able to ping to container of same netowrk via ip in both cases but for custom bridge network i was able to ping via container name too.
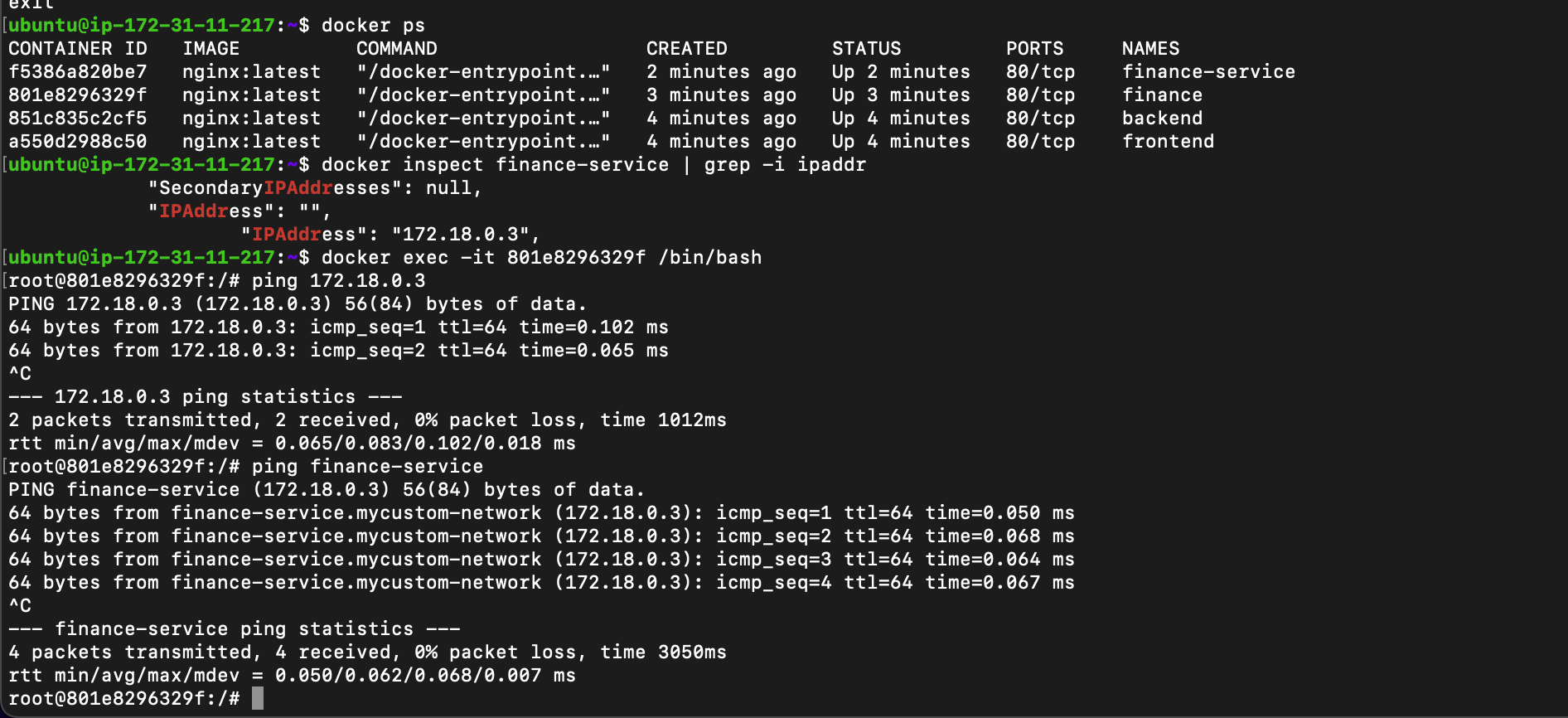
key takeways
-> docker usage docker0 interface as bridge between container and container virtual interface.
->each container has virtual interface created during container creation
->you can easily isolate docker container by placing in different networks.
->you can communicate to each other container via ip in all type of networks
but for custom bridge you can communicate via container name or service name. we always should use service name because if container is down(forced or accidental) then it will get new ip address so communicating via ip is not that good.
Subscribe to my newsletter
Read articles from Amrit Poudel directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
