Azure AKS Hands-On Labs - Creating a private cluster using Azure CNI mode overlay
 Francisco Souza
Francisco SouzaTable of contents
- 📝Introduction
- 📝Log in to the Azure Management Console
- 📝Prerequisites:
- 📝Setting an Azure Storage Account to Load Bash or PowerShell
- 📝Create a Resource Group
- 📝Create a Virtual Network and Subnet
- 📝Create Network Security Groups (NSGs)
- 📝Associate NSG with Subnet
- 📝Create a private AKS Cluster
- 📝Connect to a Private AKS Cluster

📝Introduction
In this hands-on lab, we will guide for creating an Azure Kubernetes Service (AKS) private cluster using Azure CNI mode overlay.
Learning objectives:
In this module, you'll learn how to:
Create a virtual network and a subnet where the AKS cluster will be deployed
Create an NSG and configure rules to allow necessary traffic between nodes and pods
Associate the NSG with the subnet created earlier
Create an AKS cluster with Azure CNI Overlay networking mode
📝Log in to the Azure Management Console
Using your credentials, make sure you're using the right Region. In my case, I am using the region uksouth in my Cloud Playground Sandbox.
📌Note: You can also use the VSCode tool or from your local Terminal to connect to Azure CLI
More information on how to set it up is at the link.
📝Prerequisites:
Update to PowerShell 5.1, if needed.
Install .NET Framework 4.7.2 or later.
Visual Code
Web Browser (Chrome, Edge)
Azure CLI installed
Azure subscription
Docker installed
📝Setting an Azure Storage Account to Load Bash or PowerShell
- Click the Cloud Shell icon
(>_)at the top of the page.

- Click PowerShell.

- Click Show Advanced Settings. Use the combo box under Cloud Shell region to select the Region. Under Resource Group and Storage account(It's a globally unique name), enter a name for both. In the box under File Share, enter a name. Click ***Create storage (***if you don't have any yet).

📝Create a Resource Group
Let's to create a Resource Group and some variables to be used.
#Variable created to some resources $rg=<resourcr-groupname> $location=<region-name> az group create -n $rg -l $location
📝Create a Virtual Network and Subnet
Let's to create some variables to be used and the vNet and Subnet.
#Variable created to some resources $vnet=<vnet-name> $subnet=<subnet-name> az network vnet create -g $rg -n $vnet --address-prefix 10.0.0.0/8 --subnet-name $subnet --subnet-prefix 10.240.0.0/16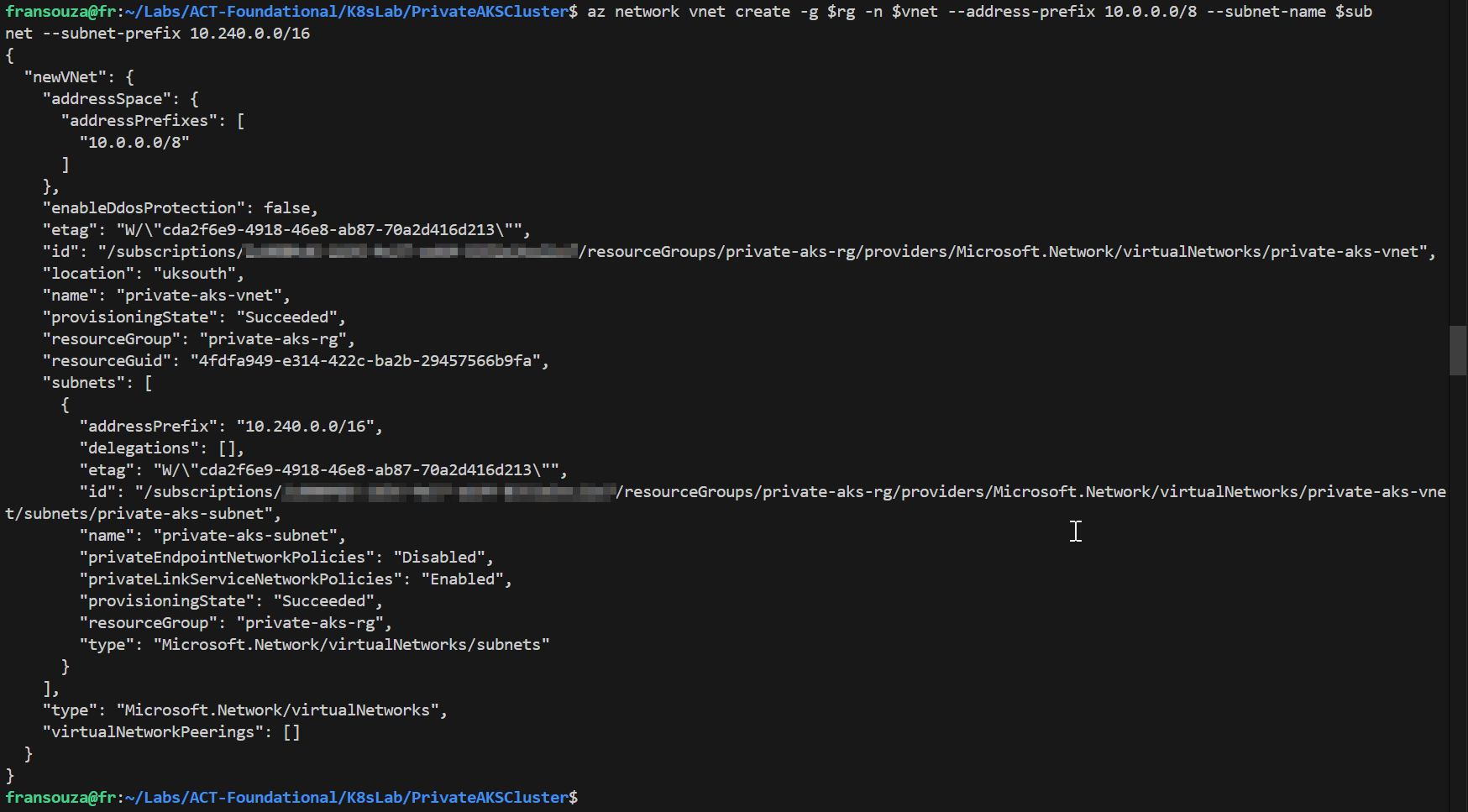
📝Create Network Security Groups (NSGs)
Let's to create some variables to be used and the NSGs.
#Variable created to some resources $nsg=<nsg-name> $subnet=<subnet-name> az network nsg create -g $rg -n $nsg az network nsg rule create -g $rg --nsg-name $nsg --name AllowInternalTraffic --priority 1000 --source-address-prefixes 10.0.0.0/8 --destination-address-prefixes 10.0.0.0/8 --access Allow --protocol '*' --direction Inbound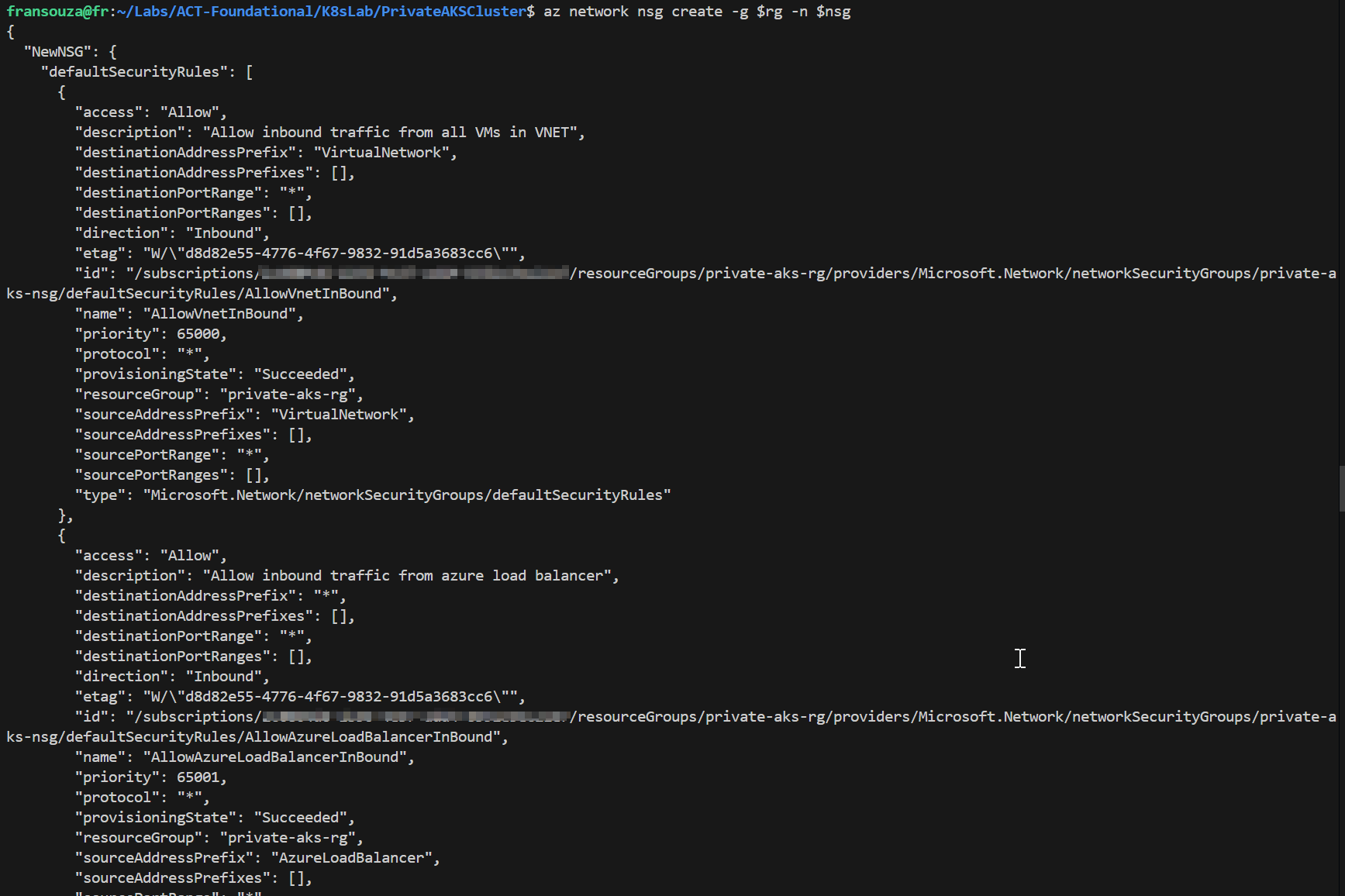
📝Associate NSG with Subnet
Let's to associate the NSG to the Subnet.
az network vnet subnet update -g $rg --vnet-name $vnet --name $subnet --network-security-group $nsg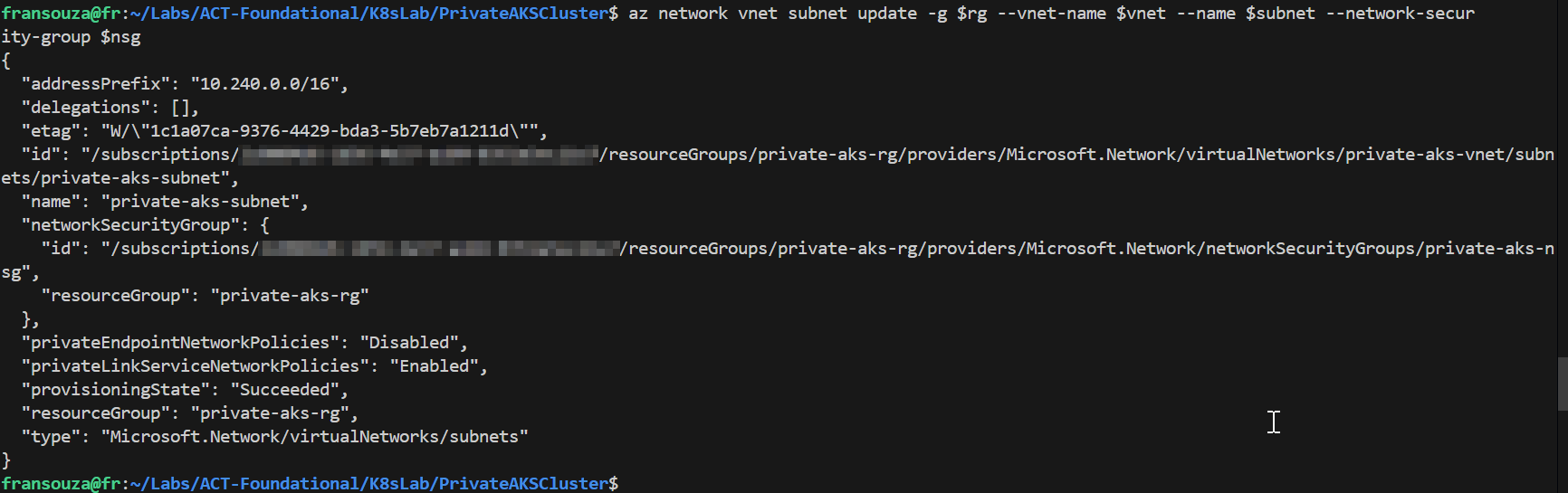
📝Create a private AKS Cluster
Let's to create some variables to be used and the following command to create an AKS cluster with Azure CNI Overlay networking.
#Variable created to some resources $aks=<aks-name> az aks create -g $rg -n $aks \ --vnet-subnet-id $(az network vnet subnet show -g $rg --vnet-name $vnet --name $subnet --query id -o tsv) \ --network-plugin azure \ --network-plugin-mode overlay \ --pod-cidr 192.168.0.0/16 \ --enable-private-cluster \ --enable-managed-identity \ --node-count 2 \ --generate-ssh-keys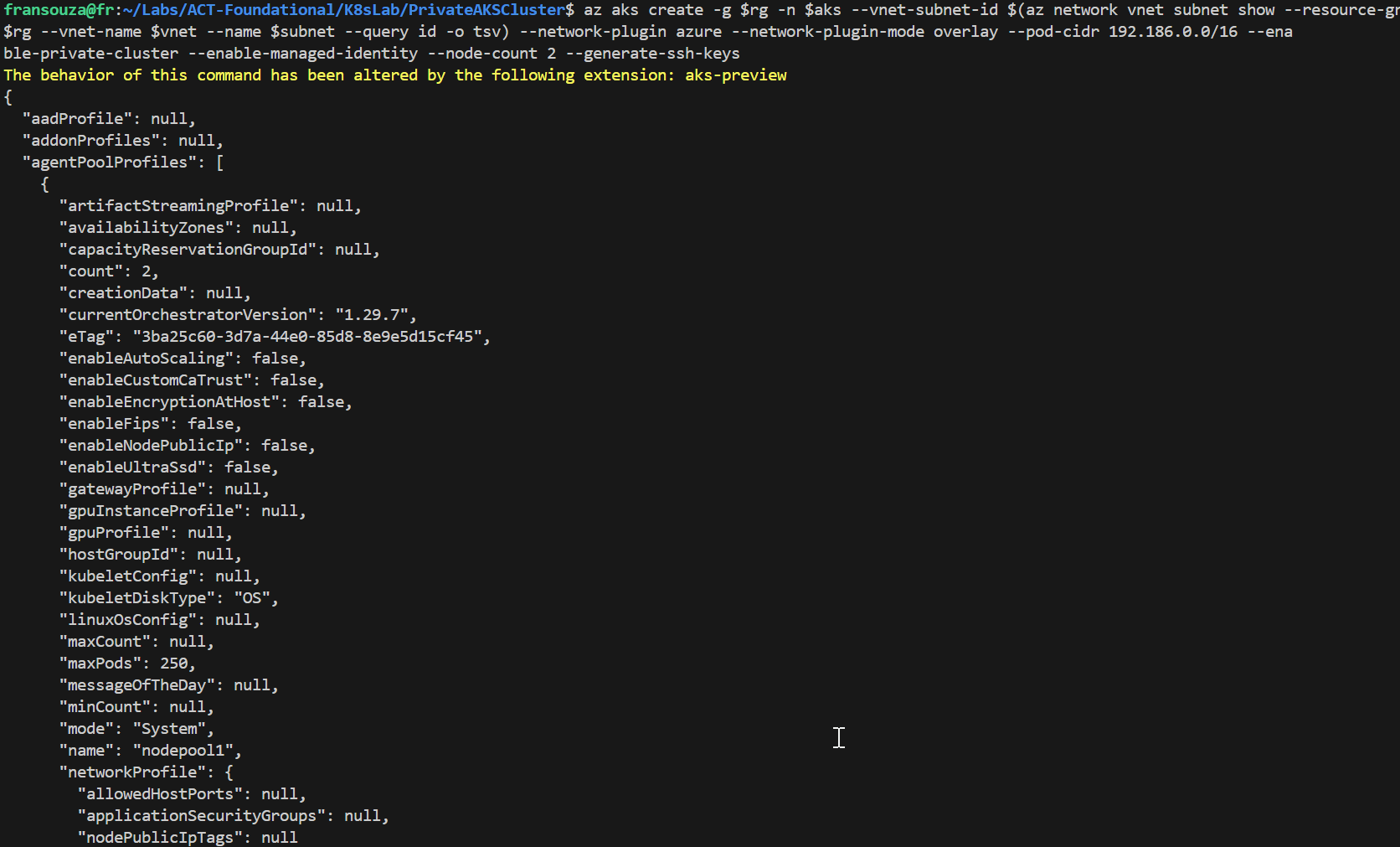
📝Connect to a Private AKS Cluster
The access to a private AKS cluster from the cluster virtual network, a peered network, or a configured private endpoint require configuring a VPN, Express Route, deploying a jumpbox within the cluster virtual network, or creating a private endpoint inside of another virtual network.
The
command invokecan be used by the Azure CLI to access private clusters without the need to configure a VPN or Express Route.command invokeallows us to remotely invoke commands, likekubectlandhelm, on our private cluster through the Azure API without directly connecting to the cluster.More details on this link.
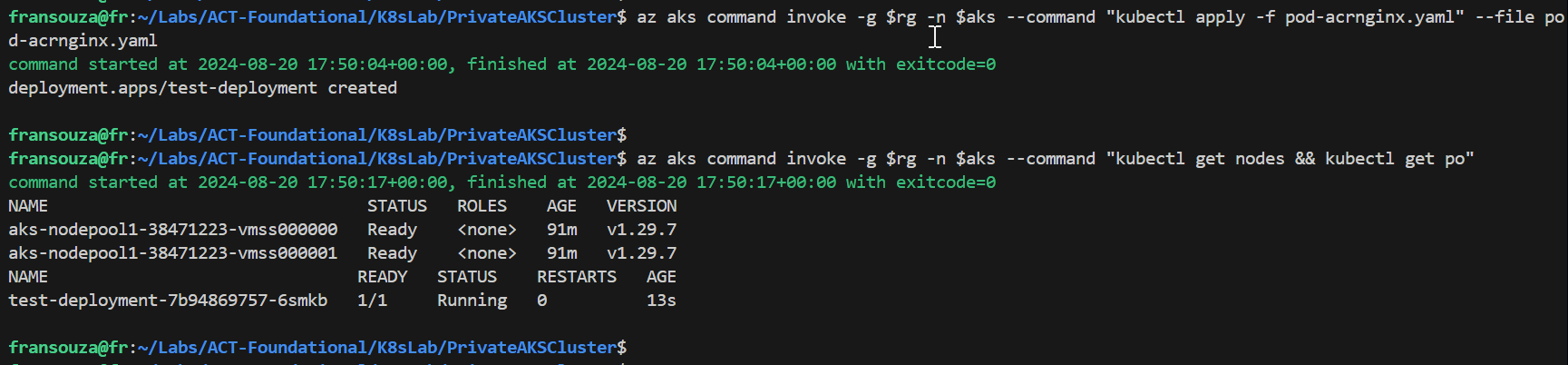
#Run multiple commands on the command invoke az aks command invoke -g $rg -n $aks --command "kubectl get nodes && kubectl get ns" az aks command invoke -g $rg -n $aks --command "kubectl get nodes && kubectl get po" #Run commands with all files in the current directory attached az aks command invoke -g $rg -n $aks --command "kubectl apply -f <file-name>.yaml" --file <file-name>.yaml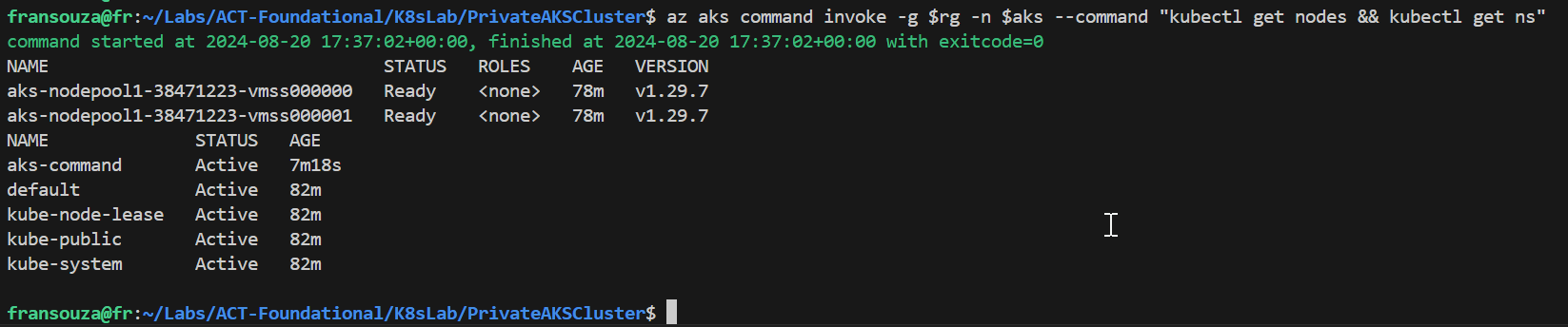
📌Note - At the end of each hands-on Lab, always clean up all resources previously created to avoid being charged.
Congratulations — you have completed this hands-on lab covering the basics of Creating a private AKS cluster using Azure CNI mode overlay.
Thank you for reading. I hope you understood and learned something helpful from my blog.
Please follow me on Cloud&DevOpsLearn and LinkedIn, franciscojblsouza
Subscribe to my newsletter
Read articles from Francisco Souza directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Francisco Souza
Francisco Souza
I have over 20 years of experience in IT Infrastructure and currently work at Microsoft as an Azure Kubernetes Support Engineer, where I support and manage the AKS, ACI, ACR, and ARO tools. Previously, I worked as a Fault Management Cloud Engineer at Nokia for 2.9 years, with expertise in OpenStack, Linux, Zabbix, Commvault, and other tools. In this role, I resolved critical technical incidents, ensured consistent uptime, and safeguarded against revenue loss from customers. Additionally, I briefly served as a Technical Team Lead for 3 months, where I distributed tasks, mentored a new team member, and managed technical requests and activities raised by our customers. Previously, I worked as an IT System Administrator at BN Paribas Cardif Portugal and other significant companies in Brazil, including an affiliate of Rede Globo Television (Rede Bahia) and Petrobras SA. In these roles, I developed a robust skill set, acquired the ability to adapt to new processes, demonstrated excellent problem-solving and analytical skills, and managed ticket systems to enhance the customer service experience. My ability to thrive in high-pressure environments and meet tight deadlines is a testament to my organizational and proactive approach. By collaborating with colleagues and other teams, I ensure robust support and incident management, contributing to the consistent satisfaction of my customers and the reliability of the entire IT Infrastructure.