Cyber Attack
 sudip adhikari
sudip adhikari
What is Cyber Attack ?
A cyber attack is any intentional effort by hackers to steal, expose, alter, disable, or destroy data, applications, or other assets by gaining unauthorized access to computer systems, networks, or digital devices.
Imagine your computer as a house. Now, imagine someone tries to enter or break into your house without your permission with the intention of causing harm or damage, like:
Stealing things.
Breaking your belongings.
Spying on you.
Threatening you for money, etc.

This is similar to what happens in a cyber attack, where someone tries to access your computer, phone, or network to steal, damage, or misuse your data.
Motive Behind Cyber Attack
Money: Stealing money or valuable information that can be sold.
Stealing Data: Taking sensitive information like personal details or business secrets.
Causing Disruption: Messing up services or operations to cause trouble.
Spying: Secretly watching or gathering information from individuals, businesses, or governments.
Revenge: Hurting someone or a company because of a personal grudge.
Making a Statement: Attacking to support a cause or protest.
Gaining an Advantage: Companies or governments attacking others to get ahead.
Cyber Warfare: Countries attacking each other’s systems to cause harm.
Showing Off: Hackers proving their skills for fun or recognition.
Sabotage: Intentionally damaging a company’s operations, often by insiders.
Common Types of Cyber Attacks :
1. Social Engineering Methods:
Social engineering in cyber attacks is when someone tricks you into giving away personal information or access by pretending to be someone trustworthy. Instead of using technical tricks, they use psychological manipulation to get what they want.

Phishing: Fake emails asking you to click a link and enter personal info. Example: An email claiming to be from your bank asking for your account details.
Spear Phishing: Targeted phishing aimed at a specific person or organization. Example: An email that appears to be from your boss asking for sensitive company information.
Whaling: Phishing targeting high-level executives. Example: An email pretending to be from a CEO asking for confidential financial reports.
Vishing: Voice phishing, where attackers call and trick you into giving information. Example: A phone call claiming to be from your bank asking for your account number.
Tailgating: Following someone into a secure area without proper authorization. Example: Walking in behind an employee who has an access card to enter a restricted building.
Impersonation: Pretending to be someone else to gain access. Example: Acting as an IT technician to get passwords from employees.
Dumpster Diving: Searching through trash to find valuable information. Example: Finding old documents with sensitive data thrown away.
Shoulder Surfing: Watching someone enter sensitive information like passwords. Example: Looking over someone’s shoulder as they type their PIN at an ATM.
Hoax: Spreading false information to create panic or mislead. Example: A fake email claiming there’s a virus in your computer that needs urgent action.
Watering Hole Attack: Compromising a website that is frequently visited by the target. Example: Infecting a popular industry blog with malware to target its readers.
Social Engineering Attack: Manipulating people into giving up confidential information. Example: Tricking someone into revealing their login credentials over a fake chat.
2. Application/Service Attacks:
An application or service attack is when hackers target a specific application or online service to cause harm, steal information, or disrupt its functioning.

DOS (Denial of Service): Overloading a system to make it unavailable. Example: Flooding a website with too many requests to crash it.
DDOS (Distributed Denial of Service): A DOS attack from multiple systems. Example: Using a network of infected computers to attack a website.
Man-in-the-Middle (MitM): Intercepting and possibly altering communication between two parties. Example: Eavesdropping on an unsecured Wi-Fi connection to steal data.
Buffer Overflow: Exploiting a program’s memory to run malicious code. Example: Sending too much data to a software application, causing it to crash and execute harmful code.
Injection: Inserting malicious code into an application. Example: Entering harmful SQL code into a web form to access a database.
Cross-Site Scripting (XSS): Injecting malicious scripts into web pages viewed by others. Example: Adding harmful JavaScript to a blog comment section.
Cross-Site Request Forgery (CSRF): Trick a user into performing actions on a site where they’re authenticated. Example: A malicious link making you transfer funds from your bank account.
Privilege Escalation: Gaining higher access rights than intended. Example: Exploiting a vulnerability to gain admin privileges on a system.
ARP Poisoning: Manipulating the ARP cache to intercept network traffic. Example: Redirecting network traffic from a victim to an attacker’s machine.
Amplification: Exploiting vulnerabilities to amplify the attack’s impact. Example: Using a DNS amplification attack to flood a target with traffic.
Domain Hijacking: Taking control of a domain name. Example: Changing the registration details of a domain to redirect traffic to a malicious site.
Man-in-the-Browser: Intercepting and altering browser communication. Example: Injecting malware into your browser to steal login credentials.
Zero-Day: Exploiting a previously unknown vulnerability. Example: Attacking a software vulnerability that the vendor has not yet patched.
Replay: Capturing and reusing valid data transmissions. Example: Recording a login session and replaying it to gain unauthorized access.
Pass-the-Hash: Using hashed passwords to authenticate. Example: Using captured hashed credentials to access a network without cracking the password.
Hijacking and Related Attacks: Taking control of sessions or data. Example: Hijacking a user’s active session to impersonate them.
Driver Manipulation: Altering or replacing drivers to gain control. Example: Installing malicious drivers that give attackers system-level access.
Spoofing: Pretending to be someone else. Example: Sending emails that appear to come from a trusted source to trick recipients.
MAC Spoofing: Changing the MAC address to impersonate a device. Example: Changing your device’s MAC address to bypass network access controls.
IP Address Spoofing: Pretending to be a different IP address. Example: Sending data from a forged IP address to evade detection.
3. Wireless Attacks:
A wireless attack targets wireless networks and devices to gain unauthorized access, steal information, or disrupt services.

Replay: Capturing and reusing wireless communication. Example: Recording a Wi-Fi handshake and using it to crack a network password.
IV (Initialization Vector): Exploiting weak encryption keys. Example: Capturing weak IVs used in WEP encryption to crack the network password.
Evil Twin: Setting up a fake Wi-Fi network to intercept connections. Example: Creating a Wi-Fi hotspot with a similar name to a legitimate network to capture user data.
Rogue AP (Access Point): Unauthorized access point that mimics a legitimate one. Example: Setting up a fake access point to trick users into connecting and capturing their data.
Jamming: Interfering with wireless signals. Example: Using a device to emit radio signals that disrupt Wi-Fi connections.
WPS (Wi-Fi Protected Setup): Exploiting WPS vulnerabilities to gain access. Example: Cracking a WPS PIN to access a secured Wi-Fi network.
Bluejacking: Sending unsolicited messages via Bluetooth. Example: Sending random messages to nearby Bluetooth devices.
Bluesnarfing: Accessing data from a Bluetooth device without permission. Example: Extracting contacts or other data from a Bluetooth-enabled phone.
RFID (Radio Frequency Identification): Exploiting RFID systems to read or alter data. Example: Using a scanner to read or clone RFID-enabled credit cards.
NFC (Near Field Communication): Exploiting NFC to steal data or make unauthorized transactions. Example: Using an NFC reader to capture payment information from a phone.
Disassociation: Forcing a device to disconnect from a network. Example: Sending disassociation packets to a device to drop it from a Wi-Fi network.
4. Cryptographic Attacks:
A cryptographic attack targets the security of encryption systems, aiming to break or bypass the methods used to protect data.
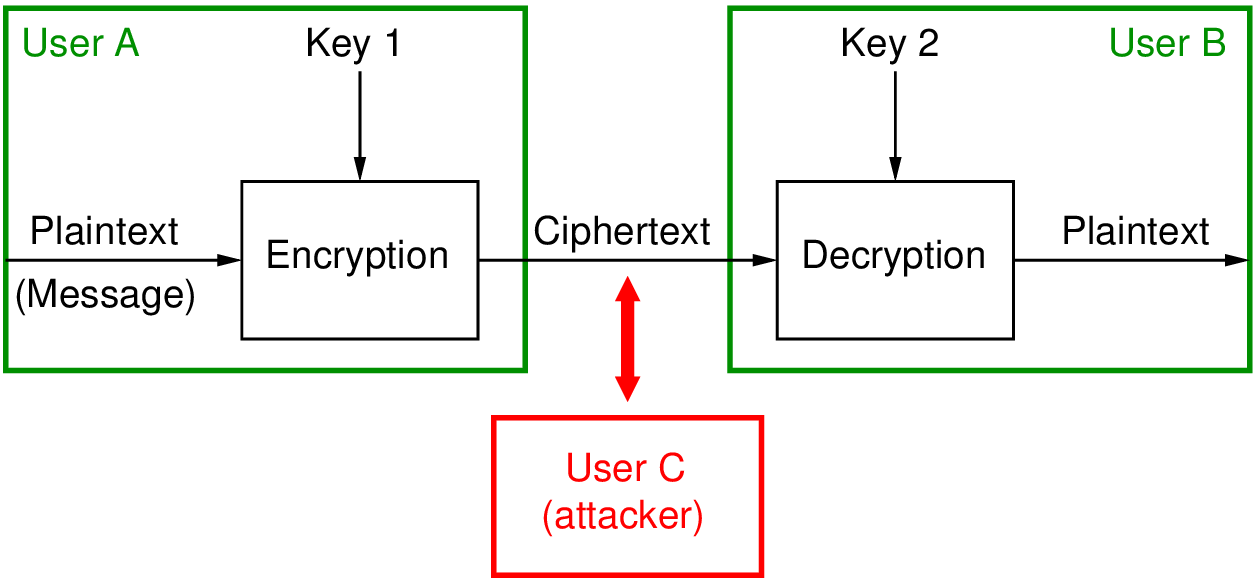
Birthday: Exploiting collisions in hash functions. Example: Finding two different pieces of data that hash to the same value.
Known Plaintext/Ciphertext: Using known data to break encryption. Example: Analyzing encrypted data where part of the plaintext is known to decrypt the rest.
Password Attacks: Trying to guess or crack passwords. Example: Using a tool to try every possible password combination.
Rainbow Tables: Precomputed tables for reversing hash functions. Example: Using a table of precomputed hashes to quickly find a password.
Dictionary: Attempting passwords from a pre-arranged list. Example: Using a list of common passwords to crack an account.
Brute Force: Trying every possible combination to crack passwords. Example: Using software to try all possible password combinations until it finds the correct one.
Hybrid Attack: Combining dictionary and brute force methods. Example: Using a dictionary list but adding numbers or symbols to guess complex passwords.
Downgrade: Forcing a system to use weaker encryption. Example: Manipulating a system to use older, less secure encryption algorithms.
Replay: Reusing encrypted messages to gain unauthorized access. Example: Capturing and replaying an encrypted authentication token.
Weak Implementations: Exploiting poorly designed encryption systems. Example: Breaking encryption due to flawed algorithm implementation or insufficient key lengths.
Cyber Attack Detection , Prevention and Response
Detection
Watch for Trouble: Use tools to keep an eye on your computer and network for any unusual activity. Example: A tool that alerts you if it spots strange behavior on your website.
Check Logs: Look at records of what’s been happening on your systems to spot any issues. Example: Reviewing logs to see if someone tried to hack into your system.
Stay Informed: Keep up-to-date with information about new cyber threats. Example: Reading updates on the latest viruses and scams.
Spot Odd Behavior: Look for anything that’s out of the ordinary. Example: Noticing a sudden increase in website traffic that might be a sign of an attack.
Prevention
Use Firewalls: Set up barriers to keep unwanted visitors out of your network. Example: A firewall that blocks suspicious connections to your network.
Install Antivirus Software: Use programs that protect your computer from malware. Example: Running antivirus scans to find and remove viruses.
Update Regularly: Keep your software up-to-date to fix security gaps. Example: Installing updates for your operating system and apps.
Control Access: Limit who can access what on your network. Example: Using passwords and extra security steps to keep unauthorized users out.
Encrypt Data: Scramble your data so only authorized people can read it. Example: Using encryption to protect sensitive files and messages.
Teach Safety: Educate people on how to avoid cyber threats. Example: Training employees on how to spot phishing emails.
Response
Have a Plan: Prepare a set of steps to follow if an attack happens. Example: Knowing exactly what to do if your computer gets infected with ransomware.
Contain the Attack: Stop the attack from spreading. Example: Disconnecting an infected computer from the network.
Remove the Threat: Get rid of the cause of the attack. Example: Using antivirus software to delete a virus.
Restore and Fix: Get your systems back to normal. Example: Reinstalling clean software and recovering data from backups.
Learn and Improve: Figure out what went wrong and fix any weaknesses. Example: Analyzing the attack to improve your security measures.
Communicate: Let everyone know what happened and what you’re doing about it. Example: Informing customers about a data breach and how you’re handling it.
By following these steps, you can better protect yourself from cyber attacks and respond effectively if one occurs.
Subscribe to my newsletter
Read articles from sudip adhikari directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

sudip adhikari
sudip adhikari
I am an explorer of IT field.