Cybersecurity in the Age of Gaming: Lessons from Watch Dogs
 Jasai Hansda
Jasai Hansda
In recent years, video games have evolved into immersive narratives, blurring the lines between fiction and reality. Among these, the Watch Dogs series stands out as a gripping portrayal of hacking and cybersecurity.
Set in a world dominated by technology, Watch Dogs offers players a chance to explore the exciting—and often terrifying—possibilities of modern hacking. However, behind the exciting gameplay, there are many real-world cybersecurity lessons. Let's explore the key insights we can learn from this popular series, especially through the different hacking scenarios shown in the game.
Understanding Hacking Techniques
One of the prominent themes in Watch Dogs is the protagonist’s ability to manipulate urban infrastructure using hacking skills. From controlling traffic lights to hacking into surveillance cameras, the game showcases the potential threats and vulnerabilities present in our daily lives.
While some of these techniques are exaggerated for entertainment, they serve as a reminder of real-world vulnerabilities. Hacking techniques used by real-life cybercriminals, including phishing, malware, and social engineering, echo the virtual exploits seen in Watch Dogs. Understanding these methods is crucial for individuals and organizations alike.
Takeaway: Awareness is Key
The first lesson from Watch Dogs is the importance of awareness. Just like the characters in the game navigate complex digital landscapes, players—and real-world users—must stay informed about hacking techniques and emerging cyber threats. A good cybersecurity posture begins with education and awareness.
The Feasibility of Car Hacking and Urban Manipulation
In Watch Dogs, players can hack vehicles, making them go out of control or crash. While this is fiction, this element is not too far from reality. Researchers have demonstrated vulnerabilities in connected vehicles, showcasing how attackers could exploit these weaknesses. Moreover, the manipulation of urban infrastructure, such as traffic lights and cameras, reflects real concerns about the security of smart city technologies.
Real-World Example: Car Hacking
There have been real-life incidents that reflect the dangers portrayed in Watch Dogs. In 2015, hackers Charlie Miller and Chris Valasek remotely accessed a Jeep Cherokee, taking control of its steering, brakes, and even its entertainment system.

Article Link- https://www.wired.com/2015/07/hackers-remotely-kill-jeep-highway/
This demonstration shocked the automotive industry and highlighted the vulnerabilities in modern vehicles, most of which rely heavily on interconnected technologies. The incident led to recalls of over 1.4 million vehicles and underscored the necessity for stronger cybersecurity in the automotive sector.
Takeaway: Securing IoT Devices
As smart devices and vehicles increasingly integrate into our lives, it’s vital to take steps to secure them. Users should:
Change Default Passwords: Many IoT devices come with factory-set passwords that are widely known. Altering these is one of the simplest ways to enhance security.
Regularly Update Firmware: Keep devices updated with the latest security patches to protect against known vulnerabilities.
Surveillance and Privacy Violations
Another hacking aspect in Watch Dogs is the ability to hack into surveillance cameras and social networks. This element reminds us of the fine line between security and privacy. As more cities implement surveillance systems for security purposes, the risk of unauthorized access to sensitive camera feeds and personal data increases.
Real-World Example: Unauthorized Surveillance Access
In 2019, a security vulnerability in a popular video surveillance system allowed hackers to gain unauthorized access to camera feeds from businesses and homes.

Article Link - https://www.nytimes.com/2019/12/15/us/Hacked-ring-home-security-cameras.html
Such breaches can have severe implications, including invasion of privacy and the potential for malicious activities through real-time surveillance. For instance, hackers can use access to plan burglaries or engage in stalking behaviors.
Takeaway: Data Privacy and Protection
To combat these risks, individuals and organizations must adopt strong data protection practices:
Use Encrypted Communications: Ensuring that sensitive communications use encryption can help protect against unauthorized interception.
Implement Access Controls: Limit access to surveillance system feeds to authorized personnel only and regularly check access logs to spot unauthorized attempts.
Infrastructure Manipulation
The manipulation of urban infrastructure, such as traffic lights and public transport systems, features prominently in Watch Dogs. The ability to reset traffic lights or hijack metro trains showcases the potential for chaos in a digitally controlled environment. Such capabilities highlight severe concerns over the security of public utilities and infrastructure.

Real-World Example: Critical Infrastructure Attacks
One significant case occurred in 2020 when a hacking group targeted the Oldsmar water treatment facility in Florida, attempting to increase the sodium hydroxide levels in the water supply remotely.

Article Link - https://edition.cnn.com/2021/02/10/us/florida-water-poison-cyber/index.html
Although the attack was stopped, it showed how vulnerable important infrastructure systems are and the serious consequences if they are compromised. Critical infrastructure hackers can disrupt services, cause public panic, and even endanger lives.
Takeaway: Protecting Critical Systems
Governments and organizations operating critical infrastructures must prioritize cybersecurity. Strategies include:
Conducting Regular Security Audits: Continuously assess the security of critical systems to identify and mitigate vulnerabilities.
Implementing Redundant Systems: Establish backup systems and manual operations to ensure the continued functioning of essential services in the case of a cyber attack.
Social Engineering: The Human Element
Perhaps one of the most fascinating elements of Watch Dogs is the social engineering aspect. The game’s protagonists often rely on manipulation and deception to achieve their goals, which is reflective of real-world scenarios where attackers exploit human psychology to gain access to systems.

Real-World Example: Social Engineering Attacks
High-profile incidents, such as the 2020 Twitter hack, emphasized the power of social engineering.
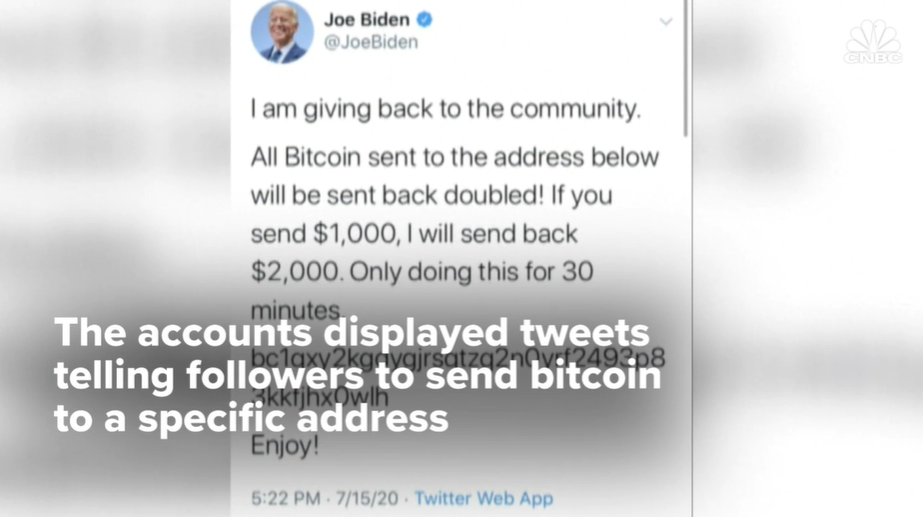
Attackers used phishing tactics to exploit Twitter employees, gaining access to internal tools and taking control of prominent accounts, including those of Barack Obama and Elon Musk. This breach highlights the importance of educating employees about the risks of social engineering.
Takeaway: Educate and Train
Organizations must invest in educating employees about the risks of social engineering. Regular training sessions that highlight common tactics used by cybercriminals can enhance the organization’s overall security posture.
Conclusion: Gaming as a Cybersecurity Tool
In an age where gaming and reality intertwine, embracing these lessons may help us safeguard our digital lives more effectively. So the next time you find yourself immersed in a gaming session, take a moment to ponder the cybersecurity implications of the virtual world—and apply them to your own. The stakes are high, and being informed is the first line of defense in the digital age.
As we continue to coexist with technology, the lessons learned from the streets of Chicago and beyond in Watch Dogs will be essential in navigating the future of cybersecurity.
Play the Game on Stream (Price Drop💰) -https://store.steampowered.com/app/243470/Watch_Dogs/
Subscribe to my newsletter
Read articles from Jasai Hansda directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jasai Hansda
Jasai Hansda
Software Engineer (2 years) | In-transition to DevOps. Passionate about building and deploying software efficiently. Eager to leverage my development background in the DevOps and cloud computing world. Open to new opportunities!