AI-Powered Ethical Hacking: Automating Penetration Testing in DevSecOps
 Subhanshu Mohan Gupta
Subhanshu Mohan Gupta
Introduction
As cyber threats evolve in complexity, the need for robust security practices has never been more critical. Traditional penetration testing, while effective, is often time-consuming and requires skilled professionals. Enter AI-powered automated penetration testing — a game changer for DevSecOps teams looking to stay ahead of potential vulnerabilities. In this article, we’ll explore how AI can transform the penetration testing process, helping teams identify and mitigate threats more efficiently, while also delving into the ethical considerations that come with automating security practices.
The Role of AI in Penetration Testing
AI-Driven Vulnerability Identification
AI models, particularly those trained on vast datasets of known vulnerabilities and attack vectors, can automatically scan and analyze systems for weaknesses. These models can identify patterns that may elude even seasoned security professionals, ensuring that no stone is left unturned in the search for vulnerabilities.
Example: Imagine a web application running in a multi-cloud environment. An AI model, continuously monitoring the application, detects an anomaly in the traffic patterns — a potential SQL injection attack vector. The AI not only identifies the vulnerability but also suggests a remediation strategy based on historical data from similar environments.
Continuous Testing with AI
Unlike traditional penetration testing, which is often conducted at scheduled intervals, AI-powered systems can perform continuous testing. This approach ensures that new vulnerabilities introduced through code changes or configuration updates are promptly detected and addressed.
Example: Consider a DevSecOps pipeline where every code commit triggers an automated security test. An AI system integrated into this pipeline scans the code for potential security flaws before it reaches production, effectively embedding security checks into the CI/CD process.
Architecture Diagram
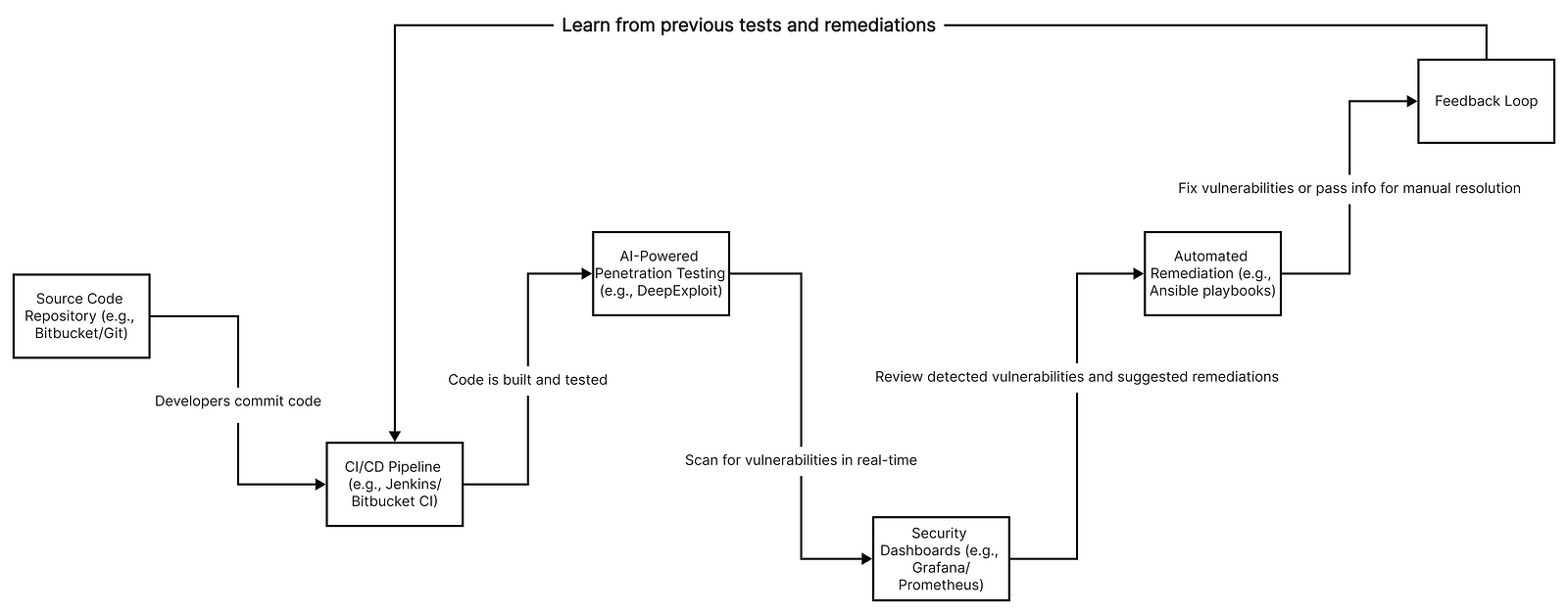
AI-powered penetration testing framework within a DevSecOps pipeline
Diagram Description -
The architecture diagram illustrates an AI-powered penetration testing framework within a DevSecOps pipeline.
1. Source Code Repository (e.g., Bitbucket/Git): The process begins with developers committing code to the repository.
- CI/CD Pipeline: The committed code triggers a CI/CD pipeline (e.g., Jenkins/Bitbucket CI), where the code is built and tested.
3. AI-Powered Penetration Testing: Within the CI/CD pipeline, an AI-powered penetration testing tool (e.g., DeepExploit) scans the application for vulnerabilities. This tool leverages machine learning algorithms to identify potential threats in real-time.
4. Security Dashboards (e.g., Grafana/Prometheus): Results from the AI-powered tests are sent to security dashboards, where DevSecOps teams can review detected vulnerabilities and suggested remediations.
5. Automated Remediation: Based on the AI’s findings, automated remediation scripts (e.g., Ansible playbooks) can be triggered to fix the vulnerabilities, or the information can be passed to developers for manual resolution.
- Feedback Loop: The system continuously learns from previous tests and remediations, improving its detection capabilities over time.
Ethical Considerations
While AI-powered penetration testing offers significant benefits, it also raises ethical questions:
- Bias in AI Models: AI models are only as good as the data they are trained on. If the training data is biased, the AI could overlook certain vulnerabilities or overemphasize others, leading to incomplete security assessments.
- Automated Decision-Making: Automating security decisions can be risky if not properly supervised. There’s a fine line between automating tasks and relying too heavily on AI, which could lead to missed vulnerabilities or false positives.
- Privacy Concerns: The use of AI in penetration testing must be handled carefully to avoid inadvertently exposing sensitive data during the scanning process.
Example: An AI system, trained primarily on datasets from financial institutions, might miss vulnerabilities unique to healthcare applications. To mitigate this, it’s essential to continually update and diversify the training data, ensuring that the AI model remains effective across different industries.
Testing and Validation
End-to-End Testing:
To ensure that the AI-powered penetration testing framework works as expected, it’s crucial to implement thorough end-to-end testing. This involves simulating various attack scenarios in a controlled environment and validating that the AI system correctly identifies and mitigates the threats.
Steps -
1. Simulate Attacks: Use tools like Metasploit to simulate different types of attacks (e.g., SQL injection, cross-site scripting) on the application.
2. AI Detection: Ensure that the AI-powered system detects these simulated attacks in real-time.
3. Remediation Validation: Verify that the automated remediation scripts effectively neutralize the threats.
4. Feedback Analysis: Review the AI’s feedback loop to confirm that it learns and adapts from each test, improving its detection accuracy over time.
Conclusion:
AI-powered ethical hacking is set to revolutionize the way DevSecOps teams approach security. By automating penetration testing, organizations can stay ahead of evolving threats, reduce the time and effort required for security assessments, and ultimately create a more secure software development lifecycle. However, as with any powerful tool, it’s essential to navigate the ethical implications carefully, ensuring that AI is used responsibly to bolster, not replace, human expertise.
Subscribe to my newsletter
Read articles from Subhanshu Mohan Gupta directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Subhanshu Mohan Gupta
Subhanshu Mohan Gupta
A passionate AI DevOps Engineer specialized in creating secure, scalable, and efficient systems that bridge development and operations. My expertise lies in automating complex processes, integrating AI-driven solutions, and ensuring seamless, secure delivery pipelines. With a deep understanding of cloud infrastructure, CI/CD, and cybersecurity, I thrive on solving challenges at the intersection of innovation and security, driving continuous improvement in both technology and team dynamics.