Understanding Zero Trust
 Dimple Menghani
Dimple MenghaniTable of contents
- Embracing Zero Trust: A Modern Approach to Securing Your Organization
- What is Zero Trust?
- Securing Your Network in a Zero-Trust World
- Addressing the Risks to Your Organization
- The Benefits of Adopting Zero Trust
- Integrating Zero Trust with Microsoft’s Cybersecurity Solutions
- Why Zero Trust is the Future of Security

Embracing Zero Trust: A Modern Approach to Securing Your Organization
In today’s digital world, where cyber threats are evolving, safeguarding your organization requires more than traditional defenses. With remote work, personal devices, and increasingly sophisticated cyber-attacks, the old methods of securing a perimeter are no longer enough. This is where the Zero Trust model comes in—a necessary approach that redefines how we protect our networks, data, and users.
What is Zero Trust?
Zero Trust is a security model built on the principle that no one, whether inside or outside the network, should be trusted by default. Instead, every access request is verified and every action is monitored. Think of it as a high-security facility where every door requires a keycard and every movement is tracked.
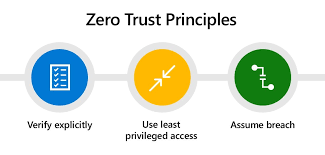
Here are the three core principles that drive Zero Trust:
Verify Explicitly: Every time someone or something tries to access your network or resources, they need to prove their legitimacy. It’s like showing ID at every checkpoint, ensuring that only those who are supposed to be there are granted access.
Use Least Privilege Access: Access is granted on a need-to-know basis. This means that users only get the permissions necessary to perform their tasks—no more, no less. By limiting access, you minimize the potential damage if an account is compromised.
Assume Breach: Zero Trust operates under the assumption that breaches are inevitable. This mindset shifts the focus from merely trying to prevent breaches to also preparing for them. It’s about having strategies in place to detect, respond to, and mitigate the effects of a breach.
Securing Your Network in a Zero-Trust World
While Zero Trust introduces new strategies, it also reinforces the importance of traditional security tools like firewalls and Virtual Private Networks (VPNs):
Firewalls: These remain the gatekeepers of your network, filtering incoming and outgoing traffic. Without them, your network would be exposed to all sorts of threats, from unauthorized access to malware.
VPNs: VPNs create secure connections over public networks, ensuring that when employees connect from places like coffee shops or airports, their data is protected. It’s like having a private conversation in a crowded room—no one can listen in.
Addressing the Risks to Your Organization
Incorporating a zero-trust policy helps mitigate a variety of risks that organizations face today:
Insider Threats: Sometimes, the biggest threats come from within. Whether intentional or accidental, employees can leak sensitive information. Zero Trust ensures that even insiders have limited access, reducing the risk of internal breaches.
Credential Theft: Hackers often use stolen credentials to gain access to networks. With Zero Trust, even if they have the credentials, they’re still required to pass multiple checks before they can do any damage.
User Exploitation: If a user’s account is compromised, Zero Trust’s continuous monitoring and verification make it difficult for attackers to move freely within the network.
Malware and Viruses: Devices infected with malware can wreak havoc on a network. Zero Trust ensures that every device is scanned, compliant, and healthy before it connects, reducing the risk of infection.
The Benefits of Adopting Zero Trust
Implementing a zero-trust framework offers several significant benefits that extend beyond just enhanced security:
Enhanced User Experience: Zero Trust automates security processes, allowing employees to work securely from anywhere—whether at home, in the office, or on the go—without constantly dealing with complicated security checks.
Protection of IT Assets: From data to devices, every layer of your IT infrastructure is safeguarded. Zero Trust ensures that vulnerabilities are continuously monitored and addressed before they can be exploited.
Improved Security Monitoring: With Zero Trust, your network is under constant surveillance, reducing the chance of human error and ensuring that potential threats are detected and mitigated quickly. It’s like having a security team that never sleeps.
Integrating Zero Trust with Microsoft’s Cybersecurity Solutions
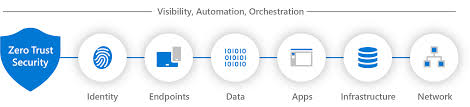
Zero Trust is a key component of Microsoft’s Cybersecurity Reference Architecture (MCRA). Through the Rapid Modernization Plan (RAMP), Microsoft helps organizations identify the most effective controls for common attacks with minimal disruption. Here’s how it works:
Identity: Tools like Azure AD and Microsoft Defender for Identity help secure user identities by implementing policies such as role-based access and multi-factor authentication (MFA).
Endpoint: Whether a device is company-owned or personal, it’s subject to the same security checks before accessing corporate data. This ensures that every device, regardless of its ownership, meets the organization’s security standards.
Data: Sensitive information is classified, labeled, and protected through encryption and rights management, ensuring that it doesn’t fall into the wrong hands.
Applications: Applications are continuously monitored for unusual activity, ensuring that only approved users have access. This helps prevent unauthorized access and data leaks.
Infrastructure: All hardware, software, and network components are under constant scrutiny, with alerts generated for any suspicious activity. This proactive approach ensures that potential threats are detected early and addressed promptly.
Network: To secure the network, Zero Trust advocates for proactive measures, such as segmenting network traffic and securing cloud environments. This reduces the risk of widespread attacks and ensures that your cloud environments are secure.
Why Zero Trust is the Future of Security
In a world where the next cyber threat could be just around the corner, Zero Trust offers a smarter, more resilient way to stay secure. By verifying every request, limiting access, and always preparing for the worst, Zero Trust not only protects your organization—it also future-proofs it. Adopting a zero-trust framework is more than just a technological shift; it’s a strategic move toward a more secure and resilient organization.
In an era where cyber threats are constantly evolving, embracing Zero Trust isn’t just about keeping up—it’s about staying ahead.
Subscribe to my newsletter
Read articles from Dimple Menghani directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
