Satoshi Scoop Weekly, 23 Aug 2024
 Cryptape
CryptapeTable of contents
- Crypto Insights
- Bitcoin Silent Payment Advantages and Limitations Analysis
- Bitcoin Core: Proposal to Allow Lightning Network Payers to Voluntarily Disclose Identity
- BitVM2 and BitVM Bridging: A New Trust-Minimized, Bitcoin Layer 2 Bridging Protocol
- Lava Loans Protocol v2: a Bitcoin Collateralized Loan Protocol Based on DLC
- Lendasat White Paper: DLC-Based Bitcoin Escrow-Less Collateral Protocol
- DA for Bitcoin L2, Necessary or Not?
- Babylon Labs: How Bitcoin Can Address the Flaws of PoS?
- Analysis of CoreDAO, a Non-Custodial Bitcoin Layer 2 Model
- Balaji's Network School Enrollment Open
- Visualized Ranking of Bitcoin Contributors
- Calculating Empires: Technological Milestones Over Five Centuries
- Top Reads on Blockchain and Beyond

Crypto Insights
Bitcoin Silent Payment Advantages and Limitations Analysis
Silent Payments (BIP352) has several benefits:
A single address published by an organization or individual auto-generates new addresses for each transaction
Sender can repeatedly use the same static address without tracking multiple addresses
Recipient cannot associate donations to the same sender due to the generation of a new address per transaction.
Transactions appear like ordinary Bitcoin transactions, making Silent Payments less noticeable.
No server is needed; any wallet that supports Silent Payments can handle all technical requirements locally.
Despite these privacy-friendly advantages, Silent Payments have downsides, including the time-consuming process of scanning the blockchain for received payments and limited wallet support. However, the article argues that protecting user privacy through native Bitcoin protocol is important.
Bitcoin Core: Proposal to Allow Lightning Network Payers to Voluntarily Disclose Identity
Bastien Teinturier posted on Delving Bitcoin, proposing to allow payers to optionally include extra data in payments, such as to reveal their identity, helping recipients recognize whether the payer is a contact.
The proposal is seeking feedback on cryptographic methods, with results to be included in BLIP42 (GitHub PR).
BitVM2 and BitVM Bridging: A New Trust-Minimized, Bitcoin Layer 2 Bridging Protocol
BitVM2 is a significant improvement over the previous BitVM; BitVM Bridge is currently the safest BTC bridge design.
BitVM2 aims to support arbitrary computations protected by Bitcoin through optimistic off-chain execution and on-chain fraud prevention, introducing a permissionless system that allows any user to challenge suspicious transactions.
Lava Loans Protocol v2: a Bitcoin Collateralized Loan Protocol Based on DLC
Lava Loans Protocol v2 is a decentralized Bitcoin collateralized loan system based on Discreet Log Contracts (DLCs), mitigating risks from centralized Bitcoin collateralized loan services.
DLCs are a smart contract structure designed for a settlement depending on the outcomes of external events, such as crypto market prices, sports results. This relies on one or multiple oracles to sign messages, proving the actual results of real-world events. These signed messages serve as the basis for adapter signatures, unlocking specific pre-signed transactions.
By slightly modifying the DLC protocol to include a basic hash lock and introducing a clearing mechanism similar to DLC Markets, Lava Loans protocol offers an atomic and trustless process for borrowers and lenders. It reflects the value of adapting existing Bitcoin contract structures to fit specific use cases without centralized risks.
Lendasat White Paper: DLC-Based Bitcoin Escrow-Less Collateral Protocol
Lendasat introduced a DLC- and HTLC-based, escrow-less Bitcoin collateral protocol.
DA for Bitcoin L2, Necessary or Not?
UTXOStack discusses data availability (DA), noting:
DA differs from data retrievability, focusing on accessing and verifying transaction sets related to a specific block, rather than obtaining on-chain historical data.
DA is crucial for Rollup security, allowing funds withdrawal back to Layer 1 even in the worst-case scenarios, such as sequencers ceasing to work or acting maliciously.
Security does not necessarily depend on DA.
DA is beneficial for Bitcoin L2 by raising the cost of malicious attacks and lowering the barrier to challenges.
Babylon Labs: How Bitcoin Can Address the Flaws of PoS?
Babylon co-founder David Tse analyzed PoS shortcomings on a podcast and explained how Bitcoin offers solutions.
For in-depth analysis, refer to his co-authored paper: Bitcoin-Enhanced Proof-of-Stake Security: Possibilities and Impossibilities
Analysis of CoreDAO, a Non-Custodial Bitcoin Layer 2 Model
BitMEX Research team evaluated several Bitcoin layer 2 systems, including the Lightning Network, Ethereum's WBTC, Blackstone's $IBIT, and CoreDAO sidechains, where the key factor to measure is whether the system is non-custodial.
CoreDAO is one of the two non-custodial systems covered by this research. It is a Bitcoin sidechain compatible with the EVM, doing merge mining with Bitcoin through OP_Return commitment in coinbase transactions.
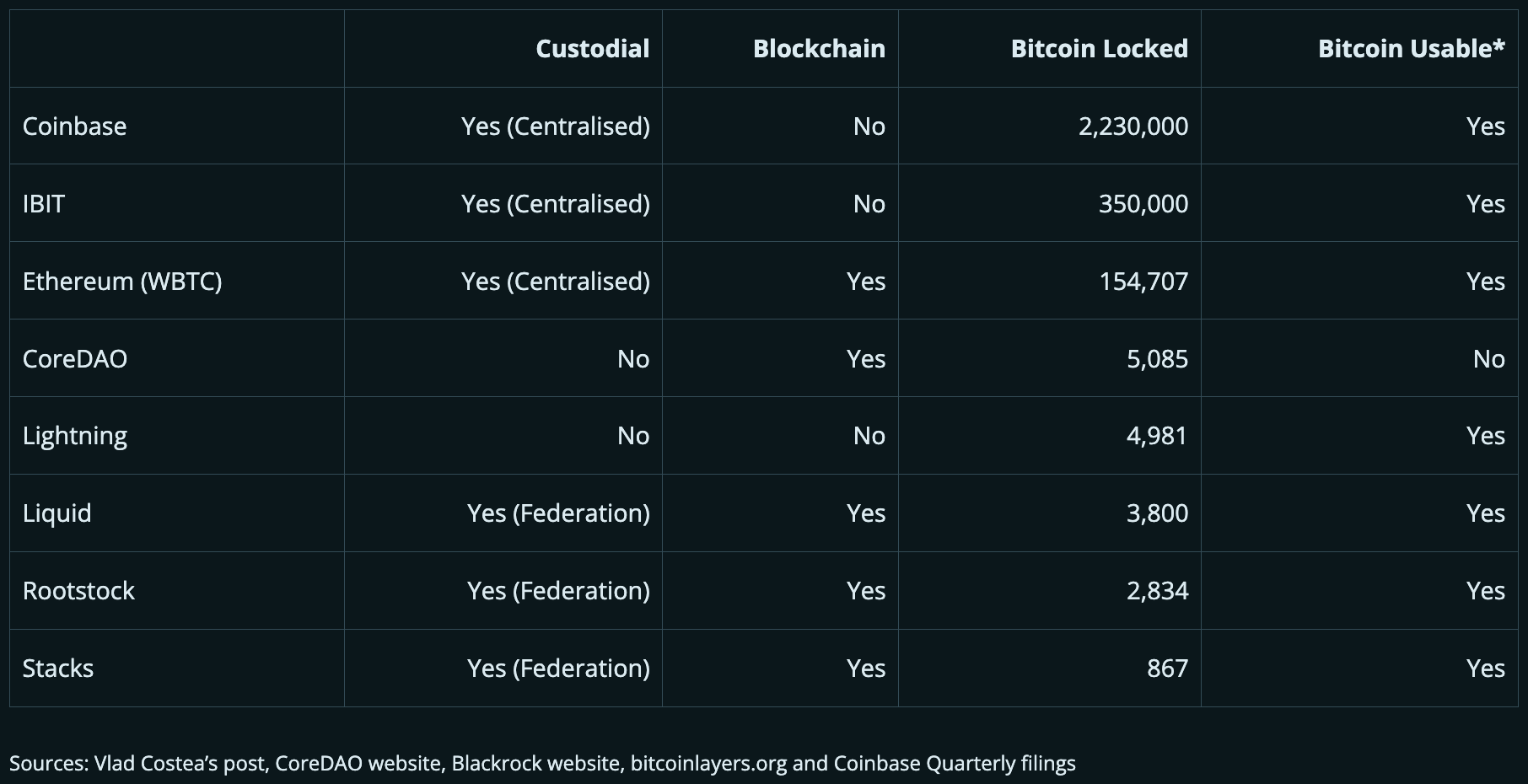
Image via: BitMEX
Balaji's Network School Enrollment Open
Balaji’s "Network School" in Singapore is open for a 90-day program from September 23 to December 23.
Designed for "dark talent", the school is "a techno-capitalist college town, a Stanford 2.0 that’s globally affordable and genuinely meritocratic", offering a structured program: learning skills, burning calories, earning currency, and having fun.
Application at: https://lu.ma/networkschool
Visualized Ranking of Bitcoin Contributors
The author explores the history of Bitcoin from Github data, finding:
Fewer than 400 contributors total
The top five contributors by the number of contributions are:
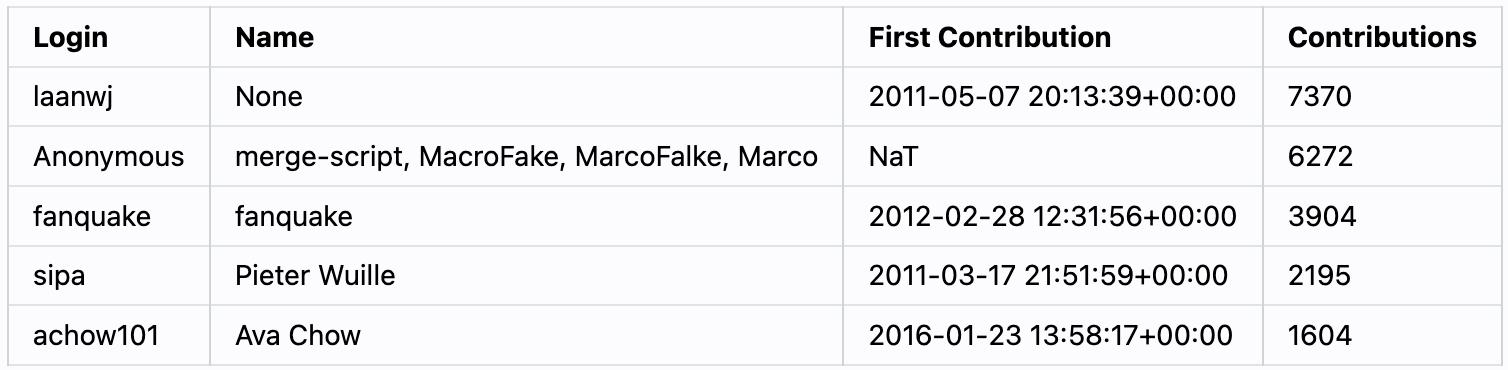
Image via: sorukumar @ Stacke Newsr
An interactive chart is also presented.
Calculating Empires: Technological Milestones Over Five Centuries
This visual genealogy plots different areas of human activities and timelines, respectively as the horizontal and vertical coordinates, to showcase technological advancements over five centuries, revealing a symbiotic evolution between technology and social structures.
Top Reads on Blockchain and Beyond
How Many Bitcoin Seed Phrases Are Only One Repeated Word?
Explores the combinatoric mathematics behind Bitcoin mnemonic phrases and checksums, revealing that repeated 12-word mnemonics are statistically more efficient than 24-word ones in terms of entropy configuration, due to the proportional differences in entropy and checksums. This difference results in a significantly higher number of valid repeated 12-word mnemonics.
By iterating through each word in the BIP39 word list, the author identifies 130 valid mnemonics consisting of the same word repeated 12 times.
Research Paper | BitVM2: Bridging Bitcoin to Second Layers
A TLDR by one of the authors Alexei Zamyatin:
This paper provides a comprehensive introduction to the design of BitVM2.
BitVM2 is:
Secure: Optimistic computation protected by Bitcoin
Practical: Challenges can be completed with 3 transactions
Permissionless: Anyone can challenge
BitVM Bridge is currently the safest Bitcoin bridge:
Traditional BTC bridges: t-of-n multi-sigs with an honest majority assumption
BitVM Bridge: A 1-of-n security model where anyone can challenge and prevent theft
Subscribe to my newsletter
Read articles from Cryptape directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
