Infrastructure Management
 Amitt Ashok
Amitt Ashok
What is Infrastructure or Configuration Management?
In simple terms, configuration management involves building or creating the infrastructure for an application or software. Let's understand this with an example: if you create an application, you need a machine with 4GB RAM, some hard disk space, and 2 or more CPUs to run it. These requirements are your application's configuration or infrastructure.
Nowadays, everything from development to deployment is fast. However, building a single machine with the required configuration can be hard and time-consuming. To make configuration fast, reliable, and accurate, we have TERRAFORM. As we understand configuration, let's move on to understanding what Terraform is??
Terraform
Terraform was started by HashiCorp team in July 2011, when the first version, Terraform 0.1, was introduced.
Terraform is an infrastructure-as-code tool that defines both cloud and on-premise resources in human-readable configuration files. It is an open-source configuration management tool that makes creating configurations easy and offers several advantages. But you will think there are other tools in the market for this management so why terraform only, let's discuss the advantages of terraform.
Multi-cloud Support: Terraform supports multiple cloud providers as well as on-premises environments, making it easy to provision configuration code. You can use the same configuration code to provision resources in multiple clouds (AWS, Azure, GCP, Alibaba, etc.).
Large Ecosystem: Many providers work with Terraform, including official, partner, and community providers. This means there are a vast number of pre-built modules and configurations available for a wide range of services.
Declarative Syntax: Terraform uses declarative syntax, where you only specify the desired state without worrying about how it will happen. This makes Terraform a leader in the industry.
State Management: Terraform maintains current state files that track the current state. This allows you to easily differentiate between the actual and desired states.
Plan and Apply: With Terraform's plan and apply features, you can easily review what will be created and what will not.
Community Support: Terraform has a large and active user base where you can find tips and troubleshooting answers easily.
Integration with Other Tools: Terraform easily integrates with other DevOps tools like Docker, Kubernetes, and Ansible, which helps make CI/CD pipelines easier.
HCL Language: Terraform uses HashiCorp Configuration Language (HCL), which is specially designed for configuration code. It is in a human-readable format, making it easy for development and operations teams to understand.
How Terraform Works
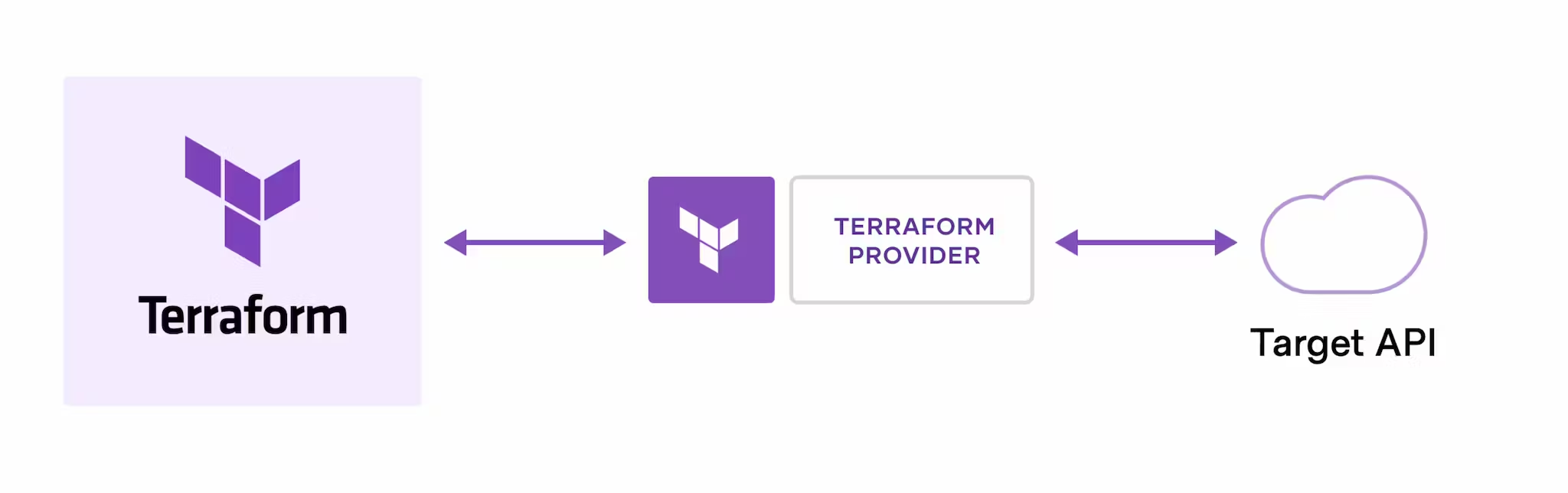
Terraform works with the help of API as code, where API hits requested providers.
Terraform Important terminology
Provider: A plugin that works according to the specified cloud provider. It defines and manages resources for specific clouds such as AWS, Azure, GCP, etc.
Resource: A specific infrastructure component in a configuration file. It can be an EC2 instance, VM machine, S3 bucket, database, network component, and so on.
Module: A reusable and encapsulated unit of Terraform code. Modules allow us to package infrastructure code efficiently.
Configuration File: A file that specifies providers, resources, variables, and outputs, with a
.tfextension, to define the desired infrastructure state.Variable: Placeholders for values that can be passed into your configurations. They make your code more flexible and reusable by allowing you to define values outside of your code and pass them in when you apply the Terraform configuration.
Output: Typically used to display the value of an infrastructure component for other requirements, like a public IP address or subnet.
Terraform Lifecycle
Lifecycle is the flow of Terraform. To run configuration code properly, you need to understand the lifecycle and use it in managing configurations.
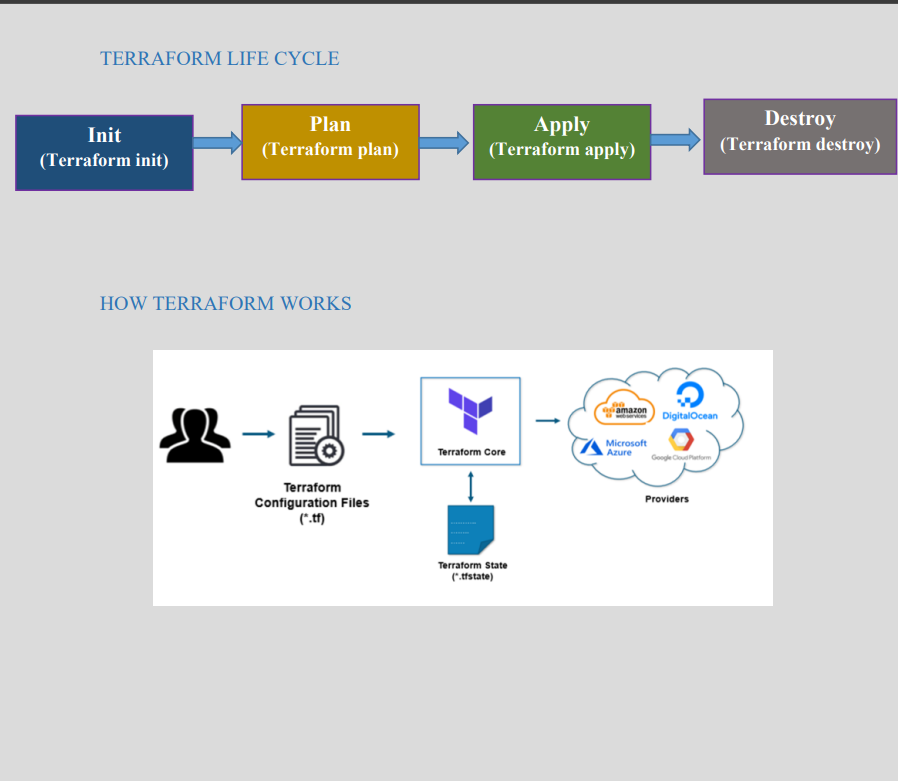
terraform init:- This is the first command used to make your code work as IaC. It initializes the working directory, downloads the necessary provider plugins and modules, and sets up the backend for storing your infrastructure's state./terra-project/module/ec2-instance$ terraform init Initializing the backend... Initializing provider plugins... - Finding hashicorp/aws versions matching "~> 5.0"... - Installing hashicorp/aws v5.63.1... - Installed hashicorp/aws v5.63.1 (signed by HashiCorp) Terraform has created a lock file .terraform.lock.hcl to record the provider selections it made above. Include this file in your version control repository so that Terraform can guarantee to make the same selections by default when you run "terraform init" in the future. Terraform has been successfully initialized! You may now begin working with Terraform. Try running "terraform plan" to see any changes that are required for your infrastructure. All Terraform commands should now work. If you ever set or change modules or backend configuration for Terraform, rerun this command to reinitialize your working directory. If you forget, other commands will detect it and remind you to do so if necessary. amitt-ashok@ubuntu:~/terra-project/module/ec2-instance$terraform plan:- Once you write the configuration code, theterraform plancommand reviews what you are about to create based on the code you have written./terra-project/module/ec2-instance$ terraform plan Terraform used the selected providers to generate the following execution plan. Resource actions are indicated with the following symbols: + create Terraform will perform the following actions: # aws_instance.my-new-server will be created + resource "aws_instance" "my-new-server" { + ami = "ami-0e86e20dae9224db8" + arn = (known after apply) + associate_public_ip_address = (known after apply) + availability_zone = (known after apply) + cpu_core_count = (known after apply) + cpu_threads_per_core = (known after apply) + disable_api_stop = (known after apply) + disable_api_termination = (known after apply) + ebs_optimized = (known after apply) + get_password_data = false + host_id = (known after apply) + host_resource_group_arn = (known after apply) + iam_instance_profile = (known after apply) + id = (known after apply) + instance_initiated_shutdown_behavior = (known after apply) + instance_lifecycle = (known after apply) + instance_state = (known after apply) + instance_type = "t2.micro" + ipv6_address_count = (known after apply) + ipv6_addresses = (known after apply) + key_name = "new_keys" + monitoring = (known after apply) + outpost_arn = (known after apply) + password_data = (known after apply) + placement_group = (known after apply) + placement_partition_number = (known after apply) + primary_network_interface_id = (known after apply) + private_dns = (known after apply) + private_ip = (known after apply) + public_dns = (known after apply) + public_ip = (known after apply) + secondary_private_ips = (known after apply) + security_groups = (known after apply) + source_dest_check = true + spot_instance_request_id = (known after apply) + subnet_id = (known after apply) + tags = { + "name" = "server1" } + tags_all = { + "name" = "server1" } + tenancy = (known after apply) + user_data = (known after apply) + user_data_base64 = (known after apply) + user_data_replace_on_change = false + vpc_security_group_ids = (known after apply) + capacity_reservation_specification (known after apply) + cpu_options (known after apply) + ebs_block_device (known after apply) + enclave_options (known after apply) + ephemeral_block_device (known after apply) + instance_market_options (known after apply) + maintenance_options (known after apply) + metadata_options (known after apply) + network_interface (known after apply) + private_dns_name_options (known after apply) + root_block_device (known after apply) } Plan: 1 to add, 0 to change, 0 to destroy. Changes to Outputs: + public_ip-address = (known after apply)terraform apply: This command uses the created configuration code to create the specified resources concerning cloud providers.terraform destroy: Terraform works with a single-click create and single-click destroy approach. The destroy command removes everything that was created earlier with the apply command.Create an EC2 instance with the help of Terraform...
you can check this website to understand different resources and providers:
https://registry.terraform.io/providers/hashicorp/aws/latest/docs/resources/instance
# First create provider terraform { required_providers { aws = { source = "hashicorp/aws" version = "~> 5.0" } } } provider "aws" { region = "ap-south-1" } # create aws ec2 instance resource "aws_instance" "my-server" { ami = "ami-0522ab6e1ddcc7055" instance_type = "t2.micro" key_name = "server-new" tags = { Name = "my-web-server" } }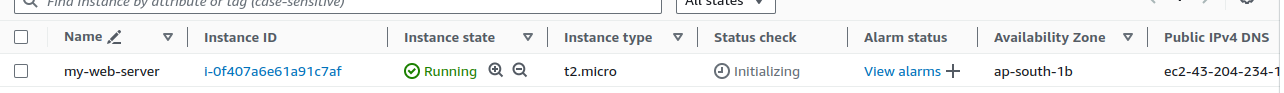
You can check that the EC2 instance is running. Now, with a single click of
terraform destroy, it will be removed.
To summarize this article, we have understood what configuration management is and how Terraform helps with configuration management as IaC. We also explored the advantages of Terraform and its lifecycle. Finally, we created a configuration file to set up an AWS EC2 instance.
Thank You for the Day...
See you Soon...
Subscribe to my newsletter
Read articles from Amitt Ashok directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Amitt Ashok
Amitt Ashok
Hey Hi there, Amit here... I love to explore new things and learn new technology.