Troubleshooting AWS IAM Identity Center Permission Issues: A Step-by-Step Guide
 Benjamin Genz
Benjamin Genz
We are managing permissions to our AWS Organization and attached accounts via IAM Identity Center (formerly AWS SSO).
We maintain a repository where a file called assignments.json holds all of the mappings (i.e. assignments) of users to accounts and permission sets. These assignments are deployed via terraform through Infrastructure-as-Code (IaC). By working with Github PRs we guarantee a review process when new permissions are needed by anyone and it it transparent, when and why these permissions where granted or denied.
Sometimes in the deployment of new assignments things go wrong and the call to CreateAccountAssignment fails. However through Cloudtrail and the Identity Center API it is quite easy to find out what has happened. Here's how:
figure out meta-information about the
CreateAccountAssignmentcallcall
DescribeAccountAssignmentCreationStatuswith the corresponding metadata and find out more about the underlying issue
Find out meta-information
Go to Event History in the Cloudtrail console. Select Event name as Lookup attribute and CreateAccountAssignment as value. Select an appropriate time frame and hit enter to see all the logged calls.
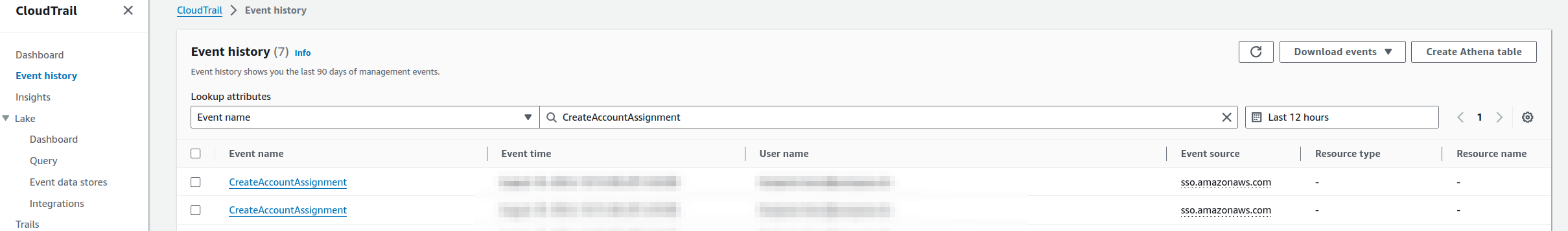
Click on the call you want to check out and from the Event record copy the relevant metainformation. You'll need requestParameters.instanceArn and responseElements.accountAssignmentCreationStatus.requestId for your inquiry.
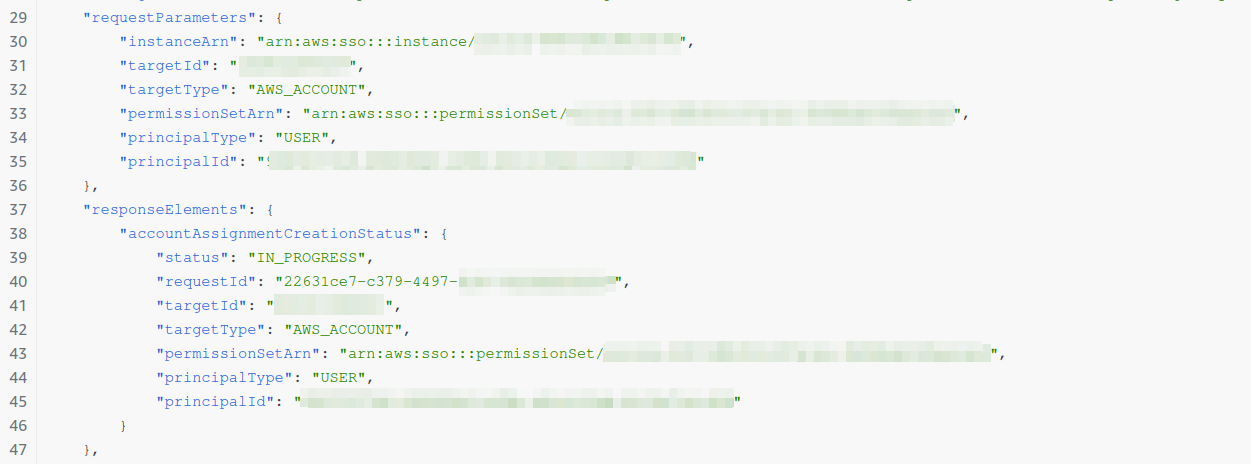
Find the reason of the failed call
Open a shell (you can also use Cloudshell) and assume the required role, like a readonly role in the account the CreateAccountAssignment call was made (usually the root account or delegated account).
Ask the DescribeAccountAssignmentCreationStatus using the AWS CLI:
aws sso-admin describe-account-assignment-creation-status \
--instance-arn arn:aws:sso:::instance/ssoins-... \
--account-assignment-creation-request-id 22631ce7-c379-...
{
"AccountAssignmentCreationStatus": {
"Status": "FAILED",
"RequestId": "22631ce7-c379-...",
"FailureReason": "Received a 402 status error: Number of attached policies to role AWSReservedSSO_... for account ... has exceeded the IAM limit.\nPlease refer to the IAM limit documentation and have the limit increased for all the accounts within the Organization.",
"TargetId": "...",
"TargetType": "AWS_ACCOUNT",
"PermissionSetArn": "arn:aws:sso:::permissionSet/...",
"PrincipalType": "USER",
"PrincipalId": "...",
"CreatedDate": "..."
}
}
As you can see here, we have tried to attach too many policies (the limit is 10) to the provisioned role.
Final Words
I hope this small how-to will help you to figure out why you cannot seem to create assignments of users to permission sets to accounts. Follow for more advanced AWS content!
Subscribe to my newsletter
Read articles from Benjamin Genz directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
