How to Activate CloudTrail in Your AWS Environment
 George Palangattil
George Palangattil
Introduction
AWS CloudTrail is a service that enables governance, compliance, and operational and risk auditing of your AWS account. It logs all API calls made within your AWS environment, including those made through the AWS Management Console, AWS SDKs, command-line tools, and other AWS services.
Why is CloudTrail Important?
With CloudTrail, you can keep an eye on and archive account activity linked to actions taken throughout your AWS infrastructure. It may be essential for compliance obligations, security audits, and identifying any strange activity in your account.
Setting Up CloudTrail in a Single Account
Prerequisites
Necessary IAM permissions to create CloudTrail (e.g., cloudtrail:CreateTrail).
S3 bucket (optional, but necessary if storing logs outside of the default location).
Enable the Trail
Navigate to the AWS CloudTrail Console and Click on Create a trail
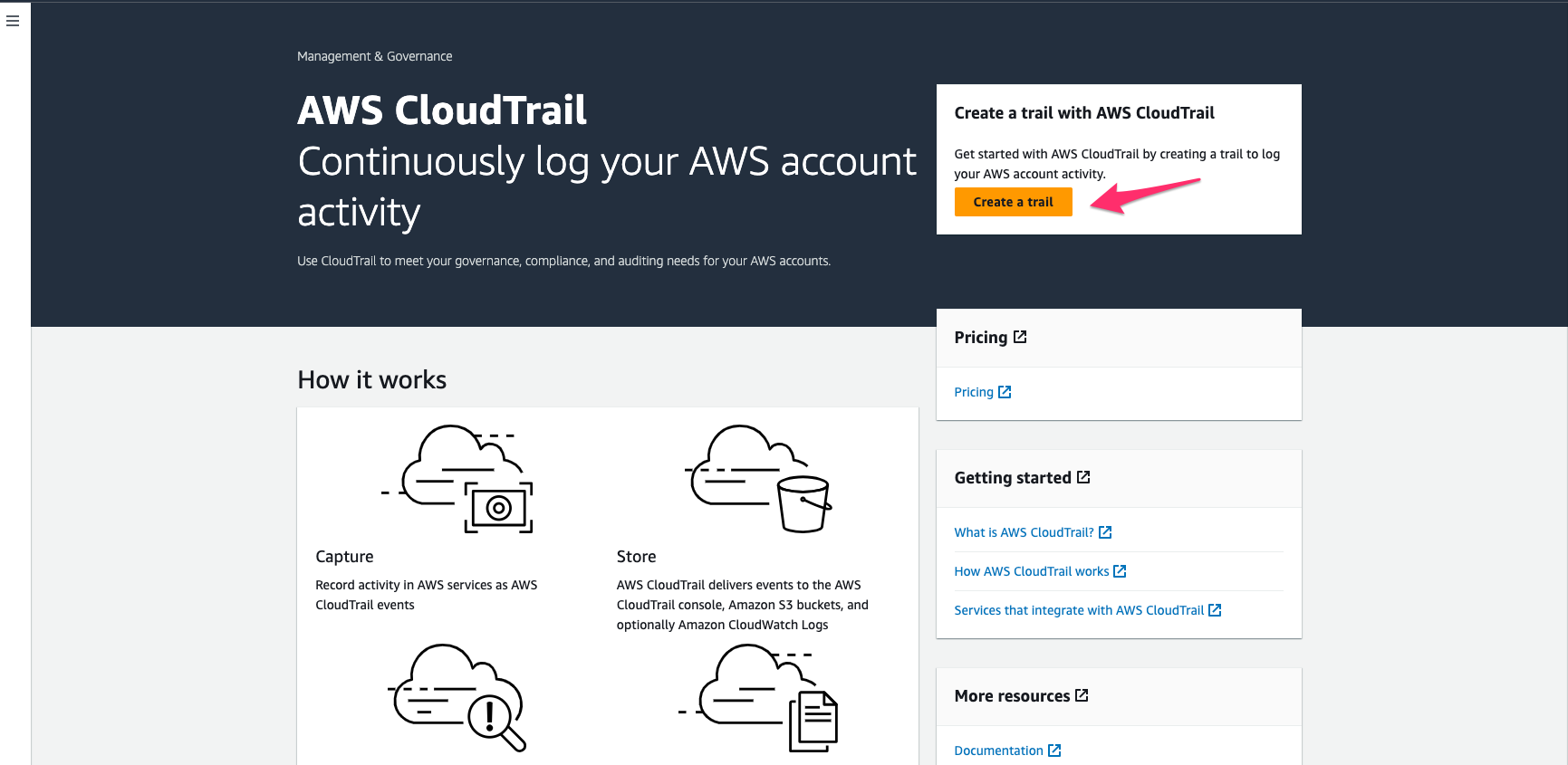
Create Trail
In the CloudTrail dashboard, click on "Create trail".
Provide a name for your trail.
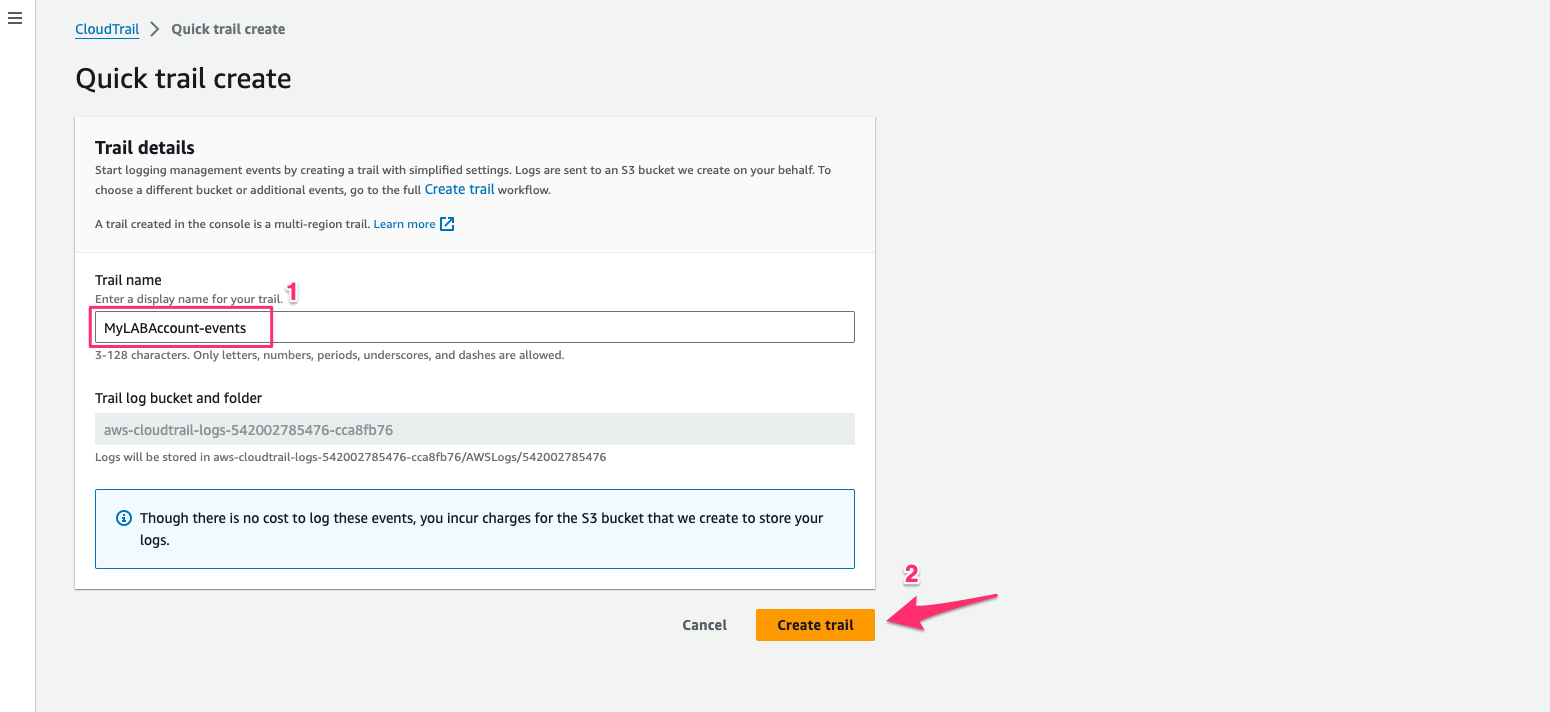
Trail first look
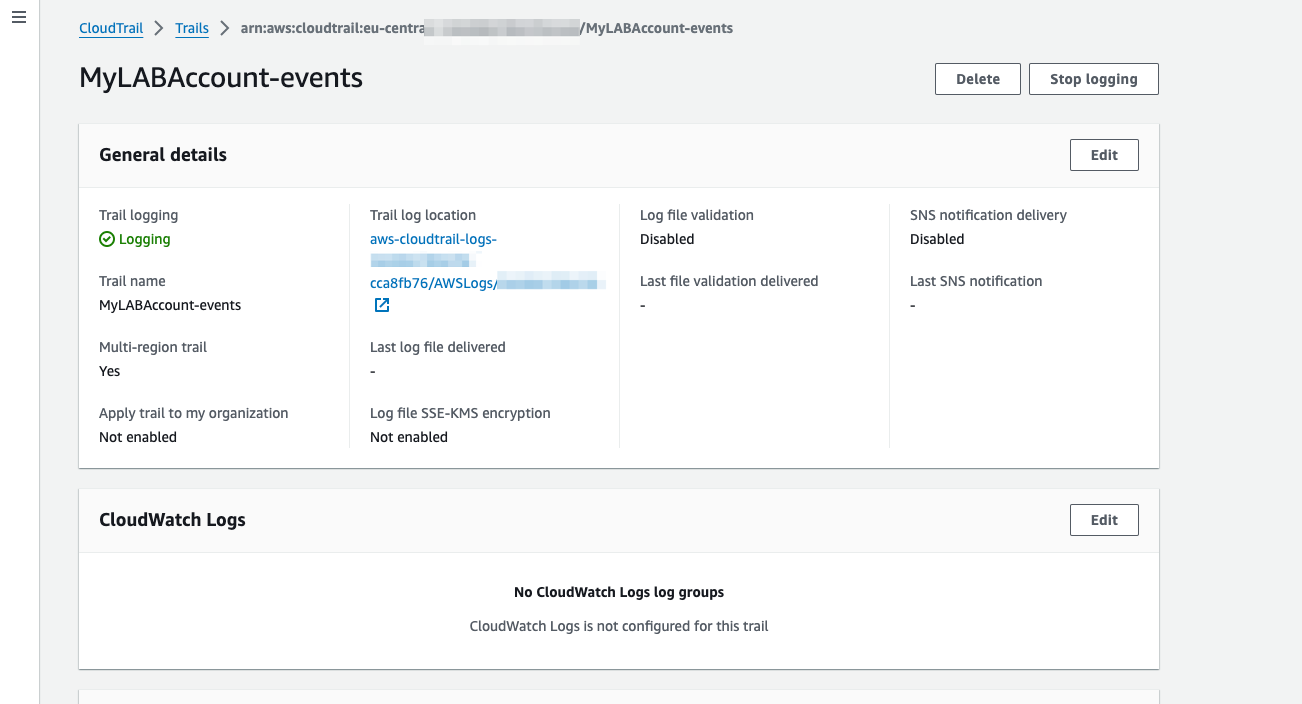
Configure the Storage.
Click on Edit in the General details section.
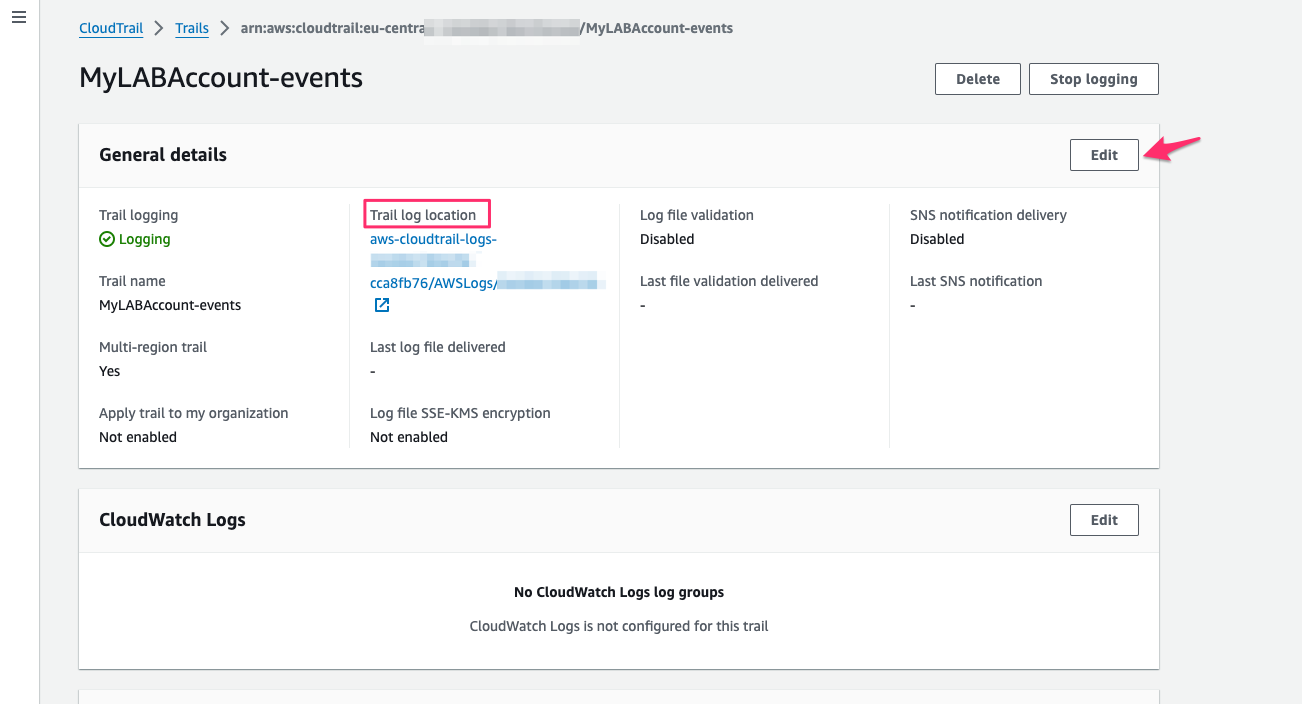
Select "Use existing S3 Bucket, then click Browse and select the bucket
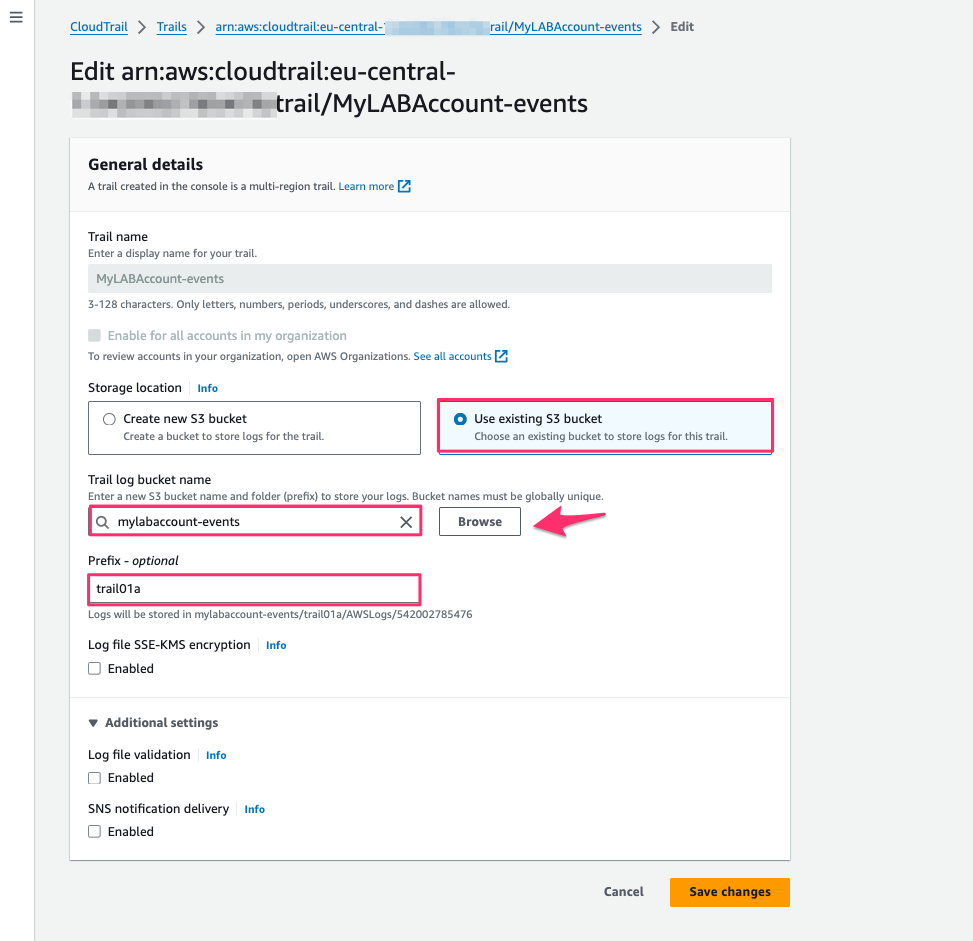
Choose Additional Settings (Recommended)
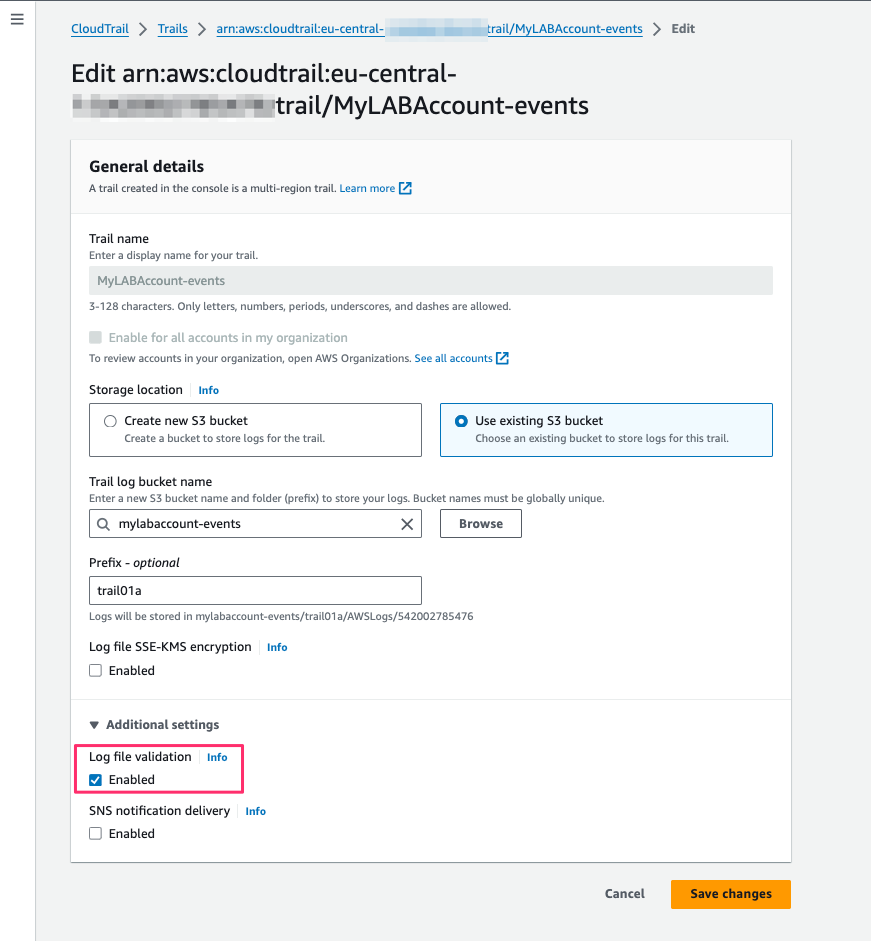
Save Changes.
Select the Events ( Management / Data /Insights)
By Default Management events is enabled read and write.
The rest must be manually enable as per the requriements.
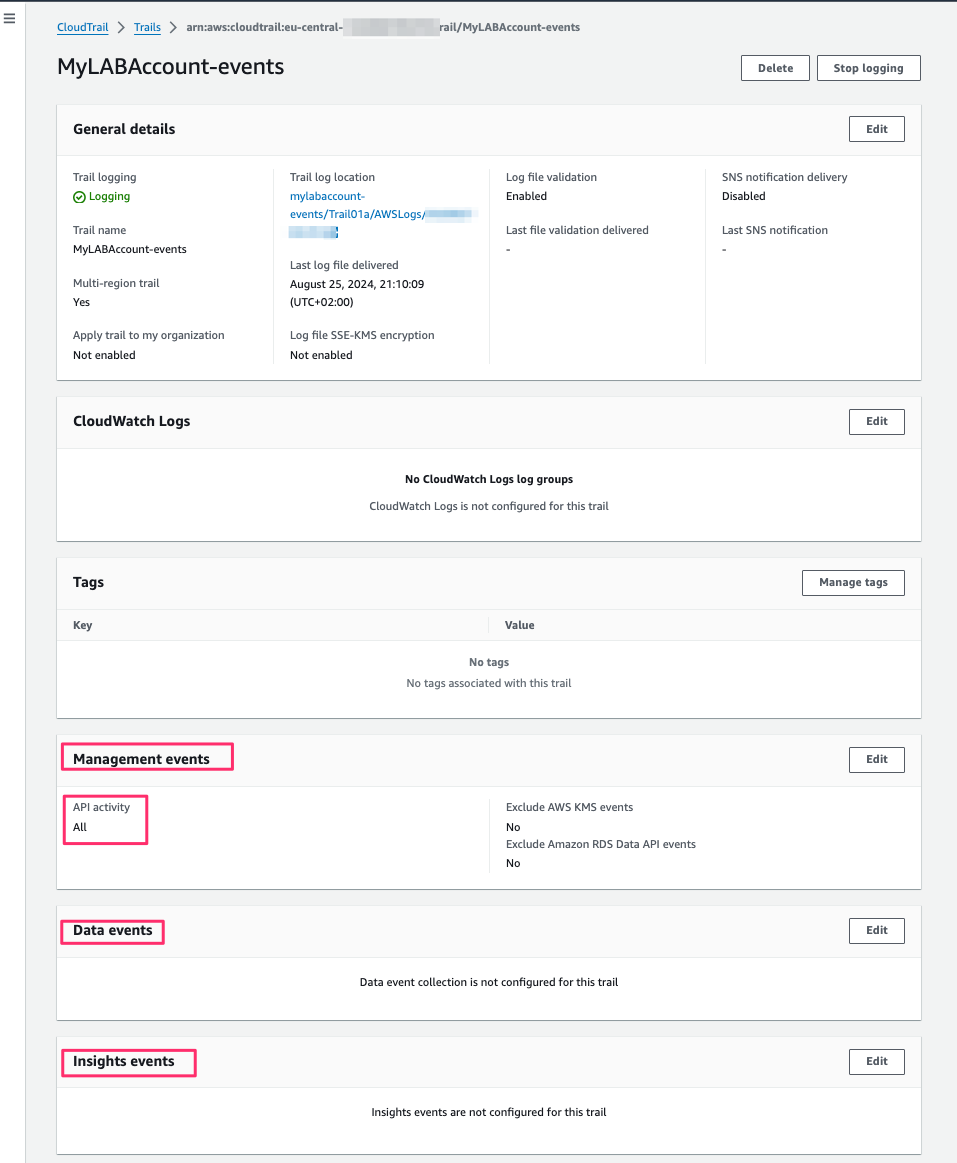
Best Practices
Enable Log File Validation
Use Multi-Region Trails
Monitor for Anomalies
Set Up Alerts
Review and Rotate Keys
Conclusion
AWS CloudTrail is a service that logs all API calls made in your AWS environment, providing detailed records of activities across your account. It plays a crucial role in security, compliance, and operational auditing by enabling you to monitor and track actions such as who accessed resources, when, and from where. CloudTrail logs can be stored in an S3 bucket, integrated with CloudWatch for real-time monitoring, and used to trigger automated responses to specific events. This makes it an essential tool for maintaining transparency, ensuring accountability, and responding to potential security incidents in your AWS environment.
Subscribe to my newsletter
Read articles from George Palangattil directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
