Is Blockchain Truly Safe? A Deep Dive into Attacks, Consensus, and Mitigation Strategies
 Navya Srivastava
Navya Srivastava
Blockchain technology has emerged as a cornerstone of the digital revolution, promising transparency, immutability, and decentralization. While these attributes contribute to a robust security framework, it is essential to recognize that no system is entirely invulnerable. This article explores the common threats to blockchain networks, the mechanisms employed to safeguard them, and real-world examples of attacks and countermeasures.
The Architecture of Blockchain Security
Blockchain security is a multifaceted construct underpinned by three key pillars:
Cryptography: The bedrock of blockchain, cryptography secures transactions, identities, and data integrity through complex mathematical algorithms.
Decentralization: By distributing control across a network of nodes, blockchain mitigates the risk of a single point of failure and renders it significantly more challenging for adversaries to compromise the system.
Consensus: This mechanism ensures agreement among network participants on the valid state of the blockchain, preventing fraudulent transactions and preserving data integrity.
Common Blockchain Attacks
Despite its inherent security, blockchain networks are susceptible to various attacks:
Network-Level Attacks
51% Attack: A malicious actor gains control of over 51% of the network's computing power, enabling manipulation and potential reversal of transactions. The Bitcoin Gold network's 2018 attack, resulting in a $18 million loss, is a stark example.
Sybil Attack: This involves creating multiple fake identities to influence network decisions. The 2019 Ethereum Sybil attack, where over 1,000 fake nodes were generated, underscores the threat.
Eclipse Attack: By isolating specific nodes, attackers can manipulate information received, potentially leading to 51% attacks or double-spending. The Bitcoin network experienced such an attack in 2019.
DoS (Denial of Service) Attack: Overwhelming the network with traffic can hinder legitimate users and disrupt operations. The 2018 Ethereum DoS attack, causing transaction delays, is a notable instance.
Transaction-Level Attacks
Double Spending: Attempting to spend the same digital currency twice. The Bitcoin SV network's 2019 attack, resulting in a $1.6 million loss, highlights the risk.
Race Attack: Exploiting smart contract vulnerabilities to manipulate transaction order. The 2018 Ethereum attack, leading to a $150,000 loss, demonstrates the threat.
Finney Attack: A specific double-spending attack where a miner includes their own transaction in a block. A 2019 Bitcoin attack resulted in a $10,000 loss.
Other Attacks
Phishing: Deceiving users into revealing private information. The 2019 Electrum wallet phishing attack, resulting in a $1 million loss, emphasizes the importance of user education.
Smart Contract Vulnerabilities: Exploiting flaws in smart contract code. The infamous 2017 DAO attack, leading to a $50 million loss, underscores the need for rigorous code audits.
Mitigation Strategies
To bolster blockchain security, various strategies are employed:
Proof of Stake (PoS): By reducing the barrier to entry for node operation, PoS makes it more challenging to amass 51% of the network's power. Ethereum's transition from Proof of Work (PoW) to PoS is a notable example.
Network Diversity: Encouraging a distributed network with numerous nodes and mining pools hinders centralization and reduces vulnerability to 51% attacks.
Code Audits: Thoroughly examining smart contract code to identify and rectify vulnerabilities is crucial. Ethereum's regular code audits exemplify this approach.
User Education: Raising awareness about phishing and other social engineering tactics is essential to protect users.
Consensus Mechanisms: The Foundation of Trust
Understanding the Challenge
Imagine a world without banks, where transactions occur directly between individuals. This is essentially the promise of blockchain technology. But how can we ensure that everyone agrees on the order of transactions and that no one cheats? This is where consensus mechanisms come into play.
Think of a blockchain as a digital ledger. Every transaction is recorded as a block, and these blocks are linked together to form a chain. The challenge is ensuring that all participants agree on the order of these blocks. A consensus mechanism is the algorithm that solves this problem.
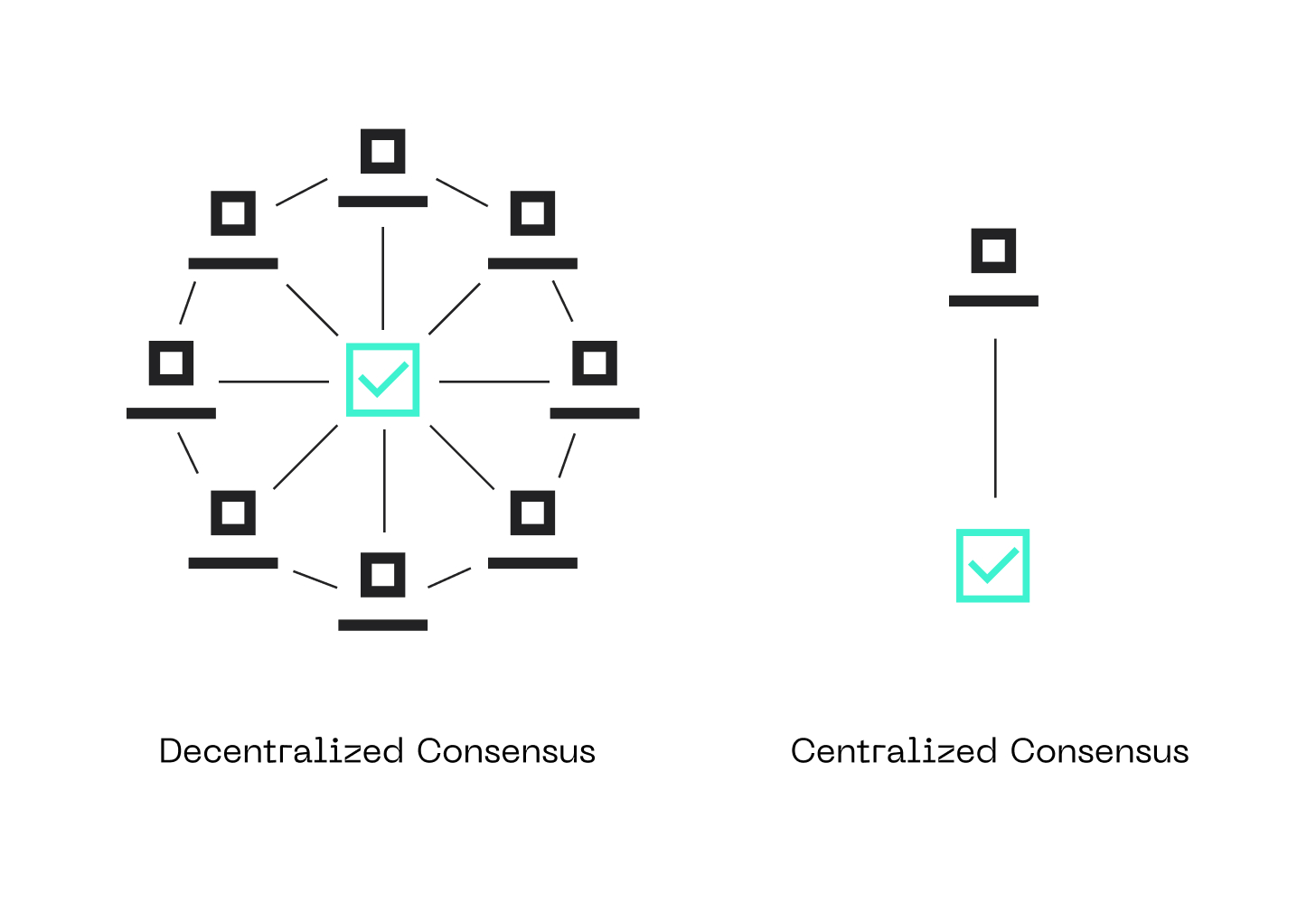
What is a Consensus Mechanism?
A consensus mechanism is a protocol that enables a distributed network of computers to agree on a single data value, despite the possibility of failures or malicious behavior by some of the participants. In the case of blockchain, this data value is the order of transactions.
To put it simply, it's like a group of people trying to decide on a single movie to watch. Everyone has their preferences, but they need to agree on one to proceed. A consensus mechanism is the process that helps them reach a decision.
Types of Consensus Mechanisms
There are several types of consensus mechanisms, each with its own strengths and weaknesses.
Proof of Work (PoW)
How it works: Nodes compete to solve complex mathematical puzzles. The first node to solve the puzzle gets to add the next block to the blockchain. This process is energy-intensive.
Example: Bitcoin
Pros: Highly secure, resistant to attacks.
Cons: Energy-consuming, slow transaction speeds.
Proof of Stake (PoS)
How it works: Nodes stake a certain amount of cryptocurrency to participate in the network. The right to create the next block is assigned based on the amount of staked cryptocurrency.
Example: Ethereum (before the Merge)
Pros: More energy-efficient, faster transaction speeds.
Cons: Less decentralized than PoW, potential for "rich get richer" scenarios.
Delegated Proof of Stake (DPoS)
How it works: A small group of delegates, elected by cryptocurrency holders, validate transactions.
Example: EOS, Tezos
Pros: Faster transaction speeds, more efficient than PoW and PoS.
Cons: Less decentralized, potential for centralization of power.
Proof of Authority (PoA)
How it works: Only pre-approved nodes can validate transactions.
Example: Private blockchains
Pros: Fast transaction speeds, high scalability.
Cons: Less decentralized, relies on trusted nodes.
The Importance of Consensus Mechanisms
Consensus mechanisms are the foundation of trust in blockchain technology. They ensure:
Security: By preventing double-spending and other attacks.
Decentralization: By distributing the validation process across multiple nodes.
Immutability: By making it extremely difficult to alter the blockchain.
Transparency: By making all transactions visible to everyone on the network.
Conclusion
Blockchain security hinges on cryptography, decentralization, and consensus. While offering robust protection, it's vulnerable to attacks like 51% attacks, Sybil attacks, and smart contract exploits. To mitigate these risks, blockchain networks employ Proof of Stake, network diversity, code audits, and user education. The ongoing evolution of consensus mechanisms further strengthens blockchain's resilience.
Subscribe to my newsletter
Read articles from Navya Srivastava directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Navya Srivastava
Navya Srivastava
Hi! I am Navya, a dedicated coding enthusiast, deeply interested in Web3 technologies and exploring the future of decentralized applications and blockchain innovation.