Day-44: ClusterRole and ClusterRoleBinding in Kubernetes
 priyadarshi ranjan
priyadarshi ranjan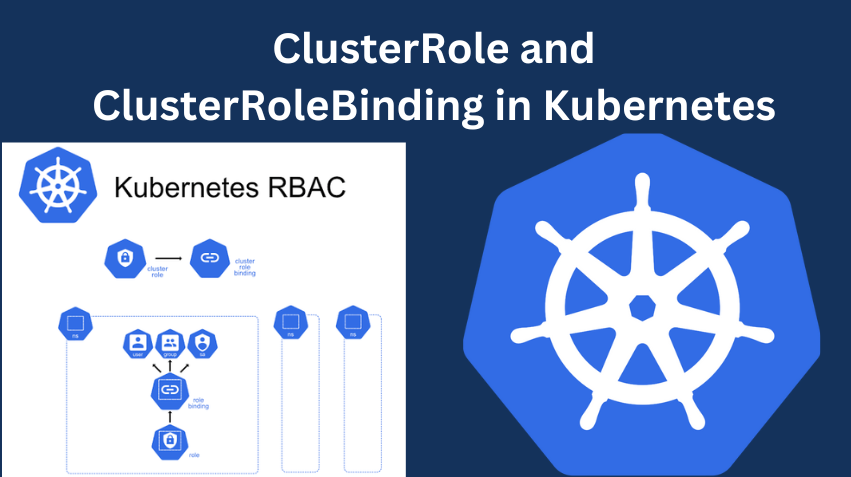
Hello DevOps Enthusiasts! 👋
Aaj hum baat karenge Kubernetes ke do important concepts ke baare mein: ClusterRole aur ClusterRoleBinding. Yeh dono concepts aapko apne Kubernetes cluster mein access control ko efficiently manage karne mein madad karte hain. Is blog mein hum in concepts ko easy language mein samjhenge, sath hi real-life examples aur practical demonstration bhi dekhenge. Chaliye shuru karte hain! 🚀
ClusterRole Kya Hai?
Soch lijiye, aapke paas ek bahut bada Kubernetes cluster hai jisme multiple namespaces hain. Aap chahte hain ki kuch users ya services ko poore cluster (matlab har namespace) mein specific resources pe actions perform karne ki permission mile. Yahi kaam ClusterRole karta hai.
ClusterRole ek aisa role hai jo cluster-wide permissions define karta hai. Matlab, is role ke through aap define kar sakte hain ki kaunse actions kisi bhi namespace ke resources pe allow kiye gaye hain.
Example:
- Agar aap chahte hain ki ek user har namespace mein pods ko dekh sake, to aap ek ClusterRole create kar sakte hain jo
get,list, aurwatchpermissions define kare pods ke liye.
ClusterRoleBinding Kya Hai?
Ab agar aapne ClusterRole bana diya, to agla step hota hai us ClusterRole ko kisi user, group, ya service account ke sath associate karna. Yahi kaam ClusterRoleBinding karta hai.
ClusterRoleBinding ek aisa object hai jo ek ClusterRole ko specific users ya groups ke sath bind karta hai. Iske through aap ensure karte hain ki woh users ya services cluster-wide permissions use kar sakein.
ClusterRole aur ClusterRoleBinding ke Components
1. ClusterRole:
apiGroups: Yeh define karta hai ki kaunse API groups par yeh role apply hoga.
resources: Yeh specify karta hai ki kaunse resources par yeh role apply hoga (jaise pods, services, etc.).
verbs: Yeh actions ko define karta hai jo is role ke through perform kiye ja sakte hain (jaise
get,list,create, etc.).
2. ClusterRoleBinding:
subjects: Yeh define karta hai ki kaunse users, groups, ya service accounts is binding ke part hain.
roleRef: Yeh specify karta hai ki kaunsa ClusterRole iss binding se associated hai.
Real-Life Example
Sochiye, aap ek DevOps engineer hain aur aapko ensure karna hai ki har team member cluster ke sabhi namespaces mein pods ko dekh sake, lekin unhe delete ya modify na kar sake. Iska solution hai ek ClusterRole banaiye jisme pods ko dekhne ki permissions ho, aur phir usse har team member ke sath bind kariye using ClusterRoleBinding.
Practical Demonstration: ClusterRole aur ClusterRoleBinding
Ab chaliye ek practical example dekhte hain jisme hum ek ClusterRole aur ClusterRoleBinding create karenge.
Step 1: ClusterRole ka Manifest File
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: pod-reader
rules:
- apiGroups: [""]
resources: ["pods"]
verbs: ["get", "list", "watch"]
Is manifest file mein humne ek pod-reader ClusterRole banaya hai jo cluster ke sabhi namespaces mein pods ko dekhne ki permission deta hai.
Step 2: ClusterRoleBinding ka Manifest File
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: read-pods-global
subjects:
- kind: User
name: "jane"
apiGroup: rbac.authorization.k8s.io
roleRef:
kind: ClusterRole
name: pod-reader
apiGroup: rbac.authorization.k8s.io
Is file mein humne jane user ko pod-reader ClusterRole bind kiya hai, jisse woh poore cluster mein pods dekh sakti hai.
Step 3: Apply Manifest Files
kubectl apply -f clusterrole.yaml
kubectl apply -f clusterrolebinding.yaml
Yeh commands aapke ClusterRole aur ClusterRoleBinding ko Kubernetes cluster mein apply kar denge.
Step 4: Test Karein
kubectl auth can-i list pods --as=jane --all-namespaces
Is command se aap check kar sakte hain ki jane user ke paas pods ko dekhne ki permission hai ya nahi.
Conclusion
So, ab aap samajh gaye honge ki ClusterRole aur ClusterRoleBinding kya hote hain aur inka use kaise kiya jata hai Kubernetes mein cluster-wide access control implement karne ke liye. Yeh concepts aapke cluster ki security aur management ko enhance karne mein bahut useful hain. Jab aapko cluster-wide permissions ko manage karna ho, to inhe zaroor consider karein.
Keep exploring, keep learning! 😊
Connect and Follow Me on Socials
Subscribe to my newsletter
Read articles from priyadarshi ranjan directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

priyadarshi ranjan
priyadarshi ranjan
Greetings! 👋 I'm Priyadarshi Ranjan, a dedicated DevOps Engineer embarking on an enriching journey. Join me as I delve into the dynamic realms of cloud computing and DevOps through insightful blogs and updates. 🛠️ My focus? Harnessing AWS services, optimizing CI/CD pipelines, and mastering infrastructure as code. Whether you're peers, interns, or curious learners, let's thrive together in the vibrant DevOps ecosystem. 🌐 Connect with me for engaging discussions, shared insights, and mutual growth opportunities. Let's embrace the learning curve and excel in the dynamic realm of AWS and DevOps technology!